ABP is a renowned open-source .NET framework, and its “
/api/abp/api-definition“ path within the framework leaks the API interfaces within the project.
Within this, we can identify the API paths inherent to the ABP framework itself.
like api/abp/xxx
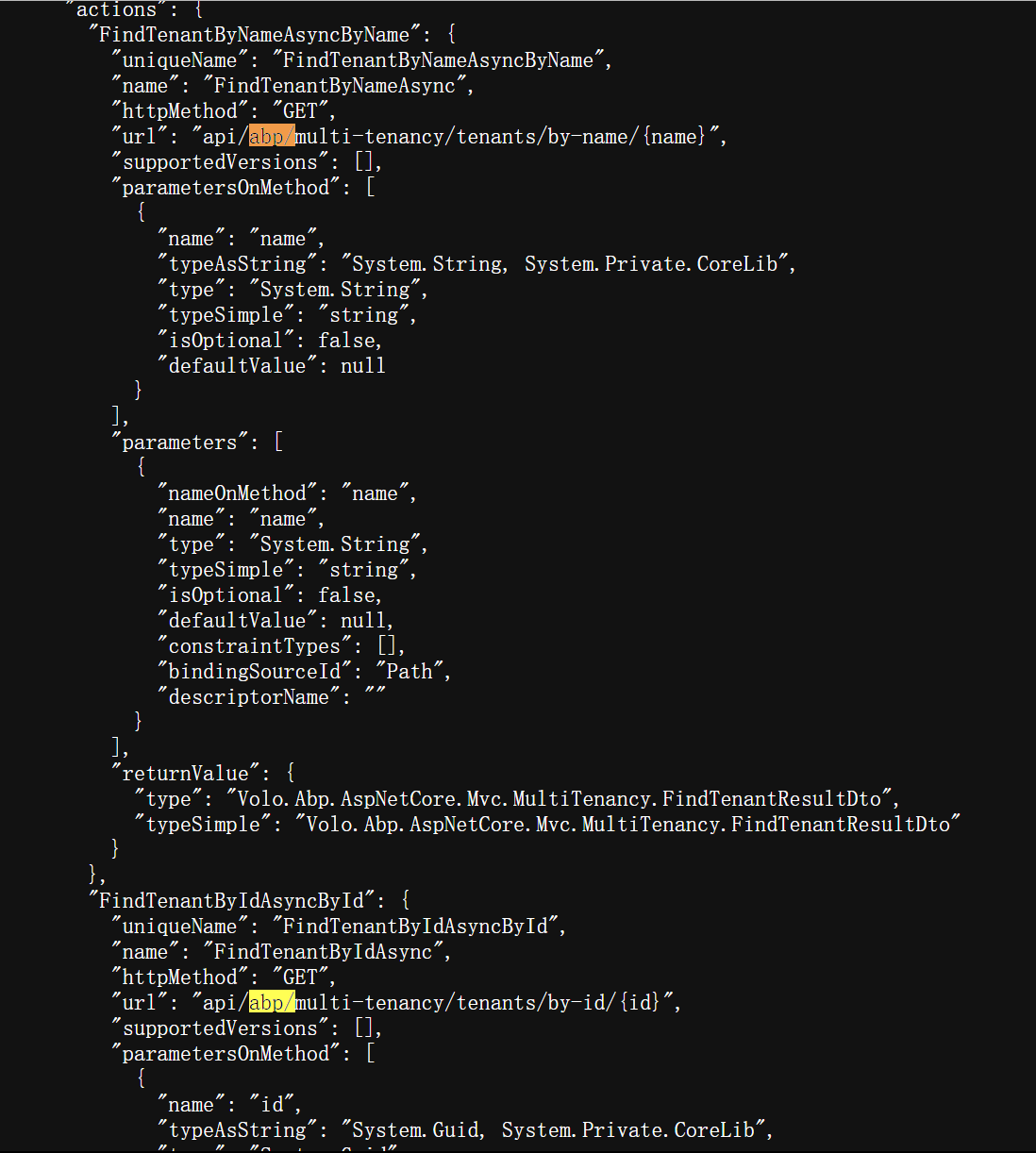
The leaked API path of ABP itself is not the primary danger, as it is quite limited. However, developers using this framework may not realize that the APIs in their own projects are directly exposed within the api-definition file. Consequently, when developers utilize this framework, the custom APIs they create during secondary development are also added to the api-definition. These newly added APIs might be subject to a lack of authentication.
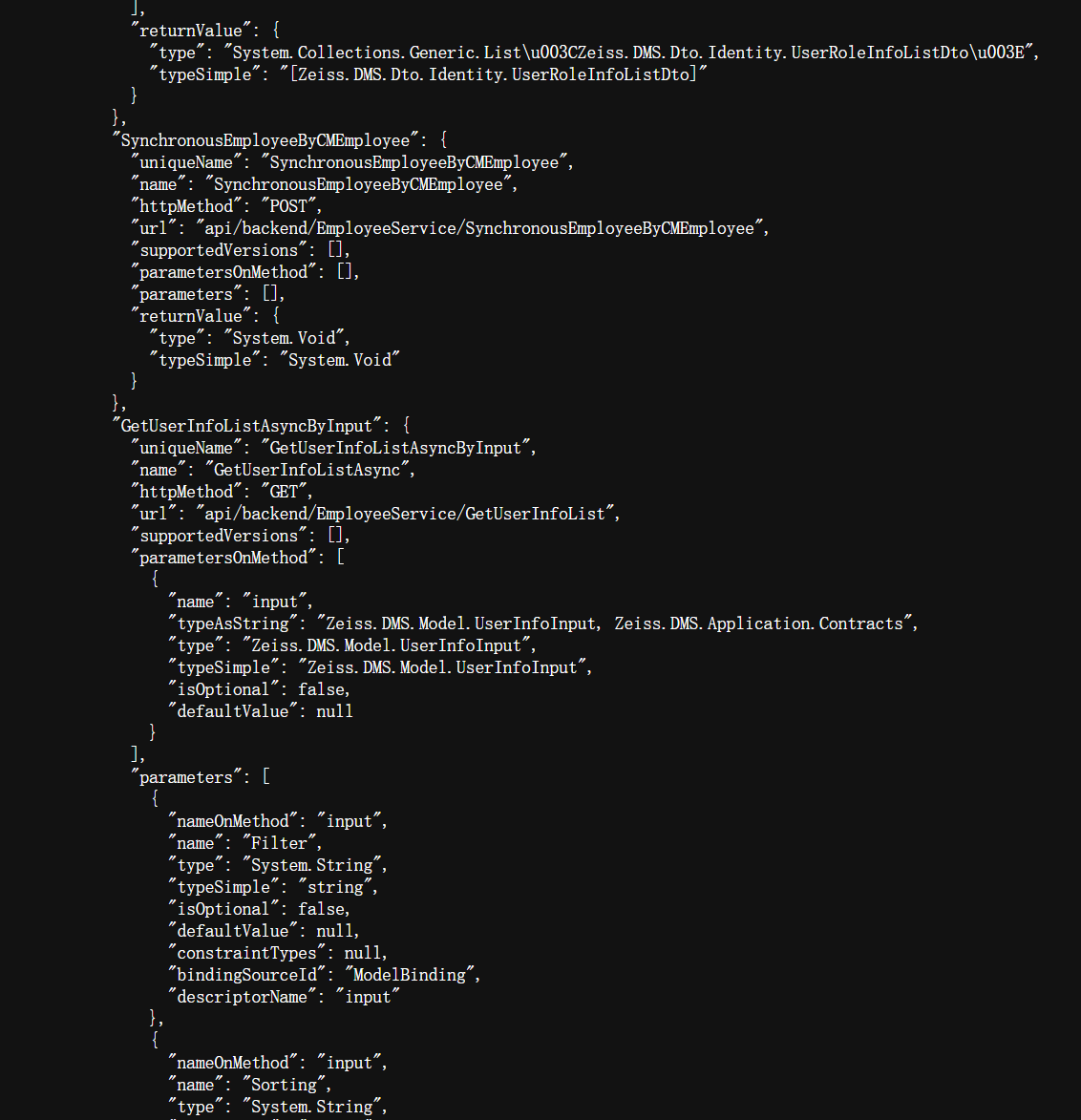
As in this case, the path api/backend/EmployeeService/GetUserInfoList is clearly an interface that was added by developers later on in the development based on ABP.
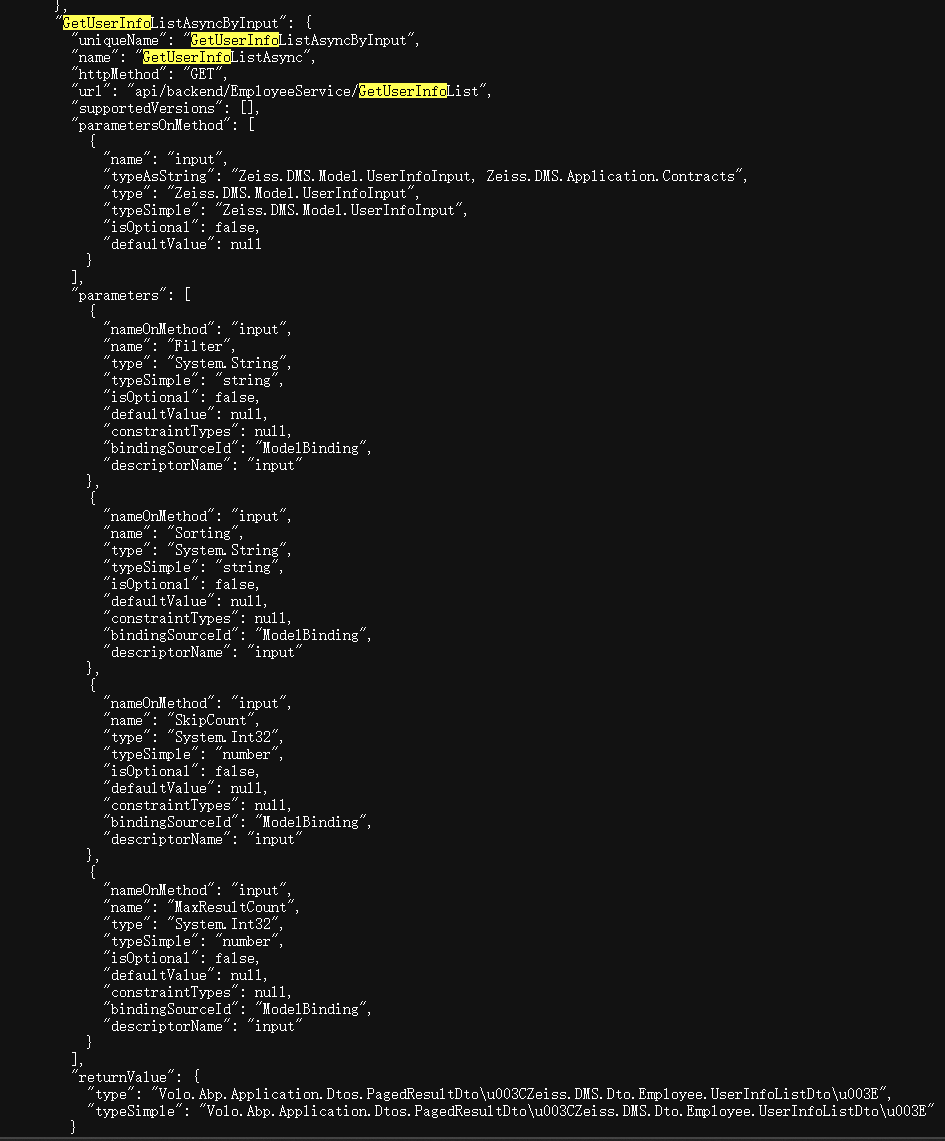
As attackers, we don’t even need to perform directory brute-forcing or fuzzy testing. Simply by exporting the interfaces from /api/abp/api-definition and conducting a validity traversal, we can obtain detailed information about these interfaces, including the structure of the invocation parameters.
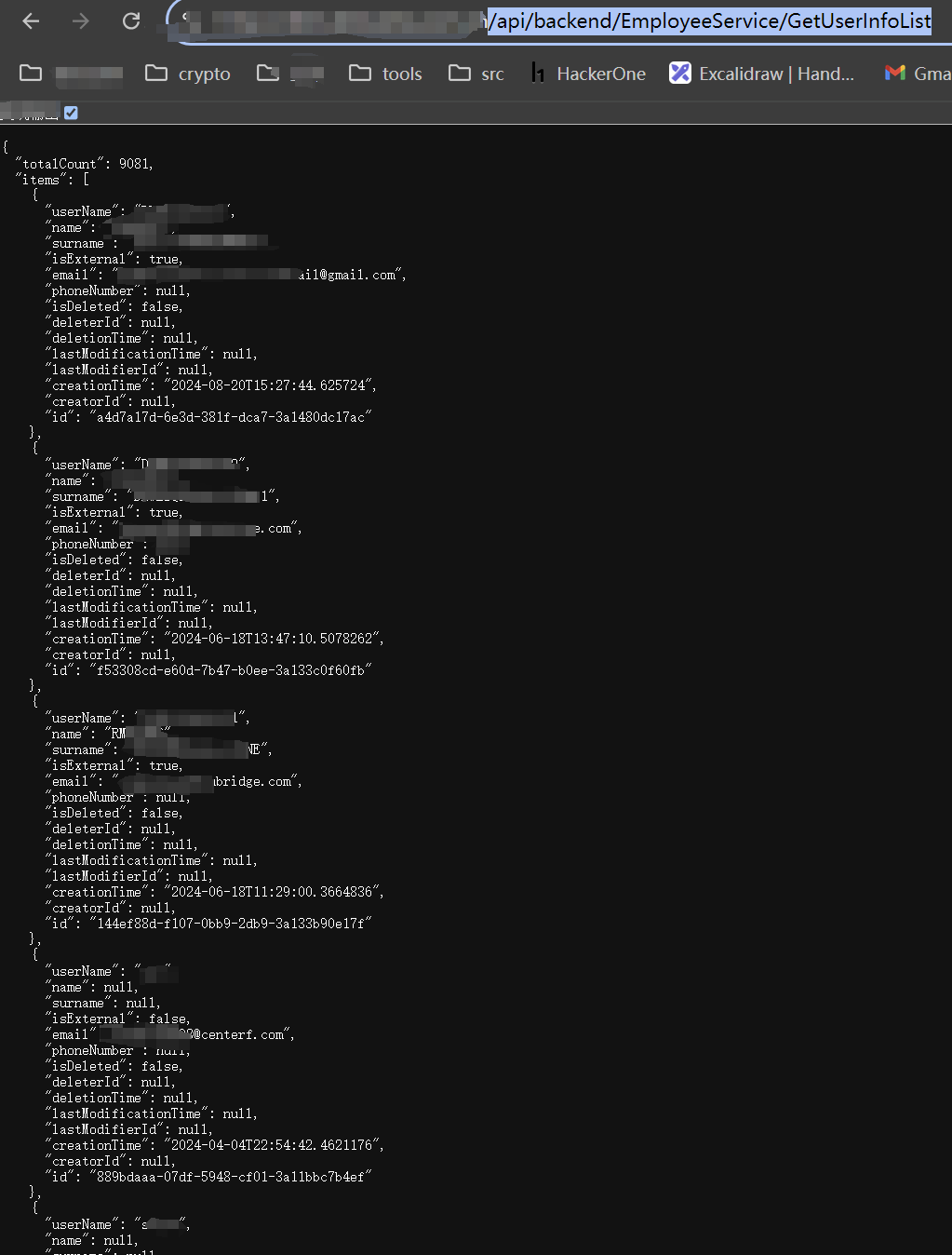
In this case, by accessing the leaked API interface, we directly obtained personnel-related information of the target application.
Certainly, this is just one of the hazards. The extent of the actual harm depends on how the developer defines the functionality of the interface. In addition, while reviewing the ABP documentation, I found that this framework comes with Swagger by default.
Of course, this issue also exists in this case.
However, some secondary developers may have noticed the presence of Swagger in the ABP framework while reviewing the official documentation and have implemented authentication or path access controls for it. Nevertheless, even then, they might not impose restrictions on the /api/abp/api-definition endpoint.
In summary, within web applications based on the ABP framework, I have successfully identified and exploited various interfaces, includinghexo personnel information leaks, file uploads, file downloads, and more. Developers may not have realized that their APIs are directly exposed through the /api/abp/api-definition endpoint. As a result, these interfaces often have serious issues with authentication. Currently, I have observed that a large number of enterprises are using this framework, and after testing several larger companies, I found that they all have this issue.
And a series of new frameworks derived from this framework also commonly have this issue.
For attackers, all they need to do is scan for the existence of the “/api/abp/api-definition” directory.

